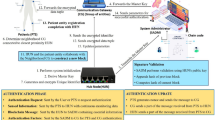
Abstract
Nowadays, IoT is growing rapidly and is a security concern as there are multiple security policy violations. Furthermore, blockchain development has grown rapidly since Bitcoin first became popular. IoT security issues can be solved by Blockchain. One way to achieve this is through the use of secure communication between IoT devices. Blockchain has emerged as one of the promising and most abundant technologies for security of cloud infrastructure. Blockchain is designed to store, read, and validate transactions within a distributed database system. Security and confidentiality can be enhanced with a distributed ledger that is shared across cloud nodes. In particular, it provides security through effective caching, encryption, and peer-aware sharing of generated hash values. Cloud computing is a centralized service in the financial sector that protects sensitive information and provides better security to protect personal data. Due to the lack of verified services and unauthorized access, compromised keys can damage important information. In this paper, we introduces the Hook Curve Master Node Key Authentication (HC-MNKA) to improve the security based on Shuffle Standard Padding Encryption Crypto Policy (S2PES) to solve the above issues. The proposed Pre-Ack decentralized chain link (P2PACD) algorithm is used to create new node transactions in the network. Furthermore, the Mutual Trust Node Behavioral Rate (MTNBR) algorithm is used to find network trust rates based on successive weight. Based on the trust rate, the hash index is created depending on the user policy to form a blockchain link. The Hook curve Master node Key authentication is applied to verify the transaction node to check if it’s a valid transaction node in the Network of Things. Security analysis shows that a decentralized blockchain network authenticates validation results, increasing transparency and security.






Similar content being viewed by others
Data availability
The data consideration is based on user communication and data processing in block blockchain. “Any text content file taken to process the proposed system”.
References
Da Silva Rodrigues CK, Rocha V. Towards Blockchain for suitable efficiency and data integrity of IoT ecosystem transactions. IEEE Latin Am Trans. 2021;19(7):1199–206. https://doi.org/10.1109/TLA.2021.9461849.
Zhou J, Feng G, Wang Y. Optimal deployment mechanism of blockchain in resource-constrained IoT systems. IEEE Internet Things J. 2022;9(11):8168–77. https://doi.org/10.1109/JIOT.2021.3106355.
Sadawi A, Hassan MS, Ndiaye M. A survey on the integration of blockchain with IoT to enhance performance and eliminate challenges. IEEE Access. 2021;9:54478–97. https://doi.org/10.1109/ACCESS.2021.3070555.
Sadawi A, Hassan MS, Ndiaye M. On the integration of blockchain with IoT and the role of oracle in the combined system: the full picture. IEEE Access. 2022;10:92532–58. https://doi.org/10.1109/ACCESS.2022.3199007.
Sun S, Du R, Chen S, Li W. Blockchain-based IoT access control system: towards security, lightweight, and cross-domain. IEEE Access. 2021;9:36868–78. https://doi.org/10.1109/ACCESS.2021.3059863.
Yuan, et al. Secure data transportation with software-defined networking and k-n secret sharing for high-confidence IoT services. IEEE Internet Things J. 2020;7(9):7967–81. https://doi.org/10.1109/JIOT.2020.2993587.
Wu W, Peng H, Tong F, Li L. Novel secure data transmission methods for IoT based on STP-CS with multilevel critical information concealment function. IEEE Internet Things J. 2023;10(5):4557–78. https://doi.org/10.1109/JIOT.2022.3218681.
Jia M, Yin Z, Li D, Guo Q, Gu X. Toward improved offloading efficiency of data transmission in the IoT-Cloud by Leveraging Secure Truncating OFDM. IEEE Internet Things J. 2019;6(3):4252–61. https://doi.org/10.1109/JIOT.2018.2875743.
Ullah A, Azeem M, Ashraf H, Alaboudi AA, Humayun M, Jhanjhi N. Secure Healthcare Data Aggregation and Transmission in IoT—a survey. IEEE Access. 2021;9:16849–65. https://doi.org/10.1109/ACCESS.2021.3052850.
Xu G. IoT-assisted ECG monitoring framework with secure data transmission for health care applications. IEEE Access. 2020;8:74586–94. https://doi.org/10.1109/ACCESS.2020.2988059.
Tao H, Bhuiyan MZA, Abdalla AN, Hassan MM, Zain JM, Hayajneh T. Secured data collection with hardware-based Ciphers for IoT-Based Healthcare. IEEE Internet Things J. 2019;6(1):410–20. https://doi.org/10.1109/JIOT.2018.2854714.
Mei Q, Yang M, Chen J, Wang L, Xiong H. Expressive data sharing and self-controlled fine-grained data deletion in Cloud-Assisted IoT. IEEE Trans Dependable Secure Comput. 2023;20(3):2625–40. https://doi.org/10.1109/TDSC.2022.3188740.
Chen S, Zhu X, Zhang H, Zhao C, Yang G, Wang K. Efficient privacy preserving data collection and computation offloading for fog-assisted IoT. IEEE Trans Sustain Comput. 2020;5(4):526–40. https://doi.org/10.1109/TSUSC.2020.2968589.
Hu C, Pu Y, Yang F, Zhao R, Alrawais A, Xiang T. Secure and Efficient Data Collection and Storage of IoT in Smart Ocean. IEEE Internet Things J. 2020;7(10):9980–94. https://doi.org/10.1109/JIOT.2020.2988733.
Zhang B. Comments on “provably secure generalized signcryption scheme with public verifiability for secure data transmission between resource-constrained IoT devices.” IEEE Internet Things J. 2020;7(5):4666–70. https://doi.org/10.1109/JIOT.2020.2974817.
Said G, Ghani A, Ullah A, Azeem M, Bilal M, Kwak KS. Light-Weight Secure Aggregated Data Sharing in IoT-Enabled Wireless Sensor Networks. IEEE Access. 2022;10:33571–85. https://doi.org/10.1109/ACCESS.2022.3160231.
Yan X, He X, Yu J, Tang Y. White-Box Traceable Ciphertext-Policy Attribute-Based Encryption in Multi-Domain Environment. IEEE Access. 2019;7:128298–312. https://doi.org/10.1109/ACCESS.2019.2939413.
Zhang L, Cui Y, Mu Y. Improving Security and Privacy Attribute Based Data Sharing in Cloud Computing. IEEE Syst J. 2020;14(1):387–97. https://doi.org/10.1109/JSYST.2019.2911391.
Rezaeibagha F, Mu Y, Huang K, Chen L, Zhang L. Toward secure data computation and outsource for multi-user Cloud-based IoT. IEEE Trans Cloud Comput. 2023;11(1):217–28. https://doi.org/10.1109/TCC.2021.3087614.
Aazam M, Islam SU, Lone ST, Abbas A. Cloud of Things (CoT): Cloud-Fog-IoT Task Offloading for Sustainable Internet of Things. IEEE Trans Sustain Comput. 2022;7(1):87–98. https://doi.org/10.1109/TSUSC.2020.3028615.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the topical collection “Advances in Computational Approaches for Image Processing, Wireless Networks, Cloud Applications and Network Security” guest edited by P. Raviraj, Maode Ma and Roopashree H R.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Vijayalakshmi, V., Sharmila, K. Security-Based Hook Curve Master Node Key Authentication (HC-MNKA) Using Shuffle Standard Padding Encryption Crypto Policy (S2PES). SN COMPUT. SCI. 5, 26 (2024). https://doi.org/10.1007/s42979-023-02305-y
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s42979-023-02305-y