Abstract
A major design concern in modern software development frameworks is to ensure that mechanisms for updating code running on remote devices comply with given safety specifications. This paper presents a delta-oriented approach for implementing product lines where software reuse is achieved at the three levels of state-diagram modeling, C/\(\text {C}^{_{_{_{++}}}} \)source code and binary code. A safety specification is expressed on the properties of reusable software libraries that can be dynamically loaded at run time after an over-the-air update. The compilation of delta-engineered code is certified using the framework of proof-carrying code in order to guarantee safety of software updates on remote devices. An empirical evaluation of the computational cost associated with formal safety checks is done by means of experimentation.












Similar content being viewed by others
References
Albert, E., Arenas, P., Puebla, G., Hermenegildo, M.: Reduced Certificates for Abstraction-Carrying Code, pp. 163–178. Springer, Berlin (2006). https://doi.org/10.1007/11799573_14
Apel, S., Batory, D., Kstner, C., Saake, G.: Feature-Oriented Software Product Lines: Concepts and Implementation. Springer, Berlin (2013). Incorporated
Arndt, J., Behlert, S., et al.: SUSE Linux. Technical report. Novel Inc, Washington (2006)
Ayavoo, D., Pont, M.J., Parker, S.: Observing the development of a reliable embedded system. In: Proceedings of the 10th Ada-Europe International Conference on Reliable Software Technologies, Springer, Berlin. Ada-Europe’05, pp. 167–179 (2005). https://doi.org/10.1007/11499909_14
Bailey, J.W., Basili, V.R.: A meta-model for software development resource expenditures. In: Proceedings of the 5th International Conference on Software Engineering. IEEE Press, Piscataway, ICSE ’81, pp. 107–116 (1981)
Basili, V.R., Weiss, D.M.: A methodology for collecting valid software engineering data. IEEE Trans. Softw. Eng. 10(6), 728–738 (1984). https://doi.org/10.1109/TSE.1984.5010301
Basili, V.R., Selby, R.W., Hutchens, D.H.: Experimentation in software engineering. IEEE Trans. Softw. Eng. 12(7), 733–743 (1986)
Batory, D., Sarvela, J., Rauschmayer, A.: Scaling step-wise refinement. IEEE Trans. Softw. Eng. 30(6), 355–371 (2004)
Bavota, G.: Using structural and semantic information to support software refactoring. In: 2012 34th International Conference on Software Engineering (ICSE), pp. 1479–1482 (2012). https://doi.org/10.1109/ICSE.2012.6227057
Berger, T., Rublack, R., Nair, D., Atlee, J.M., Becker, M., Czarnecki, K., Wąsowski, A.: A survey of variability modeling in industrial practice. In: Proceedings of the Seventh International Workshop on Variability Modelling of Software-Intensive Systems, ACM, New York, VaMoS ’13, pp. 7:1–7:8 (2013). https://doi.org/10.1145/2430502.2430513
Bernardeschi, C., Francesco, N.D., Lettieri, G., Martini, L., Masci, P.: Decomposing bytecode verification by abstract interpretation. ACM Trans Program Lang Syst 31(1), 3:1–3:63 (2008). https://doi.org/10.1145/1452044.1452047
Bertot, Y., Castran, P.: Interactive Theorem Proving and Program Development: Coq’Art The Calculus of Inductive Constructions, 1st edn. Springer, Berlin (2010)
Bezemer, C.P., Mcintosh, S., Adams, B., German, D.M., Hassan, A.E.: An empirical study of unspecified dependencies in make-based build systems. Empirical Softw Engg 22(6), 3117–3148 (2017). https://doi.org/10.1007/s10664-017-9510-8
Biere, A., Biere, A., Heule, M., van Maaren, H., Walsh, T.: Handbook of Satisfiability Volume 185: Frontiers in Artificial Intelligence and Applications. IOS Press, Amsterdam (2009)
Bordeaux, L., Hamadi, Y., Zhang, L.: Propositional satisfiability and constraint programming: a comparative survey. ACM Comput. Surv. 38(4), 1–62 (2006). https://doi.org/10.1145/1177352.1177354
