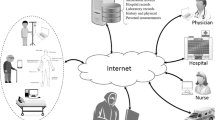
Abstract
Recently, Giri et al.’s proposed a RSA cryptosystem based remote user authentication scheme for telecare medical information system and claimed that the protocol is secure against all the relevant security attacks. However, we have scrutinized the Giri et al.’s protocol and pointed out that the protocol is not secure against off-line password guessing attack, privileged insider attack and also suffers from anonymity problem. Moreover, the extension of password guessing attack leads to more security weaknesses. Therefore, this protocol needs improvement in terms of security before implementing in real-life application. To fix the mentioned security pitfalls, this paper proposes an improved scheme over Giri et al.’s scheme, which preserves user anonymity property. We have then simulated the proposed protocol using widely-accepted AVISPA tool which ensures that the protocol is SAFE under OFMC and CL-AtSe models, that means the same protocol is secure against active and passive attacks including replay and man-in-the-middle attacks. The informal cryptanalysis has been also presented, which confirmed that the proposed protocol provides well security protection on the relevant security attacks. The performance analysis section compares the proposed protocol with other existing protocols in terms of security and it has been observed that the protocol provides more security and achieves additional functionalities such as user anonymity and session key verification.







Similar content being viewed by others
References
Amin, R., Cryptanalysis and an efficient secure id-based remote user authentication using smart card. Int. J. Comput. Appl. 75(13):43–48, 2013.
Amin, R., and Biswas, G. P.: Anonymity preserving secure hash function based authentication scheme for consumer usb mass storage device.. In: 3rd International Conference on Computer, Communication, Control and Information Technology (C3IT), 2015, pp. 1–6. doi:10.1109/C3IT.2015.7060190 (2015)
Amin, R., and Biswas, G.P., Design and analysis of bilinear pairing based mutual authentication and key agreement protocol usable in multi-server environment. Wirel. Pers. Commun., 1–24, 2015. doi:10.1007/s11277-015-2616-7.
Amin, R., and Biswas, G. P., A novel user authentication and key agreement protocol for accessing multi-medical server usable in tmis. J. Med. Syst. 39(3):33, 2015. doi:10.1007/s10916-015-0217-3.
Amin, R., and Biswas, G. P.: Remote access control mechanism using rabin public key cryptosystem.. In: Information Systems Design and Intelligent Applications, Advances in Intelligent Systems and Computing. Vol. 339, pp. 525–533. India: Springer. doi:10.1007/978-81-322-2250-7_52 (2015)
Amin, R., Maitra, T., Rana, S. P., An improvement of Wang et. al.’s remote user authentication scheme against smart card security breach. Int. J. Comput. Appl. 75(13):37–42, 2013.
Armando, A., Basin, D., Boichut, Y., Chevalier, Y., Compagna, L., Cuellar, J., Drielsma, P., Hem, P., Kouchnarenko, O., Mantovani, J., Mdersheim, S., von Oheimb, D., Rusinowitch, M., Santiago, J., Turuani, M., Vigan, L., Vigneron, L.: The avispa tool for the automated validation of internet security protocols and applications.. In: Computer Aided Verification, Lecture notes in computer science. Vol. 3576, pp. 281–285 (2005)
Arshad, H., and Nikooghadam, M., Three-factor anonymous authentication and key agreement scheme for telecare medicine information systems. J. Med. Syst. 38(12):136, 2014. doi:10.1007/s10916-014-0136-8.
Chang, Y. F., Yu, S. H., Shiao, D. R., A uniqueness-and-anonymity-preserving remote user authentication scheme for connected health care. J. Med. Syst. 37(2):9902, 2013. doi:10.1007/s10916-012-9902-7.
Dolev, D., and Yao, A. C., On the security of public key protocols. IEEE Trans. Inf. Theory 29(2):198–208, 1983.
Giri, D., Maitra, T., Amin, R., Srivastava, P., An efficient and robust rsa-based remote user authentication for telecare medical information systems. J. Med. Syst. 39(1):145, 2014. doi:10.1007/s10916-014-0145-7.
