Abstract
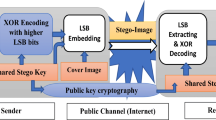
The combination of spatial information services, wireless mobile services, and social network services has generated massive social media geographic data, enriching the types of covert communication carriers. However, the imperceptibility and robustness of steganography methods based on geographic data still need to be improved. To this end, this paper proposes a steganography method, which hides secret messages into geo-coordinates. In this method, the sender analyzes the correlation between digit planes of geo-coordinate and positioning accuracy and divides digit planes into A-grade, B-grade, and C-grade according to significance. Then, secret messages are priority embedded in C-grade using the MLSBR algorithm to increase embedding capacity, and the rest are embedded into B-grade using STC adaptive steganography algorithm to enhance the imperceptibility. The receiver uses shared parameters to achieve the correct extraction of secret messages, and the extraction steps are obtaining stego geo-coordinates, dividing digit planes, and matching the steganography algorithm. Experimental results demonstrate that compared with the existing geo-coordinate steganography methods, the proposed method can realize the complete extraction of secret messages, the average embedding capacity is increased by 20.53 bits per geo-coordinate, the extraction error rate is reduced by 50.65%, the trajectory similarity is improved by 94.29%, and the PSNR is raised by 15.55 dB, which all show that the proposed method performs better under the comprehensive measure of average embedding capacity, imperceptibility, and robustness.






Similar content being viewed by others
Explore related subjects
Discover the latest articles and news from researchers in related subjects, suggested using machine learning.Availability of data and materials
The datasets analyzed during the current study are available at https://github.com/lym003/geocoordinate-steganography.
Code Availability
Code availability: The code is available at https://github.com/lym003/geocoordinate-steganography.
References
Guan Q, Liu P, Zhang W, Lu W, Zhang X (2022) Double-Layered Dual-Syndrome Trellis Codes Utilizing Channel Knowledge for Robust Steganography. IEEE T Inf Foren Sec 18:501–516
Zhang X, Qian Z, Li S (2016) Prospect of digital steganography research. J Appl Sci 34(5):476–484
Mor N (2011) Geographic information from georeferenced social media data. ACM Sigspatial Special 3(2):54–61
Peng X, Huang Z (2014) A novel popular tourist attraction discovering approach based on geo-tagged social media big data. Isprs Int J Geo-Inf 6:216
Pei T, Huang Q, Wang X et al (2021) Big geodata aggregation: Connotation, classification, and framework. Natl. Remote. Sens. Bull. 25:2153–2156
Liu Y, Liu Q, Deng M, Shi Y (2022) Recent advance and challenge in geospatial big data mining. Acta Geodaetica et Cartographica Sinica 51(7):1544–1560
Yershov A, Zabiniako V, Semenchuk P (2012) Using concatenated steganography for visual analysis in GIS SOA. Appl Comput Syst 13(1):74–82
L Hebbes, F Y Janjua, D Livingstone, J Orwell (2006) A steganographic method for the secure embedding of GIS data streams into aerial photography. In: Joint IST Workshop on Mobile Future and the Symposium on Trends in Communications, pp 97–100
Wu M, Hsu C, Jia J (2009) A GeoTagging scheme using image steganography and GPS information authentication. In: 2009 Fifth International Conference on Intelligent Information Hiding and Multimedia Signal Processing, pp 1245–1248
M Jayachandran, J Manikandan (2010) SAR image compression using steganography. In: 2010 International Conference on Advances in Computer Engineering, pp 203–206
Guo J, Xue S, Zhu R, Chen K (2016) An improved digital raster map data hiding algorithm based on H.264/AVC intra prediction. Geomat Inf Sci Wuhan Univ 41(6):825–831
M Rajeesh, A R.Ram (2021) Tree monitoring system using geotagging and steganography. In: 2021 International Conference on Communication, Control and Information Sciences (ICCISc), pp 1–6
