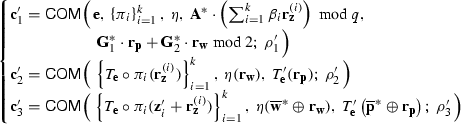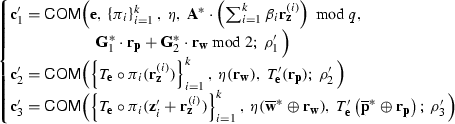Abstract
Policy-based signature, introduced by Bellare and Fuchsbauer at PKC 2014, is a new type of digital signature in which a signer is only allowed to sign messages satisfying certain policy specified by the authority, but the signatures should not reveal the underlying policy. Having these features, policy-based signatures are attractive from both theoretical and practical aspects. In their pioneering paper, Bellare and Fuchsbauer have provided generic constructions of policy-based signatures, and a concrete instantiation based on pairings. In this work, we develop the recent techniques in lattice-based cryptography to construct a (delegatable) policy-based signature scheme from lattice assumptions. Specifically, we adapt Langlois et al.’s zero-knowledge argument system (PKC 2014) for the Bonsai tree signature scheme (Eurocrypt 2010) to enable the prover to convince the verifier that its secret witness satisfies an additional condition. Making the protocol non-interactive via the Fiat-Shamir transformation, we obtain a policy-based signature scheme supporting polynomially many policies, which satisfies the two security requirements (simulatability and extractability) in the random oracle model. Furthermore, our construction can be efficiently extended to a delegatable policy-based signature, thanks to the hierarchical structure of the Bonsai tree. Our contribution is twofold. On the one hand, we enrich the scope of policy-based signatures by providing the first quantum-resistant instantiation. On the other hand, our technical approach can potentially be applied to design a wide variety of privacy-enhanced lattice-based cryptographic constructions.

Similar content being viewed by others
Notes
As noted in [4], in PBS and DPBS schemes, the signatures cannot hide the length of underlying policies. Here, for simplicity, we explicitly include r as a part of the signature.
References
Abe M., Fuchsbauer G., Groth J., Haralambiev K., Ohkubo M.: Structure-preserving signatures and commitments to group elements. In: Rabin T. (ed.) CRYPTO 2010. Lecture Notes in Computer Science, vol. 6223, pp. 209–236. Springer, Heidelberg (2010).
Ajtai M.: Generating hard instances of the short basis problem. In: Wiedermann J., van Emde Boas P., Nielsen M. (eds.) ICALP 1999. Lecture Notes in Computer Science, vol. 1644, pp. 1–9. Springer, Heidelberg (1999).
Alwen J., Peikert C.: Generating shorter bases for hard random lattices. In: Albers S., Marion J. (eds.) STACS 2009. LIPIcs, vol. 3, pp. 75–86. Schloss Dagstuhl - Leibniz-Zentrum fuer Informatik, Germany (2009).
Bellare M., Fuchsbauer G.: Policy-based signatures. In: Krawczyk H. (ed.) PKC 2014. Lecture Notes in Computer Science, vol. 8383, pp. 520–537. Springer, Heidelberg. http://eprint.iacr.org/2013/413 (2014).
Boyen X.: Mesh signatures. In: Naor M. (ed.) EUROCRYPT 2007. Lecture Notes in Computer Science, vol. 4515, pp. 210–227. Springer, Heidelberg (2007).
Boyen X.: Lattice mixing and vanishing trapdoors: a framework for fully secure short signatures and more. In: Nguyen P., Pointcheval D. (eds.) PKC 2010. Lecture Notes in Computer Science, vol. 6056, pp. 499–517. Springer, Heidelberg (2010).
Brakerski Z., Kalai Y.T.: A framework for efficient signatures, ring signatures and identity based encryption in the standard model. Cryptology ePrint Archive, Report 2010/086 (2010). http://eprint.iacr.org/2010/086.
Camenisch J., Hohenberger S., Lysyanskaya A.: Compact e-cash. In: Cramer R. (ed.) EUROCRYPT 2005. Lecture Notes in Computer Science, vol. 3494, pp. 302–321. Springer, Heidelberg (2005).
Camenisch J., Lysyanskaya A.: An Efficient system for non-transferable anonymous credentials with optional anonymity revocation. In: Pfitzmann B. (ed.) EUROCRYPT 2001. Lecture Notes in Computer Science, vol. 2045, pp. 93–118. Springer, Heidelberg (2001).
