Abstract
Due to the development of information technologies and network technologies, healthcare systems have been employed in many countries. As an important part of healthcare systems, the wireless body area network (WBAN) could bring convenience to both patients and physicians because it could help physicians to monitor patients’ physiological values remotely. It is essential to ensure secure communication in WBANs because patients’ physiological values are very sensitive. Recently, Liu et al. proposed an efficient authentication scheme for WBANs. Unfortunately, Zhao pointed out that their scheme suffered from the stolen verifier-table attack. To improve security and efficiency, Zhao proposed an anonymous authentication scheme for WBANs. However, Zhao’s scheme cannot provide real anonymity because the users’ pseudo identities are constant value and the attack could tract the users. In this paper, we propose a new anonymous authentication scheme for WBANs. Security analysis shows that the proposed scheme could overcome weaknesses in previous scheme. We also use the BAN logic to demonstrate the security of the proposed scheme.
Similar content being viewed by others
Introduction
With the wide use of information technologies and network technologies, the filed of medical systems is undergoing major revolution. As an important part of medical systems, the wireless body area network (WBAN) attracts extensive attention from both academics and industry. A WBAN consists of many clothes or implanting sensors, which are designed to collect patient’s physiological values, such as blood pressure, heartbeat rate, blood oxygen level and so on. Then physicians could access those physiological values through the Internet and give suitable treatment remotely [1, 2]. Thus, the WBAN not only could bring convenience to both patients and physicians, but also could improve the quality of treatment. To expand the applications of WBANs, the Institute of Electrical and Electronics Engineers (IEEE) designed IEEE 802.15.6 standard for communication in WBANs [3].
The physiological values transmitted in WBANs are the basis of medical diagnosis. Any destroy of physiological values may bring fatal harm to patients. Therefore, how to ensure secure communications in WBANs becomes an issue that needs to be addressed urgently. Authentication scheme is one of the most important cryptographic primitive because it could achieve mutual authentication and generate session key for encrypting data.
Related works
Many authentication schemes using traditional public key cryptosystem (TPKC) [4, 5] have been proposed for other application environments. Those TPKC-based authentication schemes are not suitable for WBANs because the computing power of medical sensors in WBANs is very limited and complicated modular exponentiation operation is needed in TPKC-based authentication schemes. To improve efficiency, many authentication schemes using elliptic curve cryptography (ECC) were proposed [6–10]. The ECC was introduced by Miller and Koblitz separately [11, 12]. Compared with the TPKC, the ECC could achieve the same security with much shorter key length. For example, the ECC with 160 bits key and the TPKC with 1024 bits key have the same security level. However, those schemes [6–10] are based on the public key infrastructure (PKI). In the PKI, the user’s identity and public key are banded through a certificate generated by the certificate authority (CA). However, the management of those certificates becomes more and more difficult with the increase of the user’s number.
To solve the certificate management problem, Shamir [13] introduced the concept of the identity based public key cryptosystem (ID-based PKC). In the ID-based PKC, the user’s identity, such as name, email address and telephone number, is his public key. Therefore, there is no need to maintain certificates. Based on the ID-based PKC, many identity-based authentication schemes have been proposed [14–20]. However, those schemes are not suitable for WBANs because most of them cannot provide user anonymity and they are designed for client–server environment. To satisfy security requirement in WBANs, Liu et al. [21] proposed two identity based authentication schemes using a certificateless signature scheme. However, Zhao [22] pointed out that Liu et al.’s schemes cannot withstand the stolen verifier-table attack. Besides, Zhao [22] also pointed out that Liu et al.’s first scheme cannot provide user anonymity. To improve security and efficiency, Zhao proposed an anonymous authentication scheme for WBANs. However, Zhao’s scheme cannot provide real anonymity because the users’ pseudo identities are constant value and the attack could tract the users. With increasing of security requirements, it is urgently to design anonymous authentication scheme to achieve real anonymity.
Our contributions
To solve problems in previous schemes, in this paper, we proposed a new anonymous authentication scheme for WBANs. The main contributions of the paper are described as follows.
-
First, we propose a new anonymous authentication scheme for WBANs using the bilinear pairing.
