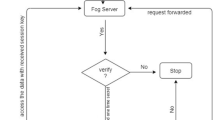
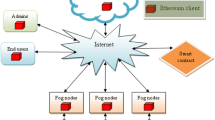
Abstract
The radical shift in the technology with the advent of connected things has led to the significant proliferation in demand for IoT devices, commonly called ‘smart devices’. These devices are capable of data collection, which can help in umpteen applications, particularly in healthcare. With the tremendous growth in these resource-constrained end devices, there has been a substantial increase in the number of attack varieties. Since these end devices deal with the sensitive data that might cause severe damage if not handled properly. Hence, defending its integrity, preserving its privacy, and maintaining its confidentiality as well as availability is of utmost importance. However, there are many protocols, models, architecture tools, etc. proposed to provide security. Nevertheless, almost every solution propound so far is not fully resilient and lacks in giving full protection to the system in some way or the other. So here, we have proposed a lightweight anonymous mutual authentication scheme for end devices and fog nodes.







Similar content being viewed by others
References
Shivraj, V.L., Rajan, M.A., Singh, M., Balamuralidhar, P.: One time password authentication scheme based on elliptic curves for Internet of Things (IoT). In: 2015 5th National Symposium on Information Technology: Towards New Smart World (NSITNSW), pp. 1–6. IEEE (2015)
Stojmenovic, I., Wen, S.: The fog computing paradigm: Scenarios and security issues. In: 2014 Federated Conference on Computer Science and Information Systems, pp. 1–8. IEEE (2014)
Arij, B. E. N., Mohamed, A. B. I. D., and MEDDEB, A.: SAMAFog: service-aware mutual authentication fog-based protocol. In: 2019 15th International Wireless Communications and Mobile Computing Conference (IWCMC), pp. 1049–1054. IEEE (2019)
Alharbi, S., Rodriguez, P., Maharaja, R., Iyer, P., Subaschandrabose, N., Ye, Z.: Secure the internet of things with challenge response authentication in fog computing. In: 2017 IEEE 36th International Performance Computing and Communications Conference (IPCCC), pp. 1–2 (2017)
Dastjerdi, A.V., Gupta, H., Calheiros, R.N., Ghosh, S.K., Buyya, R.: Fog computing: principles, architectures, and applications. In: Internet of Things, pp. 61–75 (2016)
Hu, P., Dhelim, S., Ning, H., Qiu, T.: Survey on fog computing: architecture, key technologies, applications and open issues. J. Netw. Comput. Appl. 98, 27–42 (2017)
Yi, S., Qin, Z., Li, Q.: Security and privacy issues of fog computing: a survey. In: International Conference on Wireless Algorithms, Systems, and Applications, pp. 685–695. Springer (2015)
Zhang, P., Zhou, M., Fortino, G.: Security and trust issues in Fog computing: a survey. Future Gener. Comput. Syst. 88, 16–27 (2018)
Lee, K., Kim, D., Ha, D., Rajput, U., Oh, H.: On security and privacy issues of fog computing supported Internet of Things environment. In: 2015 6th International Conference on the Network of the Future (NOF), pp. 1–3. IEEE (2015)
Alrawais, A., Alhothaily, A., Hu, C., Cheng, X.: Fog computing for the internet of things: security and privacy issues. IEEE Internet Comput. 21(2), 34–42 (2017)
Borgohain, T., Borgohain, A., Kumar, U., Sanyal, S.: Authentication systems in internet of things. arXiv preprint arXiv:1502.00870. (2015)
Hernandez-Ramos, J.L., Pawlowski, M.P., Jara, A.J., Skarmeta, A.F., Ladid, L.: Toward a lightweight authentication and authorization framework for smart objects. IEEE J. Sel. Areas Commun. 33(4), 690–702 (2015)
Liu, J., Xiao, Y., Chen, C.P.: Authentication and access control in the internet of things. In: 2012 32nd International Conference on Distributed Computing Systems Workshops, pp. 588–592. IEEE (2012)
Ferrag, M.A., Maglaras, L.A., Janicke, H., Jiang, J., Shu, L.: Authentication protocols for Internet of Things: a comprehensive survey. Secur. Commun. Netw. (2017)
Podsevalov, I., Iakushkin, O., Kurbangaliev, R., Korkhov, V.: Blockchain as a platform for Fog computing, pp. 596–605 (2019)
Khan, S., Parkinson, S., Qin, Y.: Fog computing security: a review of current applications and security solutions. J. Cloud Comput. 6(1), 19 (2017)
Ni, J., Zhang, K., Lin, X., Shen, X.S.: Securing fog computing for internet of things applications: challenges and solutions. IEEE Commun. Surv. Tutor. 20(1), 601–628 (2017)
Stojmenovic, I., Wen, S., Huang, X., Luan, H.: An overview of fog computing and its security issues. Concurr. Comput. 28(10), 2991–3005 (2016)
Ibrahim, M.H.: Octopus: an edge-fog mutual authentication scheme. IJ Netw. Secur. 18(6), 1089–1101 (2016)
Bamasag, O.O., Youcef-Toumi, K.: Towards continuous authentication in internet of things based on secret sharing scheme. In: Proceedings of the WESS’15: Workshop on Embedded Systems Security ACM, p. 1 (2015)
Salman, O., Abdallah, S., Elhajj, I.H., Chehab, A., Kayssi, A.: Identity-based authentication scheme for the internet of things. In: 2016 IEEE Symposium on Computers and Communication (ISCC), pp. 1109–1111. IEEE (2016)