Camenisch J., Neven G., Rückert M.: Fully anonymous attribute tokens from lattices. In: Visconti I., De Prisco R. (eds.) SCN 2012. Lecture Notes in Computer Science, vol. 7485, pp. 57–75. Springer, Heidelberg (2012).
Cash D., Hofheinz D., Kiltz E., Peikert C.: Bonsai trees, or how to delegate a lattice basis. In: Gilbert H. (ed.) EUROCRYPT 2010. Lecture Notes in Computer Science, vol. 6110, pp. 523–552. Springer, Heidelberg (2010).
Chase M., Lysyanskaya A.: On signatures of knowledge. In: Dwork C. (ed.) CRYPTO 2006. Lecture Notes in Computer Science, vol. 4117, pp. 78–96. Springer, Heidelberg (2006).
Chaum D., van Heyst E.: Group signatures. In: Davies D. (ed.) EUROCRYPT 1991. Lecture Notes in Computer Science, vol. 547, pp. 257–265. Springer, Heidelberg (1991).
Ducas L., Durmus A., Lepoint T., Lyubashevsky V.: Lattice signatures and bimodal Gaussians. In: Canetti R., Garay J. (eds.) CRYPTO 2013. Lecture Notes in Computer Science, vol. 8042, pp. 40–56. Springer, Heidelberg (2013).
Ducas L., Micciancio D.: Improved short lattice signatures in the standard model. In: Garay J., Gennaro R. (eds.) CRYPTO 2014. Lecture Notes in Computer Science, vol. 8616, pp. 335–352. Springer, Heidelberg (2014).
Gentry C., Peikert C., Vaikuntanathan V.: Trapdoors for hard lattices and new cryptographic constructions. In: STOC 2008, pp. 197–206. ACM, New York (2008).
Gordon S.D., Katz J., Vaikuntanathan V.: A group signature scheme from lattice assumptions. In: Abe M. (ed.) ASIACRYPT 2010. Lecture Notes in Computer Science, vol. 6477, pp. 395–412. Springer, Heidelberg (2010).
Groth J.: Evaluating security of voting schemes in the universal composability framework. In: Jakobsson M., Yung M., Zhou J. (eds.) ACNS 2004. Lecture Notes in Computer Science, vol. 3089, pp. 46–60. Springer, Heidelberg (2004).
Groth J., Sahai A.: Efficient non-interactive proof systems for bilinear groups. In: Smart N. (ed.) EUROCRYPT 2008. Lecture Notes in Computer Science, vol. 4965, pp. 415–432. Springer, Heidelberg (2008).
Kawachi A., Tanaka K., Xagawa K.: Concurrently secure identification schemes based on the worst-case hardness of lattice problems. In: Pieprzyk J. (ed.) ASIACRYPT 2008. Lecture Notes in Computer Science, vol. 5350, pp. 372–389. Springer, Heidelberg (2008).
Kiltz E., Mityagin A., Panjwani S., Raghavan B.: Append-only signatures. In: Caires L., Italiano G.F., Monteiro L., Palamidessi C., Yung M. (eds.) ICALP 2005. Lecture Notes in Computer Science, vol. 3580, pp. 434–445. Springer, Heidelberg (2005).
Laguillaumie F., Langlois A., Libert B., Stehlé D.: Lattice-based group signatures with logarithmic signature size. In: Sako K., Sarkar P. (eds.) ASIACRYPT 2013. Lecture Notes in Computer Science, vol. 8270, pp. 41–61. Springer, Heidelberg (2013).
Langlois A., Ling S., Nguyen K., Wang H.: Lattice-based group signature scheme with verifier-local revocation. In: Krawczyk H. (ed.) PKC 2014. Lecture Notes in Computer Science, vol. 8383, pp. 345–361. Springer, Heidelberg (2014).
Ling S., Nguyen K., Stehlé D., Wang H.: Improved zero-knowledge proofs of knowledge for the ISIS Problem, and applications. In: Kurosawa K., Hanaoka G. (eds.) PKC 2013. Lecture Notes in Computer Science, vol. 7778, pp. 107–124. Springer, Heidelberg (2013).
Ling S., Nguyen K., Wang H.: Group signatures from lattices: simpler, tighter, shorter, ring-based. In: Katz J. (ed.) PKC 2015. Lecture Notes in Computer Science, vol. 9020, pp. 427–449. Springer, Heidelberg (2015).
