Abstract
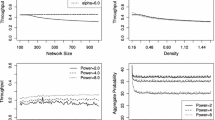
This article presents a simple local medium access control protocol, called Jade, for multi-hop wireless networks with a single channel that is provably robust against adaptive adversarial jamming. The wireless network is modeled as a unit disk graph on a set of nodes distributed arbitrarily in the plane. In addition to these nodes, there are adversarial jammers that know the protocol and its entire history and that are allowed to jam the wireless channel at any node for an arbitrary \((1-\epsilon )\)-fraction of the time steps, where \(0<\epsilon <1\) is an arbitrary constant. We assume that nodes can perform collision detection (unless they are transmitting themselves), but that they cannot distinguish between jammed transmissions and collisions of regular messages. Nevertheless, we show that Jade achieves an asymptotically optimal throughput by efficiently exploiting the unpredictable time periods in which the medium is available.

Similar content being viewed by others
Notes
In this article, disks (and later sectors) will refer both to 2-dimensional areas in the plane as well as to the set of nodes in the respective areas. The exact meaning will become clear in the specific context.
References
Alnifie, G., Simon, R.: A multi-channel defense against jamming attacks in wireless sensor networks. In: Proceedings of Q2SWinet ’07, pp. 95–104 (2007)
Awerbuch, B., Richa, A., Scheideler, C.: A jamming-resistant MAC protocol for single-hop wireless networks. In: Proceedings of PODC ’08 (2008)
Bayraktaroglu, E., King, C., Liu, X., Noubir, G., Rajaraman, R., Thapa, B.: On the performance of IEEE 802.11 under jamming. In: Proceedings of IEEE Infocom ’08, pp. 1265–1273 (2008)
Bender, M.A., Farach-Colton, M., He, S., Kuszmaul, B.C., Leiserson, C.E.: Adversarial contention resolution for simple channels. In: Proceedings of SPAA ’05 (2005)
Brown, T., James, J., Sethi, A.: Jamming and sensing of encrypted wireless ad hoc networks. In: Proceedings of MobiHoc ’06, pp. 120–130 (2006)
Chiang, J., Hu, Y.-C.: Cross-layer jamming detection and mitigation in wireless broadcast networks. In: Proceedings of MobiCom ’07, pp. 346–349 (2007)
Chlebus, B.S., Kowalski, D.R., Rokicki, M.A.: Adversarial queuing on the multiple-access channel. In: Proceedings of PODC ’06 (2006)
Czumaj, A., Rytter, W.: Broadcasting algorithms in radio networks with unknown topology. J. Algorithms 60(2), 115–143 (2006)
Dolev, S., Gilbert, S., Guerraoui, R., Kowalski, D., Newport, C., Kuhn, F., Lynch, N.: Reliable distributed computing on unreliable radio channels. In: Proceedings of the 2009 MobiHoc S3 Workshop (2009)
Dolev, S., Gilbert, S., Guerraoui, R., Kuhn, F., Newport, C.C.: The wireless synchronization problem. In: Proceedings of the 28th Annual ACM Symposium on Principles of Distributed Computing (PODC), pp. 190–199 (2009)
Dolev, S., Gilbert, S., Guerraoui, R., Newport, C.: Gossiping in a multi-channel radio network: An oblivious approach to coping with malicious interference. In: Proceedings of the Symposium on Distributed Computing (DISC) (2007)
Dolev, S., Gilbert, S., Guerraoui, R., Newport, C.: Secure communication over radio channels. In: Proceedings of the 27th ACM Symposium on Principles of Distributed Computing (PODC), pp. 105–114 (2008)
Dolev, S., Gilbert, S., Guerraoui, R., Newport, C.C.: Gossiping in a multi-channel radio network. In: Proceedings of the 21st International Symposium on Distributed Computing (DISC), pp. 208–222 (2007)
Gilbert, S., Guerraoui, R., Kowalski, D., Newport, C.: Interference-resilient information exchange. In: Proceedings of the 28th Conference on Computer Communications. IEEE Infocom 2009 (2009)
Gilbert, S., Guerraoui, R., Kowalski, D.R., Newport, C.C.: Interference-resilient information exchange. In: Proceedings of the 28th IEEE International Conference on Computer Communications (INFOCOM), pp. 2249–2257 (2009)
Gilbert, S., Guerraoui, R., Newport, C.: Of malicious motes and suspicious sensors: On the efficiency of malicious interference in wireless networks. In: Proceedings of OPODIS ’06 (2006)
Goldberg, L.A., Mackenzie, P.D., Paterson, M., Srinivasan, A.: Contention resolution with constant expected delay. J. ACM 47(6) 1048–1096 (2000). doi:10.1145/355541.355567
Håstad, J., Leighton, T., Rogoff, B.: Analysis of backoff protocols for mulitiple access channels. SIAM J. Comput. 25(4) 710–774 (1996). http://dx.doi.org/10.1137/S0097539792233828
Heusse, M., Rousseau, F., Guillier, R., Duda, A.: Idle sense: An optimal access method for high throughput and fairness in rate diverse wireless lans. In: Proceedings of SIGCOMM (2005)
IEEE: Medium access control (MAC) and physical specifications. In: IEEE P802.11/D10 (1999)
Jain, K., Padhye, J., Padmanabhan, V.N., Qiu, L.: Impact of interference on multi-hop wireless network performance. In: Proceedings of the 9th Annual International Conference on Mobile Computing and Networking (MobiCom), pp. 66–80 (2003)
