Abstract
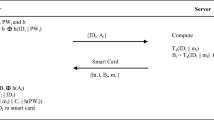
Many authentication schemes have been proposed for telecare medicine information systems (TMIS) to ensure the privacy, integrity, and availability of patient records. These schemes are crucial for TMIS systems because otherwise patients’ medical records become susceptible to tampering thus hampering diagnosis or private medical conditions of patients could be disclosed to parties who do not have a right to access such information. Very recently, Hao et al. proposed a chaotic map-based authentication scheme for telecare medicine information systems in a recent issue of Journal of Medical Systems. They claimed that the authentication scheme can withstand various attacks and it is secure to be used in TMIS. In this paper, we show that this authentication scheme is vulnerable to key-compromise impersonation attacks, off-line password guessing attacks upon compromising of a smart card, and parallel session attacks. We also exploit weaknesses in the password change phase of the scheme to mount a denial-of-service attack. Our results show that this scheme cannot be used to provide security in a telecare medicine information system.


Similar content being viewed by others
References
Bellare, M., Pointcheval, D., and Rogaway, P., Authenticated key exchange secure against dictionary attacks. In: Preneel, B. (Ed.), EUROCRYPT, Lecture Notes in Computer Science, Vol. 1807, pp. 139–155. Springer, 2000.
Bellare, M., and Rogaway, P., Entity authentication and key distribution. In: Stinson, D.R. (Ed.), CRYPTO, Lecture Notes in Computer Science. Vol. 773, pp. 232–249. Springer, 1993.
Bellovin, S. M., and Merritt, M., Encrypted key exchange: Password-based protocols secure against dictionary attacks. In: Proceedings of the IEEE Symposium on Research in Security and Privacy. pp. 72–84. Oakland, CA: IEEE Computer Society, 1992.
Bergamo, P., D’Arco, P., De Santis, A., and Kocarev, L., Security of public-key cryptosystems based on Chebyshev polynomials. IEEE Trans. Circ. Syst I: Regular Pap. 52(7):1382–1393, 2005.
Blake-Wilson, S., and Menezes, A., Unknown key-share attacks on the station-to-station (STS) protocol. In: Public Key Cryptography, Lecture Notes in Computer Science. Vol. 1560, pp. 154–170. Berlin: Springer, 1999.
Canetti, R., and Krawczyk, H., Analysis of key-exchange protocols and their use for building secure channels. In: Pfitzmann B. (Ed.), EUROCRYPT, Lecture Notes in Computer Science. Vol. 2045, pp. 453–474. Springer, 2001.
Chung, H. R., and Ku, W. C., Three weaknesses in a simple three-party key exchange protocol. Inf. Sci. 178(1):220–229, 2008.
Diffie, W., Oorschot, P. C., and Wiener, M. J., Authentication and authenticated key exchanges. Des. Codes Crypt. 2:107–125, 1992.
Dojen, R., Jurcut, A., Coffey, T., and Györödi, C.: On establishing and fixing a parallel session attack in a security protocol. In: Badica, C., Mangioni, G., Carchiolo, V., Burdescu, D. D. (Eds.), IDC, Studies in Computational Intelligence. Vol. 162, pp. 239–244. Springer, 2008.
Günther, C.G., An identity-based key-exchange protocol, In: Quisquater, J. J., and Vandewalle, J. (Eds.), EUROCRYPT, Lecture Notes in Computer Science. Vol. 434, pp. 29–37. Berlin: Springer, 1990.
Guo, C., and Chang, C. C., Chaotic maps-based password authenticated key agreement using smart cards. Commun. Nonlinear Sci. Numer. Simul. 18(6):1433–1440, 2013.
Hao, X., Wang, J., Yang, Q., Yan, X., and Li, P., A chaotic map-based authentication scheme for telecare medicine information systems. J. Med. Syst. 37(2):1–7, 2013.
He, D., Chen, J., and Zhang, R., A more secure authentication scheme for telecare medicine information systems. J. Med. Syst. 36(3):1989–1995, 2012.
He, D., and Wu, S., Security flaws in a smart card based authentication scheme for multi-server environment. Wirel. Pers. Commun. 70(1):323–329, 2013.
