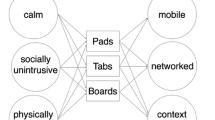
Abstract
This paper identifies and analyses potential business benefits of ubiquitous computing (ubicomp). Its aim is to challenge whether the growing visibility of topics such as ubiquitous or pervasive computing, automatic identification (Auto-ID) and radio frequency identification (RFID) can be justified from a business perspective. To do so it analyses the business contribution of existing ubicomp applications, reconstructs their development phases, introduces the business relevant base-functionalities and discusses implications on the design of products, processes and services using ubicomp applications.
The creation of an alternative and rather cost efficient machine-machine-relation between already established information systems and the real world things they try to manage has been identified as the main source of business benefit. However, before businesses can systematically leverage all potential benefits, some technical and political questions, such as creating robust solutions and solving privacy issues, have to be answered.
Similar content being viewed by others
Literatur
Abowd, G. D.; Ebling, M. R.; Gellersen, H.-W.: Context-Aware Pervasive Computing. In: IEEE Wireless Communications 9 (2002) 5, S. 8–9.
Abowd, G. D.; Mynatt, E. D.: Charting Past, Present, and Future Research in Ubiquitous Computing. In: ACM Transactions on Computer Human Interaction 47 (2000) 1, S. 29–58.
Accenture (Hrsg.): Seize the day: The Silent Commerce Imperative. http://www.accenture.com/xdoc/en/ideas/isc/pdf/SeizeTheDay.PDF, 2002, Abruf am 2003-04-22.
Antifakos, S.; Michahelles, F.; Schiele, B.: Proactive Instructions for Furniture Assembly. In: The Fourth International Conference on Ubiquitous Computing, UbiComp 2002, Göteborg, Sweden, September 2002.
Auto-ID Center: http://www.autoidcenter.org, Abruf am 2003-04-22.
Banavar, G.; Bernstein, A.: Software infrastructure and design challenges for ubiquitous computing applications. In: Communications of the ACM 45 (2002) 12, S. 92–96.
Bender, K.: Ubiquitous Computing — the inversion of virtuality. In: Wissenschaftliche Zeitschrift — TU Dresden 47 (1998) 4, S. 44–47.
Bohn, J.; Coroama, V.; Langheinrich, M.; Mattern, F.; Rohs, M.: Allgegenwart und Verschwinden des Computers: Leben in einer Welt smarter Alltagsdinge. Arbeitsbericht ETH Zürich, http://www.inf.ethz.ch/vs/publ/papers/allvercom.pdf, 2003, Abruf am 2003-04-10.
Buderi, R.: Computing goes Everywhere. In: Technology Review 104 (2001) 1, S. 52–61.
Business Week: Special report: Wireless in Cyberspace. In: Business Week (2000), 2000-05- 26, S. 136.
Business Wire: Shoplifters and Dishonest Employees Continue to Steal Profits From United States Retailers, Says Jack L. Hayes International. In: Business Wire (2002), 2002-06-27. http://www.businesswire.com/webbox/bw.062702/221782286.htm, Abruf am 2003-04-22.
Davies, N.; Gellersen, H.-W.: Beyond Prototypes: Challenges in Deploying Ubiquitous Systems. In: IEEE Pervasive Computing 1 (2002) 1, S. 26–35.
Escort Memory Systems: Fords “Quality is Job 1″ = Radio Frequency Identification (RFID) from Escort Memory Systems. http://www.ems-rfid.com/apps/fordcase.html, 2002, Abruf am 2003-04-22.
Fano, A.; Gershman, A.: The Future of Business Services in the Age of Ubiquitous Computing. In: Communications of the ACM 45 (2002) 12, S. 83–87.
Ferguson, G. T.: Have Your Objects Call My Objects. In: Harvard Business Review 80 (2003) 6, S. 138–143.
Fleisch, E.; Österle, H.: Auf dem Weg zum Echtzeitunternehmen. Erscheint in: Alt, R.; Österle, H. (Hrsg): Real-time Business. Springer, Berlin 2003.
Forrester Research: RFID: The Smart Product (R)evolution. Cambridge, August 2002.
Gain, B.: Connecting the dots. Web-enabled IC networks are demanding closer collaboration between manufacturers and their suppliers. In: EBN Online, 2003-03-10, S. 29–33.
Gellersen, H.-W.; Schmidt, A.; Beigl, M.: Adding Some Smartness to Devices and Everyday Things. In: IEEE Workshop on Mobile Computing Systems and Applications 2000, 7th.-8th. December, Monterrey, USA. http://ubicomp.teco.edu/index2.html, Abruf am 2003-04-22.
Harry, M.; Schroeder, R.: Six Sigma: The Breakthrough Management Strategy Revolutionizing The Worlds Top Corporations. Harry 1999.