Amor, A.B., Abid, M., Meddeb, A.: A privacy-preserving authentication scheme in an edge-fog environment. In: 2017 IEEE/ACS 14th International Conference on Computer Systems and Applications (AICCSA), pp. 1225–1231. IEEE (2017)
Arij, B. E. N., Mohamed, A. B. I. D., and MEDDEB, A.: CASK: conditional authentication and session key establishment in fog-assisted social IoT network. In: 2019 15th International Wireless Communications and Mobile Computing Conference (IWCMC), pp. 114–119. IEEE (2019)
Lu, R., Heung, K., Lashkari, A.H., Ghorbani, A.A.: A lightweight privacy-preserving data aggregation scheme for fog computing-enhanced IoT. IEEE Access 5, 3302–3312 (2017)
Imine, Y., Kouicem, D.E., Bouabdallah, A., Ahmed, L.: MASFOG: An Efficient Mutual Authentication Scheme for Fog Computing Architecture. In: 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), pp. 608–613. IEEE (2018)
Almadhoun, R., Kadadha, M., Alhemeiri, M., Alshehhi, M., Salah, K.: A user authentication scheme of IoT devices using blockchain-enabled fog nodes. In: 2018 IEEE/ACS 15th International Conference on Computer Systems and Applications (AICCSA), pp. 1–8. IEEE (2018)
Kaur, K., Garg, S., Kaddoum, G., Gagnon, F., Ahmed, S.H.: Blockchain based lightweight authentication mechanism for vehicular fog infrastructure. arXiv preprint arXiv:1904.01168 (2019)
Pardeshi, M.S., Yuan, S.M.: SMAP fog/edge: a secure mutual authentication protocol for fog/edge. IEEE Access 7, 101327–101335 (2019)
Lo, L., Westphall, C.M., Gr, udtner, L.D., Westphall, C.B.: Mutual authentication for IoT in the context of fog computing. In: 2019 11th International Conference on Communication Systems and Networks (COMSNETS), pp. 367–374. IEEE (2019)
Usha, S., Tamilarasi, A.: A trust based security framework with anonymous authentication system using multiple attributes in decentralized cloud. Clust. Comput. 22(2), 3883–3892 (2019)
Maharaja, R., Iyer, P., Ye, Z.: A hybrid fog-cloud approach for securing the Internet of Things. Clust. Comput. 1–9 (2019)
Pugazhenthi, A., Chitra, D.: Secured and memory overhead controlled data authentication mechanism in cloud computing. Clust. Comput. 22(6), 13559–13567 (2019)
Liu, Y., Sun, Q., Wang, Y., Zhu, L., Ji, W.: Efficient group authentication in RFID using secret sharing scheme. Clust. Comput. 22(4), 8605–8611 (2019)
Yao, Y., Chang, X., Misic, J., Misic, V.B., Li, L.: BLA: blockchain-assisted lightweight anonymous authentication for distributed vehicular fog services. IEEE Internet Things J. 6(2), 3775–3784 (2019)
Talwani, S.: Fog computing: introduction, challenges and future aspects. Heritage 67(7), 620–626 (2019)
Miller, V.S.: Use of elliptic curves in cryptography. In: Conference on the Theory and Application of Cryptographic Techniques, pp. 417–426. Springer, Berlin (1985)
Koblitz, N.: Elliptic curve cryptosystems. Math. Comput. 48(177), 203–209 (1987)
Sattam, S., Riyami, A.I., Kenneth, G.P.: Certificateless public key cryptography. In: International Conference on the Theory and Application of Cryptology and Information Security, pp. 452–473. Springer (2003)
Boneh, D., Boyen, X.: Efficient selective-ID secure identity-based encryption without random oracles. In: International Conference on the Theory and Applications of Cryptographic Techniques, pp. 223–238 (2004)
Sogani, A., Jain, A.: Energy aware and fast authentication scheme using identity based encryption in wireless sensor networks. Clust. Comput. 22(5), 10637–10648 (2019)
Zhou, L., Li, X., Yeh, K.H., Su, C., Chiu, W.: Lightweight IoT-based authentication scheme in cloud computing circumstance. Future Gener. Comput. Syst. 91, 244–251 (2019)
Yeh, H.L., Chen, T.H., Liu, P.C., Kim, T.H., Wei, H.W.: A secured authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 11(5), 4767–4779 (2011)
Shi, W., Gong, P.: A new user authentication protocol for wireless sensor networks using elliptic curves cryptography. Int. J. Distrib. Sens. Netw. 9(4), 730831 (2013)
Xu, X., Zhu, P., Wen, Q., Jin, Z., Zhang, H., He, L.: A secure and efficient authentication and key agreement scheme based on ECC for telecare medicine information systems. J. Med. Syst. 38(1), 9994 (2014)
Wazid, M., Das, A.K., Kumar, N., Vasilakos, A.V.: Design of secure key management and user authentication scheme for fog computing services. Future Gener. Comput. Syst. 91, 475–492 (2019)
Dhillon, P.K., Kalra, S.: A secure multi-factor ECC based authentication scheme for Cloud-IoT based healthcare services. J. Ambient Intell. Smart Environ. 11(2), 149–164 (2019)
Li, H., Li, F., Song, C., Yan, Y.: Towards smart card based mutual authentication schemes in cloud computing. KSII Trans. Internet Inform. Syst. 9(7), 2719–2735 (2015)
Burrows, M., Abadi, M., Needham, R.: A logic of authentication. ACM Trans. Comput. Syst. 8, 18–36 (1990)
Acknowledgements
This work was supported and funded by the Ministry of Education, Government of India.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Singh, S., Chaurasiya, V.K. Mutual authentication scheme of IoT devices in fog computing environment. Cluster Comput 24, 1643–1657 (2021). https://doi.org/10.1007/s10586-020-03211-1
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-020-03211-1