Abstract
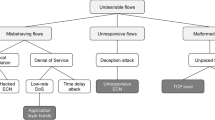
The purpose of a denial of service (DoS) attack is to render a network service unavailable for legitimate users. We address the problem of DoS attacks on connection-oriented protocols where the attacker tries to deplete the server connection by initiating communication with the server and then abandoning the communication. The most exploited attack in this category is the SYN-flood attack but other attacks using the same approach in stateful communication protocols also fall into this category. Our goals are twofold: first, to develop a mathematical model allowing us to analyse the trade-off between the attacker and the defender resources and second, to offer prevention mechanisms that can be used to defend against this category of attacks. We model the server queue of connections using Markov chains to establish a relationship between the server capacity, the attack rate and the impact on the service level. We analyse two methods of adjusting the timeout, threshold and linear, and we couple them with three policies of assigning the timeout to connections: the deterministic policy, the deferred policy and the utopian Poisson policy. First, theoretical modelling confirms that for any given strategy, there exists a linear trade-off between attack rate and targeted server queue size. However, the ratio that needs to be kept between them in order to maintain a similar level of quality of service differs between strategies; in that sense some are better than others. In particular, theoretical modelling also indicates that the linear deferred timeout strategy is very similar in performance to the linear Poisson timeout strategy, which in turn outperforms all the other dynamic timeout strategies. The dynamic timeout strategies always outperform the classical fixed timeout method. Our model is very general and can be used to capture the behaviour of the server queue during connection depletion attacks at various levels in the TCP protocol stack. We confirm the theoretical findings using stochastic simulations and network experiments of SYN-flood attacks. We also show how the model can be used when analysing a TCP connection establishment flood or a ticket reservation flood. The protection strategies we suggest are robust to changes in the attack model and our implementation is very efficient and transparent with respect to the server and applications it tries to protect. The strategies could therefore be easily integrated into existing operating systems and applications, or implemented in separate network devices.































Similar content being viewed by others
References
Adair, S.: Gambling websites under attack. http://www.shadowserver.org/wiki/pmwiki.php?n=Calendar.20080218 (2008)
Al-Duwairi, B., Manimaran, G.: Intentional dropping: a novel scheme for SYN flooding mitigation. In: INFOCOM 2005: Proceedings of the 24th Annual Joint Conference of the IEEE Computer and Communications Societies. IEEE Computer Society, Silver Spring (2005)
Ayres, P.E., Sun, H., Chao, H.J., Lau, W.C.: ALPi: a DDoS defense system for high-speed networks. IEEE J. Sel. Areas Commun. 24, 1864–1876 (2006)
Beaumont-Gay, M.: A comparison of SYN flood detection algorithms. In: ICIMP 2007: Proceedings of the Second International Conference on Internet Measurement and Protection. IEEE Computer Society, Silver Spring (2007)
Bellaïche, M., Grégoire, J.C.: SYN flooding attack detection by TCP handshake behaviour observation. In: MonAM 2007: Proceedings of the IEEE Workshop on Monitoring, Attack Detection and Mitigation (2007)
Bernstein, D.J.: SYN cookies. http://cr.yp.to/syncookies.html (2003)
Boteanu, D., Fernandez, J.M., McHugh, J., Mullins, J.: Queue management as a DoS counter-measure? In: ISC 2007: Proceedings of the Information Security Conference, pp. 263–280. Springer, Berlin (2007)
Boteanu, D., Reich, E., Fernandez, J.M., McHugh, J.: Implementing and testing dynamic timeout adjustment as a DoS counter-measure. In: QoP ’07: Proceedings of the ACM Workshop on Quality of Protection, pp. 34–39. ACM, New York (2007)
Cao, J., Cleveland, W.S., Lin, D., Sun, D.X.: On the nonstationarity of internet traffic. ACM SIGMETRICS Perform. Eval. Rev. 29(1), 102–112 (2001)
