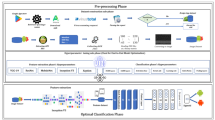
Abstract
Computer vision techniques have advanced greatly in recent years through deep learning, achieving unprecedented performance. This has motivated applying deep learning to malware detection through image-based approaches to circumvent extensive feature engineering for diverse threats. However, existing work converting Android binaries to rectangular images neglects the intrinsic byte sequence structure, introducing spurious spatial relationships that weaken detection accuracy. To address this, space-filling curves have mapped binaries to images while preserving ordering. This paper proposes a novel method using Hilbert space-filling curves to visualize and classify Android apps. Bytecode is extracted from Dalvik Executable (DEX) files and transformed to grayscale images via Hilbert coding for model training. Additionally, a novel and balanced image dataset is proposed consisting of Hilbert transformations for 4995 benign and 4995 malicious Android apps randomly sampled from the AndroZoo repository. Experiments using this dataset evaluated pre-trained InceptionV3, VGG16, ResNet50 and EfficientNetB0 via transfer learning. A custom Convolutional Neural Network (CNN) was also trained from scratch. InceptionV3 achieved the highest performance at 97.99% accuracy, 98.50% precision, 97.50% recall and 97.99% F1-score. Comparative assessment with previous image-based malware detection research indicates our approach outperforms state-of-the-art approaches. By leveraging Hilbert space-filling curves to map binaries to images while preserving sequential relationships, detection accuracy is improved over methods introducing extraneous spatial representations.















Similar content being viewed by others
Data availability
All artefacts are available online at: https://github.com/BenedictMbungang/Detecting-Android-Malware-CNN-Hilbert-Space-Filling-Curves/. However, due to the large size of the generated images dataset, they are available from the corresponding author on reasonable request.
References
Albahar MA, Elsayed MS, Jurcut AD. A modified ResNeXt for Android malware identification and classification. Comput Intell Neurosci. 2022;1:8634784. https://doi.org/10.1155/2022/8634784.
Allix K, Bissyandé TF, Klein J, et al. AndroZoo: collecting millions of android apps for the research community. In: Proceedings of the 13th international conference on mining software repositories (MSR), 2016. pp. 468–471, https://doi.org/10.1145/2901739.2903508
Aonzo S, Georgiu G, Verderame L, et al. Obfuscapk: An open-source black-box obfuscation tool for Android apps. SoftwareX. 2020;11. https://doi.org/10.1016/j.softx.2020.100403.
Bala Z, Zambuk FU, Imam BY, et al. Transfer learning approach for malware images classification on Android devices using deep convolutional neural network. Proc Comput Sci. 2022;212:429–40. https://doi.org/10.1016/j.procs.2022.11.027.
Chrysikos N, Karampelas P, Xylogiannopoulos K. Permission-based classification of Android malware applications using random forest. In: Proceedings of the 22nd European conference on cyber warfare & security (ECCWS), 2023. https://doi.org/10.34190/eccws.22.1.1212.
Daoudi N, Samhi J, Kabore A, et al. DexRay: a simple, yet effective deep Learning approach to Android malware detection based on image representation of bytecode. In: Proceedings of the 2nd international workshop on deployable machine learning for security defense (MLHat), 2021. pp. 81–106, https://doi.org/10.1007/978-3-030-87839-9_4.
Elayan ON, Mustafa AM. Android malware detection using deep learning. Proc Comput Sci. 2021;184:847–52. https://doi.org/10.1016/j.procs.2021.03.106.
Freitas S, Duggal R, Chau DH. MalNet: a large-scale image database of malicious software. In: Proceedings of the 31st ACM international conference on information and knowledge management (CIKM), 2022. pp. 3948–3952 https://doi.org/10.1145/3511808.3557533.
Hamilton CH, Rau-Chaplin A. Compact Hilbert indices for multi-dimensional data. In: Proceedings of the 1st international conference on complex, intelligent and software intensive systems (CISIS), 2007. pp. 139–146, https://doi.org/10.1109/CISIS.2007.16.
Hasan H, Tork Ladani B, Zamani B. MEGDroid: a model-driven event generation framework for dynamic Android malware analysis. Inf Softw Technol. 2021;135: 106569. https://doi.org/10.1016/j.infsof.2021.106569.
He K, Zhang X, Ren S, et al. Delving deep into rectifiers: surpassing human-level performance on ImageNet classification. In: Proceedings of the IEEE international conference on computer vision (ICCV), 2015. pp. 1026–1034, https://doi.org/10.1109/ICCV.2015.123.
