Abstract
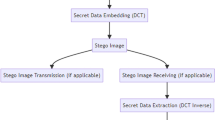
This paper proposes an adaptive fuzzy inference approach for color image steganography, taking into account the influence of image complexity such as pixel similarity, pixel brightness and color sensitivity. A fuzzy inference system is designed as a classifier which adopts the features of the cover image as its crisp input values and produces semantic concepts corresponding to the payload of image sub-classes. Furthermore, least significant bit substitution is used to hide the data adaptively according to the output of fuzzy inference system and the human eye sensitivity to the R, G, B color components. A chaotic method and random sequence scrambling are applied to the secret message to generate the random sequence which prevents the secret message from attackers. The proposed method hides a large amount of data with good quality of stego-image from the human visual system and guarantees the confidentiality in the communication. Experimental results show better mean square error, peak signal-to-noise ratio, structural similarity and payload, verifying that the proposed method can yield better performance than some state-of-the-art works. The robustness of the method is tested by RS steganalysis and pixel difference histogram analysis.
















Similar content being viewed by others
References
Al-Jbara HAG, Kiah LBM, Jalab HA (2012) Increased capacity of image based steganography using artificial neural network. AIP Conf Proc 1482:20–25
Ashraf Z, Roy ML, Muhuri PK, Lohani QMD (2020) Interval type-2 fuzzy logic system based similarity evaluation for image steganography. Heliyon 6:e03771
Aziz M, Tayarani-N MH, Afsar M (2015) A cycling chaos-based cryptic-free algorithm for image steganography. Nonlinear Dyn 80:1271–1290
Bandyopadhyay D, Dasgupta K, Mandal JK, Dutta P, Snášel V (2014) A framework of secured and bio-inspired image steganography using chaotic encryption with genetic algorithm optimization (CEGAO). Springer, Berlin
Bharati S, Rahman MA, Mandal S, Podder P (2018) Analysis of DWT, DCT, BFO & PBFO algorithm for the purpose of medical image watermarking. In: 2018 International Conference on Innovation in Engineering and Technology (ICIET), Dhaka, pp 1–6
Bharati S, Podder P, Mondal MRH (2020) Hybrid deep learning for detecting lung diseases from X-ray images. Inform Med Unlocked 20:100391
Bharati S, Khan TZ, Podder P, Hung NQ (2021) A comparative analysis of image denoising problem: noise models, denoising filters and applications. In: Hassanien AE, Khamparia A, Gupta D, Shankar K, Slowik A (eds) Cognitive Internet of Medical Things for Smart Healthcare: Services and Applications. Springer, Cham, pp 49–66
Chan CK, Cheng LM (2004) Hiding data in images by simple LSB substitution. Pattern Recognit 37:469–474
Cheddad A, Condell J, Curran K, Kevitt PM (2010) Digital image steganography: survey and analysis of current methods. Signal Process 90:727–752
Chen PY, Lin HJ (2006) A dwt based approach for image steganography. Int J Appl Sci Eng 4:275–290
Chen WJ, Chang CC, Le THN (2010) High payload steganography mechanism using hybrid edge detector. Expert Syst Appl 37:3292–3301
Chen WY (2008) Color image steganography scheme using DFT, SPIHT codec, and modified differential phase-shift keying techniques. Appl Math Comput 196:40–54
Cox IJ, Miller ML, Bloom JA, Fridrich J, Kalker T (2007) Digital watermarking and steganography. Morgan Kaufmann, San Francisco
Demirci R (2007) Similarity relation matrix-based color edge detection. AEU-Int J Electron Commun 61:469–477
El-Emam NN, Al-Diabat M (2015) A novel algorithm for colour image steganography using a new intelligent technique based on three phases. Appl Soft Comput 37:830–846
El-Emam NN, Al-Zubidy RAS (2013) New steganography algorithm to conceal a large amount of secret message using hybrid adaptive neural networks with modified adaptive genetic algorithm. J Syst Softw 86:1465–1481
Fridrich J, Goljan M, Du R (2001) Detecting LSB steganography in color and gray-scale images. IEEE Tranactionson Multimed 8:22–28
Gaurav K, Ghanekar U (2018) Image steganography based on canny edge detection, dilation operator and hybrid coding. J Inf Secur Appl 41:41–51
Guan ZH, Huang F, Guan W (2005) Chaos-based image encryption algorithm. Phys Lett A 346:153–157
Hayat AD, Ahmed AA (2016) A steganography embedding method based on edge identification and XOR coding. Expert Syst Appl 46:293–306
Hong W, Chen TS (2012) A novel data embedding method using adaptive pixel pair matching. IEEE Trans Inf Forensics Secur 7:176–184
Hussain M, Wahid A, Idris Y, Ho A, Jung KH (2018) Image steganography in spatial domain: a survey. Signal Process Image Commun 65:46–66
Jassim FA (2013) A novel steganography algorithm for hiding text in image using five modulus method. Int J Comput Appl 72:39–44
Kadhim IJ, Premaratne P, Vial PJ, Halloran B (2019) Comprehensive survey of image steganography: techniques, evaluations, and trends in future research. Neurocomputing 335:299–326
Kalita M, Tuithung T, Majumder S (2019) An adaptive color image steganography method using adjacent pixel value differencing and LSB substitution technique. Cryptologia 43:414–437
Kaur M, Juneja M (2017) Adaptive block based steganographic model with dynamic block estimation with fuzzy rules. Springer, Singapore
