Abstract
A quantum bit commitment scheme is to realize bit (rather than qubit) commitment by exploiting quantum communication and quantum computation. In this work, we study the binding property of the quantum string commitment scheme obtained by composing a generic quantum perfectly(resp. statistically)-hiding computationally-binding bit commitment scheme (which can be realized based on quantum-secure one-way permutations(resp. functions)) in parallel. We show that the resulting scheme satisfies a stronger quantum computational binding property, which we will call predicate-binding, than the trivial honest-binding. Intuitively and very roughly, the predicate-binding property guarantees that given any inconsistent predicate pair over a set of strings (i.e. no strings in this set can satisfy both predicates), if a (claimed) quantum commitment can be opened so that the revealed string satisfies one predicate with certainty, then the same commitment cannot be opened so that the revealed string satisfies the other predicate (except for a negligible probability).
As an application, we plug a generic quantum perfectly(resp. statistically)-hiding computationally-binding bit commitment scheme in Blum’s zero-knowledge protocol for the NP-complete language Hamiltonian Cycle. This will give rise to the first quantum perfect(resp. statistical) zero-knowledge argument system (with soundness error 1/2) for all NP languages based solely on quantum-secure one-way permutations(resp. functions). The quantum computational soundness of this system will follow immediately from the quantum computational predicate-binding property of commitments.
The full version of this paper is referred to [35].
This is a preview of subscription content, log in via an institution.
Buying options
Tax calculation will be finalised at checkout
Purchases are for personal use only
Learn about institutional subscriptionsNotes
- 1.
Actually, it is shown in [34] a much stronger result that any quantum bit commitment schemes just secure against the purification attack can be converted into a non-interactive one of the generic form. For this reason, in this paper we can focus on this generic form without loss of generality. At a very high level, the basis idea of how such a quantum round-collapse is possible is similar to the old idea of converting any non-interactive quantum bit commitment scheme into the generic form [15, 36].
- 2.
The round complexity of any cryptographic task might be one of the most important parameters.
- 3.
We do not claim that this holds w.r.t. a general quantum bit commitment. But any quantum bit commitment scheme can be converted to the generic form [34], as aforementioned.
- 4.
All mentioned above about the strictness of the quantum binding will become clear once one reads Definition 2, which is quite simple and intuitive.
- 5.
- 6.
Generally, the revealed value of a quantum string commitment could be a probability distribution over this set of strings.
- 7.
We note that the parallel composition of classical bit commitments secure against classical attacks gives a string commitment that is trivially predicate-binding secure against classical attacks. This is simply because the resulting string commitment (by the parallel composition) is bound to a unique classical string.
- 8.
As communicated by the authors of [12] recently [13], the definition of Q-binding in the conference version of [12] has a flaw: it misses an additional information z as another input of the predicate Q to make it efficiently computable, and the sentence “We do not require Q to be efficiently computable" there should be removed.
- 9.
Namely, the third assumption in [12, section “A General Framework"].
- 10.
This can be seen from the extractability of their commitments.
- 11.
It appears that even the reveal stage of the commitment scheme given in [19] also needs polynomial rounds of the interaction.
- 12.
For the moment, we drop the security parameter to simplify the notation.
- 13.
The formal definitions of a generic quantum bit commitment scheme and its computational binding propery are referred to Definition 2. Here for simplification, we neglect the auxiliary input state that the cheating sender may receive.
- 14.
For the moment, we can think of them as efficiently computable predicates in the common sense for simplicity.
- 15.
The tensor product m in superscripts indicates that there are m copies of the corresponding quantum register.
- 16.
The number of qubits in the state
 that are needed depends on the quantum circuit \(Q_0 (n)\) (or \(Q_1 (n)\)).
that are needed depends on the quantum circuit \(Q_0 (n)\) (or \(Q_1 (n)\)). - 17.
Informally speaking, this is a kind of security that turns out to be just slightly stronger than the semi-honest security yet much weaker than the full security.
- 18.
For example, consider a running of Blum’s zero-knowledge protocol for the language Hamiltonian Cycle in which the cheating prover responds to the challenge 1 of the verifier.
- 19.
Sometimes, it will be more covenient to identify the function \(\mathsf {val}(\cdot )\) as an algorithm that decides the validity of a candidate witness.
- 20.
We point out that a string in \(P_1\) may have multiple witnesses.
- 21.
Here, our purpose of introducing \(\alpha _s\) and
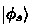 for \(s \not \in P_1\) is mainly for a cleaner way of writing the proof; it will not affect the places in the subsequent proof where the quantum computational binding property is applied.
for \(s \not \in P_1\) is mainly for a cleaner way of writing the proof; it will not affect the places in the subsequent proof where the quantum computational binding property is applied. - 22.
We highlight that in the literature we cite, various quantum zero-knowledge properties are based on different hiding properties of (classical or quantum) commitments (secure against quantum attacks) than the one considered in this work. However, their proofs extend to our setting straightforwardly, especially the proof of quantum zero-knowledge in [36].