Huang N, Xu M, Zheng N, et al. Deep Android malware classification with API-based feature graph. In: Proceedings of the 18th IEEE international conference on trust, security and privacy in computing and communications/13th IEEE international conference on big data science and engineering (TrustCom/BigDataSE), 2019. pp. 296–303, https://doi.org/10.1109/TrustCom/BigDataSE.2019.00047.
Khan MAR, Kumar N, Tripathi RC. Detection of Android malware app through feature extraction and classification of Android image. Int J Adv Comput Sci Appl. 2022. https://doi.org/10.14569/IJACSA.2022.01305103.
Li X, Tang Y, Christo MS, et al. Android malware application detection method based on RGB image features in e-commerce. J Internet Technol. 2022;23(6):1343–52.
Lin WC, Yeh YR. Efficient malware classification by binary sequences with one-dimensional convolutional neural networks. Mathematics. 2022. https://doi.org/10.3390/math10040608.
Liu K, Xu S, Xu G, et al. A review of Android malware detection approaches based on machine learning. IEEE Access. 2020;8:124579–607. https://doi.org/10.1109/ACCESS.2020.3006143.
Millar S, McLaughlin N, del Rincon JM, et al. Multi-view deep learning for zero-day Android malware detection. J Inf Secur Appl. 2021;58: 102718. https://doi.org/10.1016/j.jisa.2020.102718.
Mitsuhashi R, Shinagawa T. Exploring optimal deep learning models for image-based malware variant classification. In: Proceedings of the 46th IEEE annual computers, software and applications conference (COMPSAC), 2022. pp. 779–788, https://doi.org/10.1109/COMPSAC54236.2022.00128.
Nataraj L, Karthikeyan S, Jacob G, et al. Malware images: visualization and automatic classification. In: Proceedings of the 8th international symposium on visualization for cyber security (VizSec), 2011. https://doi.org/10.1145/2016904.2016908.
Qaisar Z, Li R. Multimodal information fusion for Android malware detection using lazy learning. Multimed Tools Appl. 2022;81:12077–91. https://doi.org/10.1007/s11042-021-10749-8.
Sagan H. Some reflections on the emergence of space-filling curves: The way it could have happened and should have happened, but did not happen. J Franklin Inst. 1991;328(4):419–30. https://doi.org/10.1016/0016-0032(91)90017-W.
Simonyan K, Zisserman A. Very deep convolutional networks for large-scale image recognition. In: Proceedings of the 3rd international conference on learning representations (ICLR), 2014. pp. 1–14.
Surendran R, Thomas Kallivayalil T, Emmanuel S. A TAN based hybrid model for Android malware detection. J Inf Secur Appl. 2020. https://doi.org/10.1016/j.jisa.2020.102483.
Szegedy C, Vanhoucke V, Ioffe S, et al. Rethinking the inception architecture for computer vision. In: Proceedings of the IEEE conference on computer vision and pattern recognition (CVPR), 2016. pp. 2818–2826, https://doi.org/10.1109/CVPR.2016.308.
Tan M, Le Q. Efficientnet: rethinking model scaling for convolutional neural networks. In: Proceedings of the 36th international conference on machine learning (ICML), 2019. pp. 6105–6114.
Taye MM. Theoretical understanding of convolutional neural network: concepts, architectures, applications, future directions. Computation. 2023. https://doi.org/10.3390/computation11030052.
Tchakounte F, Manfouo R, Fendji JL, et al. SVDroid: Singular value decomposition with CNN for Android malware classification. Int J Comput Digit Syst. 2023;14:573–87. https://doi.org/10.12785/ijcds/140145.
Thangaveloo R, Jing WW, Leng CK, et al. DATDroid: Dynamic analysis technique in Android malware detection. Int J Adv Sci Eng Inf Technol. 2020;10(2):536–41. https://doi.org/10.18517/ijaseit.10.2.10238.
Xing X, Jin X, Elahi H, et al. A malware detection approach using autoencoder in deep learning. IEEE Access. 2022;10:25696–706. https://doi.org/10.1109/ACCESS.2022.3155695.
Yadav P, Menon N, Ravi V, et al. EfficientNet convolutional neural networks-based Android malware detection. Comput Secur. 2022. https://doi.org/10.1016/j.cose.2022.102622.
Funding
No funding received for this research.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
All authors certify that they have no affiliations with or involvement in any organization or entity with any financial interest or non-financial interest in the subject matter or materials discussed in this manuscript.
Ethical Approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Research Involving Human and/or Animals
Not applicable.
Informed Consent
Not applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Mbungang, B.N., Ali Wacka, J.B., Tchakounte, F. et al. Detecting Android Malware with Convolutional Neural Networks and Hilbert Space-Filling Curves. SN COMPUT. SCI. 5, 810 (2024). https://doi.org/10.1007/s42979-024-03123-6
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s42979-024-03123-6