Brown, A.W., Wallnau, K.C.: A framework for evaluating software technology. IEEE Softw. 13(5), 39–49 (1996). https://doi.org/10.1109/52.536457
Bryant, R.E., O’Hallaron, D.R.: Computer Systems: A Programmer’s Perspective, 2nd edn. Addison-Wesley Publishing Company, New York (2010)
Burow, N., Carr, S.A., Brunthaler, S., Payer, M., Nash, J., Larsen, P., Franz, M.: Control-flow integrity: precision, security, and performance. ACM Comput. Surv. 50:16:1–16, 33 (2017). https://doi.org/10.1145/3054924
Calcote, J.: Autotools: A Practitioner’s Guide to GNU Autoconf, Automake, and Libtool. No Starch Press, San Francisco (2010)
Calder, B., Phillips, L.W., Tybout, A.: The concept of external validity. J. Consum. Res. 9, 240–244 (1982)
Catuogno, L., Visconti, I.: A format-independent architecture for run-time integrity checking of executable code. In: Cimato, S., Persiano, G., Galdi, C. (eds.) Security in Communication Networks, pp. 219–233. Springer, Berlin (2003)
Chesta, C., Damiani, F., Dobriakova, L., Guernieri, M., Martini, S., Nieke, M., Rodrigues, V., Schuster, S.: A toolchain for delta-oriented modeling of software product lines. In: Leveraging Applications of Formal Methods, Verification and Validation: Discussion, Dissemination, Applications—7th International Symposium, ISoLA 2016, Imperial, Corfu, Greece, October 10–14, 2016, Proceedings, Part II, pp. 497–511 (2016). https://doi.org/10.1007/978-3-319-47169-3_40
Clements, P., Northrop, L.: Software Product Lines: Practices and Patterns. Addison Wesley Longman, Boston (2001)
Cousot, P., Cousot, R.: Abstract interpretation: a unified lattice model for static analysis of programs by construction or approximation of fixpoints. In: Proceedings of the 4th ACM SIGACT-SIGPLAN Symposium on Principles of Programming Languages, ACM, New York, NY, USA, POPL ’77, pp. 238–252 (1977). https://doi.org/10.1145/512950.512973
De Moura, L., Bjørner, N.: Z3: An efficient SMT solver. In: Proceedings of the Theory and Practice of Software, 14th International Conference on Tools and Algorithms for the Construction and Analysis of Systems, Springer, Berlin, TACAS’08/ETAPS’08, pp. 337–340 (2008)
DeTreville, J., Leijen, D., Swierstra, W.: Dependable software deployment. Technical report, Microsoft Research (2006)
Donald, J.: Improved Portability of Shared Libraries. Technical report, Princeton University, Princeton (2003)
Drepper, U.: How to Write Shared Libraries. Technical Report. Red Hat Inc, Raleigh (2011)
Drusinsky, D.: Chapter 1—formal requirements and finite automata overview. In: Drusinsky, D. (ed) Modeling and Verification Using UML Statecharts, Newnes, Burlington, pp. 1–41 (2006). https://doi.org/10.1016/B978-075067949-7/50003-9
Drusinsky, D.: Chapter 2—Statecharts. In: Drusinsky, D. (ed.) Modeling and Verification Using UML Statecharts, pp. 43–102. Newnes, Burlington (2006). https://doi.org/10.1016/B978-075067949-7/50004-0
Ducasse, S., Nierstrasz, O., Schärli, N., Wuyts, R., Black, A.P.: Traits: a mechanism for fine-grained reuse. ACM Trans. Program Lang. Syst. 28(2), 331–388 (2006). https://doi.org/10.1145/1119479.1119483
European Commission (2017) eCall: Time saved = lives saved. https://ec.europa.eu/digital-single-market/en/ecall-time-saved-lives-saved
Fenton, N.E.: Software Metrics: A Rigorous Approach. Chapman & Hall Ltd, London (1991)
Garfinkel, S.: PGP: Pretty Good Privacy, 1st edn. O’Reilly & Associates Inc, Sebastopol (1996)
Ge, Y., de Moura, L.: Complete instantiation for quantified formulas in satisfiabiliby modulo theories. In: Bouajjani, A., Maler, O. (eds) Computer Aided Verification: 21st International Conference, CAV 2009, Grenoble, France, June 26–July 2, 2009. Proceedings, Springer, Berlin, pp. 306–320 (2009). https://doi.org/10.1007/978-3-642-02658-4_25
