Abstract
We propose a formalism for specifying event stream abstractions for use in spacecraft telemetry processing. Our work is motivated by the need to quickly process streams with millions of events generated e.g. by the Curiosity rover on Mars. The approach builds a hierarchy of event abstractions for telemetry visualization and querying to aid human comprehension. Such abstractions can also be used as input to other runtime verification tools. Our notation is inspired by Allen’s Temporal Logic, and provides a rule-based declarative way to express event abstractions. We present an algorithm for applying specifications to an event stream and explore modifications to improve the algorithm’s asymptotic complexity. The system is implemented in both Scala and C, with the specification language implemented as internal as well as external DSLs. We illustrate the solution with several examples, a performance evaluation, and a real telemetry analysis scenario.




Similar content being viewed by others
Notes
Visualization of information is e.g. at JPL considered an important approach to aid humans in daily spacecraft operations.
\(\mathcal{V}\) can be any set of values that are part of monitored events.
The trace is artificially constructed to have no resemblance to real artifacts.
A limited form of disjunction is also allowed but not described here.
Time stamps have no specified units and their interpretation depends on the specification.
The GUI was designed and implemented by Nathaniel Guy (JPL).
Note that the eDSL uses
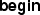 to denote the start time of an interval, in contrast to the notation in Sect. 4 where it was referred to as start (time).
to denote the start time of an interval, in contrast to the notation in Sect. 4 where it was referred to as start (time).The eDSL supports unary rules but we will avoid describing them here as they represent a special case.
References
Albarghouthi A, Baier JA, McIlraith SA (2009) On the use of planning technology for verification. In: Proceedings of the ICAPS workshop on verification & validation of planning & scheduling systems (VVPS), Citeseer
Allen JF (1983) Maintaining knowledge about temporal intervals. Commun ACM 26(11):832–843
Allen JF (1984) Towards a general theory of action and time. Artif Intell 23(2):123–154
Alur R, Fisman D, Raghothaman M (2016) Regular programming for quantitative properties of data streams. In: Programming languages and systems—25th European symposium on programming, ESOP 2016, Eindhoven, The Netherlands. Springer, LNCS, vol 9632, pp 15–40
Arasu A, Babu S, Widom J (2006) The CQL continuous query language: semantic foundations and query execution. Int J Very Large Data Bases 15(2):121–142
Barringer H, Havelund K (2011) TraceContract: a scala DSL for trace analysis. In: Proceedings of the 17th international symposium on formal methods (FM’11). Springer, LNCS, vol 6664, pp 57–72
Barringer H, Goldberg A, Havelund K, Sen K (2004) Rule-based runtime verification. In: International conference on verification, model checking, and abstract interpretation (VMCAI), vol 2937, pp 44–57
Barringer H, Rydeheard D, Havelund K (2008) Rule systems for run-time monitoring: from Eagle to RuleR. J Log Comput 20(3):675–706
Barringer H, Falcone Y, Havelund K, Reger G, Rydeheard D (2012) Quantified event automata: towards expressive and efficient runtime monitors. In: Proceedings of the 18th international symposium on formal methods (FM’12). Springer, pp 68–84. https://doi.org/10.1007/978-3-642-32759-9_9
Basin D, Harvan M, Klaedtke F, Zălinescu E (2011) MONPOLY: monitoring usage–control policies. In: 2nd international conference on runtime verification (RV’11). Springer, LNCS, vol 7186, pp 360–364
Basin D, Klaedtke F, Marinovic S, Zălinescu E (2015) Monitoring of temporal first-order properties with aggregations. Formal methods in system design. http://link.springer.com/article/10.1007/s10703-015-0222-7
Bauer A, Leucker M, Schallhart C (2007) The good, the bad, and the ugly, but how ugly is ugly? In: 7th International workshop on runtime verification (RV’07). Springer, LNCS, vol 4839, pp 126–138
Bauer A, Leucker M, Schallhart C (2011) Runtime verification for LTL and TLTL. ACM Trans Softw Eng Methodol (TOSEM) 20(4):14
Butler RW, Siminiceanu RI, Muno C (2007) The ANMLite language and logic for specifying planning problems. Report 215088:23681–2199
