Abstract
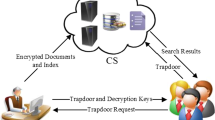
Searchable encryption (SE) is a cryptographic technique that allows the users to perform search over outsourced encrypted data in cloud servers while preserving the privacy of data and search query. In order to preserve privacy and security, data owners use various encryption schemes to encrypt their data and indexes. Due to the vulnerabilities in the encryption schemes adopted by SE schemes, information leakages are possible from the encrypted data. The cloud servers use various information disclosure attacks that exploit these leakages to infer plaintext information. In this paper, we analyze the existing SE approaches with respect to their security and precision goals and possible attacks on them. We also identify the root causes of these attacks and their remedies. An experimental study is also performed to investigate the susceptibility of SE schemes against attacks and countermeasures to prevent them.






Similar content being viewed by others
References
Abdalla M, Bellare M, Catalano D, Kiltz E, Kohno T, Lange T, Malone-Lee J, Neven G, Paillier P, Shi H (2005) Searchable encryption revisited: consistency properties, relation to anonymous ibe, and extensions. In: Annual international cryptology conference. Springer, pp 205–222
Arshad S, Ullah S, Khan SA, Awan MD, Khayal MSH (2015) A survey of cloud computing variable pricing models. In: 2015 International conference on evaluation of novel approaches to software engineering (ENASE), pp 27–32
Bellare M, Boldyreva A, O’Neill A (2007) Deterministic and efficiently searchable encryption. In: Proceedings of the 27th annual international cryptology conference on advances in cryptology, CRYPTO’07. Springer, Berlin, pp 535–552. http://dl.acm.org/citation.cfm?id=1777777.1777820. Accessed 2 July 2016
Bethencourt J, Sahai A, Waters B (2007) Ciphertext-policy attribute-based encryption. In: Proceedings of the 2007 IEEE symposium on security and privacy, SP ’07. IEEE Computer Society, Washington, DC, USA, pp 321–334. https://doi.org/10.1109/SP.2007.11
Boldyreva A, Chenette N, Lee Y, O’Neill A (2009) Order-preserving symmetric encryption. In: Proceedings of the 28th annual international conference on advances in cryptology: the theory and applications of cryptographic techniques, EUROCRYPT ’09. Springer, Berlin, pp 224–241. https://doi.org/10.1007/978-3-642-01001-9_13
Boneh D, Di Crescenzo G, Ostrovsky R, Persiano G (2004) Public key encryption with keyword search. Springer, Berlin, pp 506–522. https://doi.org/10.1007/978-3-540-24676-3_30
Boneh D, Waters B (2007) Conjunctive, subset, and range queries on encrypted data. Springer, Berlin, pp 535–554. https://doi.org/10.1007/978-3-540-70936-7_29
Bösch C, Hartel P, Jonker W, Peter A (2014) A survey of provably secure searchable encryption. ACM Comput Surv 47(2):18:1–18:51. https://doi.org/10.1145/2636328
Bost R, Minaud B, Ohrimenko O (2017) Forward and backward private searchable encryption from constrained cryptographic primitives. In: Proceedings of the 2017 ACM SIGSAC conference on computer and communications security, CCS ’17. ACM, New York, NY, USA, pp 1465–1482. https://doi.org/10.1145/3133956.3133980
Byun JW, Rhee HS, Park HA, Lee DH (2006) Off-line keyword guessing attacks on recent keyword search schemes over encrypted data. In: Jonker W, Petković M (eds) Secure data management. Springer, Berlin, pp 75–83
Cao N, Wang C, Li M, Ren K, Lou W (2014) Privacy-preserving multi-keyword ranked search over encrypted cloud data. IEEE Trans Parallel Distrib Syst 25(1):222–233. https://doi.org/10.1109/TPDS.2013.45
Chang YC, Mitzenmacher M (2005) Privacy preserving keyword searches on remote encrypted data. In: International conference on applied cryptography and network security. Springer, pp 442–455
Chor B, Kushilevitz E, Goldreich O, Sudan M (1998) Private information retrieval. J ACM 45(6):965–981. https://doi.org/10.1145/293347.293350
