Abstract
Hyperproperties are quickly becoming very popular in the context of systems security, due to their expressive power. They differ from classic trace properties since they are represented by sets of sets of executions instead of sets of executions. This allows us, for instance, to capture information flow security specifications, which cannot be expressed as trace properties, namely as predicates over single executions. In this work, we reason about how it is possible to move standard abstract interpretation-based static analysis methods, designed for trace properties, towards the verification of hyperproperties. In particular, we focus on the verification of bounded subset-closed hyperproperties which are easier to verify than generic hyperproperties. It turns out that a lot of interesting specifications (e.g., Non-Interference) lie in this category.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
Access Control is defined over systems (reachable) states. Non-Interference, instead, is defined over systems input/output (I/O) traces.
- 2.
Here \(X \leqslant Y\) iff for every \(d \in X\) exists \(d^\prime \in Y\) such that d is a prefix of \(d^\prime \) [9].
- 3.
For the sake of simplicity, we suppose the programs \(\mathsf {P}_i\) have only one variable and the state is denoted by the set of its possible values.
- 4.
Namely a semantics function, defined on a program \(\mathsf {P}\) syntax, computing \(\mathcal {S}[\mathsf {P}]\).
- 5.
\(\mathcal {A}\) is an abstract domain of \(\mathcal {C}\) if there exists a Galois connection
 , where \(\alpha ,\gamma \) are monotone maps such that: \(\forall c \in \mathcal {C}, a \in \mathcal {A}\, .\, \alpha (c) \preceq a \Leftrightarrow c \preccurlyeq \gamma (a)\).
, where \(\alpha ,\gamma \) are monotone maps such that: \(\forall c \in \mathcal {C}, a \in \mathcal {A}\, .\, \alpha (c) \preceq a \Leftrightarrow c \preccurlyeq \gamma (a)\). - 6.
It is a Galois connection with surjective abstraction function.
- 7.
We recall that any abstract domain can be made partitioning [22].
- 8.
Where
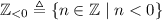 and the others are similarly defined.
and the others are similarly defined. - 9.
Here we implicitly apply a non-relational variables abstraction.
- 10.
Here \({\dot{\subseteq }}\) denotes the pointwise set inclusion.
References
Agrawal, S., Bonakdarpour, B.: Runtime verification of k-safety hyperproperties in HyperLTL. In: IEEE 29th Computer Security Foundations Symposium, pp. 239–252 (2016)
Alpern, B., Schneider, F.B.: Defining liveness. Inf. Process. Lett. 21(4), 181–185 (1985)
Antonopoulos, T., Gazzillo, P., Hicks, M., Koskinen, E., Terauchi, T., Wei, S.: Decomposition instead of self-composition for proving the absence of timing channels. In: Proceedings of PLDI, pp. 362–375 (2017)
Assaf, M., Naumann, D.A., Signoles, J., Totel, E., Tronel, F.: Hypercollecting semantics and its application to static analysis of information flow. In: Proceedings of POPL, pp. 874–887 (2017)
Banerjee, A., Giacobazzi, R., Mastroeni, I.: What you lose is what you leak: Information leakage in declassification policies. ENTCS 173, 47–66 (2007)
Barthe, G., D’Argenio, P.R., Rezk, T.: Secure information flow by self-composition. In: Proceedings of 17th IEEE Computer Security Foundations Workshop, pp. 100–114 (2004)
Buro, S., Mastroeni, I.: Abstract code injection - A semantic approach based on abstract non-interference. In: Dillig, I., Palsberg, J. (eds.) VMCAI 2018. LNCS, vol. 10747, pp. 116–137. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-73721-8_6
Clarkson, M.R., Finkbeiner, B., Koleini, M., Micinski, K.K., Rabe, M.N., Sánchez, C.: Temporal logics for hyperproperties. In: Proceedings of POST (2014)
Clarkson, M.R., Schneider, F.B.: Hyperproperties. J. Comput. Secur. 18(6), 1157–1210 (2010)
Cohen, E.: Information transmission in computational systems. SIGOPS Oper. Syst. Rev. 11(5), 133–139 (1977)
Cousot, P.: Constructive design of a hierarchy of semantics of a transition system by abstract interpretation. Theor. Comput. Sci. 277(1–2), 47–103 (2002)
Cousot, P., Cousot, R.: Abstract interpretation: a unified lattice model for static analysis of programs by construction or approximation of fixpoints. In: Proceedings of POPL, pp. 238–252 (1977)
