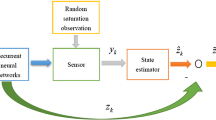
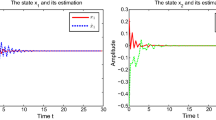
Abstract
This paper investigates the outlier-resistant variance-constrained \(H_{\infty }\) state estimation problem for a class of discrete time-varying recurrent neural networks with randomly occurring deception attacks. The randomly occurring deception attacks are modeled by a series of random variables satisfying the Bernoulli distribution with known probability. In addition, the saturation function is introduced to reduce the negative impact from the measurement outliers onto the estimation performance. The objective of this paper is to propose an outlier-resistant finite-horizon state estimation scheme without utilizing the augmentation method such that, in the presence of measurement outliers and randomly occurring deception attacks, some sufficient criteria are obtained ensuring both the desired \(H_{\infty }\) performance index and the error variance boundedness. Finally, a numerical example is used to illustrate the feasibility of the presented outlier-resistant variance-constrained \(H_{\infty }\) state estimation algorithm.







Similar content being viewed by others
Data Availability
Data sharing is not applicable to this article as no new data were created or analyzed in this study.
References
Sakthivel R, Aravinth N, Aouiti C, Arumugam K (2021) Finite-time synchronization of hierarchical hybrid coupled neural networks with mismatched quantization. Neural Comput Appl 33(24):16881–16897
Dong L, Zhang H, Yang K, Zhou D, Shi J, Ma J (2022) Crowd counting by using Top-k relations: a mixed ground-truth CNN framework. IEEE Trans Consum Electron 68(3):307–316
Morocho-Cayamcela ME, Lim W (2021) Pattern recognition of soldier uniforms with dilated convolutions and a modified encoder-decoder neural network architecture. Appl Artif Intell 35(6):476–487
Vladimir G, Yury M, Natalya K (2022) Pattern recognition techniques for classifying aeroballistic flying vehicle paths. Neural Comput Appl 34(5):4033–4045
Liao M, Wang C, Sun Y, Lin H, Xu C (2022) Memristor-based affective associative memory neural network circuit with emotional gradual processes. Neural Comput Appl 34(16):12667–13682
Zhou Y, Jiao X (2021) Intelligent analysis system for signal processing tasks based on LSTM recurrent neural network algorithm. Neural Comput Appl. https://doi.org/10.1007/s00521-021-06478-6
-Blanco EF, Rivero D, Pazos A (2020) EEG signal processing with separable convolutional neural network for automatic scoring of sleeping stage. Neurocomputing 410:220–228
Tan KH, Lin FJ, Shih CM, Kuo CN (2020) Intelligent control of microgrid with virtual inertia using recurrent probabilistic wavelet fuzzy neural network. IEEE Trans Power Electron 35(7):7451–7464
Shen H, Xing M, Huo S, Wu ZG, Park JH (2019) Finite-time \(H_{\infty }\) asynchronous state estimation for discrete-time fuzzy Markov jump neural networks with uncertain measurements. Fuzzy Sets Syst 356:113–128
Hu J, Jia C, Liu H, Yi X, Liu Y (2021) A survey on state estimation of complex dynamical networks. Int J Syst Sci 52(16):3351–3367
Jia X-C (2021) Resource-efficient and secure distributed state estimation over wireless sensor networks: a survey. Int J Syst Sci 52(16):3368–3389
Ge X, Han Q-L, Wang Z (2019) A dynamic event-triggered transmission scheme for distributed set-membership estimation over wireless sensor networks. IEEE Trans Cybern 49(1):171–183
He J, Liang Y, Yang F, Yang F (2020) New \(H_{\infty }\) state estimation criteria of delayed static neural networks via the Lyapunov–Krasovskii functional with negative definite terms. Neural Netw 123:236–247
Dong H, Hou N, Wang Z, Ren W (2018) Variance-constrained state estimation for complex networks with randomly varying topologies. IEEE Trans Neural Netw Learn Syst 29(7):2757–2768
Gao Y, Hu J, Chen D, Du J (2019) Variance-constrained resilient \(H_{\infty }\) state estimation for time-varying neural networks with randomly varying nonlinearities and missing measurements. Adv Differ Equ 1:380
Liu L, Ma L, Zhang J, Bo Y (2021) Distributed non-fragile set-membership filtering for nonlinear systems under fading channels and bias injection attacks. Int J Syst Sci 52(6):1192–1205
