Abstract
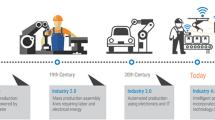
Digitalization has become a cornerstone of competitiveness in the industrial arena, especially in the cases of small lot sizes with many variants in the goods produced. Managers of industrial facilities have to handle the complexity that comes along with Industry 4.0 in diverse dimensions to leverage the potentials of digitalization for their sites. This article describes major drivers of this complexity in current industrial automation to outline the environment of today’s challenges for managers of this technical transition—and shows how managed industrial security services can contribute to stabilize the industrial system. An outlook is given to future automation scenarios as well as the major concepts involved in their protection.





Similar content being viewed by others
References
Berners-Lee T et al (2001) The Semantic Web. Scientific American, May 2001
BSI (2014) UP KRITIS Öffentlich-Private Partnerschaft zum Schutz Kritischer Infrastrukturen. Bundesamt für Sicherheit in der Informationstechnik, Bonn
Colombo AW et al (2014) Industrial cloud-based cyber-physical systems: the IMC-AESOP approach. Springer, Heidelberg
COM (2006) Communication from the commission on a European programme for critical infrastructure protection. COM(2006) 786 final. Commission of the European Communities, Brussels
Fiampolis P, Groll J (2016) Bringing together dev and ops. http://www.trainingjournal.com Accessed 23 April 2016
Fuhrmans V (2010) Virus attacks siemens plant-control systems. The Wall Street Journal, July 22
Gartner (2015). Principles and practices of DevOps. https://www.gartner.com/doc/3004719/principles-practices-devops, published 12th March 2015
Geisberger E, Broy M (2012) agendaCPS—Integrierte Forschungsagenda Cyber-Physical Systems. acatech—Deutsche Akademie der Technikwissenschaften e.V., München/Garching
Goltz U et al (2015) Design for future: managed software evolution. In: Glesner S (ed) Computer science—research and development. Springer, Heidelberg and Berlin
Hu F et al (2016) Robust cyber-physical systems: concept, models and implementation. In: Future generation computer systems, vol 56, Elsevier, Amsterdam pp 449–475
Huber A (2013) Das Ziel Digital Enterprise: die professionelle digitale Abbildung von Produktentwicklung und Produktion. In: Industry 4.0. Springer, Berlin, pp 111–124
Karnouskos S (2011). Stuxnet worm impact on industrial cyber-physical system security. In: 37th Annual Conference of the IEEE Industrial Electronics Society (IECON 2011), 7–10 Nov 2011, Melbourne, Australia
Koscher K et al (2010) Experimental security analysis of a modern automobile. In: Proceedings of the 31st IEEE symposium on security and privacy
Leavitt N (2010) Researchers fight to keep implanted medical devices save from hackers. Computer 34(8):11–14
Mills E (2009) Hackers broke into FAA air traffic control systems. The Wall Street Journal, p A6
Müller-Schloer et al (2004) Organic computing. Informatik-Spektrum, vol 27, 4, 332–336
O’Connell K (2008). CIA Report: cyber extortionists attacked foreign power grid, disrupting delivery. Internet Business Law Services
Siemens (2008) Security concept PCS 7 and WinCC. https://support.industry.siemens.com/cs/document/26462131/whitepaper-security-concept-pcs-7-and-wincc-basic-document?dti=0&lc=en-WW. Accessed 18 Jan 2017
Siemens (2016) Security concept for process and discrete industries. http://www.industry.siemens.com/topics/global/en/industrial-security/Documents/Whitepaper_Security_2016_V10_EN.pdf. Accessed 18 Jan 2017
Wan K et al (2010) Specification, analyzing challenges and approaches for cyber-physical systems (CPS). Eng Lett 18(3):308–315
Zimmerman C (2014) Ten strategies of a world-class cybersecurity operations center. The MITRE Corporation, Bedford
Author information
Authors and Affiliations
Corresponding author
Additional information
AIS Volume: Special issue: International Stability in a Digital World (ISDW)-volume to be allocated later.
Rights and permissions
About this article
Cite this article
Jansen, C., Jeschke, S. Mitigating risks of digitalization through managed industrial security services. AI & Soc 33, 163–173 (2018). https://doi.org/10.1007/s00146-018-0812-1
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00146-018-0812-1