Abstract
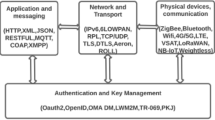
The proliferation of the Internet-of-Things (IoT) paradigm has brought about transformative changes in various real-life applications and revolutionized how we interact with technology. However, the exponential growth of global IoT implementations has also intensified cybersecurity concerns. Breaches in IoT compromise not only the associated technology but also the information it handles. Therefore, developing IoT intrusion detection systems to handle and tackle these security issues has become imperative. Intrusion detection systems (IDS) have gained popularity due to their real-time intrusion detection capabilities, evolving into signature-based and anomaly-based detection technologies over the decades. In this article, the authors propose an intrusion detection framework to enhance the security of the IoT environment. The proposed model uses the modified stacking ensemble classifier to detect anomalies in a real-time framework. Cuckoo search optimization is used to reduce data dimensionality. The performance of the developed framework is tested over several datasets, including KDD Cup 99, CSE-CIC-IDS2018, and CICIoT2023; it excels in detecting both known and evolving cyber-attack patterns with an accuracy rate of 99.87%, 98.89%, and 99.58% in binary classification tasks and 99.43%, 98.17%, and 98.86% in multiclass classification tasks. The results validate the performance of the proposed framework in both scenarios, as it outperformed several existing state-of-the-art methods over numerous evaluation metrics.







Similar content being viewed by others
Data Availability
Not applicable.
References
Guezzaz A, Benkirane S, Azrour M, Khurram S. A reliable network intrusion detection approach using decision tree with enhanced data quality. Secur Commun Netw. 2021;2021:1–8. https://doi.org/10.1155/2021/1230593.
Awad M, Alabdallah A. Addressing imbalanced classes problem of intrusion detection system using weighted extreme learning machine. Int J Comput Netw Commun. 2019;11:39–58. https://doi.org/10.5121/ijcnc.2019.11503.
Liu Y, Wu Q. A lightweight anomaly mining algorithm in the internet of things. In: Proceedings of IEEE 5th international conference on software engineering and service science. ICSESS; 2014. pp. 1142–5.
Yang A, Zhuansun Y, Liu C, Li J, Zhang C. Design of intrusion detection system for internet of things based on improved BP neural network. IEEE Access. 2019;7:106043–52. https://doi.org/10.1109/ACCESS.2019.2929919.
Jaw E, Wang X. Feature selection and ensemble-based intrusion detection system: an efficient and comprehensive approach. Symmetry (Basel). 2021;13:1764. https://doi.org/10.3390/sym13101764.
Uçar M, Uçar E, Incetaş MO. A stacking ensemble learning approach for intrusion detection system. Düzce Üniversitesi Bilim ve Teknoloji Dergisi. 2021;9:1329–41. https://doi.org/10.29130/dubited.737211.
Kabir E, Hu J, Wang H, Zhuo G. A novel statistical technique for intrusion detection systems. Futur Gener Comput Syst. 2018;79:303–18. https://doi.org/10.1016/j.future.2017.01.029.
Kumar V, Das AK, Sinha D. UIDS: a unified intrusion detection system for IoT environment. Evol Intell. 2021;14:47–59. https://doi.org/10.1007/s12065-019-00291-w.
Ravi V, Chaganti R, Alazab M. Recurrent deep learning-based feature fusion ensemble meta-classifier approach for intelligent network intrusion detection system. Comput Electr Eng. 2022;102:108156. https://doi.org/10.1016/j.compeleceng.2022.108156.
Soltani M, Siavoshani MJ, Jahangir AH. A content-based deep intrusion detection system. Int J Inf Secur. 2022;21:547–62. https://doi.org/10.1007/s10207-021-00567-2.
Jony AI, Arnob AKB. A long short-term memory based approach for detecting cyber attacks in IoT using CIC-IoT2023 dataset. J Edge Comput. 2024;3:28–42. https://doi.org/10.55056/jec.648.
Divyasree TH, Sherly KK. A network intrusion detection system based on ensemble CVM using efficient feature selection approach. Procedia Comput Sci. 2018;143:442–9. https://doi.org/10.1016/j.procs.2018.10.416.
Amouri A, Alaparthy VT, Morgera SD. A machine learning based intrusion detection system for mobile internet of things. Sensors (Switzerland). 2020;20:461. https://doi.org/10.3390/s20020461.
