Abstract
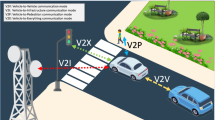
Vehicular ad hoc network (VANET) can increase the traffic efficiency by allowing arbitrary vehicles to broadcast the messages to other vehicles and road side units (RSUs). But due to the openness of the wireless network, VANET is very vulnerable to forgery attack. Thus, the security and privacy of the messages should be provided, to make sure that the real identity of vehicles can be traceable by authorized party while not be revealed to other vehicles. The existing solutions can neither satisfy the privacy requirement nor have an effective message verification scheme on vehicles. A secure and privacy protect authentication scheme is proposed in this paper, which comprises local authentication and roaming authentication for VANET based on bilinear pairing and can provide secure communications and anonymous authentication among RSUs and vehicles.









Similar content being viewed by others
References
Kim, I., Lee, D., Kim, K.J., Lee, J.: Flexible authorization in home network environments. Clust. Comput. 15, 3–15 (2012). doi:10.1007/s10586-010-0142-7
Park, C., Kim, H., Jung, I.: Traffic-aware routing protocol for wireless sensor networks. Clust. Comput. 15(1), 27–36 (2012). doi:10.1007/s10586-010-0146-3
Hubaux, J.P., Capkun, S., Luo, J.: The security and privacy of smart vehicles. IEEE Secur. Priv. 2(3), 49–55 (2004). doi:10.1109/MSP.2004.26
Sampigethaya, K., Huang, L., Li, M., Poovendran, R., Matsuura, K., Sezaki, K.: CARAVAN: providing location privacy for VANET. In: Proceedings of the Workshop on Embedded Security in Cars (ESCAR05) (2005). doi:10.1.1.102.3150
Wasef, A., Shen, X.: REP: location privacy for VANETs using random encryption periods. Mob. Netw. Appl. 15, 172–185 (2010). doi:10.1007/s11036-009-0175-4
Qin, B., Wu, Q.: Distributed privacy-preserving secure aggregation in vehicular communication. In: Third International Conference on Intelligent Networking and Collaborative Systems, pp. 100–107 (2011). doi:10.1109/INCoS.2011.78
Lu, R., Lin, X., Zhu, H.: ECPP: efficient conditional privacy preservation protocol for secure vehicular communications. In: The Proceedings of the IEEE INFOCOM, pp. 1229–1237 (2008). doi:10.1109/CIS.2010.120
Wasef, A., Lu, R., Lin, X., Shen, X.: Complementing public key infrastructure to secure vehicular ad hoc networks. Wirel. Commun. 17(5), 22–28 (2010). doi:10.1.1.228.7044
Jiang, Y., Shi, M., Shen, X., Lin, C.: BAT: a robust signature scheme for vehicular networks using binary authentication tree. IEEE Trans. Wirel. Commun. 8(4), 1974–1983 (2009). doi:10.1109/T-WC.2008.080280
Fujii, A., Ohtake, G., Hanaoka, G., Ogawa, K.: Anonymous authentication scheme for subscription services. In: Proceedings of the 11th International Conference, KES 2007 and XV. Italian Workshop on Neural Network Conference on Knowledge-Based Intelligent Information and Engineering Systems: Part III, pp. 975–983. Springer, Berlin (2007). doi:10.1007/978-3-540-74829-8_119
Slamanig, Stingl, C.: Investigating anonymity in group based anonymous authentication. Future Identity Inf. Soc. 298, 268–281 (2009). doi:10.1007/978-3-642-03315-5_20
Sun, Y., Feng, Z., Hu, Q.: An efficient distributed key management scheme for group-signature based anonymous authentication in VANET. Secur. Commun. Netw. 5(1), 79–86 (2012). doi:10.1002/sec.302
Zhang, S., Tao, J., Yuan, Y.: Anonymous authentication-oriented vehicular privacy protection technology research in VANET. In: International Conference on Electrical and Control Engineering (ICECE), pp. 4365–4368 (2011). doi:10.1109/ICECENG.2011.6057434
Xue, X., Ding, J.: LPA: a new location-based privacy-preserving authentication protocol in VANET. Secur. Commun. Netw. 5(1), 69–78 (2012). doi:10.1002/sec.305
Park, Y., Sur, C., Rhee, K.H.: A privacy-preserving location assurance protocol for location-aware services in VANETs. Wirel. Pers. Commun. 61(4), 779–791 (2011). doi:10.1007/s11277-011-0432-2
Chim, T.W., Yiu, S.M., Hui, L.C.K., Li, V.O.K.: SPECS: secure and privacy enhancing communications schemes for VANETs. Ad Hoc Netw. 9(2), 189–203 (2011). doi:10.1016/j.adhoc.2010.05.005
Baek, J., Safavi-Naini, R., Susilo, W.: Universal designated verifier signature proof (or how to efficiently prove knowledge of a signature). In: Advances in Cryptology-Asiacrypt’05, pp. 644–661. Springer, Berlin (2005). doi:10.1007/11593447_35
Zhang, F., Safavi-Naini, R., Susilo, W.: An efficient signature scheme from bilinear pairings and its applications. In: International Workshop on Practice and Theory in Public Key Cryptography-PKC’2004. Lecture Notes in Computer Science, pp. 277–290. Springer, Berlin (2004). doi:10.1007/978-3-540-24632-9_20
Bellare, M., Canetti, R., Krawczyk, H.: A modular approach to the design and analysis of authentication and key exchange protocols. In: Proceedings of the 30th Annual Symposium on the Theory of Computing, pp. 419–428 (1998). doi:10.1145/276698.276854
Canetti, R., Goldreich, O., Halevi, S.: The random oracle methodology, revisited. J. ACM 51(4), 557–594 (2004). doi:10.1145/1008731.1008734
Tin, Y.S.T., Vasanta, H., Boyd, C.: Protocols with security proofs for mobile applications. In: Information Security and Privacy: 9th Australasian Conference (ACISP 2004). LNCS, vol. 3108, pp. 358–369. Springer, Berlin (2004). doi:10.1007/978-3-540-27800-9_31
QualNet Simulator: http://www.ee.iitb.ac.in/~prakshep/IBMA_lit/manual/manual244.html. Accessed 17 June 2012
Lin, X., Sun, X., Ho, P.-H., Shen, X.: GSIS: a secure and privacy-preserving protocol for vehicular communications. IEEE Trans. Veh. Technol. 56(6), 3442–3456 (2007). doi:10.1109/TVT.2007.906878
Multiprecision Integer and Rational Arithmetic C/C++ Library (MIRACL). https://certivox.com/solutions/miracl-crypto-sdk/. Accessed 10 May 2012
Wu, Q., Domingo-Ferrer, J.: Balanced trustworthiness, safety, and privacy in vehicle-to-vehicle communications. IEEE Trans. Veh. Technol. 59(2), 559–573 (2010). doi:10.1109/TVT.2009.2034669
Acknowledgements
This work was sponsored by Natural Science Basic Research Plan in Shaanxi Province of China (2011JQ8042), the Fundamental Research Funds for the Central Universities (No. K5051301017), the National Natural Science Foundation of China (No. 60772136), and the National Science & Technology Major Projects (No. 2012ZX03001009).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zhu, H., Liu, T., Wei, G. et al. PPAS: privacy protection authentication scheme for VANET. Cluster Comput 16, 873–886 (2013). https://doi.org/10.1007/s10586-013-0260-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-013-0260-0