Chen, S., Song, Q.: Perimeter-based defense against high bandwidth DDoS attacks. IEEE Trans. Parallel Distrib. Syst. 16(6), 526–537 (2005)
Cheng, C.M., Kung, H., Tan, K.S.: Use of spectral analysis in defense against DoS attacks. In: GLOBECOM ’02: Proceedinds of the Global Telecommunications Conference, vol. 3, pp. 2143–2148. IEEE Computer Society, Silver Spring (2002)
Chouman, M., Safa, H., Artail, H.: Novel defense mechanism against SYN flooding attacks in IP networks. In: Proceedings of the Canadian Conference on Electrical and Computer Engineering (2005)
Dierks, T., Rescorla, E.: RFC4346: the transport layer security (TLS) protocol. Version 1.1. http://www.ietf.org/rfc/rfc4346.txt (2006)
Divakaran, D.M., Murthy, H.A., Gonsalves, T.A.: Detection of SYN flooding attacks using linear prediction analysis. In: ICON ’06: Proceedings of the 14th IEEE International Conference on Networks, vol. 1. IEEE Computer Society, Silver Spring (2006)
Dong, K., Yang, S., Wang, S.: Analysis of low-rate TCP DoS attack against FAST TCP. In: ISDA ’06: Proceedings of the Sixth International Conference on Intelligent Systems Design and Applications. IEEE Computer Society, Silver Spring (2006)
Douligeris, C., Mitrokotsa, A.: DDoS attacks and defense mechanisms: classification and state-of-the-art. Comput. Netw. 44(5), 643–666 (2004)
Feinstein, L., Schnackenberg, D., Balupari, R., Kindred, D.: Statistical approaches to DDoS attack detection and response. In: DISCEX-III: Proceedings of the 3rd DARPA Information Survivability Conference and Exposition, pp. 303–314. IEEE Computer Society, Silver Spring (2003)
Feng, W.C., Kaiser, E., Luu, A.: Design and implementation of network puzzles. In: INFOCOM 2005: Proceedings of the 24th Annual Joint Conference of the IEEE Computer and Communications Societies. IEEE Computer Society, Silver Spring (2005)
Ferguson, P., Senie, D.: RFC2267: Network ingress filtering: defeating denial of service attacks which employ IP source address spoofing. http://www.ietf.org/rfc/rfc2267.txt (1998)
Fielding, R., Gettys, J., Mogul, J., Frystyk, H., Masinter, L., Leach, P., Berners-Lee, T.: RFC2616: Hypertext Transfer Protocol—HTTP/1.1. http://www.ietf.org/rfc/rfc2616.txt (1999)
Ghavidel, A.Z., Issac, B.: Secure transport protocols for DDoS attack resistant communication. In: SCOReD 2007: Proceedings of the 5th Student Conference on Research and Development. IEEE, New York (2007)
Handley, M., Rescorla, E.: RFC4732—Internet denial-of-service considerations. http://www.ietf.org/rfc/rfc4732.txt (2006)
Ioannidis, J., Bellovin, S.M.: Implementing Pushback: Router-based defense against DDoS attacks. In: NDSS ’02: Proceedings of Network and Distributed System Security Symposium. The Internet Society, Washington (2002)
Jagerman, D.L.: Nonstationary blocking in telephone traffic. Bell Syst. Tech. J. 54, 625–661 (1975)
Jagerman, D.L., Melamed, B., Willinger, W.: Stochastic modeling of traffic processes. In: Frontiers in Queueing: Models and Applications in Science and Engineering (1997)
Jin, C., Wang, H., Shin, K.G.: Hop-count filtering: an effective defense against spoofed DDoS traffic. In: CCS ’03: Proceedings of the 10th ACM conference on Computer and Communications Security, pp. 30–41. ACM, New York(2003)
Juels, A., Brainard, J.: Client puzzles: A cryptographic defense against connection depletion attacks. In: NDSS ’99: Proceedings of the Network and Distributed System Security, Symposium, pp. 151–165 (1999)
Keromytis, A.D., Misra, V., Rubenstein, D.: SOS: an architecture for mitigating DDoS attacks. IEEE J. Sel. Areas Commun. 22, 176–188 (2004)
Khan, S., Traoré, I.: Queue-based analysis of DoS attacks. In: Proceedings of the IEEE Workshop on Information Assurance and Security, pp. 266–273. IEEE Computer Society, Silver Spring (2005)
Kim, Y., Lau, W.C., Chuah, M.C., Chao, H.J.: PacketScore: a statistics-based packet filtering scheme against distributed denial-of-service attacks. IEEE Trans. Dependable Secur. Comput. 03(2), 141–155 (2006)
Kuzmanovic, A., Knightly, E.W.: Low-rate TCP-targeted denial of service attacks: the shrew vs. the mice and elephants. In: SIGCOMM ’03: Proceedings of the Conference on Applications, technologies, architectures, and protocols for, computer communications. ACM, New York (2003)