GmbH VSI (2018) RTT-DCC: Data and Control Coupling Analyser. https://www.verified.de/products/rtt-dcc/. Accessed 31 July 2018
Gosling, J., Joy, B., Steele, G.L., Bracha, G., Buckley, A.: The Java Language Specification, Java SE 8 Edition, 1st edn. Addison-Wesley Professional, Boston (2014)
Guo, C., Ren, S., Jiang, Y., Wu, P.L., Sha, L., Berlin, R.B. Jr: Transforming medical best practice guidelines to executable and verifiable statechart models. In: Proceedings of the 7th International Conference on Cyber-Physical Systems. IEEE Press, Piscataway, ICCPS ’16, pp 34:1–34:10 (2016)
Haber, A., Rendel, H., Rumpe, B., Schaefer, I., van der Linden, F.: Hierarchical variability modeling for software architectures. In: Proceedings of the 15th International Software Product Line Conference, IEEE, pp. 150–159(2011). https://doi.org/10.1109/SPLC.2011.28
Habets, T.: Shared libraries diamond problem (2012). https://blog.habets.se/2012/05/Shared-libraries-diamond-problem.html. Accessed 31 July 2018
Hallsteinsen, S., Hinchey, M., Park, S., Schmid, K.: Dynamic software product lines. Computer 41(4), 93–95 (2008). https://doi.org/10.1109/MC.2008.123
Harel, D., Politi, M.: Modeling Reactive Systems with Statecharts: The Statemate Approach, 1st edn. McGraw-Hill Inc, New York (1998)
Hawkins, R.D., Kelly, T.P.: Software safety assurance—what is sufficient? In: 4th IET International Conference on Systems Safety 2009. Incorporating the SaRS Annual Conference, pp. 1–6 (2009). https://doi.org/10.1049/cp.2009.1542
Hermenegildo, M.V., Albert, E., López-García, P., Puebla, G.: Abstraction carrying code and resource-awareness. In: Proceedings of the 7th ACM SIGPLAN International Conference on Principles and Practice of Declarative Programming, ACM, New York, PPDP ’05, pp. 1–11 (2005). https://doi.org/10.1145/1069774.1069775
Hutchens, D.H., Basili, V.R.: System structure analysis: clustering with data bindings. IEEE Trans. Softw. Eng. 11(8), 749–757 (1985). https://doi.org/10.1109/TSE.1985.232524
Hutchinson, J., Rouncefield, M., Whittle, J.: Model-driven engineering practices in industry. In: Proceedings of the 33rd International Conference on Software Engineering, ACM, New York, NY, USA, ICSE ’11, pp. 633–642 (2011). https://doi.org/10.1145/1985793.1985882
Iscoe, N., Williams, G.B., Arango, G.: Domain modeling for software engineering., In: [1991 Proceedings] 13th International Conference on Software Engineering, pp. 340–343 (1991). https://doi.org/10.1109/ICSE.1991.130660
Jiang, L., Su, Z.: Profile-guided program simplification for effective testing and analysis. In: Proceedings of the 16th ACM SIGSOFT International Symposium on Foundations of Software Engineering, ACM, New York, SIGSOFT ’08/FSE-16, pp. 48–58 (2008). https://doi.org/10.1145/1453101.1453110
Kernighan, B.W., Ritchie, D.M.: The M4 Macro Processor. Technical report, Bell Laboratories (1977)
Kirovski, D., Drinić, M., Potkonjak, M.: Enabling trusted software integrity. SIGPLAN Not. 37(10), 108–120 (2002). https://doi.org/10.1145/605432.605409
Krueger, C.W.: Software reuse. ACM Comput. Surv. 24(2), 131–183 (1992). https://doi.org/10.1145/130844.130856
Lienhardt, M., Damiani, F., Testa, L., Turin, G.: On checking delta-oriented product lines of statecharts. Sci. Comput. Program. 166, 3–34 (2018). https://doi.org/10.1016/j.scico.2018.05.007
Lindholm, T., Yellin, F.: Java Virtual Machine Specification, 2nd edn. Addison-Wesley Longman Publishing Co. Inc, Boston (1999)
Martin, J.C.: Introduction to Languages and the Theory of Computation, 2nd edn. McGraw-Hill Higher Education, New York (1997)
McCabe, T.J.: A complexity measure. In: Proceedings of the 2nd International Conference on Software Engineering. IEEE Computer Society Press, Los Alamitos, ICSE ’76, p. 407 (1976)
Menon, V., Pingali, K.: A case for source-level transformations in matlab. SIGPLAN Not. 35(1), 53–65 (1999). https://doi.org/10.1145/331963.331972