Jiang, S., Xue, Y.: Providing survivability against jamming attack via joint dynamic routing and channel assigment. In: Proceedings of the 7th Workshop on Design of Reliable Communication Networks (DRCN) (2009)
Koo, C., Bhandari, V., Katz, J., Vaidya, N.: Reliable broadcast in radio networks: The bounded collision case. In: Proceedings of PODC ’06 (2006)
Kuhn, F., Moscibroda, T., Wattenhofer, R. Radio network clustering from scratch. In: Proceedings. of ESA ’04 (2004)
Kwak, B.-J., Song, N.-O., Miller, L.E.: Performance analysis of exponential backoff. IEEE/ACM Trans. Netw. 13(2), 343–355 (2005)
Law, Y., van Hoesel, L., Doumen, J., Hartel, P., Havinga, P.: Energy-efficient link-layer jamming attacks against wireless sensor network mac protocols. In: Proceedings of SASN ’05, pp. 76–88 (2005)
Li, M., Koutsopoulos, I., Poovendran, R.: Optimal jamming attacks and network defense policies in wireless sensor networks. In: Proceedings of Infocom ’07, pp. 1307–1315 (2007)
Liu, X., Noubir, G., Sundaram, R., Tan, S.: Spread: Foiling smart jammers using multi-layer agility. In: Proceedings of Infocom ’07, pp. 2536–2540 (2007)
Meier, D., Pignolet Y.A., Schmid S., Wattenhofer, R.: Speed dating despite jammers. In: Proceedings of DCOSS ’09 June (2009)
Navda, V., Bohra, A., Ganguly, S., Rubenstein, D.: Using channel hopping to increase 802.11 resilience to jamming attacks. In: Proceedings of Infocom’07, pp. 2526–2530 (2007)
Negi, R., Perrig, A.: Jamming Analysis of MAC Protocols. Technical Report. Carnegie Mellon University (2003)
Noubir, G.: On connectivity in ad hoc networks under jamming using directional antennas and mobility. In: Proceedings of the 2nd International Conference on Wired/Wireless Internet Communications (WWIC), pp. 186–200 (2004)
Pelc A., Peleg, D.: Feasibility and complexity of broadcasting with random transmission failures. In: Proceedings of PODC ’05 (2005)
Raghavan, P., Upfal, E.: Stochastic contention resolution with short delays. SIAM J. Comput. 28(2), 709–719 (1999)
Richa, A., Scheideler, C., Schmid, S., Zhang, J.: Competitive and fair medium access despite reactive jamming. In: Proceedings of the 31st International Conference on Distributed Computing Systems (ICDCS) (2011)
Richa, A., Scheideler, C., Schmid, S., Zhang, J.: Self-stabilizing leader election for single-hop wireless networks despite jamming. In: Proceedings of the 12th ACM International Symposium on Mobile Ad Hoc Networking and Computing (MobiHoc) (2011)
Schmidt, J., Siegel, A., Srinivasan, A.: Chernoff-Hoeffding bounds for applications with limited independence. SIAM J. Discrete Math. 8(2), 223–250 (1995)
Simon, M.K., Omura, J.K., Schultz, R.A., Levin, B.K.: Spread Spectrum Communications Handbook. McGraw-Hill, New York (2001)
Thuente, D., Acharya, M. Intelligent jamming in wireless networks with applications to 802.11b and other networks. In: Proceedings of MILCOM ’06 (2006)
van de Ven, P.M., Janssen, A.J.E.M., van Leeuwaarden, J.S.H., Borst, S.C.: Achieving target throughputs in random-access networks. Perform. Eval. 68, 1103–1117 (2011)
Wood, A., Stankovic, J., Zhou, G. DEEJAM: Defeating energy-efficient jamming in IEEE 802.15.4-based wireless networks. In: Proceedings of SECON ’07 (2007)
Xu, W., Ma, K., Trappe, W., Zhang, Y.: Jamming sensor networks: attack and defense strategies. IEEE Netw. 20(3), 41–47 (2006)
Xu, W., Trappe, W., Zhang, Y., Wood, T.: The feasibility of launching and detecting jamming attacks in wireless networks. In: Proceedings of MobiHoc ’05, pp. 46–57 (2005)
Xu, W., Wood, T., Zhang, Y.: Channel surfing and spatial retreats: defenses against wireless denial of service. In: Proceedings of Workshop on Wireless Security (2004)
Ye, S., Wang, Y., Tseng, Y. A jamming-based MAC protocol for wireless multihop ad hoc networks. In: Proceedings of the IEEE 58th Vehicular Technology Conference (2003)
Ye, S.-R., Wang, Y.-C., Tseng, Y.-C.: A jamming-based MAC protocol to improve the performance of wireless multihop ad-hoc networks. Wirel. Commun. Mob. Comput. 4(1), 75–84 (2004)
Zander, J.: Jamming in slotted ALOHA multihop packed radio networks. IEEE Trans. Netw. 39(10), 1525–1531 (1991)
Author information
Authors and Affiliations
Corresponding author
Additional information
A preliminary version of this article appeared at the 24th International Symposium on Distributed Computing (DISC), 2010. Research is partly supported by NSF grants CCF-1116368 and CCF-0830704, as well as by DFG grants DFG SFB 901 and DFG SCHE 1592/2-1.
Rights and permissions
About this article
Cite this article
Richa, A., Scheideler, C., Schmid, S. et al. Competitive throughput in multi-hop wireless networks despite adaptive jamming. Distrib. Comput. 26, 159–171 (2013). https://doi.org/10.1007/s00446-012-0180-x
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00446-012-0180-x