Abstract
Post-quantum cryptographic primitives have a range of trade-offs compared to traditional public key algorithms, either having slower computation or larger public keys and ciphertexts/signatures, or both. While the performance of these algorithms in isolation is easy to measure and has been a focus of optimization techniques, performance in realistic network conditions has been less studied. Google and Cloudflare have reported results from running experiments with post-quantum key exchange algorithms in the Transport Layer Security (TLS) protocol with real users’ network traffic. Such experiments are highly realistic, but cannot be replicated without access to Internet-scale infrastructure, and do not allow for isolating the effect of individual network characteristics.
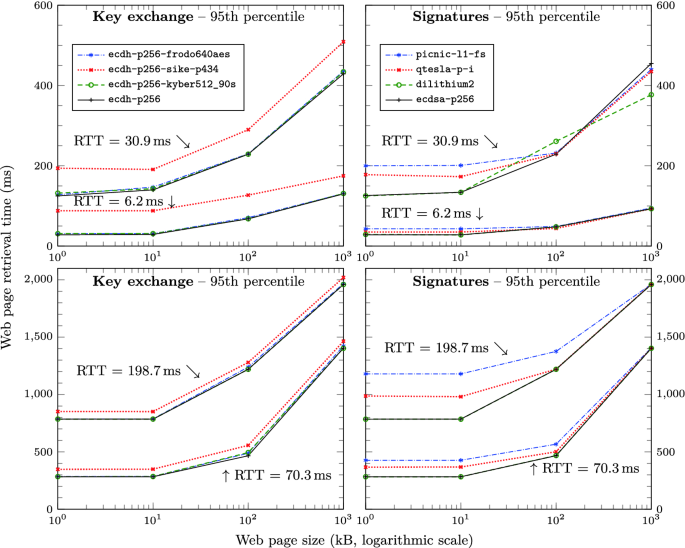
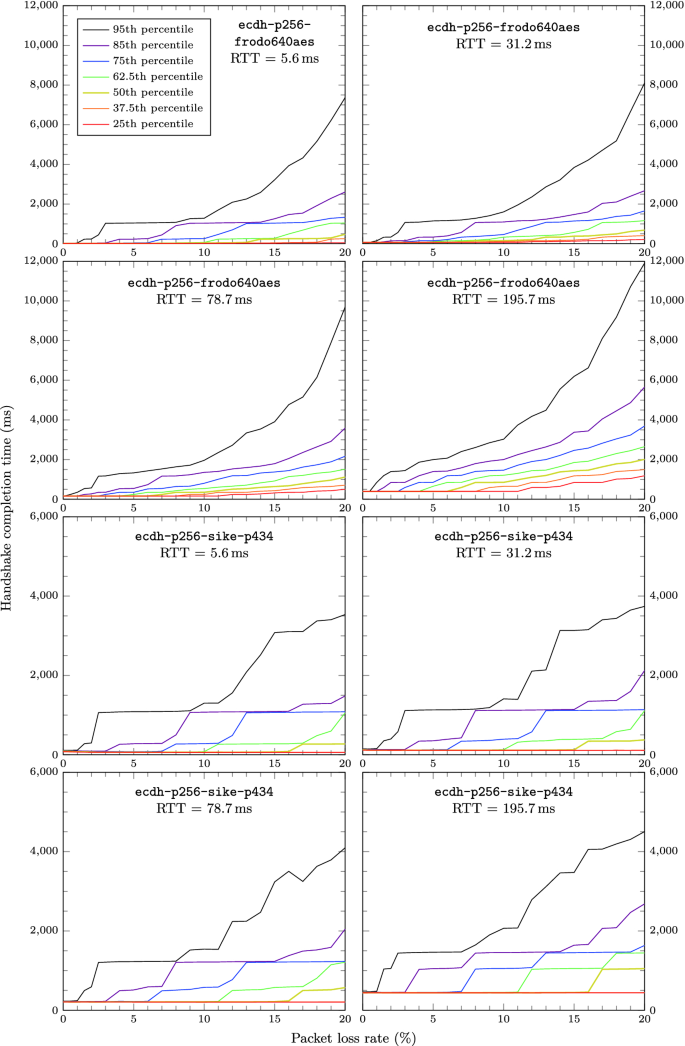
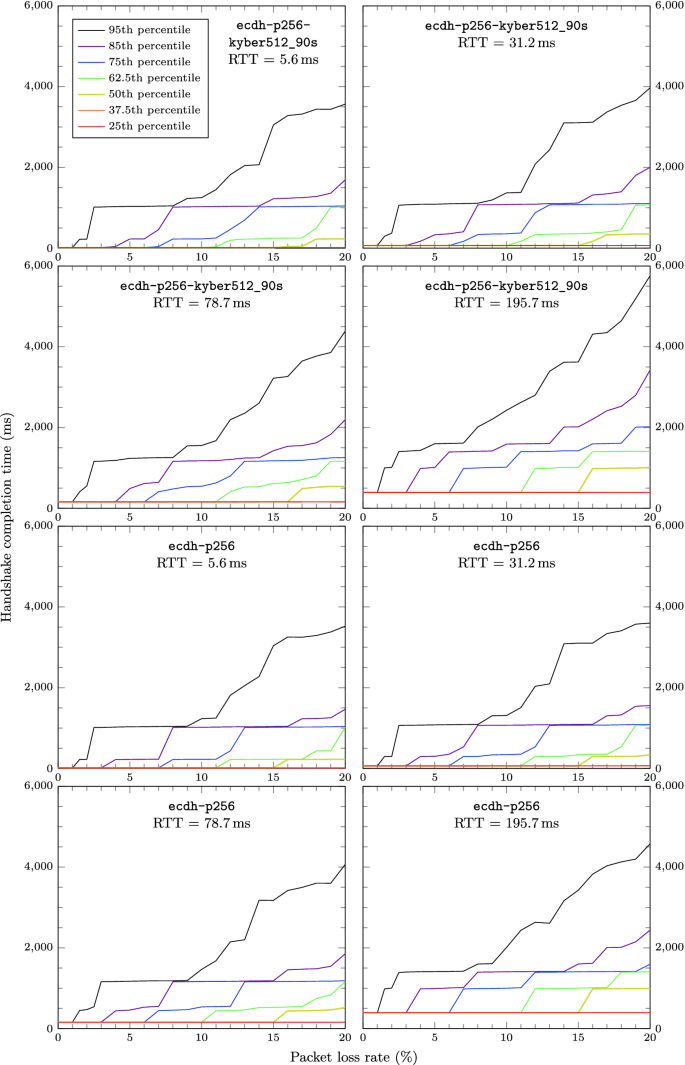
In this work, we develop and make use of a framework for running such experiments in TLS cheaply by emulating network conditions using the networking features of the Linux kernel. Our testbed allows us to independently control variables such as link latency and packet loss rate, and then examine the performance impact of various post-quantum-primitives on TLS connection establishment, specifically hybrid elliptic curve/post-quantum key exchange and post-quantum digital signatures, based on implementations from the Open Quantum Safe project. Among our key results, we observe that packet loss rates above 3–5% start to have a significant impact on post-quantum algorithms that fragment across many packets, such as those based on unstructured lattices. The results from this emulation framework are also complemented by results on the latency of loading entire web pages over TLS in real network conditions, which show that network latency hides most of the impact from algorithms with slower computations (such as supersingular isogenies).
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
It may be possible that IND-CPA KEMs suffice for ephemeral key exchange, but this is an open question. Proofs of Diffie–Hellman key exchange in TLS 1.2 [13, 18] showed that security against active attacks is required; existing proofs of TLS 1.3 [11] also use an “active” Diffie–Hellman assumption, but whether an active assumption is necessary has not yet been resolved.
