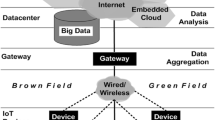
Abstract
The Internet unfolded enormous opportunities to the modern computing world where not only humans but also computers and machines, as well as any tiny sensing devices, can communicate and collaborate. The Internet of Things (IoT) is still a new concept in its early stages after 20 years of successful usage in various application domains. Nowadays, the "Internet of Things Ecosystem" term is being used more often that emphasizes its complex internal structure and functionality. Based on the available standards on the IoT’s generalized architecture and reference model, the IoT ecosystem is presented as a security object to be protected. Numerous security controls, collecting raw data for complex and multi-stage processing and further detection of events related to information security (IS), are located on its layers. The IS incident management process with different routine actions for the IoT ecosystems needs automation, for which Security Information and Event Management (SIEM) systems are the best applicable solutions. But modern challenges require modifying two previously known generations of these systems, especially for the IoT ecosystems. A new blockchain-based system called the IoTBlockSIEM is proposed to solve this problem. An example of constructing transactions in the IoTBlockSIEM for the case of its use in managing IS incidents in the IoT ecosystem is provided. Further research concludes the article.






Similar content being viewed by others
References
ITU-T Y.4000/Y 2060 Overview of the Internet of things.
ISO/IEC 20924 Information technology—Internet of Things—Definition and Vocabulary.
European Union Agency For Network And Information Security (ENISA) (2017) Baseline Security Recommendations for IoT in the context of Critical Information Infrastructures. https://www.enisa.europa.eu/publications/baseline-security-recommendations-for-iot. Accessed 22 Feb, 2020.
Bahga, A., Madisetti, V.: Internet of Things (A Hands-on-Approach). VPT, New York (2014)
European Commission (2008) Internet of Things in 2020. A roadmap for the future. https://docbox.etsi.org/erm/Open/CERP%2020080609-10/Internet-of-Things_in_2020_EC-EPoSS_Workshop_Report_2008_v1-1.pdf. Accessed 22 Feb, 2020.
Miloslavskaya, N., Tolstoy, A.: Internet of Things: information security challenges and solutions. Clust Comput 22, 103–119 (2018). https://doi.org/10.1007/s10586-018-2823-6
Manasrah, A.M., Shannaq, M.A., Nasir, M.A., (2020) An investigation study of privacy preserving in cloud computing environment., : In: Gupta, B., Perez, G., Agrawal, D., Gupta, D. (eds.) Handbook of computer networks and cyber security, pp. 43–61. Springer, Cham (2020)
Roy, M., Chowdhury, C., Aslam, N.: Security and privacy issues in wireless sensor and body area networks. In: Gupta, B., Perez, G., Agrawal, D., Gupta, D. (eds.) Handbook of computer networks and cyber security, pp. 173–200. Springer, Cham (2020)
Vyas, A., Pal, S.: Preventing security and privacy attacks in WBANs. In: Gupta, B., Perez, G., Agrawal, D., Gupta, D. (eds.) Handbook of computer networks and cyber security, pp. 201–225. Springer, Cham (2020)
Paharia, B., Bhushan, K.: A comprehensive review of distributed denial of service (DDoS) attacks in fog computing environment. In: Gupta, B., Perez, G., Agrawal, D., Gupta, D. (eds.) Handbook of computer networks and cyber security, pp. 493–524. Springer, Cham (2020)
Alloghani, M., Baker, T., Al-Jumeily, D., Hussain, A., Mustafina, J., Aljaaf, A.J.: A systematic review on security and privacy issues in mobile devices and systems. In: Gupta, B., Perez, G., Agrawal, D., Gupta, D. (eds.) Handbook of computer networks and cyber security, pp. 585–608. Springer, Cham (2020)
Vázquez-Ingelmo, A., Moreno-Montero, Á.M., García-Peñalvo, F.J.: Threats behind default configurations of network devices: wired local network attacks and their countermeasures. In: Gupta, B., Perez, G., Agrawal, D., Gupta, D. (eds.) Handbook of computer networks and cyber security, pp. 133–172. Springer, Cham (2020)
Malyuk A, Miloslavskaya N (2014) Information security theory development. Proceedings of the 7th international conference on security of information and networks (SIN2014), September, 9–11 2014 Glasgow (UK). ACM, New York, pp 52–55. ISBN: 978-1-4503-3033-6. https://doi.org/10.1145/2659651.2659659.
