Abstract
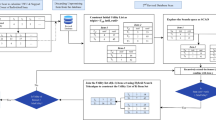
Association rule mining (ARM) is a well-known data mining scheme that is used to discover the commonly co-occurred itemsets from the transactional datasets. Two considerable steps of ARM are frequent item recognition and association rule generation. Minimum support and confidence measures are used in the generation of association rules. Many algorithms have been projected by the researchers to generate association rules. Fuzzy logic is incorporated to uncover the recurrent itemsets and interesting fuzzy association rules. In general, huge volume of datasets could be analyzed which in turn needs more number of database scans. In addition to this, all the transactions and items are not required for data analysis. Hence, the first step of this research work uses a dimensionality reduction technique which drastically reduces the size of the data set. This dimensionality reduction technique uses low variance and hash table methods. The proposed algorithm effectively identifies the significant transactions and items from the database. The issues of dimensionality reduction appear when the items in the databases are higher dimension than endure. The proposed algorithm reduces the irrelevant items and transactions from the transactional database. The proposed dimensionality reduction technique dimensionality reduction in transactions and items is compared with the extend frequent pattern (EFP) and intersection set theory EFP and dimensionality reduction using frequency count. Item reduction, transaction reduction, execution time and memory space are the performance factors. Second step proposes fuzzy and whale optimization for frequent item identification and association rule generation. The efficiency of the proposed algorithm is compared with particle swarm optimization genetic algorithm and fuzzy frequent itemset-Miner. Performance metrics used in this step are number of frequent items, association rules generated, execution time and memory required. Experimental results proved that the proposed techniques have produced the good results.














Similar content being viewed by others
References
Agrawal R, Mannila H, Srikant R, Toivonen H, Verkamo AI (1996) Fast discovery of association rules. Adv Knowl Discov Data Min 12(1):307–328
Alotaibi K, Rayward-Smith VJ, de la Iglesia B (2011) Non-metric multidimensional scaling for privacy-preserving data clustering. In: International conference on intelligent data engineering and automated learning. Springer, Berlin, pp 287–298
Chen G, Wei Q, Kerre E, Wets G (2008) Introduction the fuzzy association rules. In: Proceeding of Indiacom
Corcoran L, Sen S (1994) Using real-valued genetic algorithms to evolve rule sets for classification. In: Proceedings of 1st IEEE international conference on evolutionary computation, Orlando, FL, June 27–29, pp 120–124
Danaee S, Darakeh F, Mohammad-Khani G-R (2018) Applying an ANFIS-based algorithm in comparison with mechanistic modelling in a biofilter treating hexane. J Green Eng 8(3):319–338
Gkoulalas-Divanis A, Verykios VS (2009) An overview of privacy preserving data mining. XRDS Crossroads ACM Mag Stud 15(4):23–26
Joseph SI, Thanakumar I (2019) Survey of data mining algorithm’s for intelligent computing system. J Trends Comput Sci Smart Technol (TCSST). 1(01):14–24
Kapila D, Chopra V (2015) A survey on different fuzzy association rule mining techniques. Int J Technol Res Eng 2(9):2001–2007
Lin JCW, Li T, Fournier-Viger P, Hong TP (2015) A fast algorithm for mining fuzzy frequent itemsets. J Intell Fuzzy Syst 29(6):2373–2379
Mankad KB (2013) A genetic fuzzy approach to measure multiple intelligence
Mohamed SR, Raviraj P (2020) Optimisation of multi-body fishbot undulatory swimming speed based on SOLEIL and BhT simulators. Int J Intell Sustain Comput 1(1):19
Moustafa A, Abuelnasr B, Abougabal MS (2015) Efficient mining fuzzy association rules from ubiquitous data streams. Alexandr Eng J 54(2):163–174
Mukherjee D, Reddy BVR (2020) Design and development of a novel MOSFET structure for reduction of reverse bias PN junction leakage current. Int J Intell Sustain Comput 1(1):32