Ding D, Han Q-L, Wang Z, Ge X (2019) A survey on model-based distributed control and filtering for industrial cyber-physical systems. IEEE Trans Ind Inf 15(5):2483–2499
Shen B, Wang Z, Wang D, Li Q (2020) State-saturated recursive filter design for stochastic time-varying nonlinear complex networks under deception attacks. IEEE Trans Neural Netw Learn Syst 31(10):3788–3800
Pang Z-H, Fan L-Z, Dong Z, Han Q-L, Liu G-P (2022) False data injection attacks against partial sensor measurements of networked control systems. IEEE Trans Circuits Syst II Express Br 69(1):149–153
Pang Z-H, Fan L-Z, Sun J, Liu K, Liu G-P (2021) Detection of stealthy false data injection attacks against networked control systems via active data modification. Inf Sci 546:192–205
Zhang J, Song J, Li J, Han F, Zhang H (2021) Observer-based non-fragile \(H_{\infty }\)-consensus control for multi-agent systems under deception attacks. Int J Syst Sci 52(6):1223–1236
Ding D, Han Q-L, Xiang Y, Ge X, Zhang X (2018) A survey on security control and attack detection for industrial cyber-physical systems. Neurocomputing 275:1674–1683
Ding D, Wang Z, Ho DWC, Wei G (2017) Distributed recursive filtering for stochastic systems under uniform quantizations and deception attacks through sensor networks. Automatica 78:231–240
Feng Z, Wen G, Hu G (2017) Distributed secure coordinated control for multiagent systems under strategic attacks. IEEE Trans Cybern 47(5):1273–1284
Yoo SJ (2020) Neural-network-based adaptive resilient dynamic surface control against unknown deception attacks of uncertain nonlinear time-delay cyberphysical systems. IEEE Trans Neural Netw Learn Syst 31(10):4341–4353
Liu J, Xia J, Tian E, Fei S (2018) Hybrid-driven-based \(H_{\infty }\) filter design for neural networks subject to deception attacks. Appl Math Comput 320:158–174
Catak FO, Mustacoglu AF (2019) Distributed denial of service attack detection using autoencoder and deep neural networks. J Intell Syst 37(3):3969–3979
Wang X, Ding D, Ge X, Han Q-L (2022) Neural-network-based control for discrete-time nonlinear systems with denial-of-service attack: the adaptive event-triggered case. Int J Robust Nonlinear Control 32(5):2760–2779
Amma NGB, Selvakumar S (2022) Optimization of vector convolutional deep neural network using binary real cumulative incarnation for detection of distributed denial of service attacks. Neural Comput Appl 34(4):2869–2882
Ding D, Shen Y, Song Y, Wang Y (2016) Recursive state estimation for discrete time-varying stochastic nonlinear systems with randomly occurring deception attacks, sensor saturation and denial-of-service attacks. Int J Gen Syst 45(5):548–560
Qi W, Lv C, Park JH, Zong G, Cheng J, Shi K (2022) SMC for semi-Markov jump cyber-physical systems subject to randomly occurring deception attacks. IEEE Trans Circuits Syst II-Express Br 69(1):159–163
Song W, Wang Z, Wang J, Shan J (2021) Particle filtering for a class of cyber-physical systems under round-robin protocol subject to randomly occurring deception attacks. Inf Sci 544:298–307
Hou N, Wang Z, Ho DWC, Dong H (2020) Robust partial-nodes-based state estimation for complex networks under deception attacks. IEEE Trans Cybern 50(6):2793–2802
Gao C, He X, Dong H, Liu H, Lyu G (2022) A survey on fault-tolerant consensus control of multi-agent systems: trends, methodologies and prospects. Int J Syst Sci. https://doi.org/10.1080/00207721.2022.2056772
Gao C, Wang Z, He X, Dong H (2022) Fault-tolerant consensus control for multiagent systems: an encryption-decryption scheme. IEEE Trans Autom Control 67(5):2560–2567
Shen Y, Wang Z, Shen B, Dong H (2021) Outlier-resistant recursive filtering for multisensor multirate networked systems under weighted try-once-discard protocol. IEEE Trans Cybern 51(10):4897–4908
Li J, Wang Z, Dong H, Ghinea G (2021) Outlier-resistant remote state estimation for recurrent neural networks with mixed time-delays. IEEE Trans Neural Netw Learn Syst 32(5):2266–2273
Fu H, Dong H, Han F, Shen Y, Hou N (2020) Outlier-resistant \(H_{\infty }\) filtering for a class of networked systems under round-robin protocol. Neurocomputing 403:133–142
Alessandri A, Zaccarian L (2018) Stubborn state observers for linear time-invariant systems. Automatica 88:1–9
