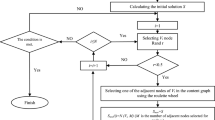
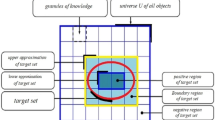
Abstract
Due to the huge amount of users and low entrance cost of online auction, there are a lot of online fraud cases in online auction sites. According to the IC3 reports from 2003 to 2010, we can understand the fraud cases and victims are increasing rapidly year by year. To improve the prevention of online auction frauds, this research will propose a hybrid approach to detect the fraudster accounts to help the users to identify which seller is more dangerous. In this research, we use social network analysis to produce the behavior features and transform these features into fuzzy rules which can represent the detection rules. Then optimize the fuzzy rules by genetic algorithms to build the auction fraud detection model. For implementation, we collect the real auction data from the online auction site http://www.ruten.com.tw which is the most popular auction site in Taiwan. Finally, we use the proposed features and methodologies to detect the fraudster accounts and find out the detection models of them. We hope the result of this research can help the website administrators to detect the possible collusive fraud groups easier in online auction.








Similar content being viewed by others
References
Borgatti, S. P. (1998). What is social network analysis? http://www.analytictech.com/networks/whatis.htm.Clarke.
Clarke, E. M., & Wing, J. M. (1996). Formal methods: state of the art and future directions. Journal ACM Computing Surveys, 28(4), 643.
Dong, F., Shatz, S. M., & Xu, H. (2009). Combating online in-auction fraud: clues, techniques and challenges. Computer Science Review, 3(4), 245–258.
Dong, F., Shatz, S. M., & Xu, H. (2009). Inference of online auction shills using dempster-shafer theory. In Proc. of the 6th international conference on information technology: new generations (pp. 908–914).
Elirlich, I. (1974). Participation in illegitimate activities. An economic analysis.
Garton, L., Haythornthwaite, C., & Wellman, B. (1999). Studying on-line social networks. In Doing Internet research: critical issues and methods for examining the Net (p. 75).
Gavish, B., & Tucci, C. L. (2006). Fraudulent auctions on the Internet. Electronic Commerce Research, 6(2), 127–140.
Internet Crime Complaint Center (2006), 2005 Internet crime report.
Internet Crime Complaint Center (2007), 2006 Internet crime report.
Internet Crime Complaint Center (2008), 2007 Internet crime report.
Internet Crime Complaint Center (2009), 2008 Internet crime report.
Internet Crime Complaint Center (2010), 2009 Internet crime report.
Internet Crime Complaint Center (2011), 2010 Internet crime report.
Lee, C. C. (1990). Fuzzy logic in control system: fuzzy logic controller. IEEE Transactions on Systems, Man and Cybernetics, 20(2), 404–435.
Livingston, J. A. (2010). Functional forms in studies of reputation in online auctions. Electronic Commerce Research, 10(2), 167–190.
Morzy, M. (2008). New algorithms for mining the reputation of participants of online auctions. Algorithmica, 52(1), 95–112.
National Police Agency (2012). http://www.165.gov.tw/, Taiwan.
Pan, W., Zhang, B., & Zhu, L. (2009). Genetic algorithm combined with immune mechanism and its application in skill fuzzy control. In Proceedings of the IEEE Chinese control and decision conference (pp. 4870–4874).
Pandit, S., Chau, D. H., Wang, S., & Faloutsos, C. (2007). Netprobe: a fast and scalable system for fraud detection in online auction networks. In Proceedings of the 16th international conference on world wide web (p. 210).
Rubin, S., Christodorescu, M., Ganapathy, V., Giffin, J. T., Kruger, L., Wang, H., et al. (2005). An auctioning reputation system based on anomaly. In Proceedings of the 12th ACM conference on computer and communications security (p. 279).
Trevathan, J., & Read, W. (2007). Detecting collusive shill bidding. In Fourth international conference on information technology, 2007, ITNG’07 (pp. 799–808).
Trevathan, J., & Read, W. (2009). Detecting shill bidding in online English auctions. In Handbook of research on social and organizational liabilities in information security.
Wang, J. C., & Chiu, C. C. (2008). Recommending trusted online auction sellers using social network analysis. Expert Systems with Applications, 34(3), 1666–1679.
Wang, J. C., & Chiu, C. (2005). Detecting online auction inflated-reputation behaviors using social network analysis. In Annual conference of the North American Association for Computational Social and Organizational Science.
Wasserman, S., & Faust, K. (1994). Social network analysis: methods and applications. Cambridge: Cambridge University Press.
Wellman, B. (1996). For a social network analysis of computer networks: a sociological perspective on collaborative work and virtual community. In Proceedings of the 1996 ACM SIGCPR/SIGMIS conference on computer personnel research (pp. 1–11).
Xu, H., & Cheng, Y. T. (2007). Model checking bidding behaviors in Internet concurrent auctions. International Journal of Computer Systems Science & Engineering, 22(4), 179–191.
Yu, C. H., & Lin, S. J. (2008). Parallel crawling and capturing for on-line auction. In Yang et al. (Eds.), LNCS: Vol. 5075. ISI 2008 workshops (pp. 455–466).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Yu, CH., Lin, SJ. Fuzzy rule optimization for online auction frauds detection based on genetic algorithm. Electron Commer Res 13, 169–182 (2013). https://doi.org/10.1007/s10660-013-9113-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10660-013-9113-4