M Diehl (2008) Geographic data and steganography - Using google earth and KML files for high-capacity steganography. In: International Conference on Security and Cryptography, pp 381–387
Li A, Li S, Lv G (2012) Disguise and reduction methods of gis vector data based on difference expansion principle. Procedia Eng 29:1344–1350
Hassan RF, Mohammed MS (2017) Information hiding using geographic information system (GIS) vector file. Eng Technol J 35(2):182–188
Kurtuldu Ö, Demirci M (2019) StegoGIS: A new steganography method using the geospatial domain. Turk J Elec Eng Comp Sci 27(1):532–546
Zhang Y, Luo X, Lu W, Yang C, Liu F (2022) Research progress on digital image robust steganography. J Image Graphics 27(01):0003–0026
Filler T, Judas J, Fridrich J (2010) Minimizing embedding impact in steganography using trellis-coded quantization. Proceedings of SPIE, Media Forensics and Security II:501–514
Du H, Liu J, Tian Y, Luo X (2022) Steganographic key recovery for adaptive steganography under "known-message attacks." Multimed Tools Appl 81(8):10981–11004
Yue M, Peng Z, Zheng K, Peng Y (2014) Rights protection for trajectory streams. In: International Conference on Database Systems for Advanced Applications, pp 407–421
Su H, Liu S, Zheng B, Zhou X, Zheng K (2020) A survey of trajectory distance measures and performance evaluation. The VLDB J 29:3–32
Fahime K, Mohammad Reza M (2021) Trajectory Similarity Measurement: An Enhanced Maximal Travel Match Method. Trans in Gis 25(3):1485–1503
Liu X (2022) Contributions to high accuracy snapshot GNSS positioning. Universitat Politècnica de Catalunya
Qian C, Liu H, Tang J et al (2017) An integrated GNSS/INS/LiDAR-SLAM positioning method for highly accurate forest stem mapping. Remote Sens 9(1):3
Li G, Geng J (2019) Characteristics of raw multi-GNSS measurement error from google android smart devices. GPS Solut 23:1–16
Chang K, Kim K, Lee S, Kim J, Lee J, Kim H, Ko Y, Kim I, Bang S (2022) Technical challenges and solutions for 10 cm-level positioning accuracy towards 6G. ICT Express 9:492–506
Li Z, Li J (2013) Quickly calculate the distance between two points and measurement error based on latitude and longitude. Geomat Spat Inf Technol 36:235–237
Esri E (1998) Shapefile technical description: An ESRI whitepaper, environmental systems research institute. Inc, Redlands, CA, USA
Peng Z, Zhang C (2004) The roles of geography markup language (GML), scalable vector graphics (SVG), and Web feature service (WFS) specifications in the development of Internet geographic information systems (GIS). J Geogr Syst 6:95–116
T Wilson (2008) OGC® KML.Version 2.2.0. Open Geospatial Consortium
Huang X, Chen Z (2021) Design and implementation of heterogeneous web platform based on JSON. Comput Technol Dev 31(03):120–125
Zheng Y, Zhang L, Xie X, Ma W (2009) Mining interesting locations and travel sequences from GPS trajectories. In: Proceedings of the 18th international conference on World wide web, pp 791–800
Yuan H, Li G, Bao Z, Feng L (2021) An effective joint prediction model for travel demands and traffic flows. In: 2021 IEEE 37th International Conference on Data Engineering (ICDE), pp 348–359
Hu D, Chen L, Fang H, Fang Z, Li T, Gao Y (2023) Spatio-Temporal Trajectory Similarity Measures: A Comprehensive Survey and Quantitative Study. arXiv:2303.05012
Funding
This work was supported by the National Natural Science Foundation of China (No.62202434, 62202495) and Henan Provincial Science and Technology Research Project (222102210079).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflicts of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix
Appendix
1.1 A The List of Abbreviations
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Liu, Y., Zhang, M., Duan, Y. et al. A strong-robust covert communication scheme based on geo-coordinate. Multimed Tools Appl 83, 32475–32496 (2024). https://doi.org/10.1007/s11042-023-16867-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-16867-9