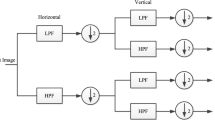
Abstract
Image steganography is the process of sending messages secretly by hiding the message in image content. Steganalytic techniques are used to detect whether an image contains a hidden message by analyzing various image features between stego-images (the images containing hidden messages) and cover-images (the images containing no hidden messages). In the past, genetic algorithm (GA) was applied to design a robust steganographic system that breaks the steganalytic systems. However, GA consumes too much time to converge to the optimal solution. In this paper, we use a different evolutionary approach, named differential evolution (DE), to increase the performance of the steganographic system. The key element that DE is distinguished from other population based approaches is differential mutation, which aims to find the global optimum of a multidimensional, multimodal function. Experimental results show that the application of the DE based steganography not only improves the peak signal to noise ratio (PSNR) of the stego-image, but also promotes the normalized correlation (NC) of the extracted secret message for the same number of iterations. It is observed that the percentage increase in PSNR values ranges from 5% to 13% and that of NC values ranges from 0.8% to 3%.
Similar content being viewed by others
References
Avcibas I, Memon N, Sankur B (2003) Steganalysis using image quality metrics. IEEE Trans Image Process 12(2): 221–229
Beyer H, Schwefel H (2004) Evolution strategies—a comprehensive introduction. Nat Comput 1: 3–52
Chang FC, Huang HC, Hang HM (2007) Layered access control schemes on watermarked scalable media. J VLSI Signal Process Syst Signal Image Video Technol 49(3): 443–455
Cox IJ, Miller M, Bloom J (2001) Digital watermarking: principles & practice. Morgan Kaufmann, Menlo Park
Fridrich J, Goljan M, Hogea D (2003) New methodology for breaking steganographic techniques for JPEGs. In: Proc. of SPIE Electronic Imaging, Santa Clara, CA, pp 143–155
Holland JH (1975) Adaptation in natural and artificial systems. The University of Michigan Press, Ann Arbor
Karboga D, Okdem S (2004) A simple and global optimization algorithm for engineering problems: differential evolution algorithm. Turk J Electr Eng Comput Sci 12(1): 53–60
Kessler GC (2004) An overview of steganography for the computer forensics examiner. Forensic Sci Commun 6(3): 1–29
Pan JS, Huang HC, Jain LC (eds) (2004) Intelligent watermarking techniques. World Scientific Publishing Company, Singapore
Price K, Storn R, Lampinen J (2005) Differential evolution: a practical approach to global optimization. Springer, Berlin
Provos N, Honeyman P (2003) Hide and seek: an introduction to steganography. IEEE Secur Priv Mag 1(3): 32–44
Shieh CS, Huang HC, Wang FH, Pan JS (2004) Genetic watermarking based on transform domain techniques. Pattern Recognit 37(3): 555–565
Shih FY (2007) Digital watermarking and steganography: fundamentals and techniques. CRC Press, Boca Raton
Wayner P (2002) Disappearing cryptography: information hiding: steganography and watermarking, 2nd edn. Morgan Kaufmann, San Francisco
Westfeld A, Pfitzmann A (1999a) Attacks on steganographic systems breaking the steganographic utilities Ezstego, Jsteg, Steganos and S-tools and some lessons learned. In: Proc. of Third Intl. Workshop on Information Hiding, Dresden, Germany, pp 61–76
Westfeld A, Pfitzmann A (1999b) Attacks on steganographic systems. In: Proc. of Third Intl. Workshop on Information Hiding, Lecture Notes in Computer Science. Springer, Berlin, vol 1768, pp 61–76
Wu Y, Shih FY (2006) Genetic algorithm based methodology for breaking the steganalytic systems. IEEE Trans Syst Man Cybern 36(1): 24–29
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Shih, F.Y., Edupuganti, V.G. A differential evolution based algorithm for breaking the visual steganalytic system. Soft Comput 13, 345–353 (2009). https://doi.org/10.1007/s00500-008-0330-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-008-0330-z