Abstract
Secure storage devices are a good example of the Internet of Things (IoTs), which require secure access control mechanisms via using the prominent pubic key cryptographic systems, e.g. RSA, ECC and related systems. However, quantum computer is in a position to attack RSA, ECC and other signature algorithms adopted by many storage devices. Therefore, storage security is facing severe threats. In this paper, an efficient hardware architecture based on multivariate scheme for storage devices is proposed. Multivariate scheme belongs to multivariate public key cryptography (MPKC), which uses affine transformations and central map transformations during cryptographic operations. The advantage of adopting multivariate scheme is that multivariate scheme is immune to quantum computer attack. The efficient hardware architecture is composed of processor module, cryptographic module, storage module, display module, power module, keyboard module, export module and terminal module (off-chip). We implement the hardware architecture on the methodology of TSMC-0.18 μm standard cell CMOS Application Specific Integrated Circuit. The implementation results show that the architecture based on multivariate scheme is very efficient and well suit for storage devices.
Similar content being viewed by others

1 Introduction
With the widespread use of personal computer and Internet, protecting personal data storage has become an increasingly crucial issue. Storage security of data is a specialty area of security that is concerned with securing data storage devices and the data that resides on these devices. According to the Storage Networking Industry Association (SNIA), data storage security represents the convergence of the storage technologies, networking communications, and security methodologies for the purpose of protecting and securing personal data. Historically, the focus of storage devices has been on both the vendor aspects of making storage devices more secure and the consumer aspects associated with using storage devices in secure ways.
Prominent examples of secure storage devices use RSA, ECC and other related cryptographic algorithms. However, quantum computer is in a position to attack RSA, ECC and other signature algorithms adopted by many storage devices. Therefore, storage security is facing severe threats. Fortunately, there are a few post-quantum candidates for storage devices, in which Multivariate Public Key Cryptography (MPKC) [1] is included. It uses affine transformations and central map transformations during cryptographic operations, which is believed to be hard on average for both classical and quantum computers [2].
Various schemes of multivariate schemes have been proposed during the past thirty years [3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19]. Hardware and software implementations of multivariate schemes have been one of the research focuses in areas of cryptography and engineering [20,21,22,23,24,25,26,27,28]. However, most of multivariate schemes are implemented on Application Specific Integrated Circuits (ASICs) and Field-Programmable Gate Arrays (FPGAs), few of them are used for storage devices.
We propose an efficient hardware architecture via using multivariate cryptographic scheme for storage devices. First, the architecture is improved and includes processor module, cryptographic module, storage module, display module, power module, keyboard module, export module and terminal module (off-chip). Second, multivariate schemes will protect the storage devices from quantum computer attacks. Third, multivariate cryptographic scheme is adopted in the architecture via using finite field GF(28), which will significantly increase the speed of cryptographic operations on storage devices since it is claimed to be faster than RSA and ECC.
The hardware architecture is implemented via using Verilog hardware programming language and Design Complier (DC), which is the Synopsys logical synthesis tool. The methodology adapted during implementation is TSMC-0.18 μm standard cell CMOS Application Specific Integrated Circuit (ASIC). The implementation results show that our design based on multivariate scheme is very efficient and well suit for storage devices.
We organize the rest of this paper as follows: In Sect. 2, we introduce cryptographic schemes of MPKCs. In Sect. 3, we propose an efficient hardware architecture based on multivariate cryptographic scheme for storage devices. In Sect. 4, we implement our design and present the experimental results. In Sect. 5, conclusions are summarized.
2 Preliminary
Multivariate cryptographic scheme includes a system of quadratic polynomials with several field elements in a small finite field K, which is illustrated in Table 1.
Multivariate cryptographic schemes are based on the multivariate Quadratic (MQ) polynomial problem: given m quadratic polynomials p(0)(x0, x1,…, xn-1), p(1)(x0, x1,…, xn-1),…,p(m−1)(x0, x1,…, xn-1) in the n variables x0, x1,…, xn-1. Multivariate cryptographic schemes relies on the difficulty of finding a vector x(x0, x1,…, xn-1) by solving a system of equations with the following form.
The multivariate cryptographic schemes are based on an invertible quadratic map F:Kn → Km and two invertible affine maps S:Km → Km and T:Kn → Kn. Thus, the public key of multivariate cryptographic schemes is the composed map P = S∘F∘T:Kn → Km. The private key includes F:Kn → Km, S:Km → Km and T:Kn → Kn.
