Abstract
We develop two variants of Cocks’ identity-based encryption. One variant has faster encryption, where the most time-consuming part only requires several modular multiplications. The other variant makes the first variant anonymous under suitable complexity assumptions, while its decryption efficiency is about twice lower than the first one. Both the variants have ciphertext expansion twice more extensive than the original Cocks’ identity-based encryption. To alleviate the issue of the second variant’s large ciphertext expansion, we consider using it to construct a public-key encryption with keyword search scheme with a fast encryption algorithm by means of the transform in [1].
This is a preview of subscription content, log in via an institution.
Buying options
Tax calculation will be finalised at checkout
Purchases are for personal use only
Learn about institutional subscriptionsNotes
- 1.
\(M(\kappa )\) is the time to multiply \(\kappa \)-bit numbers.
- 2.
Perron considered the integer 0 as a quadratic residue. We should deal with it carefully.
References
Abdalla, M., et al.: Searchable encryption revisited: consistency properties, relation to anonymous IBE, and extensions. J. Cryptol. 21(3), 350–391 (2008). https://doi.org/10.1007/s00145-007-9006-6
Ateniese, G., Gasti, P.: Universally anonymous IBE based on the quadratic residuosity assumption. In: Fischlin, M. (ed.) CT-RSA 2009. LNCS, vol. 5473, pp. 32–47. Springer, Heidelberg (2009). https://doi.org/10.1007/978-3-642-00862-7_3
Bellare, M., Boldyreva, A., Desai, A., Pointcheval, D.: Key-privacy in public-key encryption. In: Boyd, C. (ed.) ASIACRYPT 2001. LNCS, vol. 2248, pp. 566–582. Springer, Heidelberg (2001). https://doi.org/10.1007/3-540-45682-1_33
Boneh, D., Di Crescenzo, G., Ostrovsky, R., Persiano, G.: Public key encryption with keyword search. In: Cachin, C., Camenisch, J.L. (eds.) EUROCRYPT 2004. LNCS, vol. 3027, pp. 506–522. Springer, Heidelberg (2004). https://doi.org/10.1007/978-3-540-24676-3_30
Boneh, D., Franklin, M.: Identity-based encryption from the Weil pairing. In: Kilian, J. (ed.) CRYPTO 2001. LNCS, vol. 2139, pp. 213–229. Springer, Heidelberg (2001). https://doi.org/10.1007/3-540-44647-8_13
Boneh, D., Gentry, C., Hamburg, M.: Space-efficient identity based encryption without pairings. In: 48th Annual IEEE Symposium on Foundations of Computer Science (FOCS 2007), pp. 647–657. IEEE (2007)
Boneh, D., LaVigne, R., Sabin, M.: Identity-based encryption with \(e^{th}\) residuosity and its incompressibility. In: Autumn 2013 TRUST Conference. Washington DC (Oct 9–10, 2013), poster presentation (2013)
Brent, R.P., Zimmermann, P.: An O(M(n) logn) algorithm for the Jacobi symbol. In: Hanrot, G., Morain, F., Thomé, E. (eds.) ANTS 2010. LNCS, vol. 6197, pp. 83–95. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-14518-6_10
Brent, R.P., Zimmermann, P.: Modern Computer Arithmetic, vol. 18. Cambridge University Press, Cambridge (2010)
Clear, M., Hughes, A., Tewari, H.: Homomorphic encryption with access policies: characterization and new constructions. In: Youssef, A., Nitaj, A., Hassanien, A.E. (eds.) AFRICACRYPT 2013. LNCS, vol. 7918, pp. 61–87. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-38553-7_4
Clear, M., McGoldrick, C.: Additively homomorphic IBE from higher residuosity. In: Lin, D., Sako, K. (eds.) PKC 2019. LNCS, vol. 11442, pp. 496–515. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-17253-4_17