Lyubashevsky V.: Fiat–Shamir with aborts: applications to lattice and factoring-based signatures. In: Matsui M. (ed.) ASIACRYPT 2009. Lecture Notes in Computer Science, vol. 5912, pp. 598–616. Springer, Heidelberg (2009).
Lyubashevsky V.: Lattice signatures without trapdoors. In: Pointcheval D., Johansson T. (eds.) EUROCRYPT 2012. Lecture Notes in Computer Science, vol. 7237, pp. 738–755. Springer, Heidelberg (2012).
Lyubashevsky V., Micciancio D.: Asymptotically efficient lattice-based digital signatures. In: Canetti R. (ed.) TCC 2008. Lecture Notes in Computer Science, vol. 4948, pp. 37–54. Springer, Heidelberg (2008).
Maji H.K., Prabhakaran M., Rosulek M.: Attribute-based signatures. In: Kiayias A. (ed.) CT-RSA 2011. Lecture Notes in Computer Science, vol. 6558, pp. 376–392. Springer, Heidelberg (2011).
Micciancio D., Peikert C.: Trapdoors for lattices: simpler, tighter, faster, smaller. In: Pointcheval D., Johansson T. (eds.) EUROCRYPT 2012. Lecture Notes in Computer Science, vol. 7237, pp. 700–718. Springer, Heidelberg (2012).
Nguyen M.H., Ong S.J., Vadhan S.P.: Statistical zero-knowledge arguments for NP from any one-way function. In: FOCS 2006, pp. 3–14. IEEE Computer Society, Los Alamitos (2006).
Nguyen P.Q., Zhang J., Zhang Z.: Simpler efficient group signatures from lattices. In: Katz J. (ed.) PKC 2015. Lecture Notes in Computer Science, vol. 9020, pp. 401–426. Springer, Heidelberg (2015).
Pointcheval D., Vaudenay S.: On provable security for digital signature algorithms. Technical Report LIENS-96-17, Laboratoire d’Informatique de l’Ecole Normale Supérieure (1996).
Regev O.: On lattices, learning with errors, random linear codes, and cryptography. In: STOC 2005, pp. 84–93. ACM, New York (2005).
Rivest R.L., Shamir A., Tauman Y.: How to leak a secret. In: Boyd C. (ed.) ASIACRYPT 2001. Lecture Notes in Computer Science, vol. 2248, pp. 552–565. Springer, Heidelberg (2001).
Rückert M.: Lattice-based blind signatures. In: Abe M. (ed.) ASIACRYPT 2010. Lecture Notes in Computer Science, vol. 6477, pp. 413–430. Springer, Heidelberg (2010).
Stern J.: A new paradigm for public key identification. IEEE Trans. Inf. Theory 42(6), 1757–1768 (1996).
Acknowledgments
The research of Shantian Cheng is supported by NTU Research Scholarship at Nanyang Technological University. The research of Khoa Nguyen and Huaxiong Wang is supported by Research Grant TL-9014101684-01 and by the Singapore Ministry of Education under Research Grant MOE2013-T2-1-041. The authors would like to thank San Ling and Chaoping Xing for their support all along, and the anonymous reviewers for the valuable comments, which help to greatly improve the quality of this paper.
Author information
Authors and Affiliations
Corresponding author
Additional information
Communicated by C. Boyd.
Appendices
Appendix 1: Proof of Lemma 6
The simulator \(\mathcal {S}im\) begins by selecting a random \(\overline{{\textsf {Ch}}}\in \{1,2,3\}\), and a random tape \(r'\) of \(\widetilde{V}\).
-
Case \(\overline{{\textsf {Ch}}}=1\): The simulator works as follows:
-
1.
Compute \(\mathbf {z}_1',\cdots ,\mathbf {z}_k'\in {\mathbb {Z}}_q^{(2\ell +1)\cdot 3m}\) such that \({\mathbf {A}}^*\cdot \left( \sum _{i=1}^k\beta _i \mathbf {z}_i'\right) ={\mathbf {u}}\ \mathrm {mod}\ q\).
-
2.