Cousot, P., Cousot, R.: Systematic design of program analysis frameworks. In: Proceedings of POPL, pp. 269–282 (1979)
Cousot, P., Cousot, R.: Higher-order abstract interpretation (and application to comportment analysis generalizing strictness, termination, projection and PER analysis of functional languages). In: Proceedings of ICCL, pp. 95–112 (1994)
Finkbeiner, B., Rabe, M.N., Sánchez, C.: Algorithms for model checking HyperLTL and HyperCTL\(^*\). In: Kroening, D., Păsăreanu, C.S. (eds.) CAV 2015. LNCS, vol. 9206, pp. 30–48. Springer, Cham (2015). https://doi.org/10.1007/978-3-319-21690-4_3
Giacobazzi, R., Logozzo, F., Ranzato, F.: Analyzing program analyses. In: Proceedings of POPL, pp. 261–273 (2015)
Giacobazzi, R., Mastroeni, I.: Transforming semantics by abstract interpretation. Theor. Comput. Sci. 337(1–3), 1–50 (2005)
Giacobazzi, R., Mastroeni, I.: Abstract non-interference: parameterizing non-interference by abstract interpretation. In: Proceedings of POPL, pp. 186–197 (2004)
Giacobazzi, R., Mastroeni, I.: Abstract non-interference: a unifying framework for weakening information-flow. ACM Trans. Priv. Secur 21(2), 9:1–9:31 (2018)
Giacobazzi, R., Ranzato, F.: Personal communication (2017)
Goguen, J.A., Meseguer, J.: Security policies and security models. In: IEEE Symposium on Security and Privacy, pp. 11–20 (1982)
Hunt, S., Mastroeni, I.: The PER model of abstract non-interference. In: Proceedings of 12th International Symposium on Static Analysis, pp. 171–185 (2005)
Mastroeni, I., Banerjee, A.: Modelling declassification policies using abstract domain completeness. MSCS 21(6), 1253–1299 (2011)
Mastroeni, I., Nikolić, Đ.: Abstract program slicing: from theory towards an implementation. In: Dong, J.S., Zhu, H. (eds.) ICFEM 2010. LNCS, vol. 6447, pp. 452–467. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-16901-4_30
Mastroeni, I., Pasqua, M.: Hyperhierarchy of semantics - A formal framework for hyperproperties verification. In: Ranzato, F. (ed.) SAS 2017. LNCS, vol. 10422, pp. 232–252. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-66706-5_12
Mastroeni, I., Zanardini, D.: Abstract program slicing: An abstract interpretation-based approach to program slicing. ACM TOCL 18(1), 7:1–7:58 (2017)
Naumann, D.A.: From coupling relations to mated invariants for checking information flow. In: Proceedings of ESORICS, pp. 279–296 (2006)
Pasqua, M., Mastroeni, I.: On topologies for (hyper)properties. In: Proceedings of ICTCS, pp. 1–12 (2017). http://ceur-ws.org/Vol-1949/ICTCSpaper13.pdf
Ranzato, F., Tapparo, F.: Strong preservation as completeness in abstract interpretation. In: Schmidt, D. (ed.) ESOP 2004. LNCS, vol. 2986, pp. 18–32. Springer, Heidelberg (2004). https://doi.org/10.1007/978-3-540-24725-8_3
Sousa, M., Dillig, I.: Cartesian hoare logic for verifying k-safety properties. In: Proceedings of PLDI, pp. 57–69 (2016)
Terauchi, T., Aiken, A.: Secure information flow as a safety problem. In: Hankin, C., Siveroni, I. (eds.) SAS 2005. LNCS, vol. 3672, pp. 352–367. Springer, Heidelberg (2005). https://doi.org/10.1007/11547662_24
Urban, C., Müller, P.: An abstract interpretation framework for input data usage. In: ESOP, pp. 683–710 (2018)
Acknowledgments
We thank Roberto Giacobazzi and Francesco Ranzato for sharing with us their preliminary work on analyzing analyses [20], which has many connections with the present work and may create interesting future collaborations. Finally, we would like to thank the anonymous reviewers for the useful suggestions and comments, helping us in improving the presentation of our work.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2018 Springer Nature Switzerland AG
About this paper
Cite this paper
Mastroeni, I., Pasqua, M. (2018). Verifying Bounded Subset-Closed Hyperproperties. In: Podelski, A. (eds) Static Analysis. SAS 2018. Lecture Notes in Computer Science(), vol 11002. Springer, Cham. https://doi.org/10.1007/978-3-319-99725-4_17
Download citation
DOI: https://doi.org/10.1007/978-3-319-99725-4_17
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-99724-7
Online ISBN: 978-3-319-99725-4
eBook Packages: Computer ScienceComputer Science (R0)


 , where
, where 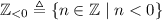 and the others are similarly defined.
and the others are similarly defined.