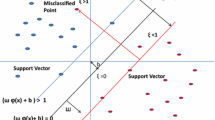
Abstract
Intrusion detection is very serious issue in these days because the prevention of intrusions depends on detection. Therefore, accurate detection of intrusion is very essential to secure information in computer and network systems of any organization such as private, public, and government. Several intrusion detection approaches are available but the main problem is their performance, which can be enhanced by increasing the detection rates and reducing false positives. This issue of the existing techniques is the focus of research in this paper. The poor performance of such techniques is due to raw dataset which confuse the classifier and results inaccurate detection due to redundant features. The recent approaches used principal component analysis (PCA) for feature subset selection which is based on highest eigenvalues, but the features corresponding to the highest eigenvalues may not have the optimal sensitivity for the classifier due to ignoring many sensitive features. Instead of using traditional approach of selecting features with the highest eigenvalues such as PCA, this research applied a genetic algorithm to search the genetic principal components that offers a subset of features with optimal sensitivity and the highest discriminatory power. The support vector machine (SVM) is used for classification purpose. This research work used the knowledge discovery and data mining cup dataset for experimentation. The performance of this approach was analyzed and compared with existing approaches. The results show that proposed method enhances SVM performance in intrusion detection that outperforms the existing approaches and has the capability to minimize the number of features and maximize the detection rates.






Similar content being viewed by others
References
Ahmad I (2011) Feature subset selection in intrusion detection using soft computing techniques. PhD thesis, Universiti Teknologi Petronas (UTP), Perak, Malaysia
Ahmad I (2012) Feature subset selection in intrusion detection. LAP Lambert Academic Publishing AG & Co, Germany
Ahmad I, Abdullah A, Alghamdi A, Hussain M (2011) Optimized intrusion detection mechanism using soft computing techniques. Telecommun Syst J. doi:10.1007/s11235-011-9541-1
Ahmad I, Abdullah A, Alghamdi A, Hussain M, Nafjan K (2011) Intrusion detection using feature subset selection based on MLP. Sci Res Essays 6(34):6804–6810
Liu G, Yi Z, Yang S (2007) A hierarchical intrusion detection model based on the PCA neural networks. Neurocomputing 70(7–9):1561–1568
Horng S, Ming-Yang S, Yuan-Hsin C, Tzong-Wann K, Rong-Jian C, Jui-Lin L, Citra Dwi P (2011) A novel intrusion detection system based on hierarchical clustering and support vector machines. Expert Syst Appl 38(1):306–313
Tong X, Wang Z, Haining Y (2009) A research using hybrid RBF/Elman neural networks for intrusion detection system secure model. Comput Phys Commun 180(10):1795–1801
Eid HF, Darwish A, Hassanien AE, Abraham A (2010) Principle components analysis and support vector machine based intrusion detection system. In: 10th international conference on intelligent systems design and applications (ISDA), Cairo, Egypt, pp 363–367
Cao LJ, Chua KS, Chong WK, Lee HP, Gu QM (2003) A comparison of PCA, KPCA and ICA for dimensionality reduction in support vector machine. Neurocomputing 55(1–2):321–336
Sun Z, Bebis B, Miller R (2004) Object detection using feature subset selection. Pattern Recognit 37(11):2165–2176
Hussain M, Wajid SK, Elzaart A, Berbar M (2011) A comparison of SVM kernel functions for breast cancer detection. In: 8th IEEE international conference on computer graphics, imaging and visualization (CGIV), pp 145–150
Yang S, Bebis G, Hussain M, Muhammad G, Mirza A (2013) Unsupervised discovery of visual face categories. Int J Artif Intell Tools 22(01):1250029-1–1250029-30. doi:10.1142/S0218213012500297
Vapnik V (1995) Statistical learning theory. Springer, New York
Boser BE,Guyon IM, Vapnik V (1992) A training algorithm for optimal margin classifiers. In: Proceedings of the 5th annual workshop on computational learning theory, pp 144–152
Burges C (1998) Tutorial on support vector machines for pattern recognition. Data Min Knowl Discov 2(2):955–974
Kim D, Nguyen H, Syng-Yup O, Jong SP (2005) Fusions of GA and SVM for anomaly detection in intrusion detection system, advances in neural networks, vol 3498. Lecture Notes in Computer Science, pp 415–420
Gao M, Tian J, Xia M (2009) Intrusion detection method based on classify support vector machine. In: Presented in the proceedings of the second international conference on intelligent computation technology and automation. IEEE Computer Society, Washington, DC, pp 391–394
Ahmad I, Abdullah A, Alghamdi A, Hussain M (2011) Denial of service attack detection using support vector machine. J Inf Tokyo 14(1):127–134
Ahmad I, Abdullah A, Alghamdi A (2009) Application of artificial neural network in detection of DOS attacks. In: Proceedings of the 2nd international conference on security of information and networks (SIN ’09), Famagusta, North Cyprus. ACM, New York, pp 229–234
Zargar G, Kabiri P(2010) Selection of effective network parameters in attacks for intrusion detection, advances in data mining. Applications and theoretical aspects, vol 6171. Lecture Notes in Computer Science, pp 643–652
Osareh A, Shadgar B (2008) Intrusion detection in computer networks based on machine learning algorithms. Int J Comput Sci Netw Secur (IJCSNS) 8(11):15–23
Lakhina S, Joseph S, Verma B (2010) Feature reduction using principal component analysis for effective anomaly-based intrusion detection on NSL–KDD. Int J Eng Sci Technol 2(6):1790–1799
Amini M, Jalili R, Shahriari H (2006) RT–UNNID: a practical solution to real-time network-based intrusion detection using unsupervised neural networks. Comput Appl Secur 25(6):459–468
Acknowledgment
The authors extend their appreciation to the College of Computer & Information Sciences Research Center, Deanship of Scientific Research, King Saud University, Saudi Arabia for funding this research work. The authors are grateful for this support.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Ahmad, I., Hussain, M., Alghamdi, A. et al. Enhancing SVM performance in intrusion detection using optimal feature subset selection based on genetic principal components. Neural Comput & Applic 24, 1671–1682 (2014). https://doi.org/10.1007/s00521-013-1370-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00521-013-1370-6