Clear, M., Tewari, H., McGoldrick, C.: Anonymous IBE from quadratic residuosity with improved performance. In: Pointcheval, D., Vergnaud, D. (eds.) AFRICACRYPT 2014. LNCS, vol. 8469, pp. 377–397. Springer, Cham (2014). https://doi.org/10.1007/978-3-319-06734-6_23
Cocks, C.: An identity based encryption scheme based on quadratic residues. In: Honary, B. (ed.) Cryptography and Coding 2001. LNCS, vol. 2260, pp. 360–363. Springer, Heidelberg (2001). https://doi.org/10.1007/3-540-45325-3_32
Di Crescenzo, G., Saraswat, V.: Public key encryption with searchable keywords based on Jacobi symbols. In: Srinathan, K., Rangan, C.P., Yung, M. (eds.) INDOCRYPT 2007. LNCS, vol. 4859, pp. 282–296. Springer, Heidelberg (2007). https://doi.org/10.1007/978-3-540-77026-8_21
Gentry, C., Peikert, C., Vaikuntanathan, V.: Trapdoors for hard lattices and new cryptographic constructions. In: Dwork, C. (ed.) Proceedings of the 40th Annual ACM Symposium on Theory of Computing, 2008. pp. 197–206. ACM (2008). https://doi.org/10.1145/1374376.1374407
Goldwasser, S., Micali, S.: Probabilistic encryption. J. Comput. Syst. Sci. 28(2), 270–299 (1984)
Joye, M.: Identity-based cryptosystems and quadratic residuosity. In: Cheng, C.-M., Chung, K.-M., Persiano, G., Yang, B.-Y. (eds.) PKC 2016. LNCS, vol. 9614, pp. 225–254. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-49384-7_9
Perron, O.: Bemerkungen über die verteilung der quadratischen reste. Math. Z. 56(2), 122–130 (1952)
Shamir, A.: Identity-Based cryptosystems and signature schemes. In: Blakley, G.R., Chaum, D. (eds.) CRYPTO 1984. LNCS, vol. 196, pp. 47–53. Springer, Heidelberg (1985). https://doi.org/10.1007/3-540-39568-7_5
Tiplea, F.L., Iftene, S., Teseleanu, G., Nica, A.: On the distribution of quadratic residues and non-residues modulo composite integers and applications to cryptography. Appl. Math. Comput. 372 (2020). https://doi.org/10.1016/j.amc.2019.124993
Acknowledgements
This work was supported in part by the National Natural Science Foundation of China (Grant No.61632012 and 61672239), in part by the Peng Cheng Laboratory Project of Guangdong Province (Grant No. PCL2018KP004), and in part by the “Fundamental Research Funds for the Central Universities”.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
A A Public-Key Encryption with Keyword Search Scheme from Quadratic Residuosity
A A Public-Key Encryption with Keyword Search Scheme from Quadratic Residuosity
Boneh et al. introduced the notion of public-key encryption with keyword search (PEKS) and gave a proper security model and a construction methodology in [4]. PEKS is a form of “searchable encryption” that performs a keyword search on data encrypted using a public-key system. A promising application of PEKS is that of intelligent email routing. One may consider that mails come through a gateway which tests whether a keyword (e.g., “urgent”) exists in an email. Of course, any other information about the email can not be revealed. A PEKS scheme consists of four \(\mathsf {PPT}\) algorithms \(\mathsf {\left( KeyGen,PEKS,Trapdoor,Test\right) }\).
-
\(\mathsf {KeyGen}(1^\kappa )\) The key generation algorithm \(\mathsf {KeyGen}\) is a randomized algorithm that takes as input a security parameter \(1^\kappa \) and generates a public/private key pair \((\mathsf {pk},\mathsf {sk})\).
-
\(\mathsf {PEKS}(\mathsf {pk},W)\) Given a public key \(\mathsf {pk}\) and a keyword W, \(\mathsf {PEKS}\) returns a searchable ciphertext S for W.
-
\(\mathsf {Trapdoor}(\mathsf {sk},W)\) Given a private key \(\mathsf {sk}\) and a keyword W, the trapdoor algorithm \(\mathsf {Trapdoor}\) produces a trapdoor \(T_W\) for keyword W.