The multivariate cryptographic schemes are used to encrypt, decrypt, signature generation and verification.
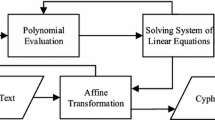
In order to encrypt a plain text z ∊ Kn, we evaluate the public key to compute the cipher text w = P(z) ∊ Km. In order to decrypt a cipher text w ∊ Km, we compute x = S−1(w) ∊ Km, y = F−1(x) ∊ Kn, and z = T−1(y) ∊ Kn. The encryption and decryption process of multivariate cryptographic schemes are depicted in Fig. 1.
In order to generate a signature of message w ∊ Km, we compute x = S−1(w) ∊ Km, y = F−1(x) ∊ Kn, and z = T−1(y) ∊ Kn. In order to verify a signature z ∊ Kn, we use the public key to compute the message w = P(z) ∊ Km. The signature generation and verification process of multivariate cryptographic schemes are depicted in Fig. 2.
3 An efficient hardware architecture based on multivariate cryptographic scheme for storage devices
3.1 An efficient hardware architecture
We propose an efficient hardware cryptographic architecture for storage devices based on multivariate scheme, which includes processor module, cryptographic module, storage module, display module, power module, keyboard module, export module and terminal module (off-chip). The architecture is constructed and depicted in Fig. 3.
It can be observed from Fig. 3 that the architecture is composed of the following modules.
- 1.
Processor module is the kernel module, which includes compute and control functions;
- 2.
Cryptographic module is the security module, which includes RAM and enTTS functions;
- 3.
Storage module is the disk module, which includes disk and disk Inputs/Outputs (I/Os) functions;
- 4.
Display module is the output module, which includes screen and screen controller functions;
- 5.
Power module is the supply module, which includes battery and power controller functions;
- 6.
Keyboard module is the input module, which includes keyboard and input controller functions;
- 7.
Export module is the peripheral module, which includes USB and export controller functions;
- 8.
Terminal module is the application module, which includes APP and USB functions.
3.2 Processor module
The processor module is the kernel module in storage devices, which connects with other modules.
The processor module is composed of compute and control functions. The control function is used to control other modules. The compute function performs addition and subtraction operations in integer fields. We adopt Streaming SIMD Extensions (SSE) instruction set in the processor module, which is an Intel instruction set extension introduced with the Intel Pentium III.
The I/Os of processor module includes output port c, which is used to output cipher texts. Besides, it includes input ports a, b, clock port clk, reset port res, which is used to input clock signal, secret keys, plain texts and reset signal. We illustrate the input and output in Table 2.
- 1.
Message: the message is 20 bytes;
- 2.
Signature: the signature is 28 bytes;
- 3.
Private keys (F): the private keys include F, L1, L2, F is a central map transformation, which includes 20 multivariate quadratic polynomial equations;
- 4.
Private keys (L1): the private key L1 is an affine transformation with the form ofy = Ax + B, where A is a 20 × 20 matrix and B is a vector with size 20;
- 5.
Private keys (L2): the private key L2 is an affine transformation with the form ofy = Ax + B, where A is a 28 × 28 matrix and B is a vector with size28;
- 6.
Public keys (\( \bar{F} \)): the public key \( \bar{F} \) is the combination of F, L1, L2 with the form of \( \bar{F} = L_{1}^\circ F^\circ L_{2} \);
- 7.
Clock signal: the clock cycle is 20 ns and the clock signal is 50 MHz;
- 8.
Reset signal: it resets all modules and sets the signal to 0 when the reset signal is 1.
3.3 Power module and display module
The display module is used to display the output information of storage devices, which takes a role as the bridge between users and storage devices. The display module includes screen and screen controller functions. We adapt a Liquid–Crystal Display (LCD) with size 3 × 2 cm2 in the display module. The output information of storage devices is displayed on the screen.
The power module is used to supply electric power for storage devices, which includes mains and power controller.
3.4 Storage module
The storage module includes disk and disk I/O functions. We adopt a 512 MB Solid-State Drive (SSD) in the storage module. We use the disk function to store user’s secret keys and personal data. Personal data includes account information, financial information, health information, certifications, etc. Secret keys are used in enTTS cryptographic operations. The disk I/O component includes ra0, ra1, rd0, rd1, ro0, ro1, re0 and re1, which are illustrated in Table 3.