- 2.
Our Internet data-centre-to-data-centre experiment actually included all Level 1 algorithms supported by liboqs (additionally bike1l1cpa, newhope512cca, ntru_hps2048509, lightsaber, and picnic2l1fs) and additionally hybrid authentication with RSA-3072. The network emulation experiments take much longer to run than the Internet experiments, so we did not have time to collect corresponding network emulation results. For parity, in this paper we only present the results obtained using the same algorithms as in the network emulation experiment. The additional data collected can be found on our GitHub repository.
- 3.
nginx worker processes handle connections using an asynchronous, event-driven approach.
- 4.
The slight downward slope for the first few packet loss rates in the median results for ecdh-p256-sike-p434 is an artifact of the experiment setup used: at low packet loss rates, the setup results in many connection requests arriving simultaneously, causing a slight denial-of-service-like effect while the server queues some calculations.
References
Amazon Web Services. s2n (2014). https://github.com/awslabs/s2n
Apache Software Foundation. ab - Apache HTTP server benchmarking tool (2019). https://httpd.apache.org/docs/current/programs/ab.html
Biederman, E.W.: IP-NETNS(8), January 2013. http://man7.org/linux/man-pages/man8/ip-netns.8.html
Biederman, E.W., Pospíšek, T.: VETH(4), February 2018. http://man7.org/linux/man-pages/man4/veth.4.html
Bindel, N., et al.: qTESLA. Technical report, National Institute of Standards and Technology (2019). https://csrc.nist.gov/projects/post-quantum-cryptography/round-2-submissions
Bos, J.W., et al.: Frodo: take off the ring! practical, quantum-secure key exchange from LWE. In: Weippl, E.R., Katzenbeisser, S., Kruegel, C., Myers, A.C., Halevi, S. (eds.) ACM CCS 2016, pp. 1006–1018. ACM Press, October 2016. https://doi.org/10.1145/2976749.2978425
Bos, J.W., Costello, C., Naehrig, M., Stebila, D.: Post-quantum key exchange for the TLS protocol from the ring learning with errors problem. In: 2015 IEEE Symposium on Security and Privacy, pp. 553–570. IEEE Computer Society Press, May 2015. https://doi.org/10.1109/SP.2015.40
Braithwaite, M.: Experimenting with post-quantum cryptography, July 2016. https://security.googleblog.com/2016/07/experimenting-with-post-quantum.html
Campagna, M., Crockett, E.: Hybrid Post-Quantum Key Encapsulation Methods (PQ KEM) for Transport Layer Security 1.2 (TLS). Internet-Draft draft-campagna-tls-bike-sike-hybrid-01, Internet Engineering Task Force, May 2019. Work in Progress. https://datatracker.ietf.org/doc/html/draft-campagna-tls-bike-sike-hybrid-01
Crockett, E., Paquin, C., Stebila, D.: Prototyping post-quantum and hybrid key exchange and authentication in TLS and SSH. In: NIST 2nd Post-Quantum Cryptography Standardization Conference 2019, August 2019
Dowling, B., Fischlin, M., Günther, F., Stebila, D.: A cryptographic analysis of the TLS 1.3 handshake protocol candidates. In: Ray, I., Li, N., Kruegel, C. (eds.) ACM CCS 2015, pp. 1197–1210. ACM Press, October 2015. https://doi.org/10.1145/2810103.2813653
http archive. Page weight, Novober 2019. https://httparchive.org/reports/page-weight
Jager, T., Kohlar, F., Schäge, S., Schwenk, J.: On the security of TLS-DHE in the standard model. In: Safavi-Naini, R., Canetti, R. (eds.) CRYPTO 2012. LNCS, vol. 7417, pp. 273–293. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-32009-5_17