Compute \(\overline{{\mathbf {p}}}\in \{0,1\}^\ell \) and \(\overline{{\mathbf {w}}}^*\in {\mathbb {Z}}_2^{2d}\) such that \(\mathbf{G}_1\cdot \overline{{\mathbf {p}}}+\mathbf{G}_2^*\cdot \overline{{\mathbf {w}}}^*=\mathbf{M}\ \mathrm {mod}\ 2\). As we set parameter d satisfies \(d+\ell >n\), it is feasible to compute \(\overline{{\mathbf {p}}}\) and \(\overline{{\mathbf {w}}}^*\). Then set \(\overline{{\mathbf {p}}}^*={\textsf {PolicyExt}}(\overline{{\mathbf {p}}})\).
-
3.
Sample
$$\begin{aligned} {\left\{ \begin{array}{ll} \rho _1',\rho _2',\rho _3'\xleftarrow {\$}\{0,1\}^n;\,{\mathbf {e}}\xleftarrow {\$}\{0,1\}^\ell ;\,{\mathbf {r}}_{{\mathbf {p}}}\xleftarrow {\$}{\mathbb {Z}}_2^{2\ell +1};\\ {\mathbf {r}}_{\mathbf {z}}^{(1)},\cdots ,{\mathbf {r}}_{\mathbf {z}}^{(k)}\xleftarrow {\$}{\mathbb {Z}}_q^{(2\ell +1)\cdot 3m};\,{\mathbf {r}}_{\mathbf {w}}\xleftarrow {\$}{\mathbb {Z}}_2^{2d};\\ \pi _1,\cdots ,\pi _k\xleftarrow {\$}{\mathcal {S}}; \, \eta \xleftarrow {\$}{\textsf {S}}_{2d}, \end{array}\right. } \end{aligned}$$and send the commitment \({\textsf {CMT}}=({\mathbf {c}}_1',{\mathbf {c}}_2',{\mathbf {c}}_3')\) to the verifier, where
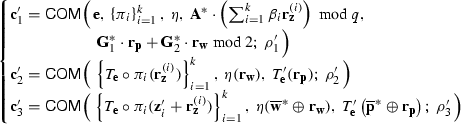
Receiving a challenge from \(\widetilde{V}\):
-
–
If \({\textsf {Ch}}=1\): Output \(\perp \) and abort.
-
–
If \({\textsf {Ch}}=2\): Set
$$\begin{aligned} {\textsf {RSP}}=\left( \,{\mathbf {e}},\,\left\{ \pi _i\right\} _{i=1}^k,\,\eta ,\,\overline{{\mathbf {p}}}^*\oplus {\mathbf {r}}_{{\mathbf {p}}}, \,\left\{ \mathbf {z}_i'+{\mathbf {r}}_{\mathbf {z}}^{(i)}\ \mathrm {mod}\ q\right\} _{i=1}^k,\,\overline{{\mathbf {w}}}^*\oplus {\mathbf {r}}_{\mathbf {w}}\,\right) , \end{aligned}$$and output \((r';{\textsf {CMT}};2;{\textsf {RSP}};\rho _1',\rho _3')\).
-
–
If \({\textsf {Ch}}=3\): Set
$$\begin{aligned} {\textsf {RSP}}=\left( \,{\mathbf {e}},\,\{\pi _i\}_{i=1}^k,\,\eta ,\,{\mathbf {r}}_{{\mathbf {p}}},\,\left\{ {\mathbf {r}}_{\mathbf {z}}^{(i)}\right\} _{i=1}^k,\,{\mathbf {r}}_{\mathbf {w}}\,\right) , \end{aligned}$$and output \((r';{\textsf {CMT}};3;{\textsf {RSP}};\rho _1',\rho _2')\).
-
1.