- 1.
ra0 and ra1: address input ports with 8-bit;
- 2.
rd0 and rd1: data input ports with 2-byte;
- 3.
ro0 and ro1: data output ports with 8-bit;
- 4.
re0 and re1: enable input ports with 1-bit.
3.5 Cryptographic module
The cryptographic module is composed of RAM and enTTS. User’s data and secret keys are stored in storage model. The cryptographic module reads them from storage model and they are delivered to RAM. The cryptographic module uses enTTS algorithm to generate and verify signature, where enTTS scheme is introduced in Table 4 and described as follows.
We suppose that the hash value of the message of enTTS is denoted by y(y0, y1,…, y19) and its size is 20, where y0, y1,…, y19 are field elements. We also suppose that the signature of enTTS is denoted by x(x0, x1,…, x27) and its size is 28, where x0, x1,…, x27 are field elements.
In order to sign an enTTS message y(y0, y1,…, y19), we need to solve the following equation.
To do this, we first solve
L−11 is an affine transformation with the form as follows.
Second, it is required to solve the following equation.
The construction of the central map transformation depends on a map with the following form.
MQ polynomial fi is defined by
In the equations, pij is part of private keys.The polynomials f0, f1,…, f19 in
can be divided into three groups:
Similarly, \( \bar{x}(\bar{x}_{0} ,\bar{x}_{1} , \ldots ,\bar{x}_{27} ) \) are divided into four groups:
We randomly choose \( \bar{x}_{0} ,\bar{x}_{1} , \ldots ,\bar{x}_{7} \) and evaluate f0, f1,…,f8.
After that, it is required to solve the systems of linear equations on \( \bar{x}_{8} ,\bar{x}_{9} , \ldots ,\bar{x}_{16} \).
Next, \( \bar{x}_{17} ,\bar{x}_{18} \) are computed by evaluating f9, f10.
Then, f11, f12,…, f19 is evaluated and it is required to solve the systems of linear equations on \( \bar{x}_{19} ,\bar{x}_{20} , \ldots ,\bar{x}_{27} \).
Last, we solve
L−12 is an affine transformation
Finally, x is the cypher text of y.
3.6 Other modules
The keyboard module includes keyboard and input controller functions. In keyboard module, we adopt a small keyboard. Interaction via the keyboard is the main input device for storage devices.
The export module is composed of USB and export controller. USB (Universal Serial Bus) is used as a bridge between storage devices and personal computers. The export module is used to standardize the connection of storage devices to personal computers. We adopt USB 3.1 in the export module. The speed of USB 3.1 is updated to 10 Gbit/s.
The terminal module includes USB and APP. The terminal module uses personal computer. The storage device is connected to a personal computer via USB. The terminal module uses USB 3.1. We implement an APP on personal computers and it connects the storage devices with a username and password.
4 Implementation
We adapt enTTS(20,28) scheme in our design. The flowchart to generate a signature of enTTS is illustrated Fig. 4.
The main computations of implementation of enTTS are multiplication, inversion in GF(28).
In order to compute multiplications in GF(28), we implement a table look-up method, which is described in the following.
The number of elements in GF(28) is 256. We suppose that α is chosen as the primitive element. Then, all non-zero elements can be represented as a power of α. We suppose that p(x) is the irreducible polynomial in GF(28). Then, we compute and store ki(x) in address i of the look-up table based on the following equation.
A look-up table is depicted in Table 5 for multiplications in GF(28). The following is an example for multiplications using table look-up. We suppose that the element in GF(28) is denoted by (xxxxxxxx)2, where x ∊ GF(2), i.e. x = 0 or x = 1.
Example 1
Compute (00000010)2 × (00000100)2. Since (00000010)2 = α1 and (00000100)2 = α2, (00000010)2 × (00000100)2 = α1 × α2 = α3. By looking up Table 5, we have α3 = (00001000)2. Therefore, (00000010)2 × (00000100)2 = (00001000)2.
In order to compute inversions in GF(28), we implement a table look-up method, which is described in the following.
The number of elements in GF(28) is 256. We compute and store ki(x) in address i of the look-up table based on the following equation.
