Abstract
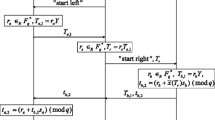
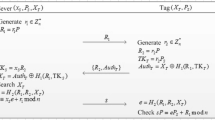
In this paper, we propose a tamper resistant prescription RFID access control protocol for different authorized readers. Not only the authentication mechanism but also the access right authorization mechanism is designed in our scheme. Only the specific doctor, usually the patient’s doctor, can access the tag. Moreover, some related information of patient’s prescription is attached to a RFID tag for tamper resistance. The patients’ rights will be guaranteed.


Similar content being viewed by others
References
J. Ericson, RFID for Hospital Care, The E-Business Executive Daily. (2004).
Fisher, J. A., and Monahan, T., Tracking The Social Dimensions of RFID Systems in Hospitals. International Journal of Medical Informatics 77(3):176–183, 2008.
Wang, S.-W., Chen, W.-H., Ong, C.-S., Liu, L., Chuang, Y.-W. RFID Applications in Hospitals: A Case Study on A Demonstration RFID Project in A Taiwan Hospital, Proceedings of The 39th Hawaii International Conference on System Sciences. (2006).
Chowdhury, B., Khosla, R., RFID-Based Hospital Real-Time Patient Management System, 6th IEEE/ACIS International Conference on Computer and Information Science (ICIS 2007). (2007).
Nahas, H.A., Deogun, J.S., Radio Frequency Identification Applications in Smart Hospitals, The Twentieth IEEE International Symposium on Computer-Based Medical Systems. (2007).
Xiao, Y., Shen, X., Sun, B., Cai, L. Security and Privacy in RFID and Applications in Telemedicine, IEEE Communications Magazine. (2006) 64–72.
Aguilar, A., van der Putten, W., and Kirrane, F., Positive Patient Identification using RFID and Wireless Networks, In HISI 11th Annual Conference and Scientific Symposium. Dublin, Ireland, 2006.
Bardram, J. Hospitals of The Future—Ubiquitous Computing Support for Medical Work in Hospitals, The Second International Workshop on Ubiquitous Computing for Pervasive Healthcare Application. (2003).
Bardram, J. Applications of Context-Aware Computing in Hospital Work: Examples and Design Principles, Proceedings of the 2004 ACM symposium on Applied Computing. (2004) 1574–1579.
V. Boginski, I.K. Mun, Y. Wu, K.P. Mason, C. Zhang, Simulation and Analysis of Hospital Operations and Resource Utilization Using RFID Data, 2007 IEEE International Conference on RFID Gaylord Texan Resort, Grapevine, TX, USA, March 26–28 (2007).
Ayoade, J., Security Implications in RFID and Authentication Processing Framework. Computers & Security 25(3):207–212, 2006.
C.-H. Kuo, H.-G. Chen, The Critical Issues about Deploying RFID in Healthcare Industry by Service Perspective, Proceedings of The 41st Hawaii International Conference on System Sciences. (2008).
H.-Y. Chien, Secure Access Control Schemes for RFID Systems with Anonymity, International Conference On Mobile Data Management. (2006) 96–99.
X. Gao, Z. Xiang, H. Wang, J. Shen, J. Huang, S.Song, An Approach to Security and Privacy of RFID System for Supply Chain, The E-Commerce Technology for Dynamic E-Business. (2004) 164–168.
H.-W. Kim, S.-Y. Lim, H.-J. Lee, Symmetric Encryption in RFID Authentication Protocol for Strong Location Privacy and Forward-Security, IEEE International Conference on Hybrid Information Technology (ICHIT′06). (2006) 718–723.
H.-S. Kim, J.-H. Oh, J.-Y. Choi, Analysis of The RFID Security Protocol for Secure Smart Home Network, International Conference on Hybrid Information Technology(ICHIT′06). 2 (2006) 356–363.
S.A. Weis, Security and Privacy in Radio-Frequency Identification Devices, Master’s Thesis, Massachusetts Institute of Technology. (2003).
S.A. Weis, S.E. Sarma, R.L. Rivest, D.W. Engels, Security and Privacy Aspects of Low-Cost Radio Frequency Identification Systems, International Conference on Security in Pervasive Computing, Lecture Notes in Computer Science. (2004) 201–212.
Zhang, L., Zhou, H., Kong, R., and Yang, F., An Improved Approach to Security And Privacy of RFID Application System, International Conference on Wireless Communications. Networking and Mobile Computing. 2:1195–1198, 2005.
Tamper Resistant Prescription Drug Pad Program, A Project of The Department of Health and Community Services, Government of Newfoundland and Labrador http://www.health.gov.nl.ca/health/nlpdp/Brochure_Updated_April_2009_Info_Pamphlet.pdf (2006).
WANURSES, New Tamper Resistant Prescription Pad Law, Nursing Practice Blog, http://www.wsnaweb.org/nursing-practice-update/index.php/2009/09/new-tamper-resistant-prescription-pad-law/. (2009).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Chen, YY., Huang, DC., Tsai, ML. et al. A Design of Tamper Resistant Prescription RFID Access Control System. J Med Syst 36, 2795–2801 (2012). https://doi.org/10.1007/s10916-011-9758-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10916-011-9758-2