Abstract
We present the first fault attack on cryptosystems based on supersingular isogenies. During the computation of the auxiliary points, the attack aims to change the base point to a random point on the curve via a fault injection. We will show that this would reveal the secret isogeny with one successful perturbation with high probability. We will exhibit the attack by placing it against signature schemes and key-exchange protocols with validations in place. Our paper therefore demonstrates the need to incorporate checks in implementations of the cryptosystem.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
It is also possible to compress \((R,\phi (R))\) by sending \((r_{1},r_{2})\) instead (c.f. [1]). The verifier can then recover R and \(\phi (R)\) given \(P_B\), \(Q_B\), \(\phi (P_B)\) and \(\phi (Q_B)\).
- 2.
It is also possible to compress \(z_i\) by sending \(r_{1,i}\) and \(r_{2,i}\) instead. The verifier can then recover R and \(\phi (R)\) given \(P_B\), \(Q_B\), \(\phi (P_B)\) and \(\phi (Q_B)\).
References
Azarderakhsh, R., Jao, D., Kalach, K., Koziel, B., Leonardi, C.: Key compression for isogeny-based cryptosystems. In: Proceedings of the 3rd ACM International Workshop on ASIA Public-Key Cryptography, pp. 1–10 (2016)
Biehl, I., Meyer, B., Müller, V.: Differential fault attacks on elliptic curve cryptosystems. In: Bellare, M. (ed.) CRYPTO 2000. LNCS, vol. 1880, pp. 131–146. Springer, Heidelberg (2000). doi:10.1007/3-540-44598-6_8
Charles, D.X., Lauter, K.E., Goren, E.Z.: Cryptographic hash functions from expander graphs. J. Cryptol. 22(1), 93–113 (2009)
Childs, A.M., Jao, D., Soukharev, V.: Constructing elliptic curve isogenies in quantum subexponential time. J. Math. Cryptol. 8(1), 1–29 (2014)
Ciet, M., Joye, M.: Elliptic curve cryptosystems in the presence of permanent and transient faults. Des. Codes Crypt. 36(1), 33–43 (2005)
Costello, C., Jao, D., Longa, P., Naehrig, M., Renes, J., Urbanik, D.: Efficient compression of SIDH public keys. In: Coron, J.-S., Nielsen, J.B. (eds.) EUROCRYPT 2017. LNCS, vol. 10210, pp. 679–706. Springer, Cham (2017). doi:10.1007/978-3-319-56620-7_24
Costello, C., Longa, P., Naehrig, M.: Efficient algorithms for supersingular isogeny Diffie-Hellman. In: Robshaw, M., Katz, J. (eds.) CRYPTO 2016. LNCS, vol. 9814, pp. 572–601. Springer, Heidelberg (2016). doi:10.1007/978-3-662-53018-4_21
Couveignes, J.M.: Hard homogeneous spaces. IACR Cryptology ePrint Archive, 2006: 291 (2006)
De Feo, L., Jao, D., Plût, J.: Towards quantum-resistant cryptosystems from supersingular elliptic curve isogenies. J. Math. Cryptol. 8(3), 209–247 (2014)
Fujisaki, E., Okamoto, T.: Secure integration of asymmetric and symmetric encryption schemes. In: Wiener, M. (ed.) CRYPTO 1999. LNCS, vol. 1666, pp. 537–554. Springer, Heidelberg (1999). doi:10.1007/3-540-48405-1_34
Galbraith, S.D., Petit, C., Shani, B., Ti, Y.B.: On the security of supersingular isogeny cryptosystems. In: Cheon, J.H., Takagi, T. (eds.) ASIACRYPT 2016. LNCS, vol. 10031, pp. 63–91. Springer, Heidelberg (2016). doi:10.1007/978-3-662-53887-6_3
Galbraith, S.D., Petit, C., Silva, J.: Signature schemes based on supersingular isogeny problems. Cryptology ePrint Archive, Report 2016/1154 (2016). http://eprint.iacr.org/2016/1154
Jao, D., De Feo, L.: Towards quantum-resistant cryptosystems from supersingular elliptic curve isogenies. In: Yang, B.-Y. (ed.) PQCrypto 2011. LNCS, vol. 7071, pp. 19–34. Springer, Heidelberg (2011). doi:10.1007/978-3-642-25405-5_2
Jao, D., Soukharev, V.: Isogeny-based quantum-resistant undeniable signatures. In: Mosca, M. (ed.) PQCrypto 2014. LNCS, vol. 8772, pp. 160–179. Springer, Cham (2014). doi:10.1007/978-3-319-11659-4_10
Kirkwood, D., Lackey, B.C., McVey, J., Motley, M., Solinas, J.A., Tuller, D.: Failure is not an option: standardization issues for post-quantum key agreement. In: Workshop on Cybersecurity in a Post-Quantum World (2015)
