Abstract
Oblivious transfer (OT) is a foundational primitive within cryptography owing to its connection with secure computation. One of the oldest constructions of oblivious transfer was from certified trapdoor permutations (TDPs). However several decades later, we do not know if a similar construction can be obtained from TDPs in general.
In this work, we study the problem of constructing round optimal oblivious transfer from trapdoor permutations. In particular, we obtain the following new results (in the plain model) relying on TDPs in a black-box manner:
– Three-round oblivious transfer protocol that guarantees indistinguishability-security against malicious senders (and semi-honest receivers).
– Four-round oblivious transfer protocol secure against malicious adversaries with black-box simulation-based security.
By combining our second result with an already known compiler we obtain the first round-optimal 2-party computation protocol that relies in a black-box way on TDPs.
A key technical tool underlying our results is a new primitive we call dual witness encryption (DWE) that may be of independent interest.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
A semi-honest adversary, unlike a malicious adversary, follows the protocol specification. However, it may still try to glean additional information from the execution of the protocol.
- 2.
Note that this is not an accurate description of the encryption scheme, but is helpful to provide an intuition.
- 3.
We note that in this example \(L_0\cup L_1= \{0,1\}^{\star }\), but this is not always the case, as we show hereafter.
- 4.
We provide privacy for the input of the receiver in the sense that a malicious sender cannot distinguishes between when the receiver is using the input 0 and when he is using the input 1.
- 5.
In this work we only refer to black-box simulation.
- 6.
In this model everyone can send messages at the same time.
- 7.
To not overburden the notation we use \(f_\alpha \) instead of
 as the evaluation algorithm hereafter in the paper.
as the evaluation algorithm hereafter in the paper. - 8.
We need to send two pairs of functions, but for now we omit this since it is a technical detail that will be helpful in the security proof.
- 9.
For convenience, we drop
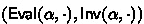 from the notation, and write \(f(\cdot )\), \(f^{-1}(\cdot )\) to denote algorithms
from the notation, and write \(f(\cdot )\), \(f^{-1}(\cdot )\) to denote algorithms  ,
,  respectively, when \(f_\alpha \) and \(\mathtt {td}\) are clear from the context. We also use the function \(f_\alpha \) instead of the index \(\alpha \) as input of the algorithm \(S\) and \(S_{DR}\).
respectively, when \(f_\alpha \) and \(\mathtt {td}\) are clear from the context. We also use the function \(f_\alpha \) instead of the index \(\alpha \) as input of the algorithm \(S\) and \(S_{DR}\). - 10.
We refer to Sect. 3.3 for a formal definition of \(\mathsf {REAL}_{\varPi _\mathcal {OT},R_\mathcal {OT}^\star (z)}\) and \(\mathsf {IDEAL}_{{F_\mathcal {OT}},\mathsf {Sim}(z)}\).
- 11.
To prove our theorem we do not need a fully secure combiner. That is, we only need a combiner that guarantees security in the case that one execution of \(\varPi _\mathcal {OT}\) is secure against malicious senders and all the executions of \(\varPi _\mathcal {OT}\) are secure against malicious receivers.