-
Case \(\overline{{\textsf {Ch}}}=2\): The simulator samples
$$\begin{aligned} {\left\{ \begin{array}{ll} \rho _1',\rho _2',\rho _3'\xleftarrow {\$}\{0,1\}^n;\,\overline{{\mathbf {p}}},{\mathbf {e}}\xleftarrow {\$}\{0,1\}^\ell ;\,{\mathbf {r}}_{{\mathbf {p}}}\xleftarrow {\$}{\mathbb {Z}}_q^{2\ell +1};\\ \mathbf {z}_1',\cdots ,\mathbf {z}_k'\xleftarrow {\$}{\textsf {SecretExt}}(\overline{{\mathbf {p}}});\,{\mathbf {r}}_{\mathbf {z}}^{(1)},\cdots ,{\mathbf {r}}_{\mathbf {z}}^{(k)}\xleftarrow {\$}{\mathbb {Z}}_q^{(2\ell +1)\cdot 3m};\, \overline{{\mathbf {w}}}^*, {\mathbf {r}}_{\mathbf {w}}\xleftarrow {\$} {\mathbb {Z}}_2^{2d};\\ \pi _1,\cdots ,\pi _k\xleftarrow {\$}{\mathcal {S}}; \, \eta \xleftarrow {\$}{\textsf {S}}_{2d}. \end{array}\right. } \end{aligned}$$Set \(\overline{{\mathbf {p}}}^*={\textsf {PolicyExt}}(\overline{{\mathbf {p}}})\) and send the commitment \({\textsf {CMT}}=({\mathbf {c}}_1',{\mathbf {c}}_2',{\mathbf {c}}_3')\) to the verifier, where
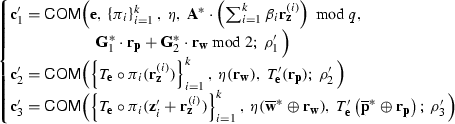
Receiving a challenge from \(\widetilde{V}\):
-
–
If \({\textsf {Ch}}=1\): Set
$$\begin{aligned} {\textsf {RSP}}&=\Big (\overline{{\mathbf {p}}}\oplus {\mathbf {e}},\,T_{\mathbf {e}}'(\overline{{\mathbf {p}}}^*),\,T_{\mathbf {e}}'({\mathbf {r}}_{{\mathbf {p}}}), \,\left\{ T_{\mathbf {e}}\circ \pi _i(\mathbf {z}_i')\right\} _{i=1}^k,\\&\quad \left\{ T_{\mathbf {e}}\circ \pi _i({\mathbf {r}}_{\mathbf {z}}^{(i)}) \right\} _{i=1}^k,\,\eta (\overline{{\mathbf {w}}}^*),\,\eta ({\mathbf {r}}_{\mathbf {w}})\,\Big ), \end{aligned}$$and output \((\,r';\,{\textsf {CMT}};\,1;\,{\textsf {RSP}};\,\rho _2',\,\rho _3'\,)\).
-
–
If \({\textsf {Ch}}=2\): Output \(\perp \) and abort.
-
–
If \({\textsf {Ch}}=3\): Set
$$\begin{aligned} {\textsf {RSP}}=\left( \,{\mathbf {e}},\,\{\pi _i\}_{i=1}^k,\,\eta ,\,{\mathbf {r}}_{\mathbf {p}}, \, \left\{ {\mathbf {r}}_{\mathbf {z}}^{(i)}\right\} _{i=1}^k,\,{\mathbf {r}}_{{\mathbf {w}}}\right) , \end{aligned}$$and output \((r';{\textsf {CMT}};3;{\textsf {RSP}};\rho _1',\rho _2')\).
-
–
-
Case \(\overline{{\textsf {Ch}}}=3\): The simulator proceeds the sampling as in the case \(\overline{{\textsf {Ch}}}=2\) above. Then send the commitment \({\textsf {CMT}}=({\mathbf {c}}_1',{\mathbf {c}}_2',{\mathbf {c}}_3')\) to the verifier, where
$$\begin{aligned} {\left\{ \begin{array}{ll} {\mathbf {c}}_1'={\textsf {COM}}\left( \,{\mathbf {e}},\,\left\{ \pi _i\right\} _{i=1}^k,\,\eta ,\,{\mathbf {A}}^*\cdot \left( \sum \nolimits _{i=1}^k\beta _i\left( \mathbf {z}_i'+{\mathbf {r}}_{\mathbf {z}}^{(i)}\right) \right) -{\mathbf {u}}\ \mathrm {mod}\ q,\right. \\ \left. \qquad \qquad \qquad \quad \,\mathbf{G}_1^*\cdot \left( \overline{{\mathbf {p}}}^*\oplus {\mathbf {r}}_{\mathbf {p}}\right) +\mathbf{G}_2^*\cdot \left( \overline{{\mathbf {w}}}^*\oplus {\mathbf {r}}_{\mathbf {w}}\right) -\mathbf{M}\ \mathrm {mod}\ 2;\,\rho _1'\,\right) \\ {\mathbf {c}}_2'={\textsf {COM}}\left( \,\left\{ T_{\mathbf {e}}\circ \pi _i({\mathbf {r}}_{\mathbf {z}}^{(i)})\right\} _{i=1}^k,\,\eta ({\mathbf {r}}_{\mathbf {w}}),\,T'_{\mathbf {e}}({\mathbf {r}}_{{\mathbf {p}}});\,\rho _2'\,\right) \\ {\mathbf {c}}_3'={\textsf {COM}}\left( \,\left\{ T_{\mathbf {e}}\circ \pi _i(\mathbf {z}_i'+{\mathbf {r}}_{\mathbf {z}}^{(i)})\right\} _{i=1}^k,\,\eta (\overline{{\mathbf {w}}}^*\oplus {\mathbf {r}}_{\mathbf {w}}),\,T'_{\mathbf {e}}\left( \overline{{\mathbf {p}}}^*\oplus {\mathbf {r}}_{{\mathbf {p}}}\right) ;\,\rho _3'\,\right) \end{array}\right. } \end{aligned}$$Receiving a challenge from \(\widetilde{V}\):
