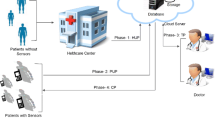
Abstract
The Telecare Medical Information System (TMIS) provides a set of different medical services to the patient and medical practitioner. The patients and medical practitioners can easily connect to the services remotely from their own premises. There are several studies carried out to enhance and authenticate smartcard-based remote user authentication protocols for TMIS system. In this article, we propose a set of enhanced and authentic Three Factor (3FA) remote user authentication protocols utilizing a smartphone capability over a dynamic Cloud Computing (CC) environment. A user can access the TMIS services presented in the form of CC services using his smart device e.g. smartphone. Our framework transforms a smartphone to act as a unique and only identity required to access the TMIS system remotely. Methods, Protocols and Authentication techniques are proposed followed by security analysis and a performance analysis with the two recent authentication protocols proposed for the healthcare TMIS system.







Similar content being viewed by others
References
Song, M., Kim, S., and Lee, S., Smart card, USPTO, Pat. No: 6050494, April 18, 2000.
Elberg, P., Electronic patient records and innovation in health care services. J. Med. Syst. 64:201–205, 2001.
Leiner, F., Gaus, W., Haux, R., and Knaup, P., Medical data management-a practical guide. Health Inf. Springer, New York 16:204, 2003.
Xiao, C., and Yu. A., Medical Smart Card System for Patient, Science, Technology, and Energy Policy. White Paper Competition, Bears Breaking Boundaries, 2009.
Huang, X., Xiang, Y., Chonka, A., Zhou, J., and Deng, R., A generic framework for three-factor authentication: Preserving security and privacy in distributed systems. Parallel Distrib. Syst. IEEE 22(08):1390–1397, 2011.
Slawomir, G., and Peter, M., Sharing cloud services: User authentication for social enhancement of home networking. Trans. Consum. Electron. IEEE 57:1424–1432, 2011.
Jucheng, Y., Naixure, X., Athanasios, V., Zhijun, F., Dongsun, P., Xianghua, X., Sook, Y., Shanjuan, X., and Yong, Y., A fingerprint recognition scheme based on assembling invariant moments for cloud computing communications. Syst. IEEE 5:574–583, 2011.
Dirk, B., Richard, C., Orl, E., Markus, J., Steve, K., Scott, M., Jesus, M., and Paul, O., The future of authentication. Secur. Priv. IEEE 10:22–27, 2012.
Cong, W., Kui, R., Wenjin, L., and Jin, L., Towards publicly auditable secure cloud data storage services. Networks IEEE 24:19–24, 2010.
Fagen, L., and Khan, M. K., A biometric identity based signcryption scheme. Futur. Gener. Comput. Syst., Elsevier Science, 28:306–310, 2012.
Jun, E., Khan, M. K., and Young, K., New robust protocols for remote user authentication and password change. Innov. Comput. Inf. Control (IJICIC) 7:5583–5603, 2011.
Khan, M. K., Alghathbar, K., and Jiashu, Z., Secure and tokenless privacy-protecting chaotic revocable biometrics authentication scheme. Telecommun. Syst., Springer-Verlag, 47:227–234, 2011.
Sayim, M., and Khan, M. K., Authentication fingerprint statistically. Imaging Sci. (UK) 60:165–171, 2012.
Sayim, M., Imran, M., and Khan, M. K., Fingerprint classification using PCA, LDA, L-LDA and BPN. Information 14:3313–3324, 2011.
Rhee, M. Y., Message Authentication Code, and Data Expansion Function, in Mobile Communication Systems and Security. John Wiley & Sons, Ltd, Chichester, UK. doi:10.1002/9780470823392.ch10.
Siddiqui, Z., Abdullah, A., Khan, M. K., Qualified Analysis B/w ESB(s) using Analytical Hierarchy Process (AHP) Method. Second International Conference on Intelligent Systems, Modelling and Simulation (ISMS’11), Kuala Lumpur Malaysia, ISBN 978-1-4244-9809-3, 100–104:2011.
Ghamdi, A., Siddiqui, Z., and Quadri, S., A Common Information Exchange Model for Multiple C4I Architectures. 12th International Conference on Computer Modelling and Simulation (UKSIM’10), UK, ISBN 978-1-4244-6614-6, 538–542, 2010.
Ghamdi, A., Siddiqui, Z., Common Information Framework b/w/Defense Architectures, A Wen Semantics Approach. 16th Internationa Conference on Distributed Multimedia Systems, USA, ISSN 2326-3261, 14–16, 2010.
Siddiqui, Z., Abdullah, A., Khan, M. K., and Alghathbar, K., Analysis of enterprise service buses on information security, interoperability and high-availability using Analytical Hierarchy Process (AHP). Phys. Sci. 6:35–42, 2011.
Siddiqui, Z., Abdullah, A., and Khan, M. K., Qualified Analysis b/w ESB(s) using Analytical Hierarchy Process (AHP) Method. International Conference on Intelligent Systems, Modelling and Simulation (ISMS’11), Malaysia, ISBN 978-1-4244-9809-3, 100–104, 2011.
Siddiqui, Z., Abdullah, A., Khan, M. K., and Ghamdi, A., Node Level Information Security in Common Information Exchange Model (CIEM). Science International, ISSN 1013-5316, 21:221–230, 2010.