Miloslavskaya N, Tolstoy A () New SIEM system for the internet of things. In: Rocha A et al (eds), New knowledge in information systems and technologies, advances in intelligent systems and computing vol. 931, pp. 317–327. Springer International Publishing AG 2019. WorldCIST’19, La Toja Island, Galicia, Spain, 16–19 April 2019. https://doi.org/10.1007/978-3-030-16184-2_31.
Miloslavskaya N, Tolstoy A, Zapechnikov S (2016) Taxonomy for unsecure big data processing in security operations centers. Proceedings of 2016 4th international conference on future internet of things and cloud workshops. The 3rd international symposium on big data research and innovation (BigR&I 2016). Vienna (Austria), 22–24 August, pp 154–159. https://doi.org/10.1109/W-FiCloud.2016.42
ISO 27000 2018 Information technology—Security techniques—Information security management systems—overview and vocabulary
Pescatore J, Shpantzer G (2014) Securing the ”Internet of Things” survey, InfoSec Reading Room. https://www.sans.org/reading-room/whitepapers/covert/paper/34785. Accessed 22 Feb, 2020.
Sfarab, A.R., Nataliziob, E., Chtourou, C.Y. : A roadmap for security challenges in internet of things. Digit Commun Netw 4(2), 118–137 (2018)
Vemulapalli, C., Madria, S.K., Linderman, M.: Security frameworks in mobile cloud computing. In: Gupta, B., Perez, G., Agrawal, D., Gupta, D. (eds.) Handbook of computer networks and cyber security, pp. 1–41. Springer, Cham (2020)
Tewari, A., Gupta, B.B.: An analysis of provable security frameworks for RFID security. In: Gupta, B., Perez, G., Agrawal, D., Gupta, D. (eds.) Handbook of computer networks and cyber security, pp. 635–651. Springer, Cham (2020)
ISO/IEC 30141:2018 Internet of Things (IoT)—Reference Architecture.
NISTIR 8222 (draft) “Internet of Things (IoT) Trust Concerns”. https://csrc.nist.rip/library/NIST%20IR%208222-draft.pdf. Accessed 22 Feb, 2020.
Fagan M, Megas KN, Scarfone K, Smith M (2020) NISTIR 8259 (draft) “Core Cybersecurity Feature Baseline for Securable IoT Devices: a starting point for IoT device manufacturers. https://doi.org/10.6028/NIST.IR.8259-draft. Accessed 22 Fe, 2020.
Boeckl K, Fagan M, Fisher W, et al (2019) NISTIR 8228 “Considerations for Managing Internet of Things (IoT) cybersecurity and privacy risks. https://doi.org/10.6028/NIST.IR.8228. Accessed 22 Feb, 2020.
Philips OGM, Signify SK, Ericsson MS (2019) IRTF RFC 8576 “Internet of Things (IoT) Security: State of the Art and Challenges”. https://tools.ietf.org/html/rfc8576. Accessed 22 Feb, 2020.
ITU-T Y.2068 Functional framework and capabilities of the Internet of things.
ISO/IEC 27035–1:2016 Information technology—Security techniques—Information security incident management—Part 1: Principles of incident management.
NIST SP 800–61 Rev. 2. Computer Security Incident Handling Guide. 2012.
ISO/IEC 27000:2018 Information technology—Security techniques—Information security management systems—Overview and vocabulary.
ISO/IEC 27043:2015 Information technology—Security techniques—Incident investigation principles and processes.
Miloslavskaya, N.: Analysis of SIEM systems and their usage in security operations and security intelligence centers. In: Samsonovich, A., Klimov, V. (eds.) Biologically inspired cognitive architectures (BICA) for young scientists. BICA 2017. Advances in intelligent systems and computing, pp. 282–288. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-63940-6_40
UK Government, Office for Science (2016) Distributed Ledger Technology: Beyond Block Chain (Report). https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/492972/gs-16-1-distributed-ledger-technology.pdf. Accessed 22 Feb, 2020.