-
–
If \({\textsf {Ch}}=1\): Set
$$\begin{aligned}&{\textsf {RSP}}=\Big (\overline{{\mathbf {p}}}\oplus {\mathbf {e}},\,T_{\mathbf {e}}'(\overline{{\mathbf {p}}}^*),\,T_{\mathbf {e}}'({\mathbf {r}}_{{\mathbf {p}}}),\,\left\{ T_{\mathbf {e}}\circ \pi _i(\mathbf {z}_i')\right\} _{i=1}^k,\,\left\{ T_{\mathbf {e}}\circ \pi _i({\mathbf {r}}_{\mathbf {z}}^{(i)})\right\} _{i=1}^k,\,\eta (\overline{{\mathbf {w}}}^*),\,\eta ({\mathbf {r}}_{\mathbf {w}})\,\Big ), \end{aligned}$$and output \((r';{\textsf {CMT}};1;{\textsf {RSP}};\rho _2',\rho _3')\).
-
–
If \({\textsf {Ch}}=2\): Set
$$\begin{aligned} {\textsf {RSP}}=\left( \,{\mathbf {e}},\,\{\pi _i\}_{i=1}^k,\,\eta ,\,\overline{{\mathbf {p}}}^*\oplus {\mathbf {r}}_{\mathbf {p}}, \, \left\{ \mathbf {z}_i'+{\mathbf {r}}_{\mathbf {z}}^{(i)}\ \mathrm {mod}\ q\right\} _{i=1}^k,\,\overline{{\mathbf {w}}}^*\oplus {\mathbf {r}}_{{\mathbf {w}}}\right) , \end{aligned}$$and output \((r';{\textsf {CMT}};2;{\textsf {RSP}};\rho _1',\rho _3')\).
-
–
If \({\textsf {Ch}}=3\): Output \(\perp \) and abort.
-
–
Since \(\mathsf {COM}\) is statistically hiding, the distribution of the commitment CMT and the challenge Ch from \(\widetilde{V}\) are statistically close to those in the real interaction. Hence the simulator outputs \(\perp \) with probability negligibly close to 1 / 3. Moreover, if it does not halt, it is easy to prove that the simulator produces a successful transcript, and the distribution of the transcript is statistically close to that of the prover in the real interaction.
Appendix 2: Proof of Lemma 7
Let \({\textsf {CMT}}=({\mathbf {c}}_1,{\mathbf {c}}_2,{\mathbf {c}}_3)\in \left( {\mathbb {Z}}_q^n\right) ^3\) and let \({\textsf {RSP}}^{(1)}\), \({\textsf {RSP}}^{(2)}\), and \({\textsf {RSP}}^{(3)}\) be as in (5), (6) and (7). Since all 3 responses satisfy the verification conditions, the followings are true:
Since the commitment scheme COM is computationally binding, one can deduce that \({\mathbf {p}}_2={\mathbf {p}}_3\), \(\rho =\theta \), \(\phi _i=\psi _i\) for all \(i\in [k]\), and that
The extractor \({\mathcal {K}}\) proceeds as follows:
-
Extract \({\mathbf {p}}^*={\mathbf {t}}_{\mathbf {p}}\oplus {\mathbf {h}}_{\mathbf {p}}\). From \({\textsf {PolicyExt}}({\mathbf {p}}_1)={\mathbf {v}}_{\mathbf {p}}=T_{{\mathbf {p}}_2}'({\mathbf {t}}_{\mathbf {p}}\oplus {\mathbf {h}}_{\mathbf {p}})=T_{{\mathbf {p}}_2}'({\mathbf {p}}^*)\) and the equivalence (4), get \({\mathbf {p}}^*={\textsf {PolicyExt}}({\mathbf {p}}_1\oplus {\mathbf {p}}_2)\). As \({\mathbf {d}}\rightarrow {\textsf {PolicyExt}}({\mathbf {d}})\) is a bijection between the set \(\{0,1\}^\ell \) and the set \(\left\{ {\textsf {PolicyExt}}({\mathbf {d}}):{\mathbf {d}}\in \{0,1\}^\ell \right\} \), extract \({\mathbf {p}}'={\mathbf {p}}_1\oplus {\mathbf {p}}_2\) from \({\mathbf {p}}^*\). Note that vectors \({\mathbf {p}}',{\mathbf {p}}^*\) clearly satisfy \({\mathbf {p}}^*={\textsf {PolicyExt}}({\mathbf {p}}')\).