Lemon, J.: Resisting SYN flood DoS attacks with a SYN cache. In: BSDC’02: Proceedings of the BSD Conference. USENIX Association, Berkeley (2002)
Lim, B., Uddin, M.S.: Statistical-based SYN-flooding detection using programmable network processor. In: ICITA ’05: Proceedings of the Third International Conference on Information Technology and Applications, pp. 465–470. IEEE Computer Society, Silver Spring (2005)
Liu, Z., César Jalpa-Villanueva, N.N.: Traffic model and performance evaluation of Web servers. Perform. Eval. 46(2–3), 77–100 (2001)
Lui, J.C.S., Misra, V., Rubenstein, D.: On the robustness of soft state protocols. In: ICNP ’04: Proceedings of the 12th IEEE International Conference on Network Protocols, pp. 50–60. IEEE Computer Society, Silver Spring (2004)
Maciá-Fernández, G., Díaz-Verdejo, J.E., García-Teodoro, P.: Evaluation of a low-rate DoS attack against iterative servers. Comput. Netw. 51(4), 1013–1030 (2007)
Massey, W.A., Whitt, W.: An analysis of the modified offered-load approximation for the nonstationary Erlang loss mode. Ann. Appl. Probab. 4(4), 1145–1160 (1994)
Meadows, C.: A formal framework and evaluation method for network denial of service. In: CSFW ’99: Proceedings of the 12th IEEE Workshop on Computer Security Foundations, p. 4. IEEE Computer Society, Silver Spring (1999)
Meadows, C.: A cost-based framework for analysis of denial of service in networks. J. Comput. Secur. 9(1–2), 143–164 (2001)
Microsoft TechNet: Security considerations for network attacks. http://www.microsoft.com/technet/security/topics/networksecurity/secdeny.mspx (2003)
Mirkovic, J., Dietrich, S., Dittrich, D., Reiher, P.: Internet denial of service: attack and defense mechanisms. Prentice Hall, Englewood Cliffs (2004)
Mirkovic, J., Prier, G., Reiher, P.L.: Attacking DDoS at the source. In: ICNP ’02: Proceedings of the 10th IEEE International Conference on Network Protocols, pp. 312–321. IEEE Computer Society, Silver Spring (2002)
Mirkovic, J., Reiher, P.: A taxonomy of DDoS attack and DDoS defense mechanisms. SIGCOMM Comput. Commun. Rev. 34(2), 39–53 (2004)
Mirkovic, J., Reiher, P., Fahmy, S., Thomas, R., Hussain, A., Schwab, S., Ko, C.: Measuring denial of service. In: QoP ’06: Proceedings of the 2nd ACM Workshop on Quality of Protection, pp. 53–58. ACM, New York (2006)
Mirkovic, J., Robinson, M., Reiher, P.: Alliance formation for DDoS defense. In: NSPW ’03: Proceedings of the Workshop on New Security Paradigms, pp. 11–18. ACM, New York (2003)
Nakashima, T., Oshima, S.: A detective method for SYN flood attacks. In: ICICIC ’06: Proceedings of the First International Conference on Innovative Computing, Information and Control, pp. 48–51. IEEE Computer Society, Silver Spring (2006)
Nakashima, T., Sueyoshi, T.: Performance estimation of TCP under SYN flood attacks. In: CISIS 2007: Proceedings of the First International Conference on Complex, Intelligent and Software Intensive Systems, pp. 92–99. IEEE Computer Society, Silver Spring (2007)
Natu, M., Mirkovic, J.: Fine-grained capabilities for flooding DDoS defense using client reputations. In: LSAD 2007: Proceedings of the ACM SIGCOMM Workshop on Large-Scale Attack and, Defense. ACM, New York (2007)
Nazario, J.: Estonian DDoS attacks—A summary to date. http://asert.arbornetworks.com/2007/05/estonian-ddos-attacks-a-summary-to-date (2007)
Noureldien, N.A., Osman, I.M.: A stateful inspection module architecture. In: Proceedings of IEEE TENCON 2000 Conference, vol. 2, pp. 259–265. IEEE Computer Society, Silver Spring (2000)
Ohsita, Y., Ata, S., Murata, M.: Deployable overlay network for defense against distributed SYN flood attacks. In: ICCCN 2005: Proceedings of the 14th International Conference on Computer Communications and Networks, pp. 407–412. IEEE Computer Society, Silver Spring (2005)
Oikonomou, G., Mirkovic, J., Reiher, P., Robinson, M.: A framework for a collaborative DDoS defense. In: ACSAC ’06: Proceedings of the 22nd Annual Computer Security Applications Conference on Annual Computer Security Applications Conference, pp. 33–42. IEEE Computer Society, Silver Spring (2006)
Postel, J., Reynolds, J.: RFC959: file transfer protocol (FTP). http://tools.ietf.org/html/rfc959 (1985)