PriceWaterhouseCoopers (2016) Making sense of bitcoin, cryptocurrency, and blockchain. https://www.pwc.com/us/en/financial-services/fintech/bitcoin-blockchain-cryptocurrency.html. Accessed 22 Feb, 2020
Nielson, B (2017) Blockchain solutions for cyber & data security. https://richtopia.com/emerging-technologies/blockchain-solutions-for-cyber-data-security. Accessed 22 Feb, 2020.
IBM (2017) What is blockchain technology? https://www.ibm.com/blockchain/what-is-blockchain. Accessed 22 Feb, 2020.
Wilson S (2017) How it works: Blockchain explained in 500 words. https://www.zdnet.com/article/blockchain-explained-in-500-words/. Accessed 22 Feb, 2020.
OpenBlockchain (2017) Researching the potential of blockchains. https://blockchain.open.ac.uk/. Accessed 22 Feb, 2020.
Internet Society (2018) Blockchain. https://www.internetsociety.org/issues/blockchain/?gclid=Cj0KCQjwuNbsBRC-ARIsAAzITufWAGKLdHA6bEnsLr6qPEI7bqNJh2on9kh7Z8u5lN0RQoUuKnOUkZ8aAjB9EALw_wcB. Accessed 22 Feb, 2020.
Primechaintech (2018) Blockchain Security Controls. https://www.primechaintech.com/docs/blockchain_security_controls.pdf. Accessed 22 Feb, 2020.
Miloslavskaya, N.: Designing Blockchain-based SIEM 3.0 System. Information Comput Sec (UK) (2018). https://doi.org/10.1108/ics-10-2017-0075
Kotari, M., Chiplunkar, N.N.: Investigation of security issues in distributed system monitoring. In: Gupta, B., Perez, G., Agrawal, D., Gupta, D. (eds.) Handbook of computer networks and cyber security, pp. 609–634. Springer, Cham (2020)
Ateniese G, Magri B, Venturi D, Andrade E (2020) Redactable Blockchain—or—rewriting history in Bitcoin and friends. https://eprint.iacr.org/2016/757.pdf. Accessed 22 Feb, 2020.
Chan, P.K.: Machine learning for IT security. In: Sammut, C., Webb, G.I. (eds.) Encyclopedia of machine learning. Springer, Boston, MA (2011)
Machine Learning in Cyber Security (2018) Fact, fantasy, and moving forward. SANS. https://www.sans.org/cyber-security-summit/archives/file/summit-archive-1543964671.pdf. Accessed 22 Feb, 2020.
Gulla, K.K., Viswanath, P., Veluru, S.B., Kumar, R.R.: Machine learning based intrusion detection techniques. In: Gupta, B., Perez, G., Agrawal, D., Gupta, D. (eds.) Handbook of computer networks and cyber security, pp. 873–888. Springer, Cham (2020)
Al-Kasassbeh, M., Mohammed, S., Alauthman, M., Almomani, A.: Feature selection using a machine learning to classify a malware. In: Gupta, B., Perez, G., Agrawal, D., Gupta, D. (eds.) Handbook of computer networks and cyber security, pp. 889–904. Springer, Cham (2020)
Rani, S., Saini, P.: Fog computing: applications and secure data aggregation. In: Gupta, B., Perez, G., Agrawal, D., Gupta, D. (eds.) Handbook of computer networks and cyber security, pp. 475–492. Springer, Cham (2020)
Lano, K.: The B language and method: a guide to practical formal development. Springer, New York (1996)
Acknowledgment
This work was supported by the MEPhI Academic Excellence Project (agreement with the Ministry of Education and Science of the Russian Federation of August 27, 2013, Project No. 02.a03.21.0005).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is an extended version of our paper published in A. Rocha et al. (eds.), New Knowledge in Information Systems and Technologies, Advances in Intelligent Systems and Computting, vol. 931—the Proceedings of the 7th World Conference on Information Systems and Technologies (WorldCIST’19), entitled “New SIEM for the Internet of Things” © Springer International Publishing AG 2019.
Rights and permissions
About this article
Cite this article
Miloslavskaya, N., Tolstoy, A. IoTBlockSIEM for information security incident management in the internet of things ecosystem. Cluster Comput 23, 1911–1925 (2020). https://doi.org/10.1007/s10586-020-03110-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-020-03110-5