Curtmola R, Garay J, Kamara S, Ostrovsky R (2006) Searchable symmetric encryption: improved definitions and efficient constructions. In: CCS-2006: ACM conference on Computers and Communications Security, pp 79–88
Drazen WA, Ekwedike E, Gennaro R (2015) Highly scalable verifiable encrypted search. In: 2015 IEEE Conference on communications and network security (CNS), pp 497–505. https://doi.org/10.1109/CNS.2015.7346862
Fabian B, Ermakova T, Junghanns P (2015) Collaborative and secure sharing of healthcare data in multi-clouds. Inf Syst 48:132–150. https://doi.org/10.1016/j.is.2014.05.004
Goh EJ et al (2003) Secure indexes. IACR Cryptol ePrint Arch 2003:216
Goldreich O, Ostrovsky R (1996) Software protection and simulation on oblivious rams. J ACM (JACM) 43(3):431–473
Goldwasser S, Micali S (1984) Probabilistic encryption. J Comput Syst Sci 28(2):270–299. https://doi.org/10.1016/0022-0000(84)90070-9
Golle P, Staddon J, Waters B (2004) Secure conjunctive keyword search over encrypted data. Springer, Berlin, pp 31–45. https://doi.org/10.1007/978-3-540-24852-1_3
Goyal V, Pandey O, Sahai A, Waters B (2006) Attribute-based encryption for fine-grained access control of encrypted data. In: Proceedings of the 13th ACM conference on computer and communications security, CCS ’06. ACM, New York, NY, USA, pp 89–98
Hacigümüş H, Iyer B, Li C, Mehrotra S (2002) Executing sql over encrypted data in the database-service-provider model. In: Proceedings of the 2002 ACM SIGMOD international conference on management of data, SIGMOD ’02. ACM, New York, NY, USA, pp 216–227. https://doi.org/10.1145/564691.564717
Han F, Qin J, Hu J (2016) Secure searches in the cloud: a survey. Future Gener Comput Syst 62:66–75. https://doi.org/10.1016/j.future.2016.01.007
Hwang YH, Lee PJ (2007) Public key encryption with conjunctive keyword search and its extension to a multi-user system. In: Proceedings of the first international conference on pairing-based cryptography, Pairing’07. Springer, Berlin, pp 2–22
Ibrahim A, Jin H, Yassin AA, Zou D (2012) Secure rank-ordered search of multi-keyword trapdoor over encrypted cloud data. In: Services computing conference (APSCC), 2012 IEEE Asia-Pacific, pp 263–270. https://doi.org/10.1109/APSCC.2012.59
Islam MS, Kuzu M, Kantarcioglu M (2012) Access pattern disclosure on searchable encryption: ramification, attack and mitigation. In: Network and distributed system security symposium (NDSS)
Katz J, Sahai A, Waters B (2008) Predicate encryption supporting disjunctions, polynomial equations, and inner products. Springer, Berlin, pp 146–162. https://doi.org/10.1007/978-3-540-78967-3_9
Keskin T, Taskin N (2014) A pricing model for cloud computing service. In: 2014 47th Hawaii international conference on system sciences, pp 699–707. https://doi.org/10.1109/HICSS.2014.94
Kim KS, Kim M, Lee D, Park JH, Kim WH (2017) Forward secure dynamic searchable symmetric encryption with efficient updates. In: Proceedings of the 2017 ACM SIGSAC conference on computer and communications security, CCS ’17. ACM, New York, NY, USA, pp 1449–1463. https://doi.org/10.1145/3133956.3133970
Kuzu M, Islam MS, Kantarcioglu M (2012) Efficient similarity search over encrypted data. In: 2012 IEEE 28th international conference on data engineering. IEEE, pp 1156–1167
Kyaw AK, Sioquim F, Joseph J (2015) Dictionary attack on wordpress: security and forensic analysis. In: 2015 2nd international conference on information security and cyber forensics (InfoSec). IEEE, pp 158–164
Li R, Xu Z, Kang W, Yow KC, Xu CZ (2014) Efficient multi-keyword ranked query over encrypted data in cloud computing. Future Gener Comput Syst 30:179–190. https://doi.org/10.1016/j.future.2013.06.029 (Special issue on extreme scale parallel architectures and systems, cryptography in cloud computing and recent advances in parallel and distributed systems, ICPADS 2012 selected papers)