Robinson, M., Mirkovic, J., Michel, S., Schnaider, M., Reiher, P.: DefCOM: defensive cooperative overlay mesh. In: DISCEX-III: Proceedings of the 3rd DARPA Information Survivability Conference and Exposition, vol. 2, pp. 101–102. IEEE Computer Society, Silver Spring (2003)
Schuba, C.L., Krsul, I.V., Kuhn, M.G., spafford, E.H., Sundaram, A., Zamboni, D.: Analysis of a denial of service attack on TCP. In: SP ’97: Proceedings of the 1997 IEEE Symposium on Security and Privacy, p. 208. IEEE Computer Society, Silver Spring (1997)
Shakkottai, S., Srikant, R., Brownlee, N., Broido, A., Claffy, K.: The RTT distribution of TCP flows in the Internet and its impact on TCP-based flow control. Tech. rep, Cooperative Association for Internet Data Analysis (CAIDA), USA (2004)
Shevtekar, A., Anantharam, K., Ansari, N.: Low rate TCP denial-of-service attack detection at edge routers. IEEE Commun. Lett. 9(4), 363–365 (2005)
Shin, S., Kim, K., Jang, J.: D-SAT: detecting SYN flooding attack by two-stage statistical approach. In: Proceedings of the Symposium on Applications and the Internet. IEEE, New York (2005)
Siris, V.A., Papagalou, F.: Application of anomaly detection algorithms for detecting SYN flooding attacks. In: GLOBECOMM ’04: Proceedings of the Global Telecommunications Conference. IEEE Computer Society, New York (2004)
Tartakovsky, A.G., Rozovskii, B.L., Blazzek, R.B., Kim, H.: A novel approach to detection of intrusions in computer networks via adaptive sequential and batch-sequential change-point detection methods. IEEE Trans. Signal Process. 54(9), 3372–3382 (2006)
Varanasi, R., Phoha, V.V., Joshi, S.: IP-traceback based attacker tracking: a probabilistic technique for detecting Internet attacks using the concept of Hidden Markov Models. In: Proceedings of the 5th IEEE Information Assurance Workshop, US Military Academy of West Point. IEEE Computer Society, Silver Spring (2004)
Wang, H., Zhang, D., Shin, K.G.: Detecting SYN flooding attack. In: NFOCOM 2002: Proceedings of the Twenty-First Annual Joint Conference of the IEEE Computer and Communications Societies, pp. 1530–1539. IEEE Computer Society, Silver Spring (2002)
Xiao, B., Chen, W., He, Y., Sha, E.H.M.: An active detecting method against SYN flooding attack. In: ICPADS ’05: Proceedings of the 11th International Conference on Parallel and Distributed Systems, pp. 709–715. IEEE Computer Society, Silver Spring (2005)
Yang, G., Gerla, M., Sanadidi, M.Y.: Defense against low-rate TCP-targeted Denial-of-Service attacks. In: ISCC ’04: Proceedings of the Ninth International Symposium on Computers and Communications, pp. 345–350. IEEE Computer Society, Silver Spring (2004)
Yang, X., Wetherall, D., Anderson, T.: A DoS-limiting network architecture. ACM SIGCOMM Comput. Commun. Rev. 35(4), 241–252 (2005)
Yau, D.K.Y., Lui, J.C.S., Liang, F., Yam, Y.: Defending against distributed denial-of-service attacks with max-min fair server-centric router throttles. IEEE/ACM Trans. Netw. 13(1), 29–42 (2005)
Zhang, S., Dasgupta, P.: Denying denial-of-service attacks: a router based solution. In: ICDCS 2003: Proceedings of the 23 IEEE International Conference on Distributed Computing Systems. IEEE Computer Society, Silver Spring (2003)
Zou, C.C., Duffield, N., Towsley, D., Gong, W.: Adaptive defense against various network attacks. IEEE J. Sel. Areas Commun. 24, 1877–1888 (2006)
Zuquete, A.: Improving the functionality of SYN cookies. In: Proceedings of the IFIP TC6/TC11 Sixth Joint Working Conference on Communications and Multimedia Security, pp. 57–77. Kluwer, Dordrecht (2002)
Acknowledgments
We would like to thank Fabian Monrose for providing some useful feedback on potential applications of our work to other types of protocols. We would also like to thank and acknowledge the co-authors of the previous versions of this work, John Mullins, John McHugh and Édouard Reich, who have accompanied us in the initial phases of this endeavour.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Boteanu, D., Fernandez, J.M. A comprehensive study of queue management as a DoS counter-measure. Int. J. Inf. Secur. 12, 347–382 (2013). https://doi.org/10.1007/s10207-013-0197-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10207-013-0197-6