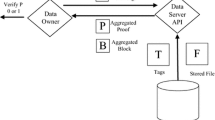
Abstract
Cloud storage is an important service of cloud computing. After data file is outsourced, data owner no longer physical controls over the storage. To efficiently verify these data integrity, several Proof of Retrievability (POR) schemes were proposed to achieve data integrity checking. The existing POR schemes offer decent solutions to address various practical issues, however, they either have a non-trivial (linear or quadratic) communication cost, or only support private verification. And most of the existing POR schemes exist active attack and information leakage problem in the data checking procedure. It remains open to design a secure POR scheme with both public verifiability and constant communication cost. To solve the above problems , we propose a novel preserving-private POR scheme with public verifiability and constant communication cost based on end-to-end aggregation authentication in this paper. To resist information leakage, we include zero-knowledge technique to hide the data in the integrity checking process. Our scheme is shown to be secure and efficient by security analysis and performance analysis. The security of our scheme is related to the Computational Diffie–Helleman Problem and Discrete logarithm problem. Finally, we also extend the POR scheme to support multi-file integrity checking and simulation results show that the verifier only needs less computational cost to achieve data integrity checking in our extended scheme.



Similar content being viewed by others
References
Timothy, G., Peter, M.M.: The nist definition of cloud computing. NIST SP 800–145 September (2011)
Amazon forum: major outage for amazon s3 and ec2. https://forums.aws.amazon.com/thread.jspa?threadID=19714&start=15&tstart=0. Accessed 2013
Amazon web service: summary of the amazon ec2 and amazon rds service disruption in the us east region. http://aws.amazon.com/message/65648/. Accessed 2013
Business insider: amazon cloud crash disaster permanently destroyed many customers data. http://www.businessinsider.com/amazon-lost-data-2011--4. Accessed 2013
Dropbox: dropbox forums on data loss topic. http://forums.dropbox.com/tags.php?tag=data-loss. Accessed 2013
Juels, A.; Kaliski, B.S. Jr.: Pors: proofs of retrievability for large files. In: Proceedings of the 14th ACM conference on Computer and communications security, CCS’07 584–597, New York, NY, USA, ACM (2007)
Ateniese, G., Burns, R., Curtmola, R., Herring, J., Kissner, L., Peterson, Z., Song, D.: Provable data possession at untrusted stores. Proceedings of the 14th ACM conference on Computer and communications security. CCS’07, pp. 598–609. NY, USA, ACM, New York (2007)
Shacham, H., Waters, B.: Compact proofs of retrievability, ASIACRYPT’08, LNCS 3123, pp. 90–107, Springer, Berlin (2008)
Dodis, Y., Vadhan, S., Wichs, D.: Proofs of retrievability via hardness amplification. In Proceedings of the 6th Theory of Cryptography Conference on Theory of Cryptography, TCC’09, pp. 109–127, Berlin, Heidelberg (2009)
Jia, X., Ee-Chien, C.: Towards efficient provable data possession. ASIACCS’12, pp. 79–80, May 2–4, Seoul, Korea (2012)
Yuan, J., Yu, S.: Proofs of retrievability with public verifiability and constant communication cost in cloud. CloudComputing’13, pp. 19–26 (2003)
Wang, Q., Wang, C., Ren, K., Lou, W., Li, J.: Enabling public auditability and data dynamics for storage security in cloud computing. IEEE Transactions on Parallel and Distributed Systems 22(5), 847–859 (2011)
Wang, C., Wang, Q., Ren, K., Lou, W.: Privacy-preserving public auditing for data storage security in cloud computing. In: Proc. of INFOCOM. IEEE pp. 525–533 (2010)
Boyang W., Li, B., Li, H., Li, H.: Certificateless public auditing for data integrity in the cloud. IEEE-CNS 2013, pp. 36–144, Washington D.C., October 14–16 (2013)
Wang, B., Chow, S.S.M., Li, M., Li, H.: Storing shared data on the cloud via security-mediator. IEEE-ICDCS 2013, pp. 124–133, Philadelphia, Pennsylvania, July 8–11 (2013)
Wang, B., Li, H., Li, M.: Privacy-preserving public auditing for shared cloud data supporting group dynamics. IEEE-ICC 2011 539–543 Budapest, Hungary, June 9–13 (2013)
Wang, B., Li, B., Li, H.: Public auditing for shared data with efficient user revocation in the cloud. IEEE-INFOCOM 2013, pp. 2904–2912, Turin, Italy, April 14–19 (2013)
Bellare, M.; Palacio, A.: The knowledge-of-exponent assumptions and 3-round zero-knowledge protocols. Proc. CRYPTO’04, LNCS 3152, Springer, Berlin 273–289 (2004)
Ma, D., Zhu, Y., Yu, M.: End-to-end aggregate authentication of time-series data. ACM Workshop on Asia Public-Key Cryptography (AsiaPKC) 51–66 May (2013)
Boneh, D., Boyen, X.: Short signatures without random oracles, Eurocrypt 2004. LNCS 3027, 56–73 (2004)
Xavier, B.:The uber-assumption family a unified complexity framework for bilinear groups, Pairing 2008, LNCS 5209, pp. 39–56 (2008)
Boneh, D., Boyen, X., Shacham, H.: Short group signatures. In Proc. Adv. CryptologyłCrypto, ser. LNCS, vol. 3152. Springer, New York pp. 41–45 (2004)
Acknowledgments
This work was supported partly by Beijing Natural Science Foundation (No. 4122024,4132056), Beijing Natural Science Foundation Program and Scientific Research Key Program of Beijing Municipal Commission of Education (No.KZ201210009011) and The importation and development of High-Caliber Talents Project of Beijing Municipal Institutions (NO:CIT&TCD201304004).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zhang, J., Tang, W. & Mao, J. Efficient public verification proof of retrievability scheme in cloud. Cluster Comput 17, 1401–1411 (2014). https://doi.org/10.1007/s10586-014-0394-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-014-0394-8