Abstract
Many present-day companies carry out a huge amount of daily operations through the use of their information systems without ever having done their own enterprise modeling. Business process mining is a well-proven solution which is used to discover the underlying business process models that are supported by existing information systems. Business process discovery techniques employ event logs as input, which are recorded by process-aware information systems. However, a wide variety of traditional information systems do not have any in-built mechanisms with which to collect events (representing the execution of business activities). Various mechanisms with which to collect events from non-process-aware information systems have been proposed in order to enable the application of process mining techniques to traditional information systems. Unfortunately, since business processes supported by traditional information systems are implicitly defined, correlating events into the appropriate process instance is not trivial. This challenge is known as the event correlation problem. This paper presents an adaptation of an existing event correlation algorithm and incorporates it into a technique in order to collect event logs from the execution of traditional information systems. The technique first instruments the source code to collect events together with some candidate correlation attributes. Based on several well-known design patterns, the technique provides a set of guidelines to support experts when instrumenting the source code. The event correlation algorithm is subsequently applied to the data set of events to discover the best correlation conditions, which are then used to create event logs. The technique has been semi-automated to facilitate its validation through an industrial case study involving a writer management system and a healthcare evaluation system. The study demonstrates that the technique is able to discover an appropriate correlation set and obtain well-formed event logs, thus enabling business process mining techniques to be applied to traditional information systems.








Similar content being viewed by others
References
Buckl, S., et al.: A meta-language for enterprise architecture analysis. In: Halpin, T. (ed.) Enterprise, Business-Process and Information Systems Modeling, pp. 511–525. Springer, Berlin (2011)
Barn, B., Clark, T.: Revisiting Naur’s programming as theory building for enterprise architecture modelling. In: Mouratidis, H., Rolland, C. (eds.) Advanced Information Systems Engineering, pp. 229–236. Springer, Berlin (2011)
Paradauskas, B., Laurikaitis, A.: Business knowledge extraction from legacy informations systems. Inf. Technol. Control 35(3), 214–221 (2006)
van der Aalst, W., Weijters, A.J.M.M.: Process mining. In: Dumas, M., van der Aalst, W., Ter Hofstede, A. (eds.) Process-aware Information Systems: Bridging People and Software Through Process Technology, pp. 235–255. Wiley, New York (2005)
Pérez-Castillo, R., et al.: Toward Obtaining Event Logs from Legacy Code. Business Process Management Workshops (BPI’10). Lecture Notes in Business Information Processing (LNBIP 66–Part 2), pp. 201–207 (2010)
Pérez-Castillo, R., et al.: Generating event logs from non-process-aware systems enabling business process mining. Enterp. Inf. Syst. J. 5(3), 301–335 (2011)
Pérez-Castillo, R., et al.: Process mining through dynamic analysis for modernizing legacy systems. IET Softw. J. 5(3), 304–319 (2011)
Motahari-Nezhad, H.R., et al.: Event correlation for process discovery from web service interaction logs. VLDB J. 20(3), 417–444 (2011)
Pérez-Castillo, R.: Experiment results about assessing event correlation in non-process-aware information systems (2012). http://alarcos.esi.uclm.es/per/rpdelcastillo/CorrelationExp.html#correlation
Ingvaldsen, J.E., Gulla, J.A.: Preprocessing support for large scale process mining of SAP transactions. Business Process Intelligence Workshop (BPI’07). In: LNCS, vol. 4928, pp. 30–41 (2008)
Günther, C.W., van der Aalst, W.M.P.: A generic import framework for process event logs. Business Process Intelligence Workshop (BPI’06). In: LNCS, vol. 4103, pp. 81–92 (2007)
McGarry, K.: A survey of interestingness measures for knowledge discovery. Knowl. Eng. Rev. 20(1), 39–61 (2005)
Burattin, A., Vigo, R.: A Framework for Semi-Automated Process Instance Discovery from Decorative Attributes. In: IEEE Symposium on Computational Intelligence and Data Mining (CIDM’11), pp. 176–183. Paris, France (2011)