Kuperberg, G.: A subexponential-time quantum algorithm for the dihedral hidden subgroup problem. SIAM J. Comput. 35(1), 170–188 (2005)
Peikert, C.: Lattice cryptography for the internet. In: Mosca, M. (ed.) PQCrypto 2014. LNCS, vol. 8772, pp. 197–219. Springer, Cham (2014). doi:10.1007/978-3-319-11659-4_12
Rostovtsev, A., Stolbunov, A.: Public-key cryptosystem based on isogenies. Cryptology ePrint Archive, Report 2006/145 (2006). http://eprint.iacr.org/
Srinath, M.S., Chandrasekaran, V.: Isogeny-based quantum-resistant undeniable blind signature scheme. Cryptology ePrint Archive, Report 2016/148 (2016). http://eprint.iacr.org/2016/148
Shor, P.W.: Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM J. Comput. 26(5), 1484–1509 (1997)
Silverman, J.H.: The Arithmetic of Elliptic Curves. Graduate Texts in Mathematics, vol. 106, 2nd edn. Springer, New York (2009)
Vélu, J.: Isogénies entre courbes elliptiques. C.R. Acad. Sc. Paris, Série A. 273, 238–241 (1971)
Xi, S., Tian, H., Wang, Y.: Toward quantum-resistant strong designated verifier signature from isogenies. Int. J. Grid Util. Comput. 5(2), 292–296 (2012)
Yoo, Y., Azarderakhsh, R., Jalali, A., Jao, D., Soukharev, V.: A post-quantum digital signature scheme based on supersingular isogenies. In: Financial Crypto 2017 (2017, to appear)
Acknowledgements
I am grateful to Steven Galbraith and Craig Costello for insightful conversations and comments. I would also like to thank the referees for their helpful feedback and suggestions.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
A Signature Schemes in Detail
A Signature Schemes in Detail
1.1 A.1 Digital Signature Scheme
The signature scheme has three steps: key generation, signing and verifying.
-
Set-up and key generation: Fix a prime p of the form \(p=\ell _A^{e_A}\cdot \ell _B^{e_B}\cdot f\pm 1\) where \(\ell _A\) and \(\ell _B\) are small distinct primes, f is a small cofactor and \(e_A\) and \(e_B\) are positive integers such that \(\ell _A^{e_A}\approx \ell _B^{e_B}\). Now fix an elliptic curve E over \(\mathbb {F}_{p^2}\). Next, let \(t=0.5\lfloor \log _2 p\rfloor \) and fix a hash function \(H:\{0,1\}^{*}\rightarrow \{0,1\}^{t}\).
The signer picks a random element \(S\in E[\ell _A^{e_A}]\) with order \(\ell _A^{e_A}\) and computes \(\phi :E\rightarrow E/\langle S\rangle =E_S\). The signer then generates a basis \(\{P_B,Q_B\}\) for \(E[\ell _B^{e_B}]\), and computes and publishes the tuple
$$\begin{aligned} (E,P_B,Q_B,E_S,\phi (P_B),\phi (Q_B)) \end{aligned}$$as the public key.
-
Signing: The signer needs to produce t challenges. So for each \(i=1,\dots ,t\), choose random elements \(r_{1,i},r_{2,i}\in \mathbb {Z}/\ell _B^{e_B}\mathbb {Z}\) such that not both are divisible by \(\ell _B\) and computes the points
$$\begin{aligned} R_i&=[r_{1,i}]P_B+[r_{2,i}]Q_B,\\ T_i&=[r_{1,i}]\phi (P_B)+[r_{2,i}]\phi (Q_B) \end{aligned}$$and the isogenies
$$\begin{aligned} \psi _i:E&\rightarrow E/\langle R_i\rangle = E_{R_i},\\ \phi _i':E_S&\rightarrow E_S/\langle T_i\rangle = E_{T_i}. \end{aligned}$$Given a message m, the signer computes
$$\begin{aligned} h=H\left( m,E_{R_1},\dots ,E_{R_t},E_{T_1},\dots ,E_{T_t}\right) . \end{aligned}$$The bit-string of h would serve as the sequence of challenge bits. If the i-th bit of h is 0, the signer sets \(z_i=(R_i,\phi (R_i))\) Footnote 2. If the i-th bit of h is 1, the signer sets \(z_i=\psi _i(S)\). The signature would then be the tuple
$$\begin{aligned} (h,z_1,z_2,\dots ,z_{t}). \end{aligned}$$ -
Verifying: To verify the signature, the verifier would use the output of the hash as the challenge bits and use the same verification procedure as seen in Sect. 2.2 to verify each \(z_i\) as the response to the challenge bits.