- 23.
References
Adcock, M., Cleve, R.: A quantum Goldreich-Levin theorem with cryptographic applications. In: Alt, H., Ferreira, A. (eds.) STACS 2002. LNCS, vol. 2285, pp. 323–334. Springer, Heidelberg (2002). https://doi.org/10.1007/3-540-45841-7_26
Ambainis, A., Rosmanis, A., Unruh, D.: Quantum attacks on classical proof systems: the hardness of quantum rewinding. In: FOCS, pp. 474–483 (2014)
Bartusek, J., Coladangelo, A., Khurana, D., Ma, F.: One-way functions imply secure computation in a quantum world. In: Malkin, T., Peikert, C. (eds.) CRYPTO 2021. LNCS, vol. 12825, pp. 467–496. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-84242-0_17
Bennett, C.H., Brassard, G.: Quantum cryptography: Public key distribution and coin tossing. In: Proceedings of IEEE International Conference on Computers, Systems and Signal Processing, vol. 175 (1984)
Blum, M.: How to prove a theorem so no one else can claim it. In: Proceedings of the International Congress of Mathematicians, vol. 1, p. 2 (1986)
Boneh, D., Dagdelen, Ö., Fischlin, M., Lehmann, A., Schaffner, C., Zhandry, M.: Random oracles in a quantum world. In: Lee, D.H., Wang, X. (eds.) ASIACRYPT 2011. LNCS, vol. 7073, pp. 41–69. Springer, Heidelberg (2011). https://doi.org/10.1007/978-3-642-25385-0_3
Brassard, G., Crépeau, C.: Quantum bit commitment and coin tossing protocols. In: Menezes, A.J., Vanstone, S.A. (eds.) CRYPTO 1990. LNCS, vol. 537, pp. 49–61. Springer, Heidelberg (1991). https://doi.org/10.1007/3-540-38424-3_4
Chailloux, A., Kerenidis, I., Rosgen, B.: Quantum commitments from complexity assumptions. In: ICALP, no. 1, pp. 73–85 (2011)
Chia, N., Chung, K., Liu, Q., Yamakawa, T.: On the impossibility of post-quantum black-box zero-knowledge in constant rounds (2021). CoRR abs/2103.11244, https://arxiv.org/abs/2103.11244
Crépeau, C., Dumais, P., Mayers, D., Salvail, L.: Computational collapse of quantum state with application to oblivious transfer. In: Naor, M. (ed.) TCC 2004. LNCS, vol. 2951, pp. 374–393. Springer, Heidelberg (2004). https://doi.org/10.1007/978-3-540-24638-1_21
Crépeau, C., Légaré, F., Salvail, L.: How to convert the flavor of a quantum bit commitment. In: Pfitzmann, B. (ed.) EUROCRYPT 2001. LNCS, vol. 2045, pp. 60–77. Springer, Heidelberg (2001). https://doi.org/10.1007/3-540-44987-6_5
Damgård, I., Fehr, S., Salvail, L.: Zero-knowledge proofs and string commitments withstanding quantum attacks. In: Franklin, M. (ed.) CRYPTO 2004. LNCS, vol. 3152, pp. 254–272. Springer, Heidelberg (2004). https://doi.org/10.1007/978-3-540-28628-8_16
Damgård, I., Fehr, S., Salvail, L.: Private communication (2021)
Dumais, P., Mayers, D., Salvail, L.: Perfectly concealing quantum bit commitment from any quantum one-way permutation. In: Preneel, B. (ed.) EUROCRYPT 2000. LNCS, vol. 1807, pp. 300–315. Springer, Heidelberg (2000). https://doi.org/10.1007/3-540-45539-6_21
Fang, J., Unruh, D., Yan, J., Zhou, D.: How to base security on the perfect/statistical binding property of quantum bit commitment? (2020). https://eprint.iacr.org/2020/621
Goldreich, O.: Foundations of Cryptography, Basic Tools, vol. I. Cambridge University Press, Cambridge (2001)
Goldreich, O., Micali, S., Wigderson, A.: Proofs that yield nothing but their validity or all languages in NP have zero-knowledge proof systems. J. ACM 38(3), 691–729 (1991)
van de Graaf, J.: Towards a formal definition of security for quantum protocols. PhD thesis, Université de Montréal (1997)
Grilo, A.B., Lin, H., Song, F., Vaikuntanathan, V.: Oblivious transfer is in MiniQCrypt. In: Canteaut, A., Standaert, F.-X. (eds.) EUROCRYPT 2021. LNCS, vol. 12697, pp. 531–561. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-77886-6_18
Haitner, I., Hoch, J.J., Reingold, O., Segev, G.: Finding collisions in interactive protocols - a tight lower bound on the round complexity of statistically-hiding commitments. In: FOCS, pp. 669–679 (2007)
Haitner, I., Nguyen, M.H., Ong, S.J., Reingold, O., Vadhan, S.P.: Statistically hiding commitments and statistical zero-knowledge arguments from any one-way function. SIAM J. Comput. 39(3), 1153–1218 (2009)
Jain, R., Kolla, A., Midrijanis, G., Reichardt, B.W.: On parallel composition of zero-knowledge proofs with black-box quantum simulators. Quant. Inf. Comput. 9(5), 513–532 (2009)
