Abstract
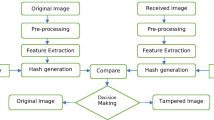
Hash functions are one way functions and often used in cryptography to ensure the integrity of files by creating a binary signature specific to that file. In a similar way, a family of special hash functions can be developed and used to generate one dimensional signatures of an image. The resultant signatures can then be used to compare the image either to a golden template or, if the image consists of repeating definite patterns, then to the texture itself. While such hash functions are sensitive enough to detect small changes and defects in repeating texture, they are immune to changes in illumination and contrast. In this paper we discuss the generation of suitable hash functions for textured images, which are simple enough to fit into a very small FPGA, and provide several examples of their use.
Similar content being viewed by others
References
Chin R.T., Harlow C.A. (1982). Automated visual Inspection: a survey. IEEE Trans. Pat Rec. PAMI-4(6):557
Thomas, A.D.H., Rodd, M.G. Holt, J.D., Neill, JC.J.: Real-time industrial visual inspection: a review, Real-Time Imaging. Academic, New York 139–158 (1995)
Onishi, H., Sasa, Y., Nagai, K., Tatsumi, S.: A pattern defect inspection method by parallel grayscale image comparison without precise image alignment. IECON 02 3, 2208–2213 (2002)
Hiroi, T., Maeda, S., Kubota, H., Watanabe, K., Nakagawa, Y.: Precise visual inspection for LSI wafer patterns using subpixel image alignment. Applications of Computer Vision. In: Proceedings of the second IEEE workshop on, 5–7 Dec. 1994 pp. 26–34 (1994)
Guan, S-U., Xie, P.: A golden block self-generating scheme for continuous patterned wafer inspections. Image analysis and processing. In: Proceedings of international conference on, 27–29 Sept. 1999 pp. 436–441 (1999)
Chen, J., Jain, A.K.: A structural approach to identify defects in textured images. In: Proceedings of IEEE., international conference Systems, Man and Cybernetics, 8–12 August, China, pp. 29–32 (1988)
Hajimowlana, S.H., Muscedere, R., Jullien, G.A., Roberts, J.W.: 1D autoregressive modeling for defect detection in web inspection systems. Circuits and Systems. In: Proceedings of 1998 Midwest Symposium on, 9–12 Aug. 1998, pp. 318–321 (1998)
Hajimowlana H., Muscedere R., Jullien G.A., Roberts J.W. (2000). Defect detection in web Inspection using fuzzy fusion of texture features. ISCAS 3:718–721
Koshimizu H. (1979). Fundemental study on automatic fabric inspection by computer image processing. SPIE Imag. Appl. Aut. Ind. Ins. Ass. 182:30–37
Fang T., Jafari M.A., Danforth S.C., Safari A. (2003). Signature analysis and defect detection in layered manufacturing of ceramic sensors and actuators. Mach. Vis. App. 15: 63–75
Venkatachalam V. (2000). Image classification using pseudo power signatures. IEEE Int. Conf. Image Process. 1:796–799
Schneier B. (1996). Applied crytography, 2nd edn. Wiley, New york
Menezes A.J., van Oorschot P.C., Vanstone S.A. (1996). Handbook of Applied Cryptography. CRC Press, Boca Raton
Baykal, I.C., Muscedere, R., Jullien, G.A. On the use of hash functions for defect detection in textures for in-camera web inspection systems. Circuits and Systems. ISCAS In: IEEE Int. symp. 5 pp. V-665 – V-668 (2002)
Walsh J.L. (1923). A closed set of orthogonal functions. Am. J. Math. 45:5–24
Fine N.J. (1949). On the Walsh functions. Trans. Am. Math. Soc. 65:372–414
Liu Y., Collins R.T., Tsin Y. (2004). A computational model for periodic pattern perception based on frieze and wallpaper groups. IEEE Trans. PAMI 26(3):354–371
Baykal, I.C., Jullien, G.A.: Detection of defects in textures with alignment error for real-time line-scan web inspection systems. Circuits and Systems, 2002. MWSCAS-2002. In: The 2002 45th Midwest Symposium on, vol. 3, 4–7 Aug. 2002 pp. III-292 – III-295 (2002)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Baykal, I.C., Jullien, G.A. On the Use of Hash Functions as Preprocessing Algorithms to Detect Defects on Repeating Definite Textures. Machine Vision and Applications 17, 185–195 (2006). https://doi.org/10.1007/s00138-006-0028-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00138-006-0028-0