Moura, L., Bjørner, N.: Satisfiability modulo theories: an appetizer. In: Oliveira, M.V., Woodcock, J. (eds.) Formal Methods: Foundations and Applications, pp. 23–36. Springer, Berlin (2009). https://doi.org/10.1007/978-3-642-10452-7_3
Necula, G.C.: Proof-carrying code. In: Proceedings of the 24th ACM SIGPLAN-SIGACT Symposium on Principles of Programming Languages, ACM, New York, POPL ’97, pp. 106–119 (1997). https://doi.org/10.1145/263699.263712
Nelson, G. (ed.): Systems Programming with Modula-3. Prentice-Hall Inc, Upper Saddle River (1991)
Oliveira, N., Varanda Pereira, M.J., Henriques, P.R., da Cruz, D.: Domain-specific languages—a theoretical survey. In: Proceedings of the 3rd Compilers, Programming Languages, Related Technologies and Applications (CoRTA’2009), pp. 35–46 (2009)
Parkes, A.P.: Finite State Transducers, pp. 189–207. Springer, London (2008). https://doi.org/10.1007/978-1-84800-121-3_8
Percival, C.: Matching with mismatches and assorted applications. Ph.D. thesis, University of Oxford (2006)
Pohl, K., Böckle, G., Linden, F.J.V.D.: Software Product Line Engineering: Foundations, Principles and Techniques. Springer, Secaucus (2005)
Raistrick, C., Francis, P., Wright, J.: Model Driven Architecture with Executable UML (TM). Cambridge University Press, New York (2004)
Ramsey, H.R., Atwood, M.E., Van Doren, J.R.: Flowcharts versus program design languages: an experimental comparison. Commun. ACM 26(6), 445–449 (1983). https://doi.org/10.1145/358141.358149
Rodrigues, V., Lopes, J.C., Moreira, A.: An hybrid design solution for spacecraft simulators. In: Proceedings of the Forum at the CAiSE’08 Conference, Montpellier, France, June 18–20, 2008, pp. 29–32 (2008)
Rodrigues, V., Akesson, B., Florido, M., de Sousa, S.A.M., Pedroso, J.A.P., Vasconcelos, P.: Certifying execution time in multicores. Sci. Comput. Program. 111(P3), 505–534 (2015). https://doi.org/10.1016/j.scico.2015.06.006
Røst, T.B., Seidl, C., Yu, I.C., Damiani, F., Johnsen, E.B., Chesta, C.: Hyvar. In: Mann, Z, Á., Stolz, V. (eds.) Advances in Service-Oriented and Cloud Computing. Springer, Cham, Communications in Computer and Information Science, vol. 824, pp. 159–163 (2018). https://doi.org/10.1007/978-3-319-79090-9_12
Rumbaugh, J., Jacobson, I., Booch, G.: Unified Modeling Language Reference Manual, 2nd edn. Pearson Higher Education, London (2004)
Schaefer, I., Bettini, L., Bono, V., Damiani, F., Tanzarella, N.: Delta-oriented programming of software product lines. In: Bosch, J., Lee, J. (eds). Software Product Lines: Going Beyond (SPLC 2010). Springer, Lecture Notes in Computer Science, vol. 6287, pp. 77–91 (2010). https://doi.org/10.1007/978-3-642-15579-6_6
Schaefer, I., Rabiser, R., Clarke, D., Bettini, L., Benavides, D., Botterweck, G., Pathak, A., Trujillo, S., Villela, K.: Software diversity: state of the art and perspectives. Int. J. Softw. Tools Technol. Transfer 14(5), 477–495 (2012). https://doi.org/10.1007/s10009-012-0253-y
Schürr, A., Selic, B. (eds.): Model driven engineering languages and systems. In: 12th International Conference, MODELS 2009, Denver, CO, USA, October 4–9, 2009. Proceedings, Lecture Notes in Computer Science, vol. 5795. Springer, Berlin (2009). https://doi.org/10.1007/978-3-642-04425-0
Seidl, C., Schaefer, I., Aßmann, U.: Deltaecore—a model-based delta language generation framework. In: Modellierung 2014, 19.-21. März 2014, Wien, Österreich, pp. 81–96 (2014)
Shneiderman, B., Mayer, R., McKay, D., Heller, P.: Experimental investigations of the utility of detailed flowcharts in programming. Commun. ACM 20(6), 373–381 (1977). https://doi.org/10.1145/359605.359610
Stallman, R.M., McGrath, R.: GNU Make: A Program for Directed Compilation. Free Software Foundation, Boston (2002)