Li Z, Fang R, Shen F, Katouzian A, Zhang S (2017) Indexing and mining large-scale neuron databases using maximum inner product search. Pattern Recognit 63:680–688. https://doi.org/10.1016/j.patcog.2016.09.041
Liu C, Zhu L, Wang M, Tan Y (2014) Search pattern leakage in searchable encryption: attacks and new construction. Inf Sci 265:176–188. https://doi.org/10.1016/j.ins.2013.11.021
Lotspiech J (2006) 12-Broadcast encryption. In: Zeng W, Yu H, Lin CY (eds) Multimedia security technologies for digital rights management. Academic Press, Burlington, pp 303–322
Manning CD, Raghavan P, Schütze H (2008) Introduction to information retrieval. Cambridge University Press, New York
Margae SE, Sanae B, Mounir AK, Youssef F (2014) Traffic sign recognition based on multi-block lbp features using svm with normalization. In: 2014 9th international conference on intelligent systems: theories and applications (SITA-14), pp 1–7. https://doi.org/10.1109/SITA.2014.6847283
Miao Y, Ma J, Liu X, Li X, Jiang Q, Zhang J (2017) Attribute-based keyword search over hierarchical data in cloud computing. IEEE Trans Serv Comput PP(99):1–1. https://doi.org/10.1109/TSC.2017.2757467
Naveed M, Kamara S, Wright CV (2015) Inference attacks on property-preserving encrypted databases. In: Proceedings of the 22Nd ACM SIGSAC conference on computer and communications security, CCS ’15. ACM, New York, NY, USA, pp 644–655. https://doi.org/10.1145/2810103.2813651
Naveed M, Prabhakaran M, Gunter CA (2014) Dynamic searchable encryption via blind storage. In: Proceedings of the 2014 IEEE symposium on security and privacy, SP ’14. IEEE Computer Society, Washington, DC, USA, pp 639–654. https://doi.org/10.1109/SP.2014.47
Orencik C, Kantarcioglu M, Savas E (2013) A practical and secure multi-keyword search method over encrypted cloud data. In: 2013 IEEE 6th international conference on cloud computing, pp 390–397. https://doi.org/10.1109/CLOUD.2013.18
Örencik C, Savaş E (2012) Efficient and secure ranked multi-keyword search on encrypted cloud data. In: Proceedings of the 2012 Joint EDBT/ICDT workshops. ACM, pp 186–195
Paillier P (1999) Public-key cryptosystems based on composite degree residuosity classes. In: Stern J (ed) Advances in cryptology—EUROCRYPT ’99. Springer, Berlin, pp 223–238
Pappas V, Krell F, Vo B, Kolesnikov V, Malkin T, Choi SG, George W, Keromytis A, Bellovin S (2014) Blind seer: a scalable private dbms. In: Proceedings of the 2014 IEEE symposium on security and privacy, SP ’14. IEEE Computer Society, Washington, DC, USA, pp 359–374. https://doi.org/10.1109/SP.2014.30
Park JH (2011) Efficient hidden vector encryption for conjunctive queries on encrypted data. IEEE Trans Knowl Data Eng 23(10):1483–1497. https://doi.org/10.1109/TKDE.2010.206
Peng T, Lin Y, Yao X, Zhang W (2018) An efficient ranked multi-keyword search for multiple data owners over encrypted cloud data. IEEE Access 6:21924–21933. https://doi.org/10.1109/ACCESS.2018.2828404
Poh GS, Chin JJ, Yau WC, Choo KKR, Mohamad MS (2017) Searchable symmetric encryption: designs and challenges. ACM Comput Surv 50(3):40:1–40:37. https://doi.org/10.1145/3064005
Popa RA, Redfield CMS, Zeldovich N, Balakrishnan H (2011) Cryptdb: protecting confidentiality with encrypted query processing. In: Proceedings of the 23rd ACM symposium on operating systems principles, SOSP ’11. ACM, New York, NY, USA, pp 85–100. https://doi.org/10.1145/2043556.2043566
Popa RA, Stark E, Helfer J, Valdez S, Zeldovich N, Kaashoek MF, Balakrishnan H (2014) Building web applications on top of encrypted data using mylar. In: Proceedings of the 11th USENIX conference on networked systems design and implementation, NSDI’14. USENIX Association, Berkeley, CA, USA, pp 157–172. http://dl.acm.org/citation.cfm?id=2616448.2616464. Accessed 10 Dec 2017
Pussewalage HSG, Oleshchuk VA (2016) Privacy preserving mechanisms for enforcing security and privacy requirements in e-health solutions. Int J Inf Manag 36(6, Part B):1161–1173. https://doi.org/10.1016/j.ijinfomgt.2016.07.006