Attota DC, Mothukuri V, Parizi RM, Pouriyeh S. An ensemble multi-view federated learning intrusion detection for IoT. IEEE Access. 2021. https://doi.org/10.1109/ACCESS.2021.3107337.
Injadat M, Moubayed A, Nassif AB, Shami A. Multi-stage optimized machine learning framework for network intrusion detection. IEEE Trans Netw Serv Manag. 2020. https://doi.org/10.1109/TNSM.2020.3014929.
Wang M, Zheng K, Yang Y, Wang X. An explainable machine learning framework for intrusion detection systems. IEEE Access. 2020;8:73127–41. https://doi.org/10.1109/ACCESS.2020.2988359.
Mohy-Eddine M, Guezzaz A, Benkirane S, Azrour M, Farhaoui Y. An ensemble learning based intrusion detection model for industrial IoT security. Big Data Min Anal. 2023;6:273–87. https://doi.org/10.26599/BDMA.2022.9020032.
Aljawarneh S, Aldwairi M, Bani YM. Anomaly-based intrusion detection system through feature selection analysis and building hybrid efficient model. J Comput Sci. 2017. https://doi.org/10.1016/j.jocs.2017.04.009.
Zhang Y, Li P, Wang X. Intrusion detection for IoT based on improved genetic algorithm and deep belief network. IEEE Access. 2019;7:31711–22. https://doi.org/10.1109/ACCESS.2019.2903723.
Alghuried A. A model for anomalies detection in internet of things (IoT) using inverse weight clustering and decision tree. 2017. https://doi.org/10.21427/D7WK7S.
Kuang F, Xu W, Zhang S. A novel hybrid KPCA and SVM with GA model for intrusion detection. App Soft Comput J. 2014;18:178–84. https://doi.org/10.1016/j.asoc.2014.01.028.
Chung YY, Wahid N. A hybrid network intrusion detection system using simplified swarm optimization (SSO). Appl Soft Comput J. 2012;12:3014–22. https://doi.org/10.1016/j.asoc.2012.04.020.
Thamilarasu G, Chawla S. Towards deep-learning-driven intrusion detection for the internet of things. Sensors (Switzerland). 2019;19:1977. https://doi.org/10.3390/s19091977.
Mbarek B, Ge M, Pitner T. Enhanced network intrusion detection system protocol for internet of things. In: Proceedings of the ACM symposium on applied computing. Association for Computing Machinery; 2020. pp. 1156–63. https://doi.org/10.1145/3341105.3373867.
Thockchom N, Singh MM, Nandi U. A novel ensemble learning-based model for network intrusion detection. Complex Intell Syst. 2023. https://doi.org/10.1007/s40747-023-01013-7.
Emanet S, Baydogmus GK, Demir O. An ensemble learning based IDS using voting rule: VEL-IDS. PeerJ Comput Sci. 2023;9:1–23. https://doi.org/10.7717/PEERJ-CS.1553.
Abbas S, A lHejaili A, Sampedro GA, Abisado M, Almadhor AS, Shahzad T, et al. A novel federated edge learning approach for detecting cyberattacks in IoT infrastructures. IEEE Access. 2023;11:112189–98. https://doi.org/10.1109/ACCESS.2023.3318866.
Zhang H, Li JL, Liu XM, Dong C. Multi-dimensional feature fusion and stacking ensemble mechanism for network intrusion detection. Futur Gener Comput Syst. 2021;122:130–43. https://doi.org/10.1016/j.future.2021.03.024.
Seth S, Chahal KK, Singh G. A novel ensemble framework for an intelligent intrusion detection system. IEEE Access. 2021;9:138451–67. https://doi.org/10.1109/ACCESS.2021.3116219.
Nguyen DT, Le KH. The robust scheme for intrusion detection system in internet of things. Internet Things (Netherlands). 2023;24:100999. https://doi.org/10.1016/j.iot.2023.100999.
Biyyapu N, Veerapaneni EJ, Surapaneni PP, Vellela SS, Vatambeti R. Designing a modified feature aggregation model with hybrid sampling techniques for network intrusion detection. Clust Comput. 2024. https://doi.org/10.1007/s10586-024-04270-4.
Turukmane AV, Devendiran R. M-MultiSVM: an efficient feature selection assisted network intrusion detection system using machine learning. Comput Secur. 2024;137:103587. https://doi.org/10.1016/j.cose.2023.103587.