The results of inversions are computed via other inversion methods, e.g. Fermat theorem. A look-up table for inversions in GF(28)is depicted in Table 6. The following is an example for inversions.
Example 2
Compute (00000001)−12. By looking up Table 6, k1(x) = (00000001)2. Thus, the inverse of (00000001)2 is (00000001)2.
We adopt multipliers and inverters to solve systems of linear equations in GF(28). It is required to solve a system of linear equations with the matrix size of 9 × 9. The method used in the architecture is Gaussian elimination. Gaussian elimination, also known as row reduction, is employed to solve systems of linear equations with two steps. The first step is to transform Ax = b into the equivalent system A′x = b′ by applying the forward elimination, where A′ is an upper triangular matrix with size of 9 × 9 and b′ is a vector with size of 9. It takes 9 iterations for the first step of solving systems of linear equations with matrix size of 9 × 9, where each iteration consists of pivoting, normalization and elimination. The second step is to solve A′x = b′ by applying the backward substitution. Then we have an equivalent system A′′x = b′′, where A′′ is an identity matrix with size of 9 × 9 and b′′ is a vector with size of 9. After that, b′′ is the solution of the systems of linear equations Ax = b.
We adopt 28 multipliers and an inverter in our architecture. The hardware architecture is implemented via using Verilog hardware programming language and Design Complier. The methodology adapted during implementation is TSMC-0.18 μm standard cell CMOS ASIC. The executing time of multivariate scheme is 240 us and its area is low, which shows that our design based on multivariate scheme is very efficient.
5 Conclusion
We propose an efficient hardware architecture via using multivariate cryptographic scheme for storage devices in this paper. First, the architecture is improved and includes processor module, cryptographic module, storage module, display module, power module, keyboard module, export module and terminal module (off-chip). Second, multivariate schemes will protect the storage devices from quantum computer attacks. Third, multivariate cryptographic scheme is adopted in the architecture for cryptographic systems via using finite field GF(28), which will significantly increase the speed of cryptographic operations on storage devices since it is claimed to be faster than RSA and ECC. We implement the architecture on ASICs. The implementation results show that our design based on multivariate scheme is very efficient and well suit for storage devices.
References
Ding, J., Petzoldt, A.: Current state of multivariate cryptography. IEEE Secur. Priv. 15(4), 28–36 (2017)
Shor, P.W.: Polynomial—time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 41(2), 303–332 (1999)
Kipnis, A., Patarin, J., Goubin, L.: Unbalanced oil and vinegar signature schemes. In: Advances in Cryptology—EUROCRYPT 99, Prague, Czech Republic, vol. 1592. Springer, Berlin, pp. 206–222 (1999)
Ding, J., Schmidt, D.: Rainbow, a new multivariable polynomial signature scheme. In: Third International Conference, ACNS 2005, New York, NY, USA, vol. 3531. Springer, Berlin, pp. 164–175 (2005)
Yi, H., Li, W.: On the importance of checking multivariate public key cryptography for side-channel attacks: the case of enTTS scheme. Comput. J. 60(8), 1197–1209 (2017)
Petzoldt, A., Chen, M.S., Ding, J., et al.: HMFEv—an efficient multivariate signature scheme. In: International Workshop on Post-Quantum Cryptography. Springer, Cham, pp. 205-223 (2017)
Petzoldt, A., Bulygin, S., Buchmann, J.: Fast Verification for Improved Versions of the UOV and Rainbow Signature Schemes, Post-Quantum Cryptography, PQCrypto 2013, pp. 188–202. Springer, Berlin Heidelberg (2013)
Liu, C.M., Zhao, L., Sun, Y.J.: The design of public key cryptography for key exchange base on multivariate equations. Appl. Mech. Mater. 513, 552–554 (2014)
Szepieniec, A., Ding, J., Preneel, B.: Extension field cancellation: A new central trapdoor for multivariate quadratic systems. In: International Workshop on Post-Quantum Cryptography. Springer-Verlag, New York, Inc., pp. 182–196 (1996)