-
\(\mathsf {Test}(\mathsf {pk},S,T_W)\) Given a public key \(\mathsf {pk}\), a searchable ciphertext \(S \leftarrow \mathsf {PEKS}\left( \mathsf {pk},W'\right) \) and a trapdoor \(T_W \leftarrow \mathsf {Trapdoor}(\mathsf {sk},W)\), the test algorithm \(\mathsf {Test}\) returns a bit b with 1 meaning “accept” or “yes” and 0 meaning “reject” or “no”. It is required that \(b=1\) when \(W=W'\).
In [1], the authors presented a new transform called \(\mathsf {new\text {-}ibe\text {-}2\text {-}peks}\) that transforms any \(\mathsf {IND}\)-\(\mathsf {ID}\)-\(\mathsf {CPA}\)-secure and anonymous IBE scheme into a \(\mathsf {PEKS}\)-\(\mathsf {IND}\)-\(\mathsf {CPA}\)-secure and computationally consistent PEKS scheme. The resulting PEKS-encryption algorithm picks and encrypts a random message X and appends X to the ciphertext. We can naturally apply \(\mathsf {new\text {-}ibe\text {-}2\text {-}peks}\) to the scheme of Sect. 4 and obtain the following PEKS scheme from quadratic residuosity.
-
\(\mathsf {KeyGen}(1^\kappa )\) Given a security parameter \(\kappa \), \(\mathsf {KeyGen}\) defines a parameter k and generates two RSA primes p and q such that
 and their product \(N=pq\). \(\mathsf {KeyGen}\) also samples an element \(u {\mathop {\leftarrow }\limits ^{\textit{R}}}\mathbb {J}_N \setminus \mathbb {QR}_N\). The public key is \(\mathsf {pk} = \{N,k,u,\mathsf {H}\}\) where \(\mathsf {H}\) is a publicly available cryptographic hash function mapping an arbitrary binary string to \(\mathbb {J}_{N}\). The secret key is \(\mathsf {sk} = \{p,q\}\).
and their product \(N=pq\). \(\mathsf {KeyGen}\) also samples an element \(u {\mathop {\leftarrow }\limits ^{\textit{R}}}\mathbb {J}_N \setminus \mathbb {QR}_N\). The public key is \(\mathsf {pk} = \{N,k,u,\mathsf {H}\}\) where \(\mathsf {H}\) is a publicly available cryptographic hash function mapping an arbitrary binary string to \(\mathbb {J}_{N}\). The secret key is \(\mathsf {sk} = \{p,q\}\). -
\(\mathsf {PEKS}(\mathsf {pk},W)\) Given a public key \(\mathsf {pk}\) and a keyword W, \(\mathsf {PEKS}\) selects a k-bit message \(X=[x_{k-1},x_{k-2}, \ldots , x_0]\) (with \(x_i \in \left\{ 0, 1\right\} \)) and computes \(R=\mathsf {H}(W)\). For each \(i = 0,1, \ldots k-1\), it chooses at random two polynomials \(f_{i,1},f_{i,2}\) of degree 1 from \(\mathbb {Z}_N[x]\), and two bits \(\beta _{i,1},\,\beta _{i,2} {\mathop {\leftarrow }\limits ^{\textit{R}}}\left\{ 0, 1\right\} \). Set
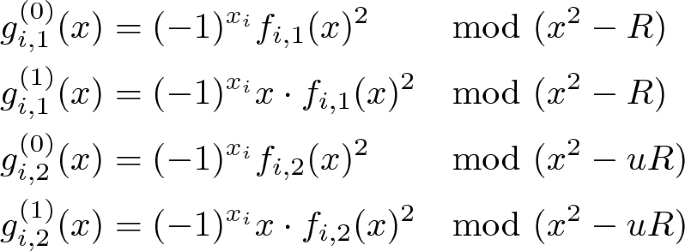
\(\mathsf {PEKS}\) returns the searchable ciphertext
$$ S=\left( g_{0,1}^{(\beta _{0,1})}(x),g_{0,2}^{(\beta _{0,2})}(x),g_{1,1}^{(\beta _{1,1})}(x),g_{1,2}^{(\beta _{1,2})}(x), \ldots , g_{k-1,1}^{(\beta _{k-1,1})}(x),g_{k-1,2}^{(\beta _{k-1,2})}(x) ,X\right) . $$ -
\(\mathsf {Trapdoor}(\mathsf {sk},W)\) Given a private key \(\mathsf {sk}\) and a keyword W, the trapdoor algorithm \(\mathsf {Trapdoor}\) computes \(R=\mathsf {H}(W)\). If \(R \in \mathbb {QR}_N\), it computes \(T_W = R^{1/2} \bmod N\); otherwise it computes \(T_W = \left( uR\right) ^{1/2} \bmod N\). \(\mathsf {Trapdoor}\) returns \(T_W\).