References
Bellare, M., Yung, M.: Certifying cryptographic tools: the case of trapdoor permutations. In: Brickell, E.F. (ed.) CRYPTO 1992. LNCS, vol. 740, pp. 442–460. Springer, Heidelberg (1993). https://doi.org/10.1007/3-540-48071-4_31
Ben-Or, M., Goldwasser, S., Wigderson, A.: Completeness theorems for non-cryptographic fault-tolerant distributed computation (extended abstract). In: 20th ACM STOC, pp. 1–10. ACM Press, May 1988. https://doi.org/10.1145/62212.62213
Benhamouda, F., Lin, H.: k-round multiparty computation from k-round oblivious transfer via garbled interactive circuits. In: Nielsen, J.B., Rijmen, V. (eds.) EUROCRYPT 2018, Part II. LNCS, vol. 10821, pp. 500–532. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-78375-8_17
Brassard, G., Crépeau, C., Santha, M.: Oblivious transfers and intersecting codes. IEEE Trans. Inf. Theory 42(6), 1769–1780 (1996). https://doi.org/10.1109/18.556673
Canetti, R., et al.: Fiat-Shamir: from practice to theory. In: Charikar, M., Cohen, E. (eds.) 51st ACM STOC, pp. 1082–1090. ACM Press, June 2019. https://doi.org/10.1145/3313276.3316380
Canetti, R., Lichtenberg, A.: Certifying trapdoor permutations, revisited. In: Beimel, A., Dziembowski, S. (eds.) TCC 2018, Part I. LNCS, vol. 11239, pp. 476–506. Springer, Cham (2018). https://doi.org/10.1007/978-3-030-03807-6_18
Chailloux, A., Ciocan, D.F., Kerenidis, I., Vadhan, S.: Interactive and noninteractive zero knowledge are equivalent in the help model. In: Canetti, R. (ed.) TCC 2008. LNCS, vol. 4948, pp. 501–534. Springer, Heidelberg (2008). https://doi.org/10.1007/978-3-540-78524-8_28
Chaum, D., Crépeau, C., Damgård, I.: Multiparty unconditionally secure protocols (extended abstract). In: 20th ACM STOC, pp. 11–19. ACM Press, May 1988. https://doi.org/10.1145/62212.62214
Rai Choudhuri, A., Ciampi, M., Goyal, V., Jain, A., Ostrovsky, R.: Round optimal secure multiparty computation from minimal assumptions. In: Pass, R., Pietrzak, K. (eds.) TCC 2020, Part II. LNCS, vol. 12551, pp. 291–319. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-64378-2_11
Ciampi, M., Ostrovsky, R., Siniscalchi, L., Visconti, I.: Round-optimal secure two-party computation from trapdoor permutations. In: Kalai, Y., Reyzin, L. (eds.) TCC 2017, Part I. LNCS, vol. 10677, pp. 678–710. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-70500-2_23
Ciampi, M., Parisella, R., Venturi, D.: On adaptive security of delayed-input sigma protocols and Fiat-Shamir NIZKs. In: Galdi, C., Kolesnikov, V. (eds.) SCN 2020. LNCS, vol. 12238, pp. 670–690. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-57990-6_33
Damgård, I., Nielsen, J.B., Polychroniadou, A., Raskin, M.: On the communication required for unconditionally secure multiplication. In: Robshaw, M., Katz, J. (eds.) CRYPTO 2016, Part II. LNCS, vol. 9815, pp. 459–488. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-53008-5_16
Even, S., Goldreich, O., Lempel, A.: A randomized protocol for signing contracts. In: Chaum, D., Rivest, R.L., Sherman, A.T. (eds.) CRYPTO 1982, pp. 205–210. Plenum Press, New York (1982)
Feige, U., Lapidot, D., Shamir, A.: Multiple non-interactive zero knowledge proofs based on a single random string (extended abstract). In: 31st FOCS. pp. 308–317. IEEE Computer Society Press, October 1990. https://doi.org/10.1109/FSCS.1990.89549
Friolo, D., Masny, D., Venturi, D.: A black-box construction of fully-simulatable, round-optimal oblivious transfer from strongly uniform key agreement. In: Hofheinz, D., Rosen, A. (eds.) TCC 2019. LNCS, vol. 11891, pp. 111–130. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-36030-6_5https://eprint.iacr.org/2018/473
