Abstract
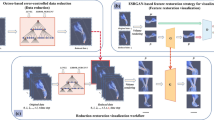
Analyzing and processing various data types in a privacy-preserving perspective has been researched in many disciplines; however, such an issue draws very limited attention in the research field of scientific visualization. We wondered if it is possible to delegate the rendering of a volume data set to a remote server(s) while still being able to preserve its privacy to certain extent. This paper presents a block-based volume data transformation algorithm that obfuscates a volume data set so as to reduce the user’s privacy concern when the volume data set is to be uploaded to a remote server. In addition, a privacy-aware transfer function adjustment is proposed so that not only the privacy is protected during the rendering process, but also the computational loading could be leveraged to the server side as much as possible. Experimental results show that the proposed method yields visually satisfactory results compared with a normal direct volume rendering approach. Moreover, the decrease of the rendering efficiency caused by the proposed method is still controlled within an acceptable range. A case study proves that the proposed approach can be adopted in practice. This work explores the possibility of rendering a volume data set through remote server(s) while the privacy of data is still maintained.













Similar content being viewed by others
References
Chu, K.Y., Kuo, Y.H., Hsu, W.H.: Real-time privacy-preserving moving object detection in the cloud. In: Proceedings of the 21st ACM International Conference on Multimedia, MM ’13, pp. 597–600 (2013)
Dasgupta, A., Kosara, R.: Adaptive privacy-preserving visualization using parallel coordinates. IEEE Trans. Vis. Comput. Graph. 17(12), 2241–2248 (2011)
Dasgupta, A., Kosara, R.: Privacy-preserving data visualization using parallel coordinates, pp. 78,680O–1–78,680O–12 (2011)
Demaine, E.D., Demaine, M.L.: Jigsaw puzzles, edge matching, and polyomino packing: connections and complexity. Graphs Comb. 23, 195–208 (2007)
Devore, J.L.: Probability and statistics for engineering and the sciences, 2nd edn. Brooks/Cole Publishing Company, USA (1987)
Erkin, Z., Piva, A., Katzenbeisser, S., Lagendijk, R.L., Shokrollahi, J., Neven, G., Barni, M.: Protection and retrieval of encrypted multimedia content: when cryptography meets signal processing. EURASIP J. Inf. Secur. 7(2), 1–20 (2007)
Fontaine, C., Galand, F.: A survey of homomorphic encryption for nonspecialists. EURASIP J. Inf. Secur (2007)
Gautam, A., Panwar, M., Gupta, P.: A new image encryption approach using block based transformation algorithm. Int. J. Adv. Eng. Sci. Technol. 8(1), 90–96 (2011)
Gentry, C.: Computing arbitrary functions of encrypted data. Commun. ACM 53(3), 97–105 (2010)
Jolfaei, A., Mirghadri, A.: An image encryption approach using chaos and stream cipher. J. Theor. Appl. Inf. Technol. 19(2), 117–125 (2010)
Koller, D., Turitzin, M., Levoy, M., Tarini, M., Croccia, G., Cignoni, P., Scopigno, R.: Protected interactive 3d graphics via remote rendering. ACM Trans. Graph. 23(3), 695–703 (2004). doi:10.1145/1015706.1015782
Levoy, M.: Display of surfaces from volume data. IEEE Comput. Graph. Appl. 8(3), 29–37 (1988)
Lin, S.C., Lin, K.J., Hsiao, I.T., Hsieh, C.J., Lin, W.Y., Lu, C.S., Wey, S.P., Yen, T.C., Kung, M.P., Weng, Y.H.: In vivo detection of monoaminergic degeneration in early Parkinson disease by 18F-9-fluoropropyl-(+)-dihydrotetrabenzazine PET. J. Nucl. Med. 55(1), 73–79 (2013)
Liu, W., Zhao, C.: Digital watermarking for volume data based on 3D-DWT and 3D-DCT. In: Proceedings of the 2nd International Conference on Interaction Sciences: Information Technology, Culture and Human, ICIS ’09, pp. 352–357 (2009)
Machanavajjhala, A., Kifer, D., Gehrke, J., Venkitasubramaniam, M.: l-diversity: privacy beyond k-anonymity. ACM Trans. Knowl. Discov. Data 1(1) (2007)
Melchor, C.A., Fau, S., Fontaine, C., Gogniat, G., Sirdey, R.: Recent advances in homomorphic encryption: a possible future for signal processing in the encrypted domain. IEEE Signal Process. Mag. 30(2), 108–117 (2013)
Mitra, A., Rao, Y.V.S., Prasanna, S.R.M.: A new image encryption approach using combinational permutation techniques. J. Comput. Sci. 1(1), 127–131 (2006)
Mohanty, M., Atrey, P., Ooi, W.T.: Secure cloud-based medical data visualization. In: Proceedings of the 20th ACM International Conference on Multimedia, MM ’12, pp. 1105–1108 (2012)
Mohanty, M., Ooi, W.T., Atrey, P.K.: Secure cloud-based volume ray-casting. CloudCom 1, 531–538 (2013)
Naehrig, M., Lauter, K., Vaikuntanathan, V.: Can homomorphic encryption be practical? In: Proceedings of the 3rd ACM Workshop on Cloud Computing Security Workshop, CCSW ’11, pp. 113–124 (2011)
Pitman, J.: Probability. Springer (texts in statistics) (1993)
Shamir, A.: How to share a secret. Commun. ACM 22(11), 612–613 (1979)
Sweeney, L.: k-anonymity: a model for protecting privacy. Int. J. Uncertain. Fuzziness Knowl. Based Syst. 10(5), 557–570 (2002)
Wu, Y., Guan, X., Kankanhalli, M.S., Huang, Z.: Robust invisible watermarking of volume data using the 3D DCT. In: Computer Graphics International 2001, CGI ’01, pp. 359–362 (2001)
Yao, A.C.: Protocols for secure computations. In: Proceedings of the 23rd Annual Symposium on Foundations of Computer Science, SFCS ’82, pp. 160–164 (1982)
Younes, M.A.B., Jantan, A.: An image encryption approach using a combination of permutation technique followed by encryption. Int. J. Comput. Sci. Netw. Secur. 8(4), 191–197 (2008)
Acknowledgments
This paper is partially sponsored by the Ministry of Science and Technology, Taiwan (Grant Number: 104-2917-I-564-068 and 101-2221-E-011-150-MY3). The authors thank the anonymous reviewers for providing helpful comments to make this paper better presented. The authors would also like to thank professor Kwan-Liu Ma and his research team at UC Davis for providing the volume rendering toolkit to help the authors have a good head start. Thanks Nick Leaf and Hendrik Schroots for proof-reading the paper. In addition, the authors also thank professor Ing-Tsung Hsiao from Chang Gung University for providing his expertise to help us conduct and verify the case study.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Funding
This study is partially funded by the Ministry of Science and Technology, Taiwan (grant number 104-2917-I-564-068 and 101-2221-E-011-150-MY3).
Electronic supplementary material
Below is the link to the electronic supplementary material.
Rights and permissions
About this article
Cite this article
Chou, JK., Yang, CK. Obfuscated volume rendering. Vis Comput 32, 1593–1604 (2016). https://doi.org/10.1007/s00371-015-1143-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00371-015-1143-6