-
\(\mathsf {Test}(\mathsf {pk},S,T_W)\) Given a public key \(\mathsf {pk}\), a searchable ciphertext
$$\begin{aligned} S=\left( C_{0,1}(x), C_{0,2}(x), C_{1,1}(x), C_{1,2}(x), \ldots , C_{k-1,1}(x), C_{k-1,2}(x), X \right) \end{aligned}$$where \(C_{i,j}(x)=c_{i,j,0}+c_{i,j,1}x,\forall 0\le i <k,\forall 1\le j \le 2\), and a trapdoor \(T_W \leftarrow \mathsf {Trapdoor}(\mathsf {sk},W)\), the test algorithm \(\mathsf {Test}\) computes \(R=\mathsf {H}(W)\). If \(T_W^2 \equiv R \pmod {N}\), \(\mathsf {Test}\) computes \(\sigma _i=\left( \frac{c_{i,1,0}^2-c_{i,1,1}^2R}{N}\right) \) and sets \(h_i(x)=C_{i,1}(x),\forall 0\le i <k \); otherwise it computes \(\sigma _i=\left( \frac{c_{i,2,0}^2-c_{i,2,1}^2uR}{N}\right) \) and sets \(h_i(x)=C_{i,2}(x),\forall 0\le i <k \). Finally, \(\mathsf {Test}\) computes
$$\begin{aligned} x'_{i}&= {\left\{ \begin{array}{ll} \left( \frac{h_i(T_W)}{N}\right) , &{} \text{ if } \sigma _i=1; \\ \left( \frac{T_Wh_i(T_W)}{N}\right) , &{} \text{ otherwise }. \end{array}\right. } \end{aligned}$$and recovers \(X'=[\mathcal {J}_{N}(x'_{k-1}),\mathcal {J}_{N}(x'_{k-2}), \ldots , \mathcal {J}_{N}(x'_0)]\). \(\mathsf {Test}\) returns 1 if \(X=X'\); and 0 otherwise.
For encrypting a message m with n keywords \(W_1,W_2,\ldots , W_n\) with user’s public key \(\mathsf {upk}\), Boneh et al. in [4] suggested that the sender computes and sends the ciphertext
to a proxy given the trapdoor \(T_{W_i}\) for each keyword \(W_i\). Then the proxy can test whether m contains some keyword \(W_i\), but it learns nothing more about any other information about m.
Rights and permissions
Copyright information
© 2020 Springer Nature Switzerland AG
About this paper
Cite this paper
Zhao, X., Cao, Z., Dong, X., Zheng, J. (2020). Anonymous IBE from Quadratic Residuosity with Fast Encryption. In: Susilo, W., Deng, R.H., Guo, F., Li, Y., Intan, R. (eds) Information Security. ISC 2020. Lecture Notes in Computer Science(), vol 12472. Springer, Cham. https://doi.org/10.1007/978-3-030-62974-8_1
Download citation
DOI: https://doi.org/10.1007/978-3-030-62974-8_1
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-62973-1
Online ISBN: 978-3-030-62974-8
eBook Packages: Computer ScienceComputer Science (R0)


 and their product
and their product