Koshiba, T., Odaira, T.: Statistically-hiding quantum bit commitment from approximable-preimage-size quantum one-way function. In: Childs, A., Mosca, M. (eds.) TQC 2009. LNCS, vol. 5906, pp. 33–46. Springer, Heidelberg (2009). https://doi.org/10.1007/978-3-642-10698-9_4
Koshiba, T., Odaira, T.: Non-interactive statistically-hiding quantum bit commitment from any quantum one-way function (2011). arXiv:1102.3441
Lo, H.K., Chau, H.F.: Why quantum bit commitment and ideal quantum coin tossing are impossible. Physica D Nonlinear Phenom. 120(1), 177–187 (1998)
Mahmoody, M., Pass, R.: The curious case of non-interactive commitments – on the power of black-box vs. non-black-box use of primitives. In: Safavi-Naini, R., Canetti, R. (eds.) CRYPTO 2012. LNCS, vol. 7417, pp. 701–718. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-32009-5_41
Mayers, D.: Unconditionally secure quantum bit commitment is impossible. Phys. Rev. Lett. 78(17), 3414–3417 (1997)
Naor, M., Ostrovsky, R., Venkatesan, R., Yung, M.: Perfect zero-knowledge arguments for NP using any one-way permutation. J. Cryptol. 11(2), 87–108 (1998)
Nielsen, M.A., Chuang, I.L.: Quantum Computation and Quantum Informatioin. Cambridge University Press, Cambridge (2000)
Unruh, D.: Quantum proofs of knowledge. In: Pointcheval, D., Johansson, T. (eds.) EUROCRYPT 2012. LNCS, vol. 7237, pp. 135–152. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-29011-4_10
Unruh, D.: Collapse-binding quantum commitments without random oracles. In: Cheon, J.H., Takagi, T. (eds.) ASIACRYPT 2016. LNCS, vol. 10032, pp. 166–195. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-53890-6_6
Unruh, D.: Computationally binding quantum commitments. In: Fischlin, M., Coron, J.-S. (eds.) EUROCRYPT 2016. LNCS, vol. 9666, pp. 497–527. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-49896-5_18
Watrous, J.: Zero-knowledge against quantum attacks. SIAM J. Comput. 39(1), 25–58 (2009)
Yan, J.: General properties of quantum bit commitments (2020). https://eprint.iacr.org/2020/1488
Yan, J.: Quantum computationally predicate-binding commitment with application in quantum zero-knowledge argument for np. Cryptology ePrint Archive, Report 2020/1510 (2020). https://eprint.iacr.org/2020/1510
Yan, J., Weng, J., Lin, D., Quan, Y.: Quantum bit commitment with application in quantum zero-knowledge proof (extended abstract). In: Elbassioni, K., Makino, K. (eds.) ISAAC 2015. LNCS, vol. 9472, pp. 555–565. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-48971-0_47
Yao, A.C.C.: Quantum circuit complexity. In: FOCS, pp. 352–361 (1993)
Acknowledgements
We thank Dominique Unruh for helpful and inspiring discussions on the strictness of the quantum binding property and the possibility of basing quantum zero-knowledge argument for NP on computationally-binding quantum bit commitments at an early stage of this work. We are also grateful to the anonymous referees of Crypto 2021, QCrypt 2021, and Asiacrypt 2021 for their corrections and useful suggestions for the presentation of this paper.
This work was supported by the National Natural Science Foundation of China (Grant No. 61602208, No. 61932019, No. 61772521, No. 62171202, No. 61771222, and No. 61772522), by the PhD Start-up Fund of Natural Science Foundation of Guangdong Province, China (Grant No. 2014A030310333), by the Key Research Program of Frontier Sciences, CAS (Grant No. QYZDB-SSW-SYS035), and by the Open Project Program of the State Key Laboratory of Information Security, IIE, CAS (Grant No. 2015-MS-08).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 International Association for Cryptologic Research
About this paper
Cite this paper
Yan, J. (2021). Quantum Computationally Predicate-Binding Commitments with Application in Quantum Zero-Knowledge Arguments for NP. In: Tibouchi, M., Wang, H. (eds) Advances in Cryptology – ASIACRYPT 2021. ASIACRYPT 2021. Lecture Notes in Computer Science(), vol 13090. Springer, Cham. https://doi.org/10.1007/978-3-030-92062-3_20
Download citation
DOI: https://doi.org/10.1007/978-3-030-92062-3_20
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-92061-6
Online ISBN: 978-3-030-92062-3
eBook Packages: Computer ScienceComputer Science (R0)


 that are needed depends on the quantum circuit
that are needed depends on the quantum circuit 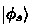 for
for 