Mustafa A, Abuelnasr B, Abougabal MS (2015) Efficient mining fuzzy association rules from ubiquitous data streams. Alexandr Eng J 54:163–174
Muyeba M, Khan MS, Coenen F (2008) A framework for mining fuzzy association rules from composite items. In: Pacific-Asia conference on knowledge discovery and data mining. Springer, Berlin, pp 62–74
Nath B et al (2007) Frequency count based filter for dimensionality reduction. In: 15th international conference on advanced computing and communications. https://doi.org/10.1109/adcom.2007.113
Pandya B, Singh UK, Dixit K (2014) A study of projection based multiplicative data perturbation for privacy preserving data mining. Int J Appl Innov Eng Manag 3(11):180–182
Pedersen TB, Saygın Y, Savas E (2008) Secret sharing vs.encryption-based techniques for privacy preserving data mining. Future and Emerging Technologies under IST-014915 GeoPKDD project.Corpus ID: 17401136
Prabamanieswari R (2013) A combined approach for mining fuzzy frequent itemset. Int J Comput Appl 975:8887
Prajapati DJ, Garg S, Chauhan NC (2017) Interesting association rule mining with consistent and inconsistent rule detection from big sales data in distributed environment. Fut Comput Inf J 2(1):19–30
Qi X, Zong M (2012) An overview of privacy preserving data mining. Proc Environ Sci 12:1341–1347
Radha P, MeenaPreethi B (2019) Machine learning approaches for disease prediction from radiology and pathology reports. J Green Eng 9(2):149–166
Rajak A, Gupta MK (2008) Association rule mining: applications in various areas. In: Proceedings of international conference on data management, Ghaziabad, India, pp 3–7
Sasikala IS, Banu N (2014) Privacy preserving data mining using piecewise vector quantization (PVQ). Int J Adv Res Comput Sci Technol 2(3):302–306
Selvaraj J, Mohammed AS (2020) Mutation-based PSO techniques for optimal location and parameter settings of STATCOM under generator contingency. Int J Intell Sustain Comput 1(1):53
Shakya S, Pulchowk LN (2020) Intelligent and adaptive multi-objective optimization in WANET using bio inspired algorithms. J Soft Comput Paradigm (JSCP) 2(01):13–23
Shang X, Sattler KU, Geist I (2004) SQL based frequent pattern mining with FP-growth. In: Applications of declarative programming and knowledge management. Springer, Berlin, pp 32–46
Singh SK, Wayal G, Sharma N (2012) A review: data mining with fuzzy association rule mining. Int J Eng Res Technol 1(5):1–4
Siraj MM, Rahmat NA, Din MM (2019) A survey on privacy preserving data mining approaches and techniques. In: Proceedings of the 2019 8th international conference on software and computer applications, pp 65–69
Sridhar M, Babu BR (2012) A fuzzy approach for privacy preserving in data mining. Int J Comput Appl 57:18
Sufal D et al (2008) 2008 IEEE region 10 colloquium and the third ICIIS, Kharagpur, India, December 8–10
Tamilmani G, Sivakumari S (2020) Safe engineering application for detecting the brain tumor using grey wolf optimization technique. J Green Eng 10(5):1971–1983
Vijayakumar T (2019) Comparative study of capsule neural network in various applications. J Artif Intell 1(01):19–27
Vijayalakshmi P, YamunaDevi S (2017) Dimensionality reduction for privacy preserving data mining using random projection perturbation approach in outsourced environment. Int J Adv Res Comput Commun Eng 6:279–284
Wang L, Dong J-Y, Li S-L (2015a) Fuzzy inference algorithm based on quantitative association rules. Proc Comput Sci 61(2015):388–394
Wang L, Dong J-Y, Li S-L (2015b) Fuzzy inference algorithm based on quantitative association rules. Proc Comput Sci 61:388–394
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
All authors declare that they have no conflict of interest.
Additional information
Communicated by V. Loia.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Sharmila, S., Vijayarani, S. Association rule mining using fuzzy logic and whale optimization algorithm. Soft Comput 25, 1431–1446 (2021). https://doi.org/10.1007/s00500-020-05229-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-020-05229-4