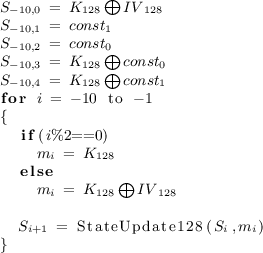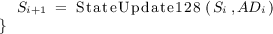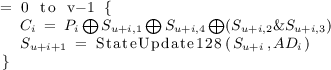Abstract
Security of transaction is of paramount importance in modern world of ubiquitous computing and data movement. To provide a framework of standard authenticated encryption techniques, CAESAR contest has been announced recently. Multiple entries in this contest are based on AES, which has been also, a popular choice as a primitive for authenticated encryption in the past. In this paper, we perform in-depth study of efficient hardware implementation for AES-based AEGIS-128 authenticated encryption, a prominent entry in the CAESAR contest. Through a complete study of possible throughput-area improvement techniques, we report multiple design points ranging from a high throughput of \(121.07\) Gbps design to a low-area implementation of \(18.72\) KGE, using commercial synthesis flows and 65 nm ASIC technology. We believe our results will serve as important design metric for the CAESAR contest as well as for efficient AEGIS-128 deployment.
This is a preview of subscription content, log in via an institution.
Buying options
Tax calculation will be finalised at checkout
Purchases are for personal use only
Learn about institutional subscriptionsNotes
- 1.
We are happy to share the RTL implementation to inquisitive researchers for this purpose.
References
Announcing the ADVANCED ENCRYPTION STANDARD (AES). Federal Information Processing Standards Publication 197. United States National Institute of Standards and Technology (NIST). 26 November 2001
Bogdanov, A., Lauridsen, M.M., Tischhauser, E.: AES-Based Authenticated Encryption Modes in Parallel High-Performance Software. https://eprint.iacr.org/2014/186.pdf. Accessed on 27 July 2014
Bogdanov, A., Mendel, F., Regazzoni, F., Rijmen, V., Tischhauser, E.: ALE: AES-based lightweight authenticated encryption. In: Moriai, S. (ed.) FSE 2013. LNCS, vol. 8424, pp. 447–466. Springer, Heidelberg (2014)
CAESAR Submissions. http://competitions.cr.yp.to/caesar.html
Canright, D., Batina, L.: A very compact “perfectly masked” S-Box for AES. In: Bellovin, S.M., Gennaro, R., Keromytis, A.D., Yung, M. (eds.) ACNS 2008. LNCS, vol. 5037, pp. 446–459. Springer, Heidelberg (2008)
Chattopadhyay, A., Meyr, H., Leupers, R.: LISA: a uniform ADL for embedded processor modelling, implementation and software toolsuite generation. In: Mishra, P., Dutt, N. (eds.) Processor Description Languages, pp. 95–130. Morgan Kaufmann, Boston (2008)
Grosso, V., Leurent, G., Standaert, F., Varici, K., Durvaux, F., Gaspar, L., Kerckhof, S.: SCREAM & iSCREAM Side-Channel Resistant Authenticated Encryption with Masking. http://competitions.cr.yp.to/round1/screamv1.pdf. Accessed on 12 July 2014
Khalid, A., Hassan, M., Chattopadhyay, A., Paul, G.: RAPID-FeinSPN: a rapid prototyping framework for feistel and SPN-based block ciphers. In: Bagchi, A., Ray, I. (eds.) ICISS 2013. LNCS, vol. 8303, pp. 169–190. Springer, Heidelberg (2013). doi:10.1007/978-3-642-45204-8 13
Kim, H., Kim, K.: Who can survive in CAESAR competition at round-zero? In: The 31th Symposium on Cryptography and Information Security Kagoshima, Japan, 21–24 January 2014
Moradi, A., Poschmann, A., Ling, S., Paar, C., Wang, H.: Pushing the limits: a very compact and a threshold implementation of AES. In: Paterson, K.G. (ed.) EUROCRYPT 2011. LNCS, vol. 6632, pp. 69–88. Springer, Heidelberg (2011)
Morawiecki, P., Gaj, K., Homsirikamol, E., Matusiewicz, K., Pieprzyk, J., Rogawski, M., Srebrny, M., Wojcik, M.: ICEPOLE v1. http://competitions.cr.yp.to/round1/icepolev1.pdf. Accessed on 12 July 2014
Mozaffari-Kermani, M., Reyhani-Masoleh, A.: Efficient and high-performance parallel hardware architectures for the AES-GCM. IEEE Trans. Comput. 61(8), 1165–1178 (2012)
Nguyen, D.K., Lanante, L., Ochi, H.: High throughput resource saving hardware implementation of AES-CCM for robust security network. J. Autom. Control Eng. 1(3), 250–254 (2013)
Paul, G., Chattopadhyay, A.: Designing stream ciphers with scalable data-widths: a case study with HC-128. Springer J. Crypt. Eng. 4(2), 135–143 (2014). doi:10.1007/s13389-014-0071-0
Sasaki, Y., Todo, Y., Aoki, K., Naito, Y., Sugawara, T., Murakami, Y., Matsui, M., Hirose, S.: Minalpher v1. http://competitions.cr.yp.to/round1/minalpherv1.pdf. Accessed on 12 July 2014
Sen Gupta, S., Chattopadhyay, A., Khalid, A.: Designing integrated accelerator for stream ciphers with structural similarities. Crypt. Commun. Discrete Struct. Boolean Funct. Sequences 5(1), 19–47 (2013). doi:10.1007/s12095-012-0074-6