Dunlop, L., Electronic health records: Interoperability challenges and patient’s right for privacy. Comput. Technol. Shidler J. 3:34–49, 2007.
Khan, M. K., and Kumari, S., An authentication scheme for secure access to healthcare services. J. Med. Syst. 37, 2012.
Kumari, S., and Khan, M. K., Cryptanalysis and improvement of a robust smart-card-based remote user authentication scheme. doi:10.1002/dac.2590, 2013.
Khan, M. K., and Zhang, J., Multimodal face and fingerprint biometrics authentication on space-limited tokens. Neurocomputing 71:3026–3031, 2008.
Dilmaghani, R., Ghavami, M., and Bobarshad. H., A new paradigm for Telehealth implementation. International On Engineering Medicine and Biology Society, IEEE, ISBN 978-1-4244-4123-5, 3915–3918, 2010.
Federal Financial Institutions Examination Council (FFIEC), http://www.ffiec.gov, Last Visit: 09 October 2013.
Federal Financial Institutions Examination Council (FFIEC), “Authentication of Internet Banking Environment”, http://www.ffiec.gov, pp. 2-4, August 2001, Last Visit: 09 October 2013.
Hung, S., Yao, C., and Yue, L., oPass: A user authentication protocol resistant to password stealing and password reuse attacks. Trans. Inf. Forensic Secur. IEEE 7:651–663, 2012.
Gagnon, S., Nabelsi, V., Passerni, K., and Cakici, K., The next web apps architecture: Challenges for SaaS vendors. IT Prof. IEEE 13:44–50, 2011.
Wei, J., Hu, X., and Liu, W., An improved authentication scheme for telecare medicine information systems. J. Med. Syst. 36:3597–3604, 2012.
Zhu, Z., An efficient authentication scheme for telecare medicine information systems. J. Med. Syst. 36:3833–3838, 2012.
Chen, M., Lo, W., and Yeh, K., An efficient and secure dynamic ID-based authentication scheme for telecare medical in- formation systems. Med. Syst. Springer, 36:3907–3915, 2012.
Qi, J., Ma, J., Ma, Z., and Li, G., A privacy enhanced authentication scheme for Telecare medical information system. Med. Syst. 37:9886–9894, 2013.
Khan, M. K., Jiashu, Z., and Xiaomin, W., Chaotic Hash-Based Fingerprint Biometric Remote User Authentication Scheme on Mobile Devices Vol. 35. Elsevier Science, UK, pp. 519–524, 2008.
Park, H., Hong, J., Park, J., Zhan, J., and Lee, D., Combined authentication-based multilevel access control in mobile application for DailyLifeService. Mob. Comput. IEEE 09:824–837, 2010.
Fuglerud, K., and Dale, O., Secure and inclusive authentication with a talking mobile OTP client. Secur. Priv. IEEE 9:27–34, 2011.
Hamdy, M., Alghathbar, K., and Khan, M. K., OTP-Based Two-Factor Authentication Using Mobile Phones. Eigth International Conference on Information Technology: New Generations (ITNG’11), IEEE, ISBN 978-0-7695-4367-3, 327–331, 2011.
Saxena, N., Jan, E., Kari, K., and Asokan, N., Scure device pairing based on a visual channel: Design and usability study. Inf. Forensic Secur. IEEE 06:28–38, 2011.
Kelin, E., GPA Location Authentication Method for Mobile Voting. USPTO, Pub. No: US 2011/0053559 A1, March 03, 2011.
Kimberly, D., and Parker, Money Transfer Smart Phone Methods and Systems. USPTO, Pub. No: US 2011/0251941 A1, October 13, 2011.
Haller, N., The S/KEY One-Time Password System. ISOC Symposium on Network and Distributed System Security, San Diego, CA, 151–157, 1994.
Hamdy, E., Khan, M. K., Alghathbar, K., Kim, T., and Hassan, E., Mobile one-time passwords: Two-factor authentication using mobile phones. Secur. Commun. Netw., John Wiley & Sons, 5:508–516, 2011.
Khan, M. K., Kumari, S., An efficient and secure dynamic id-based authentication scheme for Telecare medical information systems. doi:10.1002/sec.791, 2013.
Khan, M. K., and Kumari, S., Cryptanalysis and improvement of an efficient and secure dynamic ID-based authentication scheme for Telecare medical information systems. J. Med. Syst. 37, 2013.
Kocher, P., Jaffe, J., and Jun, B., Differential Power Analysis. Proceedings of Advances in Cryptology. Santa Barbara, CA, U.S.A., 388–397, 1999.
Messerges, T., Dabbish, E., and Sloan, R., Examining smart-card security under the threat of power analysis attacks. Comp. IEEE 51(5):541–552, 2002.
Acknowledgments
The authors acknowledge the support provided by Research Center (RC), College of Computer & Information Sciences King Saud University.
Conflict of interest
The authors declare that they have no conflict of interest.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Siddiqui, Z., Abdullah, A.H., Khan, M.K. et al. Smart Environment as a Service: Three Factor Cloud Based User Authentication for Telecare Medical Information System. J Med Syst 38, 9997 (2014). https://doi.org/10.1007/s10916-013-9997-5
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-013-9997-5