Abstract
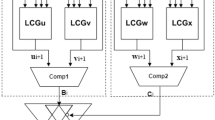
Modern FPGAs have a great market share in hardware prototyping, massive parallel systems and reconfigurable architectures. Although the field-programmability of FPGAs is an effective feature in the growth and diversity of their applications; it has caused security concerns for IPs/Designs on FPGAs. Recent researches show that a reliable mechanism is required to protect the IPs/applications on FPGAs against malicious manipulations during all stages of design lifecycle, especially when they are operating in the field. In this paper, we propose a new tamper-resistant design methodology (Security Path methodology) and a revised security-aware FPGA architecture. This methodology protects the configured design against tampering attacks in parallel with the normal operation of the circuit. When the attack is discovered, the normal data flow is obfuscated and the circuit is blocked. Experimental results show that this methodology provides near full coverage in tampering detection with overhead of 12.32 % in power, 12 % in delay and 38 % in area.










Similar content being viewed by others
References
Altera Corporation (2014) Altera unique chip ID IP core user guide. ug-altchipid
Chakraborty RS, Saha I, Palchaudhuri A (2013) Hardware Trojan insertion by direct modification of FPGA configuration bitstream. IEEE Des Test 30(2):45–54
Hori Y, Katashita T, Sasaki A (2012) Electromagnetic side-channel attack against 28-nm FPGA device. In: International workshop on information security applications, pp 16–18
Hutton M, Lewis D, Pedersen B (2006) Fracturable FPGA logic elements, CP-01006-1.0 http://www.altera.Com/literature/cp/cp-01006.pdf, Tech. Rep.
Kastensmidt F, Carro L, Reis R (2006) Fault-tolerance techniques for SRAM-based FPGAs. In: Series: frontiers in electronic testing, vol 32. Springer, pp 180–185
Lu T, Kenny R, Atsatt S (2015) Stratix 10 secure device manager provides best-in-class FPGA and SoC security. White paper, WP-01252-10
Luu J, Anderson J, Rose J (2011) Architecture description and packing for logic blocks with hierarchy, modes and complex interconnect. In: Proceedings of the 19th ACM/SIGDA international symposium on field programmable gate arrays, pp 227–236
McNeil S (2012) Solving today’s design security concerns. Xilinx, White paper, WP365 (v1.2) July 30
Moradi A, Barenghi A, Kasper T, Paar C (2011) On the vulnerability of FPGA bitstream encryption against power analysis attacks: Extracting keys from Xilinx Virtex-II FPGAs. In: Proceedings of ACM conference on computer and communications security, pp 111–124
Moradi A, Barenghi A, Paar C (2011) On the vulnerability of FPGA bitstream encryption against power analysis attacks. In: Proceedings of the 18th ACM conference on computer and communications security. ACM, pp 111–123
Moradi A, Kasper M, Parr C (2012) Black-box side-channel attacks highlight the importance of countermeasuresVAn analysis of the Xilinx Virtex 4 and Virtex-5 bitstream encryption mechanism. In: Proceedings of the 12th conference topics in cryptology doi:10.1007/978-3-642-27954-6_1
Moradi A, Oswald D, Paar C, Swierczynski P (2013) Side channel attacks on the bitstream encryption mechanism of Altera Stratix II. In: Proceedings of the ACM/SIGDA international symposium on field-programmable gate arrays, pp 91–100
Mudler E, Buysschaert P, Delmotte P (2005) Electromagnetic analysis attack on an FPGA implementation of an elliptic curve cryptosystem. In: International conference on computer as a tool (EUROCON), pp 1879–1882
Note J, Rannaud E (2008) From the bitstream to the netlist. In: Proceedings of the 16th international ACM/SIGDA symposium on field programmable gate arrays, pp 264–270
Peterson E (2013) Developing tamper resistant designs with Xilinx Virtex-6 and 7 series FPGAs. Xilinx, Appl, XAPP1084 (v13)
Rajendran J, Zhang H, Karri R (2015) Fault analysis-based logic encryption. IEEE Trans Comput 64 (2):410–424
Rajendran J, Zhang H, Karri R et al (2015) Fault analysis-based logic encryption. IEEE Trans Comput 64(2):410–424
Rose J, Luu J, Goeders J (2014) VTR 7.0: next generation architecture and CAD system for FPGAs. In: ACM transaction on reconfigurable technology and systems (TRETS), vol 7, no 2
Skorobogatov S, Woods C (2012) Breakthrough silicon scanning discovers backdoor in military chip. In: Cryptographic hardware and embedded systems VCHES 2012, vol 7428. Springer, Berlin, pp 23–40
Stratix IV FPGA ALM Logic Structure’s Fracturable LUT (2015) Available on https://www.altera.com/products
Swierczynski P, Fyrbiak M, Paar C (2015) FPGA Trojans through detecting and weakening of cryptographic primitives. In: IEEE transactions on computer aided design, pp 1–13
Trimberger S, Moore J (2014) FPGA security: from features to capabilities to trusted systems. In: Design automation conference DAC’14, pp 1–4
Trimberger SM, Moore J (2014) FPGA security: motivations, features, and applications. Invited paper in Proc IEEE 102(8):1248–1265
Vu TH, Cuong NV (2012) A framework for secure remote updating of bitstream of runtime reconfigurable embedded platforms. In: Communications and electronics, pp 471–476
Xilinx Virtex-6 FPGA Configurable Logic Block User’s Guide (2014) Available on http://www.xilinx.com/support
Xilinx Virtex-7 family overview (2015) Available on http://www.xilinx.com/products/silicon-devices/fpga/
Zhang J, Qu G (2014) A survey on security and trust of FPGA-based systems. In: International conference on field programmable technology (FPT), pp 147–152
Author information
Authors and Affiliations
Corresponding author
Additional information
Responsible Editor: M. Tehranipoor
Rights and permissions
About this article
Cite this article
Zamanzadeh, S., Jahanian, A. Security Path: An Emerging Design Methodology to Protect the FPGA IPs Against Passive/Active Design Tampering. J Electron Test 32, 329–343 (2016). https://doi.org/10.1007/s10836-016-5593-1
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10836-016-5593-1