Rozsnyai, S., Slominski, A., Lakshmanan, G.T.: Discovering Event Correlation Rules for Semi-Structured Business Processes. In: Proceedings of the 5th ACM international conference on Distributed event-based system, pp. 75–86. ACM, New York (2011)
Ferreira, D., Gillblad, D.: Discovering process models from unlabelled event logs. In: Dayal, U. (ed.) Business Process Management, pp. 143–158. Springer, Berlin (2009)
Kato, K., Kanai, T., Uehara, S.: Source code partitioning using process mining. In: Rinderle-Ma, S., Toumani, F., Wolf, K. (eds.) Business Process Management, pp. 38–49. Springer, Berlin (2011)
Myers, J., Grimaila, M.R., Mills, R.F.: Adding Value to Log Event Correlation Using Distributed Techniques. In: Proceedings of the Sixth Annual Workshop on Cyber Security and Information Intelligence Research, pp. 1–4. ACM, Oak Ridge (2010)
Hammoud, N.: Decentralized Log Event Correlation Architecture. In: Proceedings of the International Conference on Management of Emergent Digital EcoSystems, pp. 480–482. ACM, France (2009)
Zou, Y., Hung, M.: An Approach for Extracting Workflows from E-Commerce Applications. In: Proceedings of the Fourteenth International Conference on Program Comprehension. IEEE Computer Society, pp. 127–136 (2006)
Ratiu, D.: Reverse Engineering Domain Models from Source Code. In: International Workshop on Reverse Engineering Models from Software Artifacts (REM’09), pp. 13–16. Simula Research Laboratory, Lille, France (2009)
Eckerson, W.: Three tier client/server architecture: achieving scalability, performance and efficiency in client server applications. Open Inf. Syst. 10(1), 3 (1995)
Gamma, E., et al.: Design Patterns: Elements of Reusable Object-Oriented Software. Longman Publishing Co. ed., Inc., Boston, Addison Wesley, USA (1995)
Oracle Inc. Core J2EE Patterns: Data Access Object (http://java.sun.com/blueprints/corej2eepatterns/Patterns/DataAccessObject.html). Core J2EE Pattern Catalog 2001 [cited 11/04/2012]
Van der Aalst, W.M.P., et al.: ProM : The Process Mining Toolkit. In: 7th International Conference on Business Process Management (BPM’09)–Demonstration Track, pp. 1–4. Springer, Germany (2009)
Fluxicon Process Laboratories, XES 1.0 Standard Definitio (Extensible Event Stream). http://www.xes-standard.org/ (2009)
Runeson, P., Höst, M.: Guidelines for conducting and reporting case study research in software engineering. Empirical Softw. Eng. 14(2), 131–164 (2009)
Yin, R.K.: Case Study Research. Design and Methods, 3rd edn. Sage, London (2003)
Medeiros, A.K., Weijters, A.J., Aalst, W.M.: Genetic process mining: an experimental evaluation. Data Min. Knowl. Discov. 14(2), 245–304 (2007)
Acknowledgments
This work was supported by the FPU Spanish Program and the R&D projects ALTAMIRA (PII2I09-0106-2463), PEGASO/MAGO (TIN2009-13718-C02-01), MAESTRO (Alarcos Quality Center) and MOTERO (JCCM and FEDER, PEII11-0366-9449). Additionally, this work was supported by the University of Innsbruck.
Author information
Authors and Affiliations
Corresponding author
Additional information
Communicated by Dr. Tony Clark, Balbir Barn, Alan Brown, and Florian Matthes.
Appendix 1: Reference and discovered business process models
Appendix 1: Reference and discovered business process models
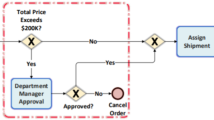
This appendix provides the reference business process models that are supported by the two traditional information systems under study. Owing to space limitations, each figure depicts the reference model and different variations of the models discovered as regards the reference model in terms of business tasks that were not discovered by means of the different correlations sets.
Firstly, Fig. 9 depicts the reference model of the AELG-member systems and presents the four variations of business process models discovered using the correlation sets A, B, C and D (cf. Sect. 4.4). The missing business tasks for each correlation data set are highlighted and the correlation set ID are specified (A, B, C and D).
Secondly, Fig. 10 provides the same information for the CHES system. In this case, two different business process models were discovered using correlation sets E and F (cf. Sect. 4.4).
Rights and permissions
About this article
Cite this article
Pérez-Castillo, R., Weber, B., de Guzmán, I.GR. et al. Assessing event correlation in non-process-aware information systems. Softw Syst Model 13, 1117–1139 (2014). https://doi.org/10.1007/s10270-012-0285-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10270-012-0285-5