RFC: Request for comments database. https://www.rfc-editor.org/retrieve/bulk/. Accessed 4 May 2016
Ryu EK, Takagi T (2007) Efficient conjunctive keyword-searchable encryption. In: 21st International conference on advanced information networking and applications workshops, 2007, AINAW ’07, vol 1, pp 409–414. https://doi.org/10.1109/AINAW.2007.166
Shen E, Shi E, Waters B (2009) Predicate privacy in encryption systems. In: Proceedings of the 6th theory of cryptography conference on theory of cryptography, TCC ’09. Springer, Berlin, pp 457–473. https://doi.org/10.1007/978-3-642-00457-5_27
Song DX, Wagner D, Perrig A (2000) Practical techniques for searches on encrypted data. In: Proceeding 2000 IEEE symposium on security and privacy. S P 2000, pp 44–55. https://doi.org/10.1109/SECPRI.2000.848445
Swaminathan A, Mao Y, Su GM, Gou H, Varna AL, He S, Wu M, Oard DW (2007) Confidentiality-preserving rank-ordered search. In: Proceedings of the 2007 ACM workshop on Storage security and survivability. ACM, pp 7–12
Wang B, Song W, Lou W, Hou YT (2015) Inverted index based multi-keyword public-key searchable encryption with strong privacy guarantee. In: 2015 IEEE conference on computer communications (INFOCOM). IEEE, pp 2092–2100
Wang C, Cao N, Ren K, Lou W (2012) Enabling secure and efficient ranked keyword search over outsourced cloud data. IEEE Trans Parallel Distrib Syst 23(8):1467–1479
Wang F, Sun J (2015) Survey on distance metric learning and dimensionality reduction in data mining. Data Min Knowl Discov 29(2):534–564. https://doi.org/10.1007/s10618-014-0356-z
Wang Y, Wang J, Chen X (2016) Secure searchable encryption: a survey. J Commun Inf Netw 1(4):52–65. https://doi.org/10.1007/BF03391580
Wong KS, Kim MH (2013) Privacy-preserving similarity coefficients for binary data. Comput Math Appl 65(9):1280–1290. https://doi.org/10.1016/j.camwa.2012.02.028. (Advanced Information Security)
Wu Z, Xu G, Yu Z, Yi X, Chen E, Zhang Y (2012) Executing SQL queries over encrypted character strings in the database-as-service model. Knowl Based Syst 35:332–348. https://doi.org/10.1016/j.knosys.2012.05.009
Xia Z, Wang X, Sun X, Wang Q (2016) A secure and dynamic multi-keyword ranked search scheme over encrypted cloud data. IEEE Trans Parallel Distrib Syst 27(2):340–352. https://doi.org/10.1109/TPDS.2015.2401003
Yang Y, Liu X, Deng RH, Weng J (2017) Flexible wildcard searchable encryption system. IEEE Trans Serv Comput PP(99):1–1. https://doi.org/10.1109/TSC.2017.2714669
Yu J, Lu P, Zhu Y, Xue G, Li M (2013) Toward secure multikeyword top-k retrieval over encrypted cloud data. IEEE Trans Dependable Secure Comput 10(4):239–250. https://doi.org/10.1109/TDSC.2013.9
Zhang B, Zhang F (2011) An efficient public key encryption with conjunctive-subset keywords search. J Netw Comput Appl 34(1):262–267. https://doi.org/10.1016/j.jnca.2010.07.007
Zhang W, Ji J, Zhu J, Li J, Xu H, Zhang B (2016) Bithash: an efficient bitwise locality sensitive hashing method with applications. Knowl Based Syst 97:40–47. https://doi.org/10.1016/j.knosys.2016.01.022
Zhang W, Lin Y, Xiao S, Wu J, Zhou S (2016) Privacy preserving ranked multi-keyword search for multiple data owners in cloud computing. IEEE Trans Comput 65(5):1566–1577. https://doi.org/10.1109/TC.2015.2448099
Zobel J, Moffat A (1998) Exploring the similarity space. SIGIR Forum 32(1):18–34. https://doi.org/10.1145/281250.281256
Acknowledgements
The authors would like to thank Ministry of Electronics and Information Technology (MeitY), Government of India, for their support in part of the research.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Siva Kumar, D.V.N., Santhi Thilagam, P. Searchable encryption approaches: attacks and challenges. Knowl Inf Syst 61, 1179–1207 (2019). https://doi.org/10.1007/s10115-018-1309-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10115-018-1309-4