Garg, S., Mukherjee, P., Pandey, O., Polychroniadou, A.: The exact round complexity of secure computation. In: Fischlin, M., Coron, J.-S. (eds.) EUROCRYPT 2016, Part II. LNCS, vol. 9666, pp. 448–476. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-49896-5_16
Garg, S., Ostrovsky, R., Visconti, I., Wadia, A.: Resettable statistical zero knowledge. In: Cramer, R. (ed.) TCC 2012. LNCS, vol. 7194, pp. 494–511. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-28914-9_28
Goldberg, S., Reyzin, L., Sagga, O., Baldimtsi, F.: Efficient noninteractive certification of RSA moduli and beyond. In: Galbraith, S.D., Moriai, S. (eds.) ASIACRYPT 2019, Part III. LNCS, vol. 11923, pp. 700–727. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-34618-8_24
Goldreich, O.: Foundations of Cryptography: Basic Applications, vol. 2. Cambridge University Press, Cambridge (2004)
Goldreich, O.: Computational complexity: a conceptual perspective. SIGACT News 39(3), 35–39 (2008). https://doi.org/10.1145/1412700.1412710
Goldreich, O.: Basing non-interactive zero-knowledge on (enhanced) trapdoor permutations: the state of the art (2011)
Goldreich, O., Oren, Y.: Definitions and properties of zero-knowledge proof systems. J. Cryptol. 7(1), 1–32 (1994). https://doi.org/10.1007/BF00195207
Goldreich, O., Rothblum, R.D.: Enhancements of trapdoor permutations. J. Cryptol. 26(3), 484–512 (2013). https://doi.org/10.1007/s00145-012-9131-8
Goldwasser, S., Micali, S., Rackoff, C.: The knowledge complexity of interactive proof-systems (extended abstract). In: 17th ACM STOC, pp. 291–304. ACM Press, May 1985. https://doi.org/10.1145/22145.22178
Goldwasser, S., Micali, S., Rackoff, C.: The knowledge complexity of interactive proof systems. SIAM J. Comput. 18(1), 186–208 (1989). https://doi.org/10.1137/0218012
Haitner, I.: Implementing oblivious transfer using collection of dense trapdoor permutations. In: Naor, M. (ed.) TCC 2004. LNCS, vol. 2951, pp. 394–409. Springer, Heidelberg (2004). https://doi.org/10.1007/978-3-540-24638-1_22
Harnik, D., Kilian, J., Naor, M., Reingold, O., Rosen, A.: On robust combiners for oblivious transfer and other primitives. In: Cramer, R. (ed.) EUROCRYPT 2005. LNCS, vol. 3494, pp. 96–113. Springer, Heidelberg (2005). https://doi.org/10.1007/11426639_6
Ishai, Y., Kushilevitz, E., Ostrovsky, R., Prabhakaran, M., Sahai, A.: Efficient non-interactive secure computation. In: Paterson, K.G. (ed.) EUROCRYPT 2011. LNCS, vol. 6632, pp. 406–425. Springer, Heidelberg (2011). https://doi.org/10.1007/978-3-642-20465-4_23
Kakvi, S.A., Kiltz, E., May, A.: Certifying RSA. In: Wang, X., Sako, K. (eds.) ASIACRYPT 2012. LNCS, vol. 7658, pp. 404–414. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-34961-4_25
Katz, J., Ostrovsky, R.: Round-optimal secure two-party computation. In: Franklin, M. (ed.) CRYPTO 2004. LNCS, vol. 3152, pp. 335–354. Springer, Heidelberg (2004). https://doi.org/10.1007/978-3-540-28628-8_21
Kilian, J.: Founding cryptography on oblivious transfer. In: 20th ACM STOC, pp. 20–31. ACM Press, May 1988. https://doi.org/10.1145/62212.62215
Kilian, J.: A note on efficient zero-knowledge proofs and arguments (extended abstract). In: 24th ACM STOC, pp. 723–732. ACM Press, May 1992. https://doi.org/10.1145/129712.129782
Lindell, Y.: Parallel coin-tossing and constant-round secure two-party computation. In: Kilian, J. (ed.) CRYPTO 2001. LNCS, vol. 2139, pp. 171–189. Springer, Heidelberg (2001). https://doi.org/10.1007/3-540-44647-8_10
Naor, M., Pinkas, B.: Efficient oblivious transfer protocols. In: Kosaraju, S.R. (ed.) 12th SODA, pp. 448–457. ACM-SIAM, January 2001
Ostrovsky, R., Richelson, S., Scafuro, A.: Round-optimal black-box two-party computation. In: Gennaro, R., Robshaw, M. (eds.) CRYPTO 2015, Part II. LNCS, vol. 9216, pp. 339–358. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-48000-7_17
