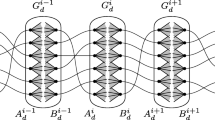
Abstract
A perfect secret sharing scheme based on a graph G is a randomized distribution of a secret among the vertices of the graph so that the secret can be recovered from the information assigned to vertices at the endpoints of any edge, while the total information assigned to an independent set of vertices is independent (in statistical sense) of the secret itself. The efficiency of a scheme is measured by the amount of information the most heavily loaded vertex receives divided by the amount of information in the secret itself. The (worst case) information ratio of G is the infimum of this number. We calculate the best lower bound on the information ratio for an infinite family of graphs the entropy method can give. We argue that almost all existing constructions for secret sharing schemes are special cases of the generalized vector space construction. We give direct constructions of this type for the first two members of the family, and show that for the other members no such construction exists which would match the bound yielded by the entropy method.
Similar content being viewed by others
References
Beimel A., Livne N., Padró C.: Matroids can be far from ideal secret sharing. In: Proceedings of TCC’08, LNCS, vol. 4948, pp. 194–212 (2008).
Beimel A., Ishai Y.: On the power of nonlinear secret sharing schemes. SIAM J. Discrete Math. 19, 258–280 (2005)
Beimel A., Livne N.: On matroids and non-ideal secret sharing. In: Halevi S., Rabin T. (eds.) Proceedings of the Third Theory of Cryptography Conference—TCC 2006, LNCS, vol. 3876, pp. 482–501 (2006).
Beimel A., Weinreb E.: Separating the power of monotone span programs over different fields. SIAM J. Comput. 34, 1196–1215 (2005)
Blakley G.R.: Safeguarding cryptographic keys. In: Proceedings of the 1979 AFIPS National Computer Conference, pp. 313–317 (1979).
Blundo C., De Santis A., Simone R.D., Vaccaro U.: Tight bounds on the information rate of secret sharing schemes. Des. Codes Cryptogr. 11, 107–110 (1997)
Brickell E.F.: Some ideal secret sharing schemes. J. Combin. Math. Combin. Comput. 9, 105–113 (1989)
Capocelli R.M., De Santis A., Gargano L., Vaccaro U.: On the size of shares of secret sharing schemes. J. Cryptology 6(3), 157–168 (1993)
Chor B., Kushilevitz E.: Secret sharing over infinite domains. J. Cryptology 6, 87–96 (1993)
Csirmaz L.: The size of a share must be large. J. Cryptology 10(4), 223–231 (1997)
Csirmaz L.: Secret sharing schemes on graphs. Studia Sci. Math. Hungar. 44, 297–306 (2007)—available as IACR preprint http://eprint.iacr.org/2005/059.
Csirmaz L., Ligeti P.: On an infinite families of graphs with information ratio 2 − 1/k (Special Issue of Computing on the occasion CECC’08 to appear).
Csiszár I., Körner J.: Information Theory. Coding Theorems for Discrete Memoryless Systems. Academic Press, New York (1981)
Ferrás O., Martí-Farré J., Padró C.: Ideal multipartite secret sharing schemes. In: Advances in Cryptology—EUROCRYPT 2007, LNCS, vol. 4515, pp. 448–465 (2007).
Ingleton A.W.: Conditions for representability and transversability of matroids. In: Proc. Fr. Br. Conf. 1970, pp. 62–27. Springer-Verlag (1971).
Jackson W., Martin K.M.: Perfect secret sharing schemes on five participants. Des. Codes Cryptogr. 9, 233–250 (1996)
Karchmer M., Widgerson A.: On span programs. In: Proc. of the 8th IEEE Trans. on Information Theory, vol. 29, pp. 102–111 (1993).
Martí-Farré J., Padró C.: Secret sharing schemes with three or four minimal qualified subsets. Des. Codes Cryptogr. 34, 17–34 (2005)
Martí-Farré J., Padró C.: On secret sharing schemes, matroids and polymatroids. In: TCC 2007, Lecture Notes in Comput. Sci., vol. 4392, pp. 273–290 (2007).
Matus F.: Matroid representations by partitions. Discrete Math. 203, 169–194 (1999)
Matus F.: Adhesivity of polymatroids. Discrete Math. 307(21), 2464–2477 (2007)
Shamir A.: How to share a secret. Commun. ACM 22, 612–613 (1979)
Stinson D.R.: Decomposition constructions for secret sharing schemes. IEEE Trans. Inform. Theory 40, 118–125 (1994)
van Dijk M.: On the information rate of perfect secret sharing schemes. Des. Codes Cryptogr. 12, 143–169 (1997)
van Dijk M., Kevenaar T., Schrijen G., Tuyls P.: Improved constructions of secret sharing schemes by applying (λ,ω)-decompositions. Inform. Process. Lett. 99(4), 154–157 (2006)
Welsh D.J.A.: Matroid Theory. Academic Press, London (1976)
Zhang Z., Yeung R.W.: On characterization of entropy function via information inequalities. IEEE Trans. Inform. Theory 44, 1440–1452 (1998)
Author information
Authors and Affiliations
Corresponding author
Additional information
Communicated by Daniel Panario.
Rights and permissions
About this article
Cite this article
Csirmaz, L. An impossibility result on graph secret sharing. Des. Codes Cryptogr. 53, 195–209 (2009). https://doi.org/10.1007/s10623-009-9304-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10623-009-9304-0