He, D., Jianhua, C., Rui, Z., A more secure authentication scheme for telecare medicine information systems. J. Med. Syst. 36(3):1989–1995, 2012.
He, D., Kumar, N., Chilamkurti, N., Lee, J. H., Lightweight ecc based rfid authentication integrated with an id verifier transfer protocol. J. Med. Syst. 38(10):116, 2014. doi:10.1007/s10916-014-0116-z doi:10.1007/s10916-014-0116-z.
Islam, S. H., Design and analysis of a three party password-based authenticated key exchange protocol using extended chaotic maps. Inf. Sci. 312(0):104–130, 2015. doi:10.1016/j.ins.2015.03.050.
Islam, S. H., and Biswas, G. P., A more efficient and secure id-based remote mutual authentication with key agreement scheme for mobile devices on elliptic curve cryptosystem. J. Syst. Softw. 84(11):1892–1898, 2011.
Islam, S. H., and Biswas, G. P., A provably secure identity-based strong designated verifier proxy signature scheme from bilinear pairings. Journal of King Saud University - Computer and Information Sciences 26(1):55–67, 2014. doi:10.1016/j.jksuci.2013.03.004.
Islam, S. H., and Khan, M. K., Cryptanalysis and improvement of authentication and key agreement protocols for telecare medicine information systems. J. Med. Syst. 38(10):135, 2014. doi:10.1007/s10916-014-0135-9.
Khan, M. K., and Kumari, S., An authentication scheme for secure access to healthcare services. J. Med. Syst. 37(4):9954, 2013. doi:10.1007/s10916-013-9954-3.
Khan, M. K., and Kumari, S., Cryptanalysis and improvement of an efficient and secure dynamic id-based authentication scheme for telecare medical information systems. Security and Communication Networks 7(2):399–408, 2014 . doi:10.1002/sec.791.
Kocher, P., Jaffe, J., Jun, B.: Differential power analysis. In: Advances in Cryptology CRYPTO 99, Lecture Notes in Computer Science. Vol. 1666, pp. 388–397 (1999)
Kumari, S., Gupta, M. K., Khan, M. K., Li, X., An improved timestamp-based password authentication scheme: Comments, cryptanalysis, and improvement. Security and Communication Networks 7:1921–1932, 2014. doi:10.1002/sec.906.
Kumari, S., and Khan, M. K., More secure smart card based remote user password authentication scheme with user anonymity. Security and Communication Networks 7:2039–2053, 2013. doi:10.1002/sec.916.
Kumari, S., and Khan, M. K., Cryptanalysis and improvement of ’a robust smart-card-based remote user password authentication scheme. Int. J. Commun. Syst. 27:3939–3955, 2014. doi:10.1002/dac.2590.
Kumari, S., Khan, M. K., Li, X., An improved remote user authentication scheme with key agreement. Comput. Electr. Eng. 40(6):1997–2012, 2014. doi:10.1016/j.compeleceng.2014.05.007.
Kumari, S., Khan, M. K., Li, X., Wu, F., Design of a user anonymous password authentication scheme without smart card. Int. J. Commun. Syst. 27(10):609–618, 2014 . doi:10.1002/dac.2853.
Lamport, L., Password authentication with insecure communication. Commun. ACM 24(11):770–772, 1981. doi:10.1145/358790.358797.
Lee, T. F., An efficient chaotic maps-based authentication and key agreement scheme using smartcards for telecare medicine information systems. J. Med. Syst. 37(6):9985, 2013. doi:10.1007/s10916-013-9985-9.
Lee, T. F., Chang, I. P., Lin, T. H., Wang, C. C., A secure and efficient password- based user authentication scheme using smart cards for the integrated epr information system. J. Med. Syst. 37(3):1–7, 2013.
Li, X., Niu, J. W., Ma, J., Wang, W. D., Liu, C. L., Cryptanalysis and improvement of a biometrics-based remote user authentication scheme using smart cards. J. Netw. Comput. Appl. 34(1):73–79, 2011.