Ostrovsky, R., Venkatesan, R., Yung, M.: Fair games against an all-powerful adversary. In: Cai, J. (ed.) Advances in Computational Complexity Theory, Proceedings of a DIMACS Workshop, New Jersey, USA, 3–7 December 1990. DIMACS Series in Discrete Mathematics and Theoretical Computer Science, vol. 13, pp. 155–169. DIMACS/AMS (1990). https://doi.org/10.1090/dimacs/013/09
Peikert, C., Vaikuntanathan, V., Waters, B.: A framework for efficient and composable oblivious transfer. In: Wagner, D. (ed.) CRYPTO 2008. LNCS, vol. 5157, pp. 554–571. Springer, Heidelberg (2008). https://doi.org/10.1007/978-3-540-85174-5_31
Rabin, M.O.: Digital signatures and public key functions as intractable as factorization. Technical report MIT/LCS/TR-212, Massachusetts Institute of Technology, January 1979
Rothblum, R.: A taxonomy of enhanced trapdoor permutations. Electron. Colloq. Comput. Complex. (ECCC) 17, 145 (2010). http://eccc.hpi-web.de/report/2010/145
Yao, A.C.C.: Protocols for secure computations (extended abstract). In: 23rd FOCS, pp. 160–164. IEEE Computer Society Press, November 1982. https://doi.org/10.1109/SFCS.1982.38
Yao, A.C.C.: How to generate and exchange secrets (extended abstract). In: 27th FOCS, pp. 162–167. IEEE Computer Society Press, October 1986. https://doi.org/10.1109/SFCS.1986.25
Acknowledgments
Arka Rai Choudhuri is supported by NSF CNS-1814919, NSF CAREER 1942789, Johns Hopkins University Catalyst award, NSF CNS-1908181, Office of Naval Research N00014-19-1-2294.
Michele Ciampi has done part of this work while consulting for Stealth Software Technologies, Inc.
Vipul Goyal is supported in part by the NSF award 1916939, DARPA SIEVE program, a gift from Ripple, a DoE NETL award, a JP Morgan Faculty Fellowship, a PNC center for financial services innovation award, and a Cylab seed funding award.
Abhishek Jain is supported in part by an NSF CNS grant 1814919, NSF CAREER award 1942789, Johns Hopkins University Catalyst award and Office of Naval Research grant N00014-19-1-2294.
Rafail Ostrovsky is supported in part by DARPA under Cooperative Agreement HR0011-20-2-0025, NSF grant CNS-2001096, US-Israel BSF grant 2015782, Google Faculty Award, JP Morgan Faculty Award, IBM Faculty Research Award, Xerox Faculty Research Award, OKAWA Foundation Research Award, B. John Garrick Foundation Award, Teradata Research Award, Lockheed-Martin Research Award and Sunday Group. The views and conclusions contained herein are those of the authors and should not be interpreted as necessarily representing the official policies, either expressed or implied, of DARPA, the Department of Defense, or the U.S. Government. The U.S. Government is authorized to reproduce and distribute reprints for governmental purposes not withstanding any copyright annotation therein.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 International Association for Cryptologic Research
About this paper
Cite this paper
Choudhuri, A.R., Ciampi, M., Goyal, V., Jain, A., Ostrovsky, R. (2021). Oblivious Transfer from Trapdoor Permutations in Minimal Rounds. In: Nissim, K., Waters, B. (eds) Theory of Cryptography. TCC 2021. Lecture Notes in Computer Science(), vol 13043. Springer, Cham. https://doi.org/10.1007/978-3-030-90453-1_18
Download citation
DOI: https://doi.org/10.1007/978-3-030-90453-1_18
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-90452-4
Online ISBN: 978-3-030-90453-1
eBook Packages: Computer ScienceComputer Science (R0)


 as the evaluation algorithm hereafter in the paper.
as the evaluation algorithm hereafter in the paper.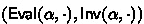 from the notation, and write
from the notation, and write  ,
,  respectively, when
respectively, when 