Team CAS (2004) Clarification of Structural Coverage Analyses of Data Coupling and Control Coupling. https://www.faa.gov/aircraft/air_cert/design_approvals/air_software/cast/cast_papers/archive/
Thüm, T., Apel, S., Kästner, C., Schaefer, I., Saake, G.: A classification and survey of analysis strategies for software product lines. ACM Comput. Surv. 47(1), 6:1–6:45 (2014a). https://doi.org/10.1145/2580950
Thüm, T., Kästner, C., Benduhn, F., Meinicke, J., Saake, G., Leich, T.: Featureide: an extensible framework for feature-oriented software development. Sci. Comput. Program. 79, 70–85 (2014b). https://doi.org/10.1016/j.scico.2012.06.002
Tichy, W.F., Lukowicz, P., Prechelt, L., Heinz, E.A.: Experimental evaluation in computer science: a quantitative study. J. Syst. Softw. 28(1), 9–18 (1995). https://doi.org/10.1016/0164-1212(94)00111-Y
Tu, Q., Godfrey, M.W.: The build-time software architecture view. In: Proceedings IEEE International Conference on Software Maintenance. ICSM 2001, pp. 398–407 (2001). https://doi.org/10.1109/ICSM.2001.972753
Turner, A.J.: Iterative enhancement: a practical technique for software development. IEEE Trans. Softw. Eng. 1(1), 390–396 (1975). https://doi.org/10.1109/TSE.1975.6312870
Vaughan, G.V, Elliston, B., Tromey, T., Taylor, I.L., Mac Kenzie, D.: GNU Autoconf, Automake and Libtool. Expert Insight into Porting Software and Building Large Projects using GNU Autotools. New Riders, Indianapolis (2001)
Weiss, D.M., Basili, V.R.: Evaluating software development by analysis of changes: some data from the software engineering laboratory. IEEE Trans. Softw. Eng. SE–11(2), 157–168 (1985). https://doi.org/10.1109/TSE.1985.232190
Weyuker, E.J.: Evaluating software complexity measures. IEEE Trans. Softw. Eng. 14(9), 1357–1365 (1988). https://doi.org/10.1109/32.6178
Williams, M., Grajales, C., Kurkiewicz, D.: Assumptions of multiple regression: correcting two misconceptions. Pract. Assess. Res. Eval. 18, 1 (2013)
Wolverton, R.W.: The cost of developing large-scale software. IEEE Trans. Comput. C–23(6), 615–636 (1974). https://doi.org/10.1109/T-C.1974.224002
Wong, B., Czajkowski, G., Daynes, L.: Dynamically loaded classes as shared libraries: an approach to improving virtual machine scalability. In: Proceedings International Parallel and Distributed Processing Symposium (2003). https://doi.org/10.1109/IPDPS.2003.1213123
Yourdon, E.: Techniques of Program Structure and Design, 1st edn. Prentice Hall PTR, Upper Saddle River (1986)
Yu, D., Hamid, N.A., Shao, Z.: Building certified libraries for PCC: dynamic storage allocation. In: 12th European Symposium on Programming on Science of Computer Programming, vol. 50, no. 1, pp. 101–127 (2004). https://doi.org/10.1016/j.scico.2004.01.003 (ESOP 2003)
Acknowledgements
We thank the anonymous SoSyM referees for comments and suggestions for improving the paper.
Author information
Authors and Affiliations
Corresponding author
Additional information
Communicated by Dr. Philippe Collet.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This work was partially supported by the European Commission within the Project HyVar (http://www.hyvar-project.eu/), Grant Agreement H2020-644298.
Appendices
Appendices
1.1 Appendix A: Consistency check using the Z3 SMT solver
This appendix shows the Z3 [25] SMT solver scripts that check the satisfiability and validity of the consistency specification established between the state-diagram and build-system DOP product lines. The consistency \(\varSigma \)-theory [57] is formalized using constraints between pairs of deltas that share the same index in the application order. Further, the configuration knowledge (CK) of the DOP-SPL is consistent only if there is an activation rule for every delta index. The activation rules are defined in conjunctive normal form (CNF) and implicitly determine the application order.