Shen B, Wang Z, Qiao H (2017) Event-triggered state estimation for discrete-time multidelayed neural networks with stochastic parameters and incomplete measurements. IEEE Trans Neural Netw Learn Syst 28(5):1152–1163
Shen B, Wang Z, Shu H, Wei G (2011) \(H_{\infty }\) filtering for uncertain time-varying systems with multiple randomly occurred nonlinearities and successive packet dropouts. Int J Robust Nonlinear Control 21(14):1693–1709
Dehghani A, Seyyedsalehi SA (2022) Time-frequency localization using deep convolutional maxout neural network in Persian speech recognition. Neural Process Lett. https://doi.org/10.1007/s11063-022-11006-1
Shashidhar R, Patilkulkarni S (2022) Audiovisual speech recognition for Kannada language using feed forward neural network. Neural Comput Appl 34(18):15603–15615
Liu B, Cai H, Zhang Z, Ding X, Wang Z, Gong Y, Liu W, Yang J, Wang Z, Yang J (2022) More is less: domain-specific speech recognition microprocessor using one-dimensional convolutional recurrent neural network. IEEE Trans Circuits Syst I-Regul Pap 69(4):1571–1582
Acknowledgements
This work was supported in part by the National Natural Science Foundation of China under Grant 12171124 and 72001059, the Natural Science Foundation of Heilongjiang Province of China under Grant ZD2022F003, the Heilongjiang Provincial Key Laboratory of Complex Intelligent System and Integration of China under Grant HPKL-CICS-202203, the Postdoctoral Science Foundation of Heilongjiang Province of China under Grant LBH-Z22199, the Fundamental Research Funds in Heilongjiang Provincial Universities of China under Grant 135509121, the Educational Research Project of the Qiqihar University of China under Grant YB201904, and the Alexander von Humboldt Foundation of Germany.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix A \(H_{\infty }\) Performance analysis
Proof of Theorem 1:
Define
To proceed, considering the EE dynamical system (6), we can get
where \(\bar{\sigma }_{k}=\sigma [D_{k}e_{k}-\tilde{\beta }_{k}D_{k}(\hat{x}_{k}+e_{k})-\bar{\beta }D_{k}(\hat{x}_{k}+e_{k})+\tilde{\beta }_{k}\xi _{k}+\bar{\beta }\xi _{k}].\)
Using the fundamental inequality \(2x^{T}Py\le x^{T}Px+y^{T}Py\) \((P>0)\), we can get the following results
Adding the zero term \(\tilde{z}^{T}_{k}\tilde{z}_{k}-\gamma ^{2}v_{k}^{T}U_{\varphi }v_{k}-\tilde{z}^{T}_{k}\tilde{z}_{k}+\gamma ^{2}v_{k}^{T}U_{\varphi }v_{k}\) to \(\mathbb {E}\big \{\bar{L}_{k}\big \}\) yields
where
with \(\Psi _{66}\) defined below (12).
According to Lemma 1, the following form can be obtained
where \(\Psi\) is defined in (12).
Summarizing both sides of (A6) from 0 to \(N-1\) on k, we obtain
Furthermore, we derive the following form
Noting \(\Psi <0\), \(Q_{N}>0\) and \(Q_{0}\le \gamma ^{2}U_{\phi }\), it follows that \(J_{1}<0\). \(\square\)
Appendix B Boundedness analysis of error variance
Proof of Theorem 2
According to (7), we can calculate the EE covariance matrix \(X_{k}\) as follows:
where \(\bar{\sigma }_{k}=\sigma [D_{k}e_{k}-\tilde{\beta }_{k}D_{k}(\hat{x}_{k}+e_{k})-\bar{\beta }D_{k}(\hat{x}_{k}+e_{k})+\tilde{\beta }_{k}\xi _{k}+\bar{\beta }\xi _{k}].\)
Using the inequality \(xy^{T}+yx^{T}\le xx^{T}+yy^{T}\), it can be obtained
It follows from Lemma 2 that
where Y is defined in (14).
According to (5), the following results can be obtained by calculation
Noticing \(x^{T}y+y^{T}x<\varpi x^{T}x+\frac{1}{\varpi }y^{T}y\), we can derive that
where \(0<\varpi <\frac{2}{1+\bar{g}+3\bar{\beta }+3\bar{g}\bar{\beta }}\).
Based on the above derivation results, we can get
where \(\iota _{1}\), \(\iota _{2}\) and \(\iota _{3}\) are defined in (14). Furthermore, it can be obtained that
According to the feature of the trace, one has
Combining (B9) with (B10) results in
It is easy to get that \(G_{0}\ge X_{0}\). Letting \(G_{k}\ge X_{k}\), the following inequality can be derived as
Then, from (13) and (B11), we obtain
The proof is complete. \(\square\)
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Gao, Y., Hu, J., Yu, H. et al. Outlier-resistant variance-constrained \(\mathit{H}_{\infty }\) state estimation for time-varying recurrent neural networks with randomly occurring deception attacks. Neural Comput & Applic 35, 13261–13273 (2023). https://doi.org/10.1007/s00521-023-08419-x
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00521-023-08419-x