Abstract
Developing distributed applications typically requires to integrate new code with legacy third-party services, e.g., e-commerce facilities, maps, etc. These services cannot always be assumed to smoothly collaborate with each other; rather, they live in a “wild” environment where they must compete for resources, and possibly diverge from the expected behaviour if they find it convenient to do so. To overcome these issues, some recent works have proposed to discipline the interaction of mutually distrusting services through behavioural contracts. The idea is a dynamic composition, where only those services with compliant contracts can establish sessions through which they interact. Compliance between contracts guarantees that, if services behave honestly, they will enjoy safe interactions. We exploit a theory of timed behavioural contracts to formalise, design and implement a message-oriented middleware where distributed services can be dynamically composed, and their interaction monitored to detect contract violations. We show that the middleware allows to reduce the complexity of developing distributed applications, by relieving programmers from the need to explicitly deal with the misbehaviour of external services.
This is a preview of subscription content, log in via an institution.
Buying options
Tax calculation will be finalised at checkout
Purchases are for personal use only
Learn about institutional subscriptionsNotes
- 1.
We denote with \(\mathbf {u}\) a sequence of names/variables, and we assume each
 to have a unique definition
to have a unique definition 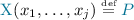 , with the free vars of
, with the free vars of 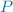 included in
included in  .
. - 2.
To avoid confusion between “channel-kinded” variables used in input/output prefixes and “session-kinded” variables, we forbid processes which improperly mix them, like e.g.
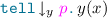 , where y is used both as a session variable and a channel variable.
, where y is used both as a session variable and a channel variable. - 3.
Asynchronous communication is possible despite TSTs having a synchronous semantics, as the middleware is delegated to receive messages on behalf of the recipient.
- 4.
Note that verifying the correctness of private keys has a polynomial complexity in the number of bits of the public key, while the problem of cracking RSA keys is considered to be exponentially hard.
References
PayPal buyer protection. https://www.paypal.com/us/webapps/mpp/ua/useragreement-full#13. Accessed 8 July 2015
Alur, R., Dill, D.L.: A theory of timed automata. Theor. Comput. Sci. 126(2), 183–235 (1994)
Ardagna, D., Pernici, B.: Adaptive service composition in flexible processes. IEEE Trans. Software Eng. 33(6), 369–384 (2007)
Banavar, G., Chandra, T., Strom, R.E., Sturman, D.: A case for message oriented middleware. In: Jayanti, P. (ed.) DISC 1999. LNCS, vol. 1693, pp. 1–17. Springer, Heidelberg (1999)
Bartoletti, M., Cimoli, T., Murgia, M., Patteri, M.G., Mascia, M.J., Podda, A.S., Pompianu, L., COREserve: a contract-oriented reservation marketplace (2015). http://coreserve.unica.it
Bartoletti, M., Cimoli, T., Murgia, M., Podda, A.S., Pompianu, L.: Compliance and subtyping in timed session types. In: Graf, S., Viswanathan, M. (eds.) Formal Techniques for Distributed Objects, Components, and Systems. LNCS, vol. 9039, pp. 161–177. Springer, Heidelberg (2015)
Bartoletti, M., Cimoli,T., Murgia, M., Podda, A.S., Pompianu, L.: A contract-oriented middleware (2015). http://co2.unica.it
Bartoletti, M., Cimoli, T., Zunino, R.: Compliance in behavioural contracts: a brief survey. In: Kahramanogullari, O., et al. (eds.) Degano Festschrift. LNCS, vol. 9465, pp. 103–121. Springer, Heidelberg (2015). doi:10.1007/978-3-319-25527-9_9
Bartoletti, M., Tuosto, E., Zunino, R.: Contract-oriented computing in \(CO_2\). Sci. Ann. Comp. Sci. 22(1), 5–60 (2012)
Bartoletti, M., Zunino, R.: A calculus of contracting processes. In: LICS (2010)
Behrmann, G., David, A., Larsen, K.G.: A tutorial on Uppaal. In: Bernardo, M., Corradini, F. (eds.) SFM-RT 2004. LNCS, vol. 3185, pp. 200–236. Springer, Heidelberg (2004)
Rueß, H., Schätz, B., Blech, J.O., Falcone, Y.: Behavioral specification based runtime monitors for OSGi services. In: Margaria, T., Steffen, B. (eds.) ISoLA 2012, Part I. LNCS, vol. 7609, pp. 405–419. Springer, Heidelberg (2012)
Tuosto, E., Bocchi, L., Yoshida, N., Honda, K.: A theory of design-by-contract for distributed multiparty interactions. In: Gastin, P., Laroussinie, F. (eds.) CONCUR 2010. LNCS, vol. 6269, pp. 162–176. Springer, Heidelberg (2010)
Bocchi, L., Lange, J., Yoshida, N.: Meeting deadlines together. In: CONCUR (2015, to appear)
Yang, W., Yoshida, N., Bocchi, L.: Timed multiparty session types. In: Baldan, P., Gorla, D. (eds.) CONCUR 2014. LNCS, vol. 8704, pp. 419–434. Springer, Heidelberg (2014)