Hsu, C. L., Security of Chien et al.’s remote user authentication scheme using smart cards. Comput. Stand. Interfaces 26(3):167–169, 2004.
Just, M., and Vaudenay, S., Authenticated multi-party key agreement. In: Kim, K., and Matsumoto, T. (Eds.), ASIACRYPT, Lecture Notes in Computer Science. Vol. 1163, pp. 36–49. Springer, 1996.
Kaliski, B. S. Jr., An unknown key-share attack on the MQV key agreement protocol. ACM Trans. Inf. Syst. Secur 4(3):275–288, 2001.
Kocher, P. C., Jaffe, J., and Jun, B., Differential power analysis. In: Wiener, M. J. (Ed.) , CRYPTO, Lecture Notes in Computer Science, Vol. 1666, pp. 388–397. Springer, 1999.
Krawczyk, H., HMQV: A high-performance secure Diffie-Hellman protocol. In: Shoup, V. (Ed.) ,CRYPTO, Lecture Notes in Computer Science, Vol. 3621, pp. 546–566. Springer, 2005.
Lee, T.F., and Liu, C.M., A secure smart-card based authentication and key agreement scheme for telecare medicine information systems. J. Med. Syst. 37(3):1–8, 2013.
Lu, R., and Cao, Z., Simple three-party key exchange protocol. Comput. Secur. 26(1):94–97, 2007.
Menezes, A., van Oorschot, P.C., and Vanstone, S.A., Handbook of Applied Cryptography. Boca Raton, Florida: CRC Press, 1996.
Messerges, T.S., Dabbish, E.A., and Sloan, R.H., Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 51(5):541–552, 2002.
Nam, J., Kim, S., Park, S., and Won, D., Security analysis of a nonce-based user authentication scheme using smart cards. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. E90-A(1):299–302, 2007.
Nam, J., Paik, J., Kang, H.K., Kim, U.M., and Won, D., An off-line dictionary attack on a simple three-party key exchange protocol. IEEE Commun. Lett. 13(3):205–207, 2009.
Phan, R.C.W., Yau, W.C., Goi, B.M., Cryptanalysis of simple three-party key exchange protocol (S-3PAKE). Inf. Sci. 178(13):2849–2856, 2008.
Stern, J., Why provable security matters? In: Biham, E. (Ed.) , EUROCRYPT, Lecture Notes in Computer Science. Vol. 2656, pp. 449–461. Springer, 2003.
Wang, D., and Ma, C.G. Cryptanalysis of a remote user authentication scheme for mobile client server environment based on ECC. Inf. Fusion. 2013. doi:10.1016/j.inffus.2012.12.002
Wei, J., Hu, X., and Liu, W., An improved authentication scheme for telecare medicine information systems. J. Med. Syst. 36(6):3597–3604, 2012.
Wu, Z.Y., Lee, Y.C., Lai, F., Lee, H.C., and Chung, Y., A secure authentication scheme for telecare medicine information systems. J. Med. Syst. 36(3):1529–1535, 2012.
Xu, J., Zhu, W.T., and Feng, D.G., An improved smart card based password authentication scheme with provable security. Comput. Stand. Interfaces 31(4):723–728, 2009.
Yau, W.C., Phan, R.C.W., Goi, B.M., and Heng, S.H., Cryptanalysis of a provably secure cross-realm client-to-client password-authenticated key agreement protocol of CANS ’09. In: Lin, D., Tsudik, G., Wang, X. (Eds.) , CANS, Lecture Notes in Computer Science. Vol. 7092, pp. 172–184. Springer, 2011.
Zhang, L., Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos, Solitons Fractals 37(3):669–674, 2008.
Zhu, Z., An effcient authentication scheme for telecare medicine information systems. J. Med. Syst. 36(6):3833–3838, 2012.
Author information
Authors and Affiliations
Corresponding author
Additional information
Conflict of Interest
The authors declare that they have no conflict of interest.
Rights and permissions
About this article
Cite this article
Yau, WC., Phan, R.CW. Security Analysis of a Chaotic Map-based Authentication Scheme for Telecare Medicine Information Systems. J Med Syst 37, 9993 (2013). https://doi.org/10.1007/s10916-013-9993-9
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-013-9993-9