1.2 A.2 Undeniable Signature Scheme
This signature scheme has three steps: key generation, signing and verifying. The last step is split into confirmation or disavowal.
-
Set-up and key generation: Fix a hash function \(H:\{0,1\}^{*}\rightarrow \mathbb {Z}\). Fix a prime p of the form \(p=\ell _A^{e_A}\cdot \ell _M^{e_M}\cdot \ell _C^{e_C}\cdot f\pm 1\) and fix a supersingular elliptic curve E over \(\mathbb {F}_{p^2}\). Now pick bases \(\{P_A,Q_A\}\), \(\{P_M,Q_M\}\) and \(\{P_C,Q_C\}\) for the \(\ell _A^{e_A}\), \(\ell _M^{e_M}\) and \(\ell _C^{e_C}\)-torsion points respectively. The signer then randomly picks elements \(a_1,a_2\in \mathbb {Z}/\ell _A^{e_A}\mathbb {Z}\) not both divisible by \(\ell _A\), computes the subgroup \(G_A=\langle [a_1]P_A+[a_2]Q_A\rangle \) and uses Vélu’s formula to compute \(E_A=E/G_A\) and the isogeny \(\phi _A:E\rightarrow E_A\). The signer computes the image of \(P_C\) and \(Q_C\) under this isogeny and publishes the tuple \((E_A,\phi _A(P_C),\phi _A(Q_C))\).
-
Signing: Given a message M, the signer computes the hash \(h=H(M)\) and the subgroup \(G_M=P_M+[h]Q_M\). Next, the signer computes the following isogenies:
-
\(\phi _M:E\rightarrow E_M=E/G_M\)
-
\(\phi _{M,AM}:E_M\rightarrow E_{AM}=E/\phi _M(G_A)\)
-
\(\phi _{A,AM}:E_A\rightarrow E_{AM}=E/\phi _A(G_M)\)
The signature then consists of the tuple
$$\begin{aligned} \left( E_{AM},\phi _{M,AM}(\phi _M(P_C)), \phi _{M,AM}(\phi _M(Q_C))\right) . \end{aligned}$$ -
-
Verification: Since this is an undeniable signature scheme, there are two components to this: the confirmation protocol and the disavowal protocol. In the former protocol, given the signature
$$\begin{aligned} \left( E_{AM},\phi _{M,AM}(\phi _M(P_C)), \phi _{M,AM}(\phi _M(Q_C))\right) , \end{aligned}$$the objective is to confirm \(E_{AM}\). In the latter, given the signature \((E_F,F_P,F_Q)\), the objective is to disavow the signature.
-
Confirmation:
-
1.
The signer picks random elements \(c_1,c_2\in \mathbb {Z}/\ell _C^{e_C}\mathbb {Z}\) not both divisible by \(\ell _C\), computes the subgroup \(G_C=\langle [c_1]P_C+[c_2]Q_C\rangle \) and computes
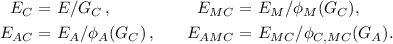
-
2.
The signer publishes \((E_C,E_{AC},E_{MC}, E_{AMC},\phi _C(P_M)+[h]\phi _C(Q_M))\).
-
3.
The verifier randomly selects \(b\in \{0,1\}\).
-
If \(b=0\): the signer outputs \(\ker \phi _C\). The verifier then computes \(\phi _C\), \(\phi _{M,MC}\), \(\phi _{A,AC}\) and \(\phi _{F}:E_F\rightarrow E_{FC}\) and checks that each isogeny maps between the curves in the commitment. The verifier also computes \(\phi _{C,MC}\) and checks that it matches the commitment.
-
If \(b=1\): the signer outputs \(\ker \phi _{C,AC}\) and the verifier then computes \(\phi _{MC,AMC}\), \(\phi _{AC,AMC}\) and checks that \(E_{AMC}\) is the codomain.
-
-
1.
-
Disavowal: The disavowal step is almost exactly the same as the confirmation step with the exception in the last step where if \(b=0\), the verifier would see that \(E_{FC}\not \cong E_{AMC}\) (Fig. 4).
-
Rights and permissions
Copyright information
© 2017 Springer International Publishing AG
About this paper
Cite this paper
Ti, Y.B. (2017). Fault Attack on Supersingular Isogeny Cryptosystems. In: Lange, T., Takagi, T. (eds) Post-Quantum Cryptography . PQCrypto 2017. Lecture Notes in Computer Science(), vol 10346. Springer, Cham. https://doi.org/10.1007/978-3-319-59879-6_7
Download citation
DOI: https://doi.org/10.1007/978-3-319-59879-6_7
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-59878-9
Online ISBN: 978-3-319-59879-6
eBook Packages: Computer ScienceComputer Science (R0)