Brogi, A., Canal, C., Pimentel, E.: Behavioural types for service integration: achievements and challenges. ENTCS 180(2), 41–54 (2007)
Buscemi, M.G., Montanari, U.: CC-Pi: a constraint-based language for specifying service level agreements. In: De Nicola, R. (ed.) ESOP 2007. LNCS, vol. 4421, pp. 18–32. Springer, Heidelberg (2007)
Göbel, J., Joschko, P., Koors, A., Page, B.: The discrete event simulation framework DESMO-J: review, comparison to other frameworks and latest development. In: Proceedings of ECMS, pp. 100–109 (2013)
Harel, D., Marelly, R.: Playing with time: on the specification and execution of time-enriched LSCs. In: MASCOTS, pp. 193–202 (2002)
Heckel, R., Lohmann, M.: Towards contract-based testing of Web services. Electr. Notes Theor. Comput. Sci. 116, 145–156 (2005)
Hoffman, K.J., Zage, D., Nita-Rotaru, C.: A survey of attack and defense techniques for reputation systems. ACM Comput. Surv. 42(1), 1:1–1:31 (2009)
Honda, K., Vasconcelos, V.T., Kubo, M.: Language primitives and type discipline for structured communication-based programming. In: Hankin, C. (ed.) ESOP 1998. LNCS, vol. 1381, pp. 122–138. Springer, Heidelberg (1998)
Honda, K., Yoshida, N., Carbone, M.: Multiparty asynchronous session types. In: POPL (2008)
Ligatti, J., Bauer, L., Walker, D.: Run-time enforcement of nonsafety policies. ACM Trans. Inf. Syst. Secur. 12(3), 19:1–19:41 (2009)
Milner, R., Parrow, P., Walker, D.: A calculus of mobile processes. I and II. Inf. Comput. 100(1), 1–77 (1992)
Mukhija, A., Dingwall-Smith, A., Rosenblum, D.: QoS-aware service composition in Dino. In: ECOWS, pp. 3–12 (2007)
Neykova, R., Bocchi, L., Yoshida, N.: Timed runtime monitoring for multiparty conversations. In: BEAT, pp. 19–26 (2014)
Larsen, K.G., Skou, A.: An overview and synthesis on timed process algebras. In: Larsen, K.G., Skou, A. (eds.) CAV 1991. LNCS, vol. 575, pp. 376–398. Springer, Heidelberg (1992)
Rivest, R.L., Shamir, A., Adleman, L.: A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 21(2), 120–126 (1978)
Sahai, A., Machiraju, V., Sayal, M., van Moorsel, A.P.A., Casati, F.: Automated SLA monitoring for Web services. In: DSOM, pp. 28–41 (2002)
Saraswat, V.A., Rinard, M.C.: Concurrent constraint programming. In: POPL, pp. 232–245 (1990)
Sebastio, S., Vandin, A.: MultiVeStA: statistical model checking for discrete event simulators. In: Proceedings of ValueTools, pp. 310–315 (2013)
Srivatsa, M., Xiong, L., Liu, L.: TrustGuard: countering vulnerabilities in reputation management for decentralized overlay networks. In: WWW, pp. 422–431 (2005)
Strunk, A.: QoS-aware service composition: a survey. In: ECOWS, pp. 67–74. IEEE (2010)
Takeuchi, K., Honda, K., Kubo, M.: An interaction-based language and its typing system. In: Halatsis, C., Philokyprou, G., Maritsas, D., Theodoridis, S. (eds.) PARLE 1994. LNCS, vol. 817, pp. 398–413. Springer, Heidelberg (1994)
Tuosto, E.: Contract-oriented services. In: Beek, M.H., Lohmann, N. (eds.) WS-FM 2012. LNCS, vol. 7843, pp. 16–29. Springer, Heidelberg (2013)
Yu, T., Zhang, Y., Lin, K.-J.: Efficient algorithms for Web services selection with end-to-end QoS constraints. ACM Trans. Web 1(1), 6 (2007)
Zeng, L., Benatallah, B., Ngu, A.H., Dumas, M., Kalagnanam, J., Chang, H.: QoS-aware middleware for Web services composition. IEEE Trans. Software Eng. 30(5), 311–327 (2004)
Acknowledgments
The authors thank Maria Grazia Patteri, Mirko Joshua Mascia and Stefano Lande for their assistance in setting up the evalution and the case studies, and Alceste Scalas for the discussion about Java APIs. This work is partially supported by Aut. Reg. of Sardinia grants L.R.7/2007 CRP-17285 (TRICS), P.I.A. 2010 (“Social Glue”), P.O.R. F.S.E. Operational Programme of the Aut. Reg. of Sardinia, EU Social Fund 2007-13 – Axis IV Human Resources, Objective l.3, Line of Activity l.3.1), by MIUR PRIN 2010-11 project “Security Horizons”, and by EU COST Action IC1201 “Behavioural Types for Reliable Large-Scale Software Systems” (BETTY).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2016 Springer International Publishing Switzerland
About this paper
Cite this paper
Bartoletti, M., Cimoli, T., Murgia, M., Podda, A.S., Pompianu, L. (2016). A Contract-Oriented Middleware. In: Braga, C., Ölveczky, P. (eds) Formal Aspects of Component Software. FACS 2015. Lecture Notes in Computer Science(), vol 9539. Springer, Cham. https://doi.org/10.1007/978-3-319-28934-2_5
Download citation
DOI: https://doi.org/10.1007/978-3-319-28934-2_5
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-28933-5
Online ISBN: 978-3-319-28934-2
eBook Packages: Computer ScienceComputer Science (R0)


 to have a unique definition
to have a unique definition 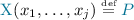 , with the free vars of
, with the free vars of 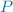 included in
included in  .
.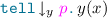 , where y is used both as a session variable and a channel variable.
, where y is used both as a session variable and a channel variable.