Abstract
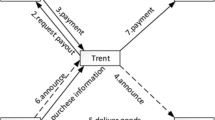
In this paper we present a secure and efficient transaction protocol that provides the anonymity and can detect the double spending. The proposed payment system is based on the ElGamal encryption scheme, the ElGamal signature scheme and the ElGamal blind signature protocol. We show that our transaction protocol is secure and efficient. We give the definitions of unlinkability and unforgeability of our security model and we prove that the proposed transaction protocol is unforgeable and satisfies the unlinkability property. We show that the proposed system is more efficient, in terms of the computation and communication cost, than the compared payment systems (Eslami et al. in Electron Commer Res Appl 10:59–66, 2011; Chen et al. in Electron Commer Res Appl 10:279–287, 2011; Liu et al. in Proceedings of second European PKI workshop: research and applications. Lecture notes in computer science, vol 3545, pp 206–214, 2005 and Chen et al. in Electron Commer Res Appl 10:673–682, 2011) for a customer who withdraws and spends an e-coin and for the merchant who verifies an electronic coin. Also, the proposed e-cash system is useful for the electronic transactions when the connection between the bank and the merchant is not available during the payment protocol. This means a less bandwidth of the payment protocol and then increases the speed of the electronic transaction.

Similar content being viewed by others
References
Bertoni, G., Breveglieri, L., Chen, L., Fragneto, P., Harrison, K., & Pelosi, G. (2008). A pairing SW implementation for smart-cards. J Syst Softw, 81(7), 1240–1247.
Camenisch, J., Piveteau, J. M., Stadler, M. (1995). Blind signatures based on the discrete logarithm problem. In A. De Santis (Ed.), Proceedings of EUROCRYPT ’94, Lecture notes in computer science, vol. 950, (pp. 428–432). Berlin: Springer.
Camenisch, J., Hohenberger, S., Lysyanskaya, A. (2005). Compact e-cash. In R. Cramer (Ed.), Proceedings of EuroCrypt’2005, Lecture notes in computer science, vol. 3494, (pp. 302–321). Berlin: Springer.
Canard, S., Gouget, A. (2007). Divisible e-cash systems can be truly anonymous. In S. Canard & A. Gouget (Eds.), Proceedings of EUROCRYPT 2007, Lecture notes in computer science, vol. 4515, (pp. 482–497). Berlin: Springer.
Chang, T., Hwang, M., & Yang, W. (2012). Cryptanalysis on an improved version of ElGamal-like public-key encryption scheme for encrypting large messages. Informatica, 23(4), 537–562.
Chaum, D. (1983). Blind signature for untraceable payments. In T. Beth (Ed.), Proceedings of Eurocrypt’82, Lecture notes in computer science, (pp. 199–203). New York: Plenum Press.
Chaum, D., Fiat, A., Naor, M. (1990) . Untraceable electronic cash. In S. Goldwasser (Ed.), Proceedings of the Crypto’88, Lecture notes in computer science, vol. 403, (pp. 319–327). Berlin: Springer.
Chen, C. L., & Liao, J. J. (2011). A fair online payment system for digital content via subliminal channel. Electron Commer Res Appl, 10(3), 279–287.
Chen, Y., Chou, J. S., Sun, H. M., & Cho, M. H. (2011). A novel electronic cash system with trustee-based anonymity revocation from pairing. Electron Commer Res Appl, 10(6), 673–682.
De Santis, A., Ferrara, A. L., & Masucci, B. (2007). An attack on a payment scheme. Inf Sci, 178(5), 1418–1421.
ECRYPT. (2008). Ecrypt yearly report on algorithms and key length. http://www.ecrypt.eu.org/ecrypt1/documents/D.SPA.28-1.1. Accessed 10 Jan 2015.
ElGamal, T. (1985). A public key cryptosystem and signature scheme based on discrete logarithms. IEEE Transact Inf Theor, 31(4), 469–472.