Sen Gupta, S., Chattopadhyay, A., Sinha, K., Maitra, S., Sinha, B.P.: High performance hardware implementation for RC4 stream cipher. IEEE Trans. Comput. 62(4), 730–743 (2012)
Synopsys Processor Designer. http://www.synopsys.com/systems/blockdesign/processordev/pages/default.aspx
Wu, H., Preneel, B.: AEGIS: a fast authenticated encryption algorithm. In: Lange, T., Lauter, K., Lisoněk, P. (eds.) SAC 2013. LNCS, vol. 8282, pp. 185–202. Springer, Heidelberg (2014)
Wu, S., Wu, H., Huang, T., Wang, M., Wu, W.: Leaked-state-forgery attack against the authenticated encryption algorithm ALE. In: Sako, K., Sarkar, P. (eds.) ASIACRYPT 2013, Part I. LNCS, vol. 8269, pp. 377–404. Springer, Heidelberg (2013)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
A AEGIS-128
A AEGIS-128
We briefly describe the AEGIS-128 algorithm [19]. AEGIS-128 uses a 128-bit key and 128-bit initialization vector to encrypt and authenticate a message. The associated data length and plain text length are less than \(2^{64}\) bits. The authentication tag length is less than or equal to 128-bits. The use of 128-bit tag length is strongly recommended.
The state update function StateUpdate128 of AEGIS-128 updates a 80-byte state \(S_i\) using a 16-byte message block \(m_i\). StateUpdate128 is stated in Algorithm 1. The block diagram of StateUpdate128 function is shown in Fig. 1. The function Round is an AES encryption round as shown in Fig. 11.

1.1 A.1 Encryption and Generation of Tag of AEGIS-128
AEGIS-128 has \(4\) phases for encryption. We describe each phase concisely. We use the same notations that are defined in the original paper with the description of AEGIS-128 [19].
-
1
Initialization of AEGIS-128
Initialization of AEGIS-128 consists of loading the key and IV into the state, and running the cipher for 10 steps with the key and IV being used as message.
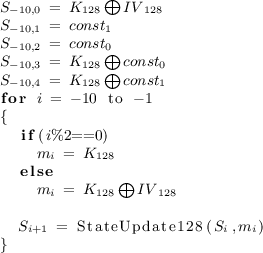
-
2
Processing the Authenticated Data
The associated data AD is used to update the state. If the last associated data block is not a full block, use 0 bits to pad it to 128 bits, and the padded full block is used to update the state. Note that if adlen = 0, the state will not be updated.
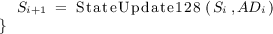
-
3
Encryption of Plaintext Data
If the last plaintext block is not a full block, use 0 bits to pad it to 128 bits, and the padded full block is used to update the state. But only the partial block is encrypted. Note that if msglen = 0, the state will not get updated, and there is no encryption.
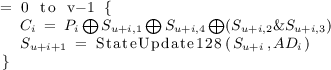
-
4
Finalization
After encrypting all the plaintext blocks, we generate the authentication tag using seven more steps. The length of the associated data and the length of the message are used to update the state.

The authentication tag \(T\) consists of the first \(t\) bits of \(T'\).
1.2 A.2 Decryption and Verification of AEGIS-128
The exact values of key size, IV, size, and tag-size should be known to the decryption and verification processes. The decryption starts with the initialization and the processing of authenticated data. Then the ciphertext is decrypted as follows:
-
If the last ciphertext block is not a full block, decrypt only the partial ciphertext block. The partial plaintext block is padded with 0 bits, and the padded full plaintext block is used to update the state.
-
For \(i= 0\) to \(v-1\), Perform decryption and update the state.
The finalization in the decryption process is the same as that in the encryption process. It is emphasized that if the verification fails, the ciphertext and the newly generated authentication tag should not be given as output; otherwise, the state of AEGIS-128 is vulnerable to known-plaintext or chosen-ciphertext attacks (using a fixed IV).
Rights and permissions
Copyright information
© 2015 Springer International Publishing Switzerland
About this paper
Cite this paper
Bhattacharjee, D., Chattopadhyay, A. (2015). Efficient Hardware Accelerator for AEGIS-128 Authenticated Encryption. In: Lin, D., Yung, M., Zhou, J. (eds) Information Security and Cryptology. Inscrypt 2014. Lecture Notes in Computer Science(), vol 8957. Springer, Cham. https://doi.org/10.1007/978-3-319-16745-9_21
Download citation
DOI: https://doi.org/10.1007/978-3-319-16745-9_21
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-16744-2
Online ISBN: 978-3-319-16745-9
eBook Packages: Computer ScienceComputer Science (R0)