Chen F, Roşu G (2007) MOP: an efficient and generic runtime verification framework. In: ACM SIGPLAN notices. ACM, vol 42, pp 569–588
CLIPS (2017) Website. http://clipsrules.sourceforge.net. Accessed 21 March 2017
Colombo C, Pace GJ, Schneider G (2009) Larva—safer monitoring of real-time java programs (tool paper). In: Proceedings of the 2009 seventh IEEE international conference on software engineering and formal methods. IEEE Computer Society, Washington, DC, USA, SEFM ’09, pp 33–37. https://doi.org/10.1109/SEFM.2009.13
Cranor C, Johnson T, Spataschek O, Shkapenyuk V (2003) Gigascope: a stream database for network applications. In: Proceedings of the 2003 ACM SIGMOD international conference on management of data. ACM, pp 647–651
Cugola G, Margara A (2012) Processing flows of information: from data stream to complex event processing. ACM Comput Surv (CSUR) 44(3):15
D’Angelo B, Sankaranarayanan S, Sánchez C, Robinson W, Finkbeiner B, Sipma HB, Mehrotra S, Manna Z (2005) LOLA: Runtime monitoring of synchronous systems. In: Proceedings of the 12th international symposium on temporal representation and reasoning. IEEE Computer Society, pp 166–174
Decker N, Leucker M, Thoma D (2013) jUnitRV—adding runtime verification to jUnit. In: Brat G, Rungta N, Venet A (eds) NASA formal methods, 5th international symposium, NFM 2013, Moffett Field, CA, USA, May 14–16, 2013. Proceedings. Springer, Lecture Notes in Computer Science, vol 7871, pp 459–464. https://doi.org/10.1007/978-3-642-38088-4_34
Decker N, Leucker M, Thoma D (2016) Monitoring modulo theories. Int J Softw Tools Technol Transf 18(2):205–225. https://doi.org/10.1007/s10009-015-0380-3
Dillon LK, Kutty G, Moser LE, Melliar-Smith PM, Ramakrishna YS (1994) A graphical interval logic for specifying concurrent systems. ACM Trans Softw Eng Methodol 3:131–165
Doorenbos RB (1995) Production matching for large learning systems. Ph.D. thesis, Carnegie Mellon University, Pittsburgh, PA, USA
Drools (2017) Website. http://www.jboss.org/drools. Accessed 21 March 2017
Eckert M, Bry F (2009) Complex event processing (CEP). Informatik-Spektrum 32(2):163–167
Ernst MD, Perkins JH, Guo PJ, McCamant S, Pacheco C, Tschantz MS, Xiao C (2007) The Daikon system for dynamic detection of likely invariants. Sci Comput Progr 69(1):35–45
Falcone Y, Havelund K, Reger G (2013) A tutorial on runtime verification. In: Engineering dependable software systems, pp 141–175. https://doi.org/10.3233/978-1-61499-207-3-141
Finkbeiner B, Sankaranarayanan S, Sipma H (2005) Collecting statistics over runtime executions. Form Methods Syst Des 27(3):253–274
Forgy C (1982) Rete: a fast algorithm for the many pattern/many object pattern match problem. Artif Intell 19:17–37
Goubault-Larrecq J, Olivain J (2008) A smell of ORCHIDS. In: Proceedings of the 8th international workshop on runtime verification (RV’08). Springer, LNCS, vol 5289, pp 1–20
Hallé S (2016) When RV, Meets CEP. In: Runtime verification: Proceedings of 16th international conference, RV 2016, Madrid, Spain, September 23–30, 2016. Springer, pp 68–91
Hallé S, Gaboury S, Bouchard B (2016) Activity recognition through complex event processing: first findings. In: AAAI workshop: artificial intelligence applied to assistive technologies and smart environments
Hansen MR, Van Hung D (2007) A theory of duration calculus with application. In: Domain modeling and the duration calculus, LNCS, vol 4710. Springer, pp 119–176
Havelund K (2015) Rule-based runtime verification revisited. Int J Softw Tools Technol Transf 17(2):143–170
Havelund K, Joshi R (2014) Comprehension of spacecraft telemetry using hierarchical specifications of behavior. In: Merz S, Pang J (eds) Formal methods and software engineering: 16th international conference on formal engineering methods, ICFEM 2014, Luxembourg, November 3–5, 2014. Proceedings. Springer International Publishing, LNCS, vol 8829, pp 187–202
Havelund K, Joshi R (2015) Experience with rule-based analysis of spacecraft logs. In: Artho C, Ölveczky CP (eds) Formal techniques for safety-critical systems: third international workshop (FTSCS 2014), November 2014, Luxembourg. Springer International Publishing, Communications in Computer and Information Science, vol 476, pp 1–16
Havelund K, Peled D, Ulus D (2017) First order temporal logic monitoring with BDDs. 17th Conference on formal methods in computer-aided design (FMCAD 2017), 2–6 October, Austria. IEEE Computer Society, Vienna, pp 116–123
