Abstract
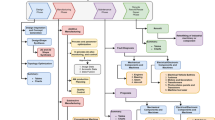
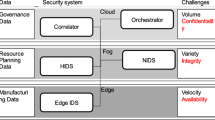
CyberManufacturing system (CMS) is a vision for future manufacturing systems. The concept delineates a vision of advanced manufacturing system integrated with technologies such as Internet of Things, Cloud Computing, Sensors Network and Machine Learning. As a result, cyber-attacks such as Stuxnet attack will increase along with growing simultaneous connectivity. Now, cyber-physical attacks are new and unique risks to CMSs and modern cyber security countermeasure is not enough. To learn this new vulnerability, the cyber-physical attacks is defined via a taxonomy under the vision of CMS. Machine learning on physical data is studied for detecting cyber-physical attacks. Two examples were developed with simulation and experiments: 3D printing malicious attack and CNC milling machine malicious attack. By implementing machine learning methods in physical data, the anomaly detection algorithm reached 96.1% accuracy in detecting cyber-physical attacks in 3D printing process; random forest algorithm reached on average 91.1% accuracy in detecting cyber-physical attacks in CNC milling process.









Similar content being viewed by others
References
Bosch, A., Zisserman, A., & Munoz, X. (2007). Image classification using random forests and ferns. In 2007 IEEE 11th international conference on computer vision, pp. 1–8.
Chandola, V., Banerjee, A., & Kumar, V. (2009). Anomaly detection. ACM Computing Surveys, 41(3), 1–58.
Chandola, V., Banerjee, A., & Kumar, V. (2009). Anomaly detection: A survey. ACM Computig Surveys, 41(3), 1–58.
Duro, J. A., Padget, J. A., Bowen, C. R., & Kim, H. A. (2016). Multi-sensor data fusion framework for Cnc machining monitoring. Mechanical Systems and Signal Processing, 67, 505–520.
Garcia, R. F., Rolle, J. L. C., & Castelo, J. P. (2011). A review of SCADA anomaly detection systems. Advances in Intelligent and Soft Computing, 87, 405–414.
IBM (2016). Reviewing a year of serious data breaches, major attacks and new vulnerabilities.
Jain, A. K., Ross, A., & Prabhakar, S. (2004). An introduction to biometric recognition. IEEE Transactions on Circuits and Systems for Video Technology, 14(1), 4–20.
Jazdi, N. (2014). Cyber physical systems in the context of industry 4.0. In Automation, quality and testing, robotics. 2014 IEEE , pp. 2–4.
Jia, H., Murphey, Y. L., Shi, J., & Chang, T. S. (2004). An intelligent real-time vision system for surface defect detection. Proceedings—International Conference on Pattern Recognition, 3(February), 239–242.
Karthikeyan, K. R., & Indra, A. (2010). Intrusion detection tools and techniques–A survey. International Journal of Computer Theory and Engineering, 2(6), 901–906.
Kelley, M. B. (2013). The Stuxnet attack On Iran’s nuclear plant was ‘Far More Dangerous’ than previously thought. Business Insider. http://www.businessinsider.com/stuxnet-was-far-more-dangerous-than-previous-thought-2013-11.
Kim, A. C., Park, W. H., & Lee, D. H. (2013). A study on the live forensic techniques for anomaly detection in user terminals. International Journal of Security and Its Applications, 7(1), 181–187.
Minnick, J. (2016). The Biggest Cybersecurity problems facing manufacturing in 2016. http://www.mbtmag.com/article/2016/01/biggest-cybersecurity-problems-facing-manufacturing.
Peterson, L. (2009). K-nearest neighbor. Scholarpedia. http://www.scholarpedia.org/article/K-nearest_neighbor. Accessed June 23, 2016.
Prashanth, G., Prashanth, V., Jayashree, P., & Srinivasan, N. (2008). Using random forests for network-based anomaly detection at active routers. In 2008 International conference on signal processing communications. Networking, 2008, pp. 93–96
Rabatel, J., Bringay, S., & Poncelet, P. (2011). Anomaly detection in monitoring sensor data for preventive maintenance. Expert Systems with Applications., 38, 7003–7015.