-
Extract \({\mathbf {w}}^*={\mathbf {t}}_{\mathbf {w}}\oplus {\mathbf {h}}_{\mathbf {w}}\). From \({\mathbf {v}}_{{\mathbf {w}}} \in \{0,1\}^{2d}, wt({\mathbf {v}}_{{\mathbf {w}}})=d\), \({\mathbf {v}}_{\mathbf {w}}=\rho ({\mathbf {t}}_{\mathbf {w}}\oplus {\mathbf {h}}_{\mathbf {w}})\), get \({\mathbf {w}}^*\in \{0,1\}^{2d}\), \(wt({\mathbf {w}}^*)=d\). Parse \({\mathbf {w}}^*\) as \(({\mathbf {w}}',{\mathbf {w}}'')\), where \({\mathbf {w}}',{\mathbf {w}}''\in \{0,1\}^d\). Note that from
$$\begin{aligned} \mathbf{G}_1^*\cdot \left( {\mathbf {t}}_{{\mathbf {p}}}\oplus {\mathbf {h}}_{\mathbf {p}}\right) +\mathbf{G}_2^*\cdot \left( {\mathbf {t}}_{\mathbf {w}}\oplus {\mathbf {h}}_{\mathbf {w}}\right) =\mathbf{M}\ \mathrm {mod}\ 2 \end{aligned}$$and the structure of \(\mathbf{G}_1^*,\mathbf{G}_2^*\), vector \({\mathbf {w}}'\) satisfies \(\mathbf{G}_1\cdot {\mathbf {p}}'+\mathbf{G}_2\cdot {\mathbf {w}}'=\mathbf{M}\ \mathrm {mod}\ 2\).
-
From
$$\begin{aligned} {\mathbf {A}}^*\cdot \left( \sum _{i=1}^k\beta _i\left( {\mathbf {t}}_\mathbf {z}^{(i)}-{\mathbf {h}}_\mathbf {z}^{(i)}\right) \right) ={\mathbf {u}}\ \mathrm {mod}\ q, \end{aligned}$$extract \(\mathbf {z}^*=\sum _{i=1}^k\beta _i\widetilde{{\mathbf {w}}}_i\), where for each \(i\in [k]\), \(\widetilde{{\mathbf {w}}}_i\) is obtained as follows:
-
Write the vector \(\widehat{{\mathbf {w}}}_i={\mathbf {t}}_\mathbf {z}^{(i)}-{\mathbf {h}}_\mathbf {z}^{(i)}\in \{-1,0,1\}^{(2l+1)\cdot 3m}\) as \(2\ell + 1\) blocks of length 3m.
-
Delete last 2m coordinates in each block of \(\widehat{{\mathbf {w}}}_i\).
Note that from \({\mathbf {A}}^*={\textsf {MatrixExt}}({\mathbf {A}})\), vector \(\mathbf {z}^*\) satisfies \({\mathbf {A}}\cdot \mathbf {z}^*={\mathbf {u}}\ \mathrm {mod}\ q\). Moreover, from \({\textsf {SecretExt}}({\mathbf {p}}_1)\ni {\mathbf {v}}_\mathbf {z}^{(i)}=T_{{\mathbf {p}}_2}\circ \phi _i\left( {\mathbf {t}}_\mathbf {z}^{(i)}-{\mathbf {h}}_\mathbf {z}^{(i)}\right) =T_{{\mathbf {p}}_2}\circ \phi _i\left( \widehat{{\mathbf {w}}}_i\right) \) and \(\phi _i\in {\mathcal {S}}\), by the equivalence (3), vector \(\widehat{{\mathbf {w}}}_i\) satisfies \(\widehat{{\mathbf {w}}}_i\in {\textsf {SecretExt}}({\mathbf {p}}_1\oplus {\mathbf {p}}_2)={\textsf {SecretExt}}({\mathbf {p}}')\).