Jao, D., et al.: SIKE. Technical report, National Institute of Standards and Technology (2019). https://csrc.nist.gov/projects/post-quantum-cryptography/round-2-submissions
Kampanakis, P., Sikeridis, D.: Two post-quantum signature use-cases: Non-issues, challenges and potential solutions. Cryptology ePrint Archive, Report 2019/1276 (2019). https://eprint.iacr.org/2019/1276
Kannwischer, M.J., Rijneveld, J., Schwabe, P., Stebila, D., Wiggers, T.: The PQClean project, November 2019. https://github.com/PQClean/PQClean
Kiefer, F., Kwiatkowski, K.: Hybrid ECDHE-SIDH key exchange for TLS. Internet-Draft draft-kiefer-tls-ecdhe-sidh-00, Internet Engineering Task Force, November 2018. Work in Progress. https://datatracker.ietf.org/doc/html/draft-kiefer-tls-ecdhe-sidh-00
Krawczyk, H., Paterson, K.G., Wee, H.: On the security of the TLS protocol: a systematic analysis. In: Canetti, R., Garay, J.A. (eds.) CRYPTO 2013. LNCS, vol. 8042, pp. 429–448. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-40041-4_24
Kwiatkowski, K., Langley, A., Sullivan, N., Levin, D., Mislove, A., Valenta, L.: Measuring TLS key exchange with post-quantum KEM. In: NIST 2nd Post-Quantum Cryptography Standardization Conference 2019, Auguest 2019
Langley, A.: CECPQ2, December 2018. https://www.imperialviolet.org/2018/12/12/cecpq2.html
Langley, A.: Post-quantum confidentiality for TLS, April 2018. https://www.imperialviolet.org/2018/04/11/pqconftls.html
Langley, A.: Real-world measurements of structured-lattices and supersingular isogenies in TLS, October 2019. https://www.imperialviolet.org/2019/10/30/pqsivssl.html
Lantz, B., Heller, B., Handigol, N., Jeyakumar, V., O’Connor, B., Burkard, C.: Mininet, November 2019. http://mininet.org/
Ludovici, F., Pfeifer, H.P.: NETEM(4), November 2011. http://man7.org/linux/man-pages/man8/tc-netem.8.html
Lyubashevsky, V., et al.: CRYSTALS-DILITHIUM. Technical report, National Institute of Standards and Technology (2019). https://csrc.nist.gov/projects/post-quantum-cryptography/round-2-submissions
Mozilla. Telemetry portal, February 2020. https://telemetry.mozilla.org/
Naehrig, M., et al.: FrodoKEM. Technical report, National Institute of Standards and Technology (2019). https://csrc.nist.gov/projects/post-quantum-cryptography/round-2-submissions
NGINX, Inc.: NGINX | High Performance Load Balancer, Web Server, & Reverse Proxy (2019). https://www.nginx.com/
Open Quantum Safe Project. Open Quantum Safe, November 2019. https://openquantumsafe.org/
Open Quantum Safe Project. OQS-OpenSSL\_1\_0\_2-stable, November 2019. https://github.com/open-quantum-safe/openssl/tree/OQS-OpenSSL_1_0_2-stable
Open Quantum Safe Project. OQS-OpenSSL\_1\_1\_1-stable, November 2019. https://github.com/open-quantum-safe/openssl/tree/OQS-OpenSSL_1_1_1-stable
Rescorla, E.: The Transport Layer Security (TLS) protocol version 1.3. RFC 8446, August 2018. https://rfc-editor.org/rfc/rfc8446.txt
Schanck, J.M., Stebila, D.: A Transport Layer Security (TLS) extension for establishing an additional shared secret. Internet-Draft draft-schanck-tls-additional-keyshare-00, Internet Engineering Task Force, April 2017. Work in Progress. https://datatracker.ietf.org/doc/html/draft-schanck-tls-additional-keyshare-00
Schanck, J.M., Whyte, W., Zhang, Z.: Quantum-safe hybrid (QSH) ciphersuite for Transport Layer Security (TLS) version 1.2. Internet-Draft draft-whyte-qsh-tls12-02, Internet Engineering Task Force, July 2016. Work in Progress.https://datatracker.ietf.org/doc/html/draft-whyte-qsh-tls12-02