In order to demonstrate the use of Z3 encoding of the \(\varSigma \)-theory presented in Sect. 5.2 consider two delta indexes and, correspondingly, two activation rules. Next, we present the CKs of the two DOP-SPLs under consideration. The delta sequences under consideration are \(\langle \delta _1 \mathbin {;} \delta _1 \rangle \) and \(\langle \dot{\delta }_1 \mathbin {;} \dot{\delta }_1 \rangle \), respectively.
-
1.
Configuration Knowledge of the State Diagram DOP-SPL:
\(F_1\) | \(\delta _1\) |
|---|---|
\(F_1 \wedge F_2\) | \(\delta _2\) |
-
2.
Configuration Knowledge of the Filenames DOP-SPL:
\(F_1\) | \(\dot{\delta }_1\) |
|---|---|
\(F_1 \wedge F_2\) | \(\dot{\delta }_2\) |
The Z3 definitions are given in Listing 1. The encoding of theory specifying the cross-consistency between the state-diagram DOP-SPL and the build-system DOP-SPL is presented in Listing 2, and the encoding of the DOP semantics with respect to cross-consistency between SPLs is given in Listing 2. The source script is available at https://github.com/esmifro/CertifiedDOP/tree/master/z3.
Examples of valid and unsatisfiable instances of product lines are described in Listing 4, Listing 5 and Listing 6.



The following encoding SPL shows that both deltas have the same position in the order and both declare the functions named name_1 and name_2 and the corresponding filenames (which must have the same name). Further, the predicate ck is satisfiable for every formula and delta index. This instance corresponds to a single virtual product (cf. Sect. 5) that is satisfiable.
The constraints (assert (=> (ck formula_1 index_2) false)) and (assert (=> (ck formula_1 index_2) false)) are necessary to properly encode CK (1) and CK (2).

Now consider Configuration Knowledge that is inconsistent, where \(F_2\) is disabled by writing (assert (= false feature_2)). In this case, the activation rule for index_2 is not satisfiable. Therefore, the answer from the SMT solver is going to be “unsat”.

Now consider the case of inconsistency between deltas, \(\delta _1\) and \(\dot{\delta }_1\), written (assert (=(state “name_1” index_1) false)). The answer from the SMT solver is again going to be “unsat”.

1.2 Appendix B: The COQ proof system
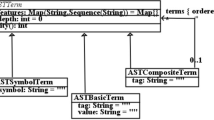
This appendix shows the COQ definitions required to define the safety specification presented in Sect. 6. Listing 1 shows the inductive definitions for symbols, where the ELF type is an “ascii,” table of symbols and delta actions. The dynamic semantics of the delta-oriented “apply” function is encoded by predicate Apply in Listing 2. The definitions for types of symbols and table of symbols are shown in Listing 3.



Listing 4 shows the encoding of typed symbols and delta actions (\(e \mathbin {:} \tau \)), and the safety predicate Resolved. Finally, the inductive definitions for well-typed values (table of symbols) are shown in Listing 5. The proof of the safety theorem, which is presented in Sect. 6, is shown in Listing 6, and the required tactics to solve the verification conditions are given in Listing 7.




1.3 Appendix C: Haskell interpreter for the PCC agent
This appendix shows the Haskell source code that implements an interpreter for the big-step semantics of the PCC Agent presented in Table 6 and Sect. 6. The complete source-code project is available at https://github.com/esmifro/CertifiedDOP.
Listing 1 shows the algebraic datatypes used to represent tables of symbols, the verification-condition proof result and other type constructors for files and directories. The internal function signatures shown in Listing 4 are defined exclusively over the Internal domain. Listing 2 shows the algebraic datatypes and types used by the interpreter using Monad transformers (runCheck). The correspondence between high-level syntax and system-(Linux)level syntax is stored inside the map MetaMap. Abstract programs are created using Command.


The interpreter shown in Listing 3 implements the big-step semantics of the PCC Agent. For each of the big-step relations, that is, for variables, expressions and commands, there is a correspondent interpretation function. The map between abstract functions and internal functions is defined in Listing 4.


Finally, the function that runs the interpreter with a given set of arguments is shown in Listing 5.

Rights and permissions
About this article
Cite this article
Rodrigues, V., Donetti, S. & Damiani, F. Certifying delta-oriented programs. Softw Syst Model 18, 2875–2906 (2019). https://doi.org/10.1007/s10270-018-00704-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10270-018-00704-x