Kawaguchi E, Eason RO (1999) Principles and applications of BPCS steganography. In: Tescher AG, Vasudev B, Bove VM, Derryberry B (eds) Multimed Syst Appl. SPIE, Bellingham, pp 464–473
Khamparia A, Bharati S, Podder P, Gupta D, Khanna A, Phung TK, Thanh DNH (2021) Diagnosis of breast cancer based on modern mammography using hybrid transfer learning. Multidimens Syst Signal Process. https://doi.org/10.1007/s11045-020-00756-7
Koptyra K, Ogiela MR (2019) Multiply information coding and hiding using fuzzy vault. Soft Comput 23:4357–4366
Kumar S, Singh A, Kumar M (2019) Information hiding with adaptive steganography based on novel fuzzy edge identification. Def Technol 15:162–169
Laishram D, Tuithung T (2021) A novel minimal distortion-based edge adaptive image steganography scheme using local complexity. Multimed Tools Appl 80:831–854
Lee YP, Lee JC, Chen WK, Chang KC, Su IJ, Chang CP (2012) High-payload image hiding with quality recovery using tri-way pixel-value differencing. Inf Sci 191:214–225
Li J, Li X, Yang B (2013) Reversible data hiding scheme for color image based on prediction-error expansion and cross-channel correlation. Signal Process 93:2748–2758
Martino FD, Loia V, Perfilieva I, Sessa S (2008) An image coding/decoding method based on direct and inverse fuzzy transforms. Int J Approx Reason 48:110–131
Microchip G (2002) gm6010/gm6015 programming guide. Genesis Microchip Company, California US
Muhammad K, Jan Z, Ahmad J, Khan Z (2015) An adaptive secret key-directed cryptographic scheme for secure transmission in wireless sensor networks. Tech J Univ Eng Technol Taxila 20:48–53
Muhammad K, Ahmad J, Rehman NU, Jan Z, Sajjad M (2017) CISSKA-LSB: color image steganography using stego key-directed adaptive LSB substitution method. Multim Tools Appl 76:8597–8626
Noda H, Niimi M, Kawaguchi E (2006) High-performance JPEG steganography using quantization index modulation in DCT domain. Pattern Recognit Lett 27:455–461
Ou B, Li X, Zhao Y, Ni R (2015) Efficient color image reversible data hiding based on channel-dependent payload partition and adaptive embedding. Signal Process 108:642–657
Pak C, Kim J, An K, Kim C, Kim K, Pak C (2020) A novel color image LSB steganography using improved 1D chaotic map. Multimed Tools Appl 79:1409–1425
Pareek NK, Patidar V, Sud KK (2006) Image encryption using chaotic logistic map. Image Vision Comput 24:926–934
Pradhan A, Sahu AK, Swain G, Sekhar KR (2016) Performance evaluation parameters of image steganography techniques. In: 2016 International Conference on Research Advances in Integrated Navigation Systems (RAINS). IEEE, Bangalore, pp 1–8
Sajasi S, Moghadam AME (2013) A high quality image steganography scheme based on fuzzy inference system. In: 2013 13th Iranian Conference on Fuzzy Systems (IFSC). IEEE, Qazvin, pp 1–6
Shah PD, Bichkar RS (2018) A secure spatial domain image steganography using genetic algorithm and linear congruential generator. In: Dash S, Das S, Panigrahi B (eds) Int Conf Intell Comput Appl. Springer, Singapore, pp 119–129
Sharp T (2001) An implementation of key-based digital signal steganography. In: International Workshop on Information Hiding. Springer, Berlin, pp 13–26
Sivanandam N, Sai S, Deepa SN (2007) Introduction to fuzzy logic using MATLAB. Springer, Berlin
Swain G (2018) Adaptive and non-adaptive PVD steganography using overlapped pixel blocks. Arab J Sci Eng 43:7549–7562
Swain G (2019) Very high capacity image steganography technique using quotient value differencing and LSB substitution. Arab J Sci Eng 44:2995–3004
Toony Z, Sajedi H, Jamzad M (2009) A high capacity image hiding method based on fuzzy image coding/decoding. In: 2009 14th International CSI Computer Conference. IEEE, Tehran, pp 518–523
Vanmathi C, Prabu S (2018) Image steganography using fuzzy logic and chaotic for large payload and high imperceptibility. Int J Fuzzy Syst 20:460–473
Wu DC, Tsai WH (2003) A steganographic method for images by pixel-value differencing. Pattern Recognit Lett 24:1613–1626
Yuan YH (2016) Research on significance detection method based on RGB visual sensitivity. Dissertation, University of Shandong, in Chinese
Acknowledgements
This paper would like to thank the editors and the anonymous referees for their professional comments, which improved the quality of the manuscript. This work was supported in part by the National Natural Science Foundation of China (No. 11371130, 12071179), Soft science research program of Fujian Province (No. B19085), the project of Education Department of Fujian Province (No. JT180263), the Youth Innovation Fund of Xiamen City (3502Z20206020), the open fund of Key Laboratory of Applied Mathematics of Fujian Province University (Putian University) (No. SX201906) and Digital Fujian big data modeling and intelligent computing institute, Pre-Research Fund of Jimei University.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
All authors declare that they have no conflict of interest.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Informed consent
Informed consent was obtained from all individual participants included in the study.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Tang, L., Wu, D., Wang, H. et al. An adaptive fuzzy inference approach for color image steganography. Soft Comput 25, 10987–11004 (2021). https://doi.org/10.1007/s00500-021-05825-y
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-021-05825-y