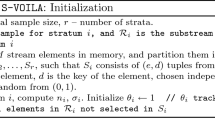
Abstract
Results indicate that the two recently introduced self-adjusting heaps are the most competitive choices for the applications considered. Further, the results indicate that only some heap structures support lazymerge/lazydelete operations well, partially confirming that algorithms based on top-down skew heap compare more favorably than those based on binomial queues, that there are strong grounds for believing the conjectured amortized time bounds for pairing heap operations, and that pairing heaps are a competitive alternative to Fibonacci heaps.
Similar content being viewed by others
References
Brown, M. R., Implementation and analysis of binomial queue algorithms,SIAM J. Comput.,7 (1978), 298–319.
Cheriton, D., and Tarjan, R. E., Finding minimum spanning trees,SIAM J. Comput.,5 (1976), 724–742.
deCarvahlo, M., Private communication.
Eliot, B., Private communication.
Fredman, M. L.,et al., The pairing heap: a new form of self-adjusting heap,Algorithmica,1 (1986), 111–129.
Fredman, M. L., and Tarjan, R. E., Fibonacci heaps and their uses in network optimization algorithms,Proc. 25th Annual IEEE Symp. on Foundations of Computing, 1984, pp. 338–345.
Jones, D. W., An empirical comparison of priority queue and event set implementations,Comm. ACM,29 (1986), 300–311.
Jones, D. W., Private communication.
Knuth, D. E.,The Art of Computer Programming, Vol. 2, 2nd edn., Addison-Wesley, Reading, MA, 1973, pp. 9–24, 39–45.
Knuth, D. E.,The Art of Computer Programming, Vol. 3, 2nd edn., Addison-Wesley, Reading, MA, 1973, pp. 145–152.
Kupferschmid, M., Private communication.
Sedgewick, R.,Algorithms, Addison-Wesley, Reading, MA, 1983, pp. 35–42, 398–405.
Sleator, D. D., and Tarjan, R. E., Self-adjusting binary trees,Proc. 15th ACM Symp. on Theory of Computing, 1983, pp. 235–246.
Sleator, D. D., and Tarjan, R. E., Self-adjusting binary search trees,J. Assoc. Comput. Mach.,32 (1985), 652–686.
Sleator, D. D., and Tarjan, R. E., Self-adjusting heaps,SIAM J. Comput.,15 (1986), 52–69.
Tarjan, R. E.,Data Structures and Network Algorithms, CBMS Regional Conference Series in Applied Mathematics, Vol. 44, SIAM, Philadephia, PA, 1983.
Vaucher, J., and Jones, D. W., Technical correspondence on “An empirical comparison of priority queue and event set implementations,”Comm. ACM,29 (1986), 1002–1005.
Vuillemin, J., A data structure for manipulating priority queues,Comm. ACM,21 (1978), 309–314.
Author information
Authors and Affiliations
Additional information
Communicated by D. T. Lee.
This work was carried out during the author's final graduate year (1987) at Rensselaer Polytechnic Institute. Though the author is currently with Thomson Financial Networks, this is an unaffiliated paper.
Rights and permissions
About this article
Cite this article
Liao, A.M. Three priority queue applications revisited. Algorithmica 7, 415–427 (1992). https://doi.org/10.1007/BF01758771
Received:
Revised:
Issue Date:
DOI: https://doi.org/10.1007/BF01758771