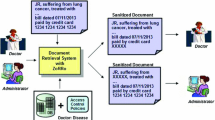
Abstract
Intense regulatory focus on secure retention of electronic records has led to a need to ensure that records are trustworthy, i.e., able to provide irrefutable proof and accurate details of past events. In this paper, we analyze the requirements for a trustworthy index to support keyword-based search queries. We argue that trustworthy index entries must be durable—the index must be updated when new documents arrive, and not periodically deleted and rebuilt. To this end, we propose a scheme for efficiently updating an inverted index, based on judicious merging of the posting lists of terms. Through extensive simulations and experiments with two real world data sets and workloads, we demonstrate that the scheme achieves online update speed while maintaining good query performance. We also present and evaluate jump indexes, a novel trustworthy and efficient index for join operations on posting lists for multi-keyword queries. Jump indexes support insert, lookup and range queries in time logarithmic in the number of indexed documents.
Similar content being viewed by others
References
Becker B., Gschwind S., Ohler T., Seeger B. and Widmayer P. (1996). An asymptotically optimal multiversion B-tree. Very Large Data Bases J. 5: 264–275
libech, K., Gabillon, A.: Chronos: an authenticated dictionary based on skip lists for timestamping systems. In: Workshop on Secure Web Services, pp. 84–90 (2005)
Brown, E., Callan, J., oft, W.: Fast inemental indexing for full-text information retrieval. In: Very Large Data Bases (VLDB) (1994)
Brown, E.W., Callan, J.P., Croft, W.B., Moss, J.E.B.: Supporting full-text information retrieval with a persistent object store. In: Extending Database Technology (EDBT) (1994)
Congress of the United States of America. Sarbanes-Oxley Act, 2002. Available at http://thomas.loc.gov
Crescenzi, P., Kann, V.: A compendium of NP optimization problems. http://www.nada.kth.se/viggo/problemlist
Cutting, D., Pedersen, J.: Optimization for dynamic inverted index maintenance. In: ACM Special Interest Group on Information Retrieval (SIGIR) (1990)
Easton, M.C.: Key-sequence data sets on indelible storage. IBM J. Res. Develop. (1986) (in press)
EMC Corp. EMC Centera Content Addressed Storage System, 2003. Available at http://www.emc.com/products/systems/centera_ce.jsp
Faloutsos C. (1985). Access methods for text. ACM Comput. Surv. 17: 49–74
Faloutsos, C., Jagadish, H.V.: On B-tree indices for skewed distributions. In: Very Large Data Bases (VLDB) (1992)
Fontoura, M.F., Neumann, A., Rajagopalan, S., Shekita, E., Zien, J.: High performance index build algorithms for intranet search engines. In: Very Large Data Bases (VLDB) (2004)
Goh, E., Shacham, H., Modadugu, N., Boneh, D.: Sirius: Securing remote untrusted storage. In: Network and Distributed System Security Symposium (NDSS) (2003)
Goodrich, M., Tamassia, R., Schwerin, A.: Implementation of an authenticated dictionary with skip lists and commutative hashing. In: DARPA Information Survivability Conference and Exposition (DISCEX) II (2001)
Garcia-Molina J.W.H. and Ullman J.D. (2000). Database Systems, A Complete Book. Prentice-Hall, New Jersely
Hacigumus, H., Iyer, B.R., Mehrotra, S.: Providing database as a service. In: International Conference on Data Engineering (ICDE) (2002)
Heinz, S., Zobel, J.: Efficient single-pass index construction for text databases. In: Journal of the American Society for Information Science and Technology (JASIST) (2003)
Hirai, J., Raghavan, S., Garcia-Molina, H., Paepcke, A.: Webbase: a repository of web pages. In: The International Journal of Computer and Telecommunications Networking, pp. 277–293 (2000)
Huang, L., Hsu, W., Zheng, F.: Content immutable storage for trustworthy record keeping. In: NASA Conference on Mass Storage Systems and Technologies (MSST) (2006)
IBM Corp. IBM TotalStorage DR550, 2004. Available at http://www-1.ibm.com/servers/storage/disk/dr
Klimt, B., Yang, Y.: Introducing the Enron Corpus. In: Conference on Email and Anti-Spam (CEAS) (2004)
Lester, N., Zobel, J., Williams, H.E.: In-place versus re-build versus re-merge: index maintenance strategies for text retrieval systems. In: Conference on Australasian Computer Science (2004)
Miller, E.L., Freeman, W.E., Long, D.D.E., Reed, B.C.: Strong security for network-attached storage. In: USENIX Conference on File and Storage Technologies (FAST) (2002)
Network Appliance, Inc. SnapLockTM Compliance and SnapLock Enterprise Software, 2003. Available at http://www.netapp.com/products/filer/snaplock.html
Rathmann, P.: Dynamic data structures on optical disks. In: International Conference on Data Engineering (ICDE) (1984)
Robertson, S.E., Walker, S., Hancock-Beaulieu, M., Gull, A., Lau, M.: Okapi at TREC. In: Text Retrieval Conference (TREC) (1992)
Securities and Exchange Commission. Guidance to Broker- Dealers on the Use of Electronic Storage Media under the National Commerce Act of 2000 with Respect to Rule 17a-4(f), 2001. Available at http://www.sec.gov/rules/interp/34-44238.htm
Krijnen, T., Meertens, L.G.L.T.: Making B-Trees Work for B.IW 219/83. The Mathematical Centre, Amsterdam, The Netherlands (1983)
The Enterprise Storage Group, Inc. Compliance.: the effect on information management and the storage industry, May 2003. Available at http://www.enterprisestoragegroup.com
Tomasic, A., García-Molina, H., Shoens, K.: Inemental updates of inverted lists for text document retrieval. In: Very Large Data Bases (VLDB) (1994)
United States Department of Health and Human Services. Health Insurance Portability and Accountability Act of 1996. Available at http://www.hhs.gov/o/hipaa/
Wittenm, I.H., Moffat, A., Bell, T.C.: Managing Gigabytes: Compressing and Indexing Documents and Images. Morgan Kaufman, San Francisco (1999)
Zhu, Q., Hsu, W.: Fossilized index: the linchpin of trustworthy non-alterable electronic records. In: ACM SIGMOD International Conference on Management of Data (2005)
Zipf G.K. (1949). Human Behavior and the Principle of Least Effort: An Introduction to Human Ecology. Addison-Wesley, Cambridge
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Mitra, S., Winslett, M., Hsu, W.W. et al. Trustworthy keyword search for compliance storage. The VLDB Journal 17, 225–242 (2008). https://doi.org/10.1007/s00778-007-0069-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00778-007-0069-7