Schwabe, P., et al.: CRYSTALS-KYBER. Technical report, National Institute of Standards and Technology (2019). https://csrc.nist.gov/projects/post-quantum-cryptography/round-2-submissions
Sikeridis, D., Kampanakis, P., Devetsikiotis, M.: Post-quantum authentication in TLS 1.3: a performance study. Cryptology ePrint Archive, Report 2020/071 (2020). https://eprint.iacr.org/2020/071
Stebila, D., Fluhrer, S., Gueron, S.: Design issues for hybrid key exchange in TLS 1.3. Internet-Draft draft-stebila-tls-hybrid-design-01, Internet Engineering Task Force, July 2019. Work in Progress. https://datatracker.ietf.org/doc/html/draft-stebila-tls-hybrid-design-01
Stebila, D., Mosca, M.: Post-quantum key exchange for the internet and the Open Quantum Safe project. In: Avanzi, R., Heys, H. (eds.) SAC 2016. LNCS, vol. 10532, pp. 14–37. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-69453-5_2
The Ethernet Alliance. Ethernet jumbo frames, November 2009. http://ethernetalliance.org/wp-content/uploads/2011/10/EA-Ethernet-Jumbo-Frames-v0-1.pdf
Unger, N., Goldberg, I.: Qatar University, and the Qatar Foundation for Education, Science and Community Development. Netmirage, November 2019. https://crysp.uwaterloo.ca/software/netmirage/
Whyte, W., Zhang, Z., Fluhrer, S., Garcia-Morchon, O.: Quantum-safe hybrid (QSH) key exchange for Transport Layer Security (TLS) version 1.3. Internet-Draft draft-whyte-qsh-tls13-06, Internet Engineering Task Force, October 2017. Work in Progress. https://datatracker.ietf.org/doc/html/draft-whyte-qsh-tls13-06
Zaverucha, G., et al.: Picnic. Technical report, National Institute of Standards and Technology (2019). https://csrc.nist.gov/projects/post-quantum-cryptography/round-2-submissions
Acknowledgements
We would like to thank Eric Crockett for helpful discussions in the early parts of this work. We are grateful to Geovandro C. C. F. Pereira, Justin Tracey, and Nik Unger for their help with the network emulation experiments. We also thank the anonymous reviewers for their helpful suggestions.
Contributors to the Open Quantum Safe project are listed on the project website [29]. The Open Quantum Safe project has received funding from Amazon Web Services and the Tutte Institute for Mathematics and Computing, and in-kind contributions of developer time from Amazon Web Services, Cisco Systems, evolutionQ, IBM Research, and Microsoft Research. The post-quantum algorithm implementations used in the experiments are directly or indirectly from the original NIST submission teams. Some implementations have been provided by the PQClean project [16].
D.S. is supported in part by Natural Sciences and Engineering Research Council (NSERC) of Canada Discovery grant RGPIN-2016-05146 and a NSERC Discovery Accelerator Supplement. Computation time on Azure was donated by Microsoft Research.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
A Additional Charts
A Additional Charts
Rights and permissions
Copyright information
© 2020 Springer Nature Switzerland AG
About this paper
Cite this paper
Paquin, C., Stebila, D., Tamvada, G. (2020). Benchmarking Post-quantum Cryptography in TLS. In: Ding, J., Tillich, JP. (eds) Post-Quantum Cryptography. PQCrypto 2020. Lecture Notes in Computer Science(), vol 12100. Springer, Cham. https://doi.org/10.1007/978-3-030-44223-1_5
Download citation
DOI: https://doi.org/10.1007/978-3-030-44223-1_5
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-44222-4
Online ISBN: 978-3-030-44223-1
eBook Packages: Computer ScienceComputer Science (R0)