Imran M, Khan S, Hlavacs H, Khan FA, Anwar S. Intrusion detection in networks using cuckoo search optimization. Soft Comput. 2022. https://doi.org/10.1007/s00500-022-06798-2.
Awais M, Shamshad F, Bae S-H. Towards an adversarially robust normalization approach. 2020. https://doi.org/10.48550/arXiv.2006.11007.
Naskath J, Sivakamasundari G, Begum AAS. A study on different deep learning algorithms used in deep neural nets: MLP SOM and DBN. Wirel Pers Commun. 2023;128:2913–36. https://doi.org/10.1007/s11277-022-10079-4.
Süzen AA. Developing a multi-level intrusion detection system using hybrid-DBN. J Ambient Intell Human Comput. 2021;12:1913–23. https://doi.org/10.1007/s12652-020-02271-w.
Aggarwal A, Mittal M, Battineni G. Generative adversarial network: an overview of theory and applications. Int J Inf Manag Data Insights. 2021;1:100004. https://doi.org/10.1016/j.jjimei.2020.100004.
Chen X, Ding M, Wang X, Xin Y, Mo S, Wang Y, et al. Context autoencoder for self-supervised representation learning. Int J Comput Vis. 2024;132:208–23. https://doi.org/10.1007/s11263-023-01852-4.
Hassanieh W, Chehade A. Selective deep autoencoder for unsupervised feature selection. AAAI. 2024;38:12322–30.
Chowdhury R, Sen S, Roy A, Saha B. An optimal feature based network intrusion detection system using bagging ensemble method for real-time traffic analysis. Multimedia Tools Appl. 2022;81:41225–47. https://doi.org/10.1007/s11042-022-12330-3.
Zhou Y, Cheng G, Jiang S, Dai M. Building an efficient intrusion detection system based on feature selection and ensemble classifier. Comput Netw. 2020;174:107247. https://doi.org/10.1016/j.comnet.2020.107247.
Chohra A, Shirani P, Karbab EMB, Debbabi M. CHAMELEON: optimized feature selection using particle swarm optimization and ensemble methods for network anomaly detection. Comput Secur. 2022;117:102684. https://doi.org/10.1016/j.cose.2022.102684.
Rashid M, Kamruzzaman J, Imam T, Wibowo S, Gordon S. A tree-based stacking ensemble technique with feature selection for network intrusion detection. Appl Intell. 2022;52:9768–81. https://doi.org/10.1007/s10489-021-02968-1.
Mokbal F, Dan W, Osman M, Ping Y, Alsamhi S. An efficient intrusion detection framework based on embedding feature selection and ensemble learning technique. Int Arab J Inf Technol. 2022;19:237–48. https://doi.org/10.34028/iajit/19/2/11.
Abu Alghanam O, Almobaideen W, Saadeh M, Adwan O. An improved PIO feature selection algorithm for IoT network intrusion detection system based on ensemble learning. Expert Syst Appl. 2023;213:118745. https://doi.org/10.1016/j.eswa.2022.118745.
Mebawondu JO, Alowolodu OD, Mebawondu JO, Adetunmbi AO. Network intrusion detection system using supervised learning paradigm. Sci Afr. 2020;9:e00497. https://doi.org/10.1016/j.sciaf.2020.e00497.
Cao Y, Wang Z, Ding H, Zhang J, Li B. An intrusion detection system based on stacked ensemble learning for IoT network. Comput Electr Eng. 2023;110:108836. https://doi.org/10.1016/j.compeleceng.2023.108836.
Funding
This research received no external funding.
Author information
Authors and Affiliations
Contributions
Aishwarya Vardhan conceived the presented idea, developed the theory, and performed the computations. Prashant Kumar verified the analytical methods and supervised the findings of this work. Lalit Kumar Awasthi validated the proposed work and wrote- reviewed, and edited the paper. All authors discussed the results and contributed to the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
There are non-financial competing interests to report.
Research involving humans and/or animals
This article does not contain any studies involving humans and/or animals.
Informed consent
All authors have consented to submission to the journal.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Vardhan, A., Kumar, P. & Awasthi, L.K. A Resilient Intrusion Detection System for IoT Environment Based on a Modified Stacking Ensemble Classifier. SN COMPUT. SCI. 5, 1020 (2024). https://doi.org/10.1007/s42979-024-03364-5
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s42979-024-03364-5