Ren, L., Zhang, L., Tao, F., Zhao, C., Chai, X., & Zhao, X. (2015). Cloud manufacturing: From concept to practice. Enterprise Information Systems, 9(2), 186–209.
Shen, Q., Gao, J., & Li, C. (2010). Automatic classification of weld defects in radiographic images. Insight Non-Destructive Testing Condition Monitoring, 52(3), 134–139.
Song, Z., & Moon, Y. B. (2016). Performance analysis of CyberManufacturing systems?: A simulation study. In 13th IFIP international conference on product lifecycle management.
Song, Z., Zhou, H., Cheung, J., & Lin, L. L. (2017). Detecting attacks in CyberManufacturing systems?: Subtractive manufacturing example. In International conference on manufacturing technologies, pp. 1–4.
Sturm, L. D., Williams, C. B., Camelio, J. A., White, J., & Parker, R. (2014). Cyber-physical Vunerabilities In Additive manufacturing systems, in international solid freeform fabrication symposium proceedings, pp. 951–963.
Turner, H., White, J., Camelio, J. A., Williams, C., Amos, B., & Parker, R. (2015). Bad parts: Are our manufacturing systems at risk of silent cyberattacks? IEEE Security & Privacy, 13(3), 40–47.
Vincent, H., Wells, L., Tarazaga, P., & Camelio, J. (2015). Trojan detection and side-channel analyses for cyber-security in cyber-physical manufacturing systems. Procedia Manufacturing, 1, 77–85.
Wells, L. J., Camelio, J. A., Williams, C. B., & White J. (2014). Cyber-physical security challenges in manufacturing systems. Manufacturing Letters, 2(2), 74–77.
WIRED (2015). Hackers remotely kill a jeep on the highway. https://www.wired.com/2015/07/hackers-remotely-kill-jeep-highway/. Accessed May 03, 2016.
Wu, M., Phoha, V. V., Moon, Y. B., & Belman, A. K.(2016). Detecting malicious defects in 3d printing process using machine learning and image classification. In Proceedings of the ASME 2016 international mechanical engineering congress and exposition, pp. 4–9.
Wu, M., Zhou, H., Lin, L. L., Silva, B., Song, Z., Cheung, J., & Moon, Y. (2016). Detecting attacks in CyberManufacturing systems?: Additive manufacturing example. In International conference on mechanical, materials and manufacturing, pp. 1–5.
Yampolskiy, M., Horvath, P., Koutsoukos, X. D., Xue, Y., & Sztipanovits, J. (2013). Taxonomy for description of cross-domain attacks on CPS. In Proceedings of the 2nd ACM international conference on high confidence networked systems, pp. 135–142.
Zeltmann, S. E., Gupta, N., Tsoutsos, N. G., Maniatakos, M., Rajendran, J., & Karri, R. (2016). Manufacturing and security challenges in 3D printing. Jom, 68(7), 1872–1881.
Zetter, K. (2015). A cyberattack has caused confirmed physical damage for the second time ever. In WIRED. https://www.wired.com/2015/01/german-steel-mill-hack-destruction/.
Zetter, K. (2015). Feds say that banned researcher commandeered a plane. In WIRED. https://www.wired.com/2015/05/feds-say-banned-researcher-commandeered-plane/.
Zhang, X. W., Ding, Y. Q., Lv, Y. Y., Shi, A. Y., & Liang, R. Y. (2011). A vision inspection system for the surface defects of strongly reflected metal based on multi-class SVM. Expert Systems with Applications, 38(5), 5930–5939.
Zhu, T., Ma, Q., Zhang, S., & Liu, Y. (2014). Context-free attacks using keyboard acoustic emanations. In Proceedings of 2014 ACM SIGSAC conference on computer and communication security— CCS ’14, 3(1), 453–464.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Wu, M., Song, Z. & Moon, Y.B. Detecting cyber-physical attacks in CyberManufacturing systems with machine learning methods. J Intell Manuf 30, 1111–1123 (2019). https://doi.org/10.1007/s10845-017-1315-5
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10845-017-1315-5