Jess (2017) Website. http://www.jessrules.com/jess. Accessed 21 March 2017
Kauffman S, Havelund K, Joshi R (2016) nfer—a notation and system for inferring event stream abstractions. In: Falcone Y, Sánchez C (eds) Runtime verification: 16th international conference, RV 2016, Madrid, Spain, September 23–30, 2016, Proceedings. Springer, LNCS, vol 10012, pp 235–250
Kearns SM (1991) Extending regular expressions with context operators and parse extraction. Softw Pract Exp 21(8):787–804. https://doi.org/10.1002/spe.4380210803
Kreps J, Narkhede N, Rao J (2011) Kafka: a distributed messaging system for log processing. In: Proceedings of the 6th international workshop on networking meets databases (NetDB’11). ACM, pp 1–7
Legay A, Delahaye B, Bensalem S (2010) Statistical model checking: an overview. In: 1st international conference on runtime verification (RV’10). Springer, LNCS, vol 6418
Leucker M, Schallhart C (2009) A brief account of runtime verification. J Log Algebr Program 78(5):293–303. https://doi.org/10.1016/j.jlap.2008.08.004
Luckham D (2002) The power of events: an introduction to complex event processing in distributed enterprise systems. Addison-Wesley, Boston
Mcdermott D, Ghallab M, Howe A, Knoblock C, Ram A, Veloso M, Weld D, Wilkins D (1998) PDDL—the planning domain definition language. Tech. rep., CVC TR-98-003/DCS TR-1165, Yale Center for Computational Vision and Control
Meredith P, Jin D, Griffith D, Chen F, Roşu G (2011) An overview of the MOP runtime verification framework. Int J Softw Tools Technol Transf. https://doi.org/10.1007/s10009-011-0198-6
Moszkowski BC (1985) A temporal logic for multilevel reasoning about hardware. IEEE Comput 18:10–19
Narayan A, Kauffman S, Morgan J, Tchamgoue GM, Joshi Y, Hobbs C, Fischmeister S (2017) System call logs with natural random faults: experimental design and application. In: SELSE-13: the 13th workshop on silicon errors in logic, system effects, Boston, MA, USA
Navabpour S, Joshi Y, Wu W, Berkovich S, Medhat R, Bonakdarpour B, Fischmeister S (2013) RiTHM: a tool for enabling time-triggered runtime verification for C programs. In: Proceedings of the 2013 9th joint meeting on foundations of software engineering. ACM, pp 603–606
QNX (1997) QNX operating system: system architecture. QNX Software Systems Ltd, Ontario
R Development Core Team (2008) R: A Language and Environment for Statistical Computing. R Foundation for Statistical Computing, Vienna, Austria. ISBN: 3-900051-07-0. http://www.R-project.org
Reger G (2014) Automata based monitoring and mining of execution traces. Ph.D. thesis, University of Manchester
Reger G, Cruz HC, Rydeheard D (2015) MarQ: monitoring at runtime with QEA. In: Proceedings of the 21st international conference on tools and algorithms for the construction and analysis of systems (TACAS’15)
Rosu G, Bensalem S (2006) Allen linear (interval) temporal logic—translation to LTL and monitor synthesis. In: 18th international conference on computer aided verification (CAV’06). Springer, LNCS, vol 4144, pp 263–277
Siminiceanu R, Butler RW, Muñoz CA (2009) Experimental evaluation of a planning language suitable for formal verification. In: 5th international workshop on model checking and artificial intelligence (MoChArt’08), LNCS, vol 5348. Springer, pp 132–146
Xilinx (2017) Zynq-7000 all programmable soc zc706 evaluation kit. https://www.xilinx.com/products/boards-and-kits/ek-z7-zc706-g.html. Accessed 13 March 2017
Author information
Authors and Affiliations
Corresponding author
Additional information
The research performed by K. Havelund and R. Joshi and part of the research performed by S. Kauffman was carried out at Jet Propulsion Laboratory, California Institute of Technology, under a contract with the National Aeronautics and Space Administration. The research performed by K. Havelund was furthermore supported by AFOSR Grant FA9550-14-1-0261.
Rights and permissions
About this article
Cite this article
Kauffman, S., Havelund, K., Joshi, R. et al. Inferring event stream abstractions. Form Methods Syst Des 53, 54–82 (2018). https://doi.org/10.1007/s10703-018-0317-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10703-018-0317-z





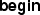 to denote the start time of an interval, in contrast to the notation in Sect.
to denote the start time of an interval, in contrast to the notation in Sect.