Furthermore, \(\left||\mathbf {z}^*\right||_\infty \le \sum _{i=1}^k\beta _i\cdot \left||\widetilde{{\mathbf {w}}_i}\right||_\infty \le \sum _{i=1}^k\beta _i=\beta \), thus \(\mathbf {z}^*\in {\textsf {Secret}}_{\beta }({\mathbf {p}}')\), where \({\textsf {Secret}}_\beta ({\mathbf {p}})\) is the set of all vectors
$$\begin{aligned} {\mathbf {x}}=\left( {\mathbf {x}}_0||{\mathbf {x}}_1^0||{\mathbf {x}}_1^1||\cdots ||{\mathbf {x}}_\ell ^0||{\mathbf {x}}_\ell ^1\right) \in {\mathbb {Z}}^{(2\ell +1)\cdot m} \end{aligned}$$having \(2\ell +1\) blocks of size m, such that \(\left||{\mathbf {x}}\right||_\infty \le \beta \), and the following \(\ell \) blocks are zero-blocks \({\mathbf {0}}^m\): \({\mathbf {x}}_1^{1-{\mathbf {p}}[1]},\cdots ,{\mathbf {x}}_\ell ^{1-{\mathbf {p}}[\ell ]}\). Deleting zero blocks, extract \(\mathbf {z}'\in {\mathbb {Z}}^{(\ell +1)m}\) from \(\mathbf {z}^*\in {\mathbb {Z}}^{(2\ell +1)m}\). Then vector \(\mathbf {z}'\) satisfies \(\left||\mathbf {z}'\right||_\infty \le \beta \) and \({\mathbf {A}}_{{\mathbf {p}}'}\cdot \mathbf {z}'={\mathbf {u}}\ \mathrm {mod}\ q\).
-
From the discussion above, the output \(({\mathbf {p}}',\mathbf {z}',{\mathbf {w}}')\) of extractor \({\mathcal {K}}\) satisfies the requirement in \(R_{\text {PBS}}\) (see Definition 4).
Appendix 3: An improved forking lemma
In [33], Pointcheval and Vaudenay introduced an improved forking lemma for multiple forks. We state an adaptation of their result to the case of 3-fork as follows.
Lemma 8
Let \(\mathcal {SS}\) be a signature scheme with security parameter n. Let \(\mathcal {A}\) be a probability polynomial-time algorithm whose input only consists of public parameters, and which can ask \(q_{\mathcal {H}}\) queries to the random oracle, where \(q_{\mathcal {H}}>0\). Assume that, within the time bound T, algorithm \(\mathcal {A}\) produces, with probability \(\epsilon \), a valid signature \((\{{\textsf {CMT}}^{(i)}\}_{i=1}^t,\{{\textsf {Ch}}^{(i)}\}_{i=1}^t,\{{\textsf {RSP}}^{(i)}\}_{i=1}^t)\) of message \(\mathbf{M}\). Then, within time \(32\cdot T\cdot q_{\mathcal {H}}/\epsilon \), and with probability \(\epsilon '>1/2\), a replay of \(\mathcal {A}\) can output 3 valid signatures of message \(\mathbf{M}\):
such that the vectors \(\left( {\textsf {Ch}}_1^{(1)},\cdots ,{\textsf {Ch}}_1^{(t)}\right) \), \(\left( {\textsf {Ch}}_2^{(1)},\cdots ,{\textsf {Ch}}_2^{(t)}\right) \), \(\left( {\textsf {Ch}}_3^{(1)},\cdots ,{\textsf {Ch}}_3^{(t)}\right) \) are pairwise distinct.
Rights and permissions
About this article
Cite this article
Cheng, S., Nguyen, K. & Wang, H. Policy-based signature scheme from lattices. Des. Codes Cryptogr. 81, 43–74 (2016). https://doi.org/10.1007/s10623-015-0126-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10623-015-0126-y