Lu, Y., Li, L., Peng, H., Yang, Y., An enhanced biometric-based authentication scheme for telecare medicine information systems using elliptic curve cryptosystem. J. Med. Syst. 39(3):32, 2015. doi:10.1007/s10916-015-0221-7.
Messerges, T. S., Dabbish, E. A., Sloan, R. H., Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 51(5):541–552, 2002.
Mishra, D., On the security flaws in id-based password authentication schemes for telecare medical information systems. J. Med. Syst. 39(1):154, 2014. doi:10.1007/s10916-014-0154-6.
Mishra, D., Understanding security failures of two authentication and key agreement schemes for telecare medicine information systems. J. Med. Syst. 39(3):19, 2015. doi:10.1007/s10916-015-0193-7.
Mishra, D., Mukhopadhyay, S., Chaturvedi, A., Kumari, S., Khan, M. K., Cryptanalysis and improvement of Yan et al.’s biometric-based authentication scheme for telecare medicine information systems. J. Med. Syst. 38(6):24, 2014. doi:10.1007/s10916-014-0024-2.
Mishra, D., Mukhopadhyay, S., Kumari, S., Khan, M., Chaturvedi, A., Security enhancement of a biometric based authentication scheme for telecare medicine information systems with nonce. J. Med. Syst. 38(5):41, 2014. doi:10.1007/s10916-014-0041-1.
Mishra, D., Srinivas, J., Mukhopadhyay, S., A secure and efficient chaotic map-based authenticated key agreement scheme for telecare medicine information systems. J. Med. Syst. 38(10): 120, 2014. doi:10.1007/s10916-014-0120-3.
Rivest, R. L., Shamir, A., Adleman, L., A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 21(2):120–126, 1978. doi:10.1145/359340.359342.
Shor, P. W., Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM J. Comput. 26(5):1484–1509, 1997. doi:10.1137/S0097539795293172.
Tool, A. W. http://www.avispa-project.org/web-interface/ February (2015)
Wei, J., Hu, X., Liu, W., An improved authentication scheme for telecare medicine information systems. J. Med. Syst. 36(6):3597–3604, 2012.
Wu, Z. Y., Lee, Y. C., Lai, F., Lee, H. C., Chung, Y., A secure authentication scheme for telecare medicine information systems. J. Med. Syst. 36(3):1529–1535, 2012.
Xie, Q., Liu, W., Wang, S., Han, L., Hu, B., Wu, T., Improvement of a uniqueness-and-anonymity-preserving user authentication scheme for connected health care. J. Med. Syst. 38(9):91, 2014. doi:10.1007/s10916-014-0091-4.
Xu, L., and Wu, F., Cryptanalysis and improvement of a user authentication scheme preserving uniqueness and anonymity for connected health care. J. Med. Syst. 39(2):10, 2015. doi:10.1007/s10916-014-0179-x.
Xu, X., Zhu, P., Wen, Q., Jin, Z., Zhang, H., He, L., A secure and efficient authentication and key agreement scheme based on ecc for telecare medicine information systems. J. Med. Syst. 38(1):9994, 2013. doi:10.1007/s10916-013-9994-8.
Zhang, L., and Zhu, S., Robust ecc-based authenticated key agreement scheme with privacy protection for telecare medicine information systems. J. Med. Syst. 39(5):49, 2015. doi:10.1007/s10916-015-0233-3.
Zhu, Z., An efficient authentication scheme for telecare medicine information systems. J. Med. Syst. 36(6): 3833–3838, 2012.
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is part of the Topical Collection on Transactional Processing Systems
Rights and permissions
About this article
Cite this article
Amin, R., Biswas, G.P. An Improved RSA Based User Authentication and Session Key Agreement Protocol Usable in TMIS. J Med Syst 39, 79 (2015). https://doi.org/10.1007/s10916-015-0262-y
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-015-0262-y