Abstract
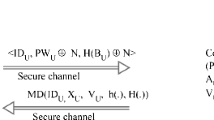
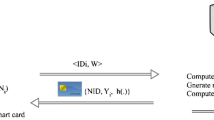
Telecare medical information system (TMIS) offers healthcare delivery services and patients can acquire their desired medical services conveniently through public networks. The protection of patients’ privacy and data confidentiality are significant. Very recently, Mishra et al. proposed a biometrics-based authentication scheme for telecare medical information system. Their scheme can protect user privacy and is believed to resist a range of network attacks. In this paper, we analyze Mishra et al.’s scheme and identify that their scheme is insecure to against known session key attack and impersonation attack. Thereby, we present a modified biometrics-based authentication scheme for TMIS to eliminate the aforementioned faults. Besides, we demonstrate the completeness of the proposed sche-me through BAN-logic. Compared to the related schemes, our protocol can provide stronger security and it is more practical.


Similar content being viewed by others
References
Das, M.L., Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 8(3):1086–1090, 2009.
Hwang, M.S., and Li, L.H., A new remote user authentication scheme using smart cards. IEEE Trans. Consum. Electron. 46(1):28–30, 2000.
Wen, F.T., Susilo, W., Yang, G.M., A robust smart card-based anonymous user authentication protocol for wireless communications. Security Comm. Networks, 2013. 10.1002/sec.816.
Guo, D.L., and Wen, F.T., Analysis and improvement of a robust smart card based-authentication scheme for multi-server architecture. Wireless Pers Commun. 78(1):475–490, 2014.
Li, X., Niu, J.W., Khan, M.K., Liao, J.G., An enhanced smart card based remote user password authentication scheme. J. Netw. Comput. Appl. 36(5):1365–1371, 2013.
Li, X., Niu, J.W., Khan, M.K., Liao, J.G., Zhao, X.K., Robust three-factor remote user authentication scheme with key agreement for multimedia systems, 2013. doi:10.1002/sec.961.
Li, X., Niu, J.W., Liu, Y.Z., Liao, J.G., Liang, W., Robust dynamic ID-based remote user authentication scheme using smart cards. Int. J. Ad Hoc Ubiquit. Comput. 17(4):254–264, 2014.
Wu, Z.Y., Lee, Y.C., Lai, F., Lee, H.C., Chung, Y., A secure authentication scheme for telecare medicine information systems. J. Med. Syst. 36(3):1529–1535, 2012.
He, D.B., Chen, J.H., Zhang, R., A more secure authentication scheme for telecare medicine information systems. J. Med. Syst. 36(3):1989–1995, 2012.
Wei, J., Hu, X., Liu, W., An improved authentication scheme for telecare medicine information systems. J. Med. Syst. 36(6):3597–3604, 2012.
Zhu, Z., An efficient authentication scheme for telecare medicine information systems. J. Med. Syst. 36(6):3833–3838, 2012.
Wen, F.T., and Guo, D.L., An improved anonymous authentication scheme for telecare medical information systems. J. Med. Syst., 2014. doi:10.1007/s10916-014-0026-0.
Li, X., Niu, J.W., Ma, J., Wang, W.D., Liu, C.L., Cryptanalysis and improvement of a biometrics-based remote user authentication scheme using smart cards. J. Netw. Comput. Appl. 34(1):73–79, 2011.
Das, A.K., and Goswami, A., An enhanced biometric authentication scheme for telecare medicine information systems with nonce using chaotic hash function, 2014. doi:10.1007/s10916-014-0027-z.
Jiang, Q., Ma, J.F., Lu, X., Tian, Y.L., Robust Chaotic Map-based authentication and key agreement scheme with strong anonymity for telecare medicine information systems, 2014. doi:10.1007/s10916-014-0012-6.
Tan, Z.W., An efficient biometrics-based authentication scheme for telecare medicine information systems. Przegl. Elektrotech. 89(5):200–204, 2013.
Yan, X., Li, W., Li, P., Wang, J., Hao, X., Gong, P., A secure biometrics-based authentication scheme for telecare medicine information systems. J. Med. Syst. 37(5):1–6, 2013.
Mishra, D., Mukhopadhyay, S., Chaturvedi, A., Kumari, S., and Khan, M., Cryptanalysis and improvement of Yan et al.’s Biometric-based authentication scheme for telecare medicine information systemes. J. Med. Syst., 2014. doi:10.1007/s10916-014-0024-2.
Tan, Z.W., A user anonymity preserving three-factor authentication scheme for telecare medicine information systems. J. Med. Syst., 2014. doi:10.1007/s10916-014-0016-2.
Arshad, H., and Nikooghadam, M., Three-factor anonymous authentication and key agreement scheme for telecare medicine information systems. J. Med. Syst., 2014. doi:10.1007/s10916-014-0136-8.
Maitra, T., and Giri, D., An efficient biometric and password-based remote user authentication using smart card for telecare medical information systems in multi-server environment. J. Med. Syst., 2014. doi:10.1007/s10916-014-0142-x.
Li, X.L.,Wen, Q.Y., Li, W.M., Zhang, H., and Jin, Z.P., Secure privacy-preserving biometric authentication scheme for telecare medicine information systems. J. Med. Syst., 2014. doi:10.1007/s10916-014-0139-5.
Li, X., Niu, J.W., Wang, Z.B., Chen, C.S., Applying biometrics to design three-factor remote user authentication scheme with key agreement. Secur. Commun. Netw. 7(10):1488–1497, 2014.
Das, A.K., and Goswami, A., An enhanced biometric authentication scheme for telecare medicine information systems with nonce using chaotic hash function. J. Med. Syst., 2014. doi:10.1007/s10916-014-0027-z.
Kocher, P., Jaffe, J., Jun, B., Differential power analysis, pp. 388–397. Santa Barbara: Proceedings of Advances in Cryptology, 1999.
Messerges, T.S., Dabbish, E.A., Sloan, E.A., Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 51(5):541–552, 2002.
Juels, A., and Wattenberg, M., A fuzzy commitment scheme. CCS ’99 Proceedings of the 6th ACM conference on Computer and communications security, pp. 28–36. New York: ACM, 1999.
Burrows, M., Abadi, M., Needham, R., A logic of authentication. ACM Trans. Comput. Syst. 8(1):18–36, 1990.
Chang, Y.F., Yu, S.H., Shiao, D.R., An uniqueness-andanonymity-preserving remote user authentication scheme for connected health care. J. Med. Syst. 37:9902, 2013.
Acknowledgments
The authors are grateful to the editor and anonymous reviewers for their valuable suggestions, which improved the paper. This work is supported by NSFC (Grant Nos. 61300181, 61202434), the Fundamental Research Funds for the Central Universities (Grant No. 2015RC23).
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is part of the Topical Collection on Systems-Level Quality Improvement
Rights and permissions
About this article
Cite this article
Guo, D., Wen, Q., Li, W. et al. An Improved Biometrics-Based Authentication Scheme for Telecare Medical Information Systems. J Med Syst 39, 20 (2015). https://doi.org/10.1007/s10916-015-0194-6
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-015-0194-6