Thomae, E, Wolf, C.: Cryptanalysis of enhanced TTS, STS and all its variants, or: why cross—terms are important. In: 5th International Conference on Cryptology in Africa, Ifrance, Morocco. Springer-Verlag, Berlin, pp. 188–202 (2012)
Porras, J., Baena, J., Ding, J.: ZHFE, a New multivariate public key encryption scheme. In: International Workshop on Post-Quantum Cryptography. Springer International Publishing, pp. 229–245 (2014)
Tao, C., Xiang, H., Petzoldt, A., et al.: Simple matrix–a multivariate public key cryptosystem (MPKC) for encryption. Finite Fields Appl. 35, 352–368 (2015)
Gao, S., Heindl, R.: Multivariate public key cryptosystems from diophantine equations. Designs Codes Cryptogr. 67(1), 1–18 (2013)
Huang, Y.J., Liu, F.H., Yang, B.Y.: Public-key cryptography from new multivariate quadratic assumptions. In: International Conference on Practice and Theory in Public Key Cryptography. Springer-Verlag, pp. 190–205 (2012)
An, X.: Certificateless multi-receiver signcryption scheme based on multivariate public key cryptography. Chin. J. Comput. 35(9), 1881 (2012)
Ustimenko, V.: On the flag geometry of simple group of Lie type and multivariate cryptography. Algebra Discret. Math. 19(1), 130–144 (2015)
Wang, J., Cheng, L.M., Su, T.: Multivariate cryptography based on clipped hopfield neural network. IEEE Trans. Neural Netw. Learn. Syst. 99, 1–11 (2016)
Sun, X., Liu, H., Zhang, M.: Multivariate symmetric cryptography with 2-dimesion chaotic disturbation. in: International Conference on Wireless Communications & Signal Processing. IEEE, pp. 1–4 (2016)
Albrecht, M.R., Faugére, J.C., Fitzpatrick, R., et al.: Practical cryptanalysis of a public-key encryption scheme based on new multivariate quadratic assumptions. In: International Workshop on Public Key Cryptography. Springer Berlin Heidelberg, pp. 446–464 (2014)
Bogdanov, A., Eisenbarth, T., Rupp, A., Wolf, C.: Time–area optimized public-key engines: MQ—cryptosystems as replacement for elliptic curves? In: Cryptographic Hardware and Embedded Systems—CHES 2008, Washington, D.C., USA. Springer-Verlag, Berlin, pp. 45–61 (2008)
Yi, H., Li, W.: Fast three-input multipliers over small composite fields for multivariate public key cryptography. Int. J. Secur. Appl. 9(9), 165–178 (2015)
Yi, H., Tang, S., Vemuri, R.: Fast inversions in small finite fields by using binary trees. Comput. J. 59(7), 1102–1112 (2016)
Balasubramanian, S., Bogdanov, A., Rupp, A.,et al.: Fast multivariate signature generation in hardware: The case of Rainbow. In: International Conference on Application—Specific Systems, Architectures and Processors. IEEE, pp. 25–30 (2008)
Yi, H., Tang, S.: Very small FPGA processor for multivariate signatures. Comput. J. 59(7), 1091–1101 (2016)
Shih JR., Hu, Y., Hsiao, M.C., et al.: Securing M2M with post-quantum public-key cryptography. IEEE J. Emerg. Sel. Top. Circuits Syst. 3(1), 106–116 (2013)
Yi, H., Li, W., Nie, Z.: Fast hardware implementations of inversions in small finite fields for special irreducible polynomials on FPGAs. Int. J. Secur. Appl. 19(9), 109–120 (2016)
Czypek, P, Heyse, S., Thomae, E.: Efficient implementations of MQPKS on constrained devices, Cryptographic Hardware and Embedded Systems—CHES 2012. Springer Berlin Heidelberg, pp. 374–389 (2012)
Tang, S., Yi, H., Ding, J., et al.: High-speed hardware implementation of rainbow signature on FPGAs. In: Post-Quantum Cryptography. Springer Berlin Heidelberg, pp. 228–243 (2011)
Acknowledgements
This work is supported by Shenzhen Science and Technology Program under Grant (No. JCYJ20170306144219159, No. JCYJ20160428092427867), Special Fund for the Development of Strategic Emerging Industries and Future Industries of Shenzhen (No. 20170502142224600), Science and Technology Program of Shenzhen Polytechnic (No. 601722K20018).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Yi, H., Nie, Z. Towards data storage in cryptographic systems: an efficient hardware architecture based on multivariate scheme for secure storage applications. Cluster Comput 22 (Suppl 4), 8639–8646 (2019). https://doi.org/10.1007/s10586-018-1933-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-018-1933-5