Eslami, Z., & Talebi, M. (2011). A new untraceable off-line electronic cash system. Electron Commer Res Appl, 10(1), 59–66.
Fan, C., & Huang, V. S. M. (2010). Provably secure integrated on/off-line electronic cash for flexible and efficient payment. IEEE Transact Syst Man Cybernetics-Part C: Appl Rev, 40(5), 567–579.
Hankerson, D., Menezes, A., & Scott, M. (2008). Software implementation of pairings. Identity Based Cryptogr, 2, 188–206.
Juang, W. S. (2003). A practical anonymous payment scheme for electronic commerce. Comput Math Appl, 46(12), 1787–1798.
Juang, W. S. (2007). D-cash: a flexible pre-paid e-cash scheme for date-attachment. Electron Commer Res Appl, 6(1), 74–80.
Kugler, D., Vogt, H. (2001). Marking: a privacy protecting approach against blackmailing. In K. Kim (Ed.), Proceedings of the 4th International Workshop on practice and theory in public key cryptography, vol.1992, (pp. 137–152). Berlin: Springer.
Lee, M., Ahn, G., Kim, J., Park, J., Lee, B., Kim, K., et al. (2002). Design and implementation of an efficient fair off-line e-cash system based on elliptic curve discrete logarithm problem. J Commun Netw, 4(2), 81–89.
Liu, K., Tsang, P., Wong, S. (2005). Recoverable and untraceable e-cash. In D. Chadwick & G. Zhao (Eds.), Proceedings of Second European PKI workshop: research and applications, Lecture notes in computer science, vol. 3545, (pp. 206–214). Berlin: Springer.
Menezes, A., van Oorschot, P., & Vanstone, S. (1997). Handbook of applied cryptography. Boca Raton: CRC Press Inc.
National Institute of Standards and Technology. (2013). Digital signature standard (DSS), Federal Information Processing Standards Publication 186-4.
National Institute of Standards and Technology. (2015). Secure hash standard, Federal Information Processing Standards Publication 180-4.
Okamoto, T. (1995). An efficient divisible electronic cash scheme. In D. Coppersmith (Ed.), Proceedings of Crypto’95, Lecture notes in computer science, vol. 963, (pp. 302–318). Berlin: Springer.
Oros, H., & Popescu, C. (2010). A secure and efficient off-line electronic payment system for wireless networks. Int J Comput Commun Control, 5(4), 551–557.
Pointcheval, D., & Stern, J. (2000). Security arguments for digital signatures and blind signatures. J Cryptol, 13(3), 361–396.
Popescu, C. (2009). An anonymous mobile payment system based on bilinear pairings. Informatica, 20(4), 579–590.
Popescu, C. (2011). A secure e-cash transfer system based on the elliptic curve discrete logarithm problem. Informatica, 22(3), 395–409.
Ramachandran, A., Zhou, Z., Huang, D. (2007). Computing cryptographic algorithms in portable and embedded devices. Proceedings of IEEE International Conference on Portable Information Devices (pp. 1–7), 25–29 March 2007. Orlando: IEEE.
Rivest, R. L., Shamir, A., & Adelman, L. (1978). A method for obtain digital signatures and public-key cryptosystem. Commun ACM, 21, 120–126.
Schneier, B. (1996). Applied cryptography (2nd ed.). New York: Wiley.
Trolin, M. (2005). A universally composable scheme for electronic cash. Proc INDOCRYPT, 3797, 347–360.
Wang, H., Cao, J., & Zhang, Y. (2005). A flexible payment scheme and its role-based access control. IEEE Transact Knowl Data Eng, 17(3), 425–436.
Zhang, L., Zhang, F., Qin, B., & Liu, S. (2011). Provably-secure electronic cash based on certificateless partially-blind signatures. Electron Commer Res Appl, 10(5), 545–552.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Popescu, C. A secure and efficient payment protocol based on ElGamal cryptographic algorithms. Electron Commer Res 18, 339–358 (2018). https://doi.org/10.1007/s10660-016-9236-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10660-016-9236-5