IDTechEx: Authentication and Counterfeiting Protection Conference Review. In: Smart Labels Analyst 2 (2002) 2, S. 1–3.
Jessup, L. M.; Robey, D.: The relevance of social issues in ubiquitous computing environments. In: Communications of the ACM 45 (2002) 12, S. 88–81.
Kaerner, H.: Profitabler dank Telematik: Wenn Service neu gestaltet wird. http://www.accenture.de/4publika/4fachart/index.jsp, 2002-10, Abruf am 2003-04-22.
Kärkkäinen, M.; Holström, J.: Wireless product identification: enabler for handling efficiency, customisation and information sharing. In: Supply Chain Management 7 (2002) 4, S. 242–252.
Kaihla, P.: The ghosts in the machines. In: Canadian Business 74 (2001) 17, S. 24–30.
Kaye, J.; Matsakis, N.; Gray, M.; Wheeler, A.; Hawley, M.: PC Dinners, Mr. Java and Counter Intelligence: Prototyping Smart Appliances for the Kitchen. MIT Media Laboratory, Cambridge, USA 2000.
Khan, J. M.; Katz, R. H.; Pister, K. S. J.: Emerging Challenges: Mobile Networking for „Smart Dust”. In: Journal of Communications and Networks 2 (2000) 3, S. 188–196.
Kindberg, T. et al.: People, Places, Things: Web Presence for the RealWorld. http://www.cooltown.com/dev/wpapers/webpres/WebPresence.asp, 2001, Abruf am 2003-04-22.
Langheinrich, M.: Privacy by Design — Principles of Privacy-Aware Ubiquitous Systems. In: Proceedings of Ubicomp 2001, September 30-October 2, 2001, Atlanta, USA.
Lyytinen, K.; Yoo, Y.: Issues and Challenges in Ubiquitous Computing. In: Communications of the ACM 45 (2002) 12, S. 83–87.
Malone, T.; Crowston, K.: The Interdisciplinary Study of Coordination. In: ACM Computing Surveys 26 (1994) 1, S. 87–119.
Mattern, F. (Hrsg.): Total vernetzt. Springer, Berlin etc. 2003.
Midkiff, S. F.: The First Summer School on Ubiquitous and Pervasive Computing. in IEEE Pervasive Computing 2 (2003) 1, S. 84–88.
Negus, K. J.; Stephans, A. P.; Lansford, J.: HomeRF: wireless networking for the connected home. In: IEEE Personal Communications 7 (2000) 1, S. 20–27.
Norman, D. A.: The Invisible Computer. MIT Press, Cambridge, USA 1998.
Papazoglou, M. P.: The Role of Agent Technology in Business Electronic Commerce. In: Lecture Notes in Computer Science (1999) 1652, S. 245–264.
Pierre, S.: Mobile computing and ubiquitous networking: concepts, technologies and challenges. In: Telematics and Informatics 18 (2001) 2-3, S. 109–131.
RFID Journal: Diverse Fallstudien. http://www.rfidjournal.com/article/archive/4/, Abruf am 2003-04-22.
Satyanarayanan, M.: (2001) Pervasive computing: vision and challenges. In: IEEE Personal Communications 8 (2001) 4, S. 10–17.
Sharp, K. R.: Technology Edge RFID Goes Mainstream. In: ID Systems 21 (2001) 1, S. 58–59.
Stajano, F.; Anderson, R.: The Resurrecting Duckling: Security Issues for Ubiquitous Computing. In: Computer 35 (2002) 4, Supp., S. 22–26.
Utterback, J.: Mastering the Dynamics of Innovation. Harvard Business School Press, Boston, Massachusetts 1994.
Waldo, J.: Virtual Organizations, Pervasive Computing, and an Infrastructure for Networking at the Edge. In: Information Systems Frontiers 4 (2002) 1, S. 9–18.
Watzlawick, P.; Beavin, J. H.; Jackson, D. D.: Menschliche Kommunikation. Formen, Störungen, Paradoxien. Hans Huber, Bern 1967.
Weiser, M.: The computer for the 21st century. In: Scientific American 256 (1991) 3, S. 94–104.
Wolff, J. A.: RFID tags — an intelligent bar code replacement. ftp://service.boulder.ibm.com/software/pervasive/info/tech/gsoee200.pdf, 2001, Abruf am 2003-04-22.
Author information
Authors and Affiliations
Rights and permissions
About this article
Cite this article
Fleisch, E., Dierkes, M. Ubiquitous Computing aus betriebswirtschaftlicher Sicht. Wirtschaftsinf 45, 611–620 (2003). https://doi.org/10.1007/BF03250924
Published:
Issue Date:
DOI: https://doi.org/10.1007/BF03250924