-
Section, we give security analysis of the proposed scheme to show it could achieve real anonymity and overcome weaknesses in previous schemes. We also use the BAN logic [23] to demonstrate the security of the proposed scheme.
-
At last, Performance analysis of related schemes is also demonstated to show the proposed scheme is practical for applications.
The organization of the paper
The organization of the paper is sketched as follows. Section “The proposed authentication scheme” presents our authentication scheme for WBANs. Section “Security analysis” gives the security analysis of the proposed scheme. Section “Performance analysis” analyzes the performance of the proposed scheme. At last, some conclusions are proposed in Section “Conclusion”.
The proposed authentication scheme
In this section, we propose an anonymous authentication scheme for WBANs. For convenience, some notations used in this paper are defined as follows.
-
p, q: two large prime numbers;
-
G 1: an additive group with order q;
-
G 2: a multiplicative group with order q;
-
e: a bilinear pairing, where e : G 1 × G 1 → G 2;
-
P: a generator of the group G 1;
-
h: a secure hash function, where h : {0, 1}* → Z q ;
-
H: a secure hash function, where H : {0, 1}* → G 1;
-
C: a WBAN client;
-
ID C : the identity of C;
-
AP: an application provider;
-
ID AP : the identity of AP;
-
NM: the network manager;
-
s NM : NM’s private key;
-
Q NM : NM’s public key, where Q NM = s NM ⋅ P;
-
s AP : AP’s private key;
-
Q AP : AP’s public key, where Q AP = s AP ⋅ P;
-
E k (⋅)/D k (⋅): a symmetric encryption/decryption algorithm with key k;
There are three participants in the execution of the authentication scheme for WBANs: a client C, the network manager (NM) and a application provider AP. The NM is a trusted third party, which is responsible for generating private keys for each C and AP. The AP is a clinic or a physician, which is responsible for providing medical services in the WBANs. The C is a patient, who could enjoy medical services using mobile devices such as PDA or mobile phone. There are three phases in the proposed authentication scheme for WBANs: the initialization phase, the registration phase and the authentication phase.
Initialization phase
In this phase, the network manager NM generates its private key, public key and the system parameters.
-
1).
NM generates a large prime number q, an additive group G 1 with the order q, a multiplicative group G 2 with the same order q, a generator P of the group G 1 and a bilinear pairing e : G 1 × G 1 → G 2.
-
2).
NM chooses two secure hash functions h and H, where h : {0, 1}* → Z q and H : {0, 1}* → G 1.
-
3).
NM generates a random number s NM ∈ Z q as its private key and computes its public key Q NM = s NM ⋅ P.
-
4).
NM publishes the systems parameters parmas = {q, G 1, G 2, e, P, h, H, Q NM }.
Registration phase
In this phase, the network manager NM generates the private key for each client C and application provider AP.
-
1).
The object O sends its identity ID O to NM, where O is C or AP.
-
2).
Upon receiving ID O , NM computes the private key S O = s NM ⋅ Q O , where Q O = H(ID O ). At last, NM sends the private key S O to O through a secure channel.
-
3).
Upon receiving the private key, O stores it secretly.
Authentication phase
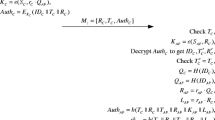
In this phase, the client C and the application provider AP authenticate each other and generate a session key to encrypt physiological values. As shown in Fig. 1, the following steps are executed between C and AP.
-
1).
C generates a random number r C ∈ Z q , and computes Q AP = H(ID AP ), Q C = H(ID C ), R C = r C ⋅ Q C , K C = e(S C , r C ⋅ Q AP ) and \( Aut{h}_C={E}_{K_C}\left(I{D}_C\left|\right|{T}_C\left|\right|{R}_C\right) \), where T C is the current timestamp. At last, C sends the message M 1 = {R C , T C , Auth C } to AP.
-
2).
Upon receiving M 1 = {R C , T C , Auth C }, AP checks the freshness of T C . If it is not fresh, AP rejects the request. AP computes K AP = e(S AP , R C ) and gets (ID C ||T C ||R C ) by decrypting Auth C . AP checks if T C and the decrypted one are equal. If they are not equal, AP rejects the request. AP generates a random number r AP ∈ Z q , and computes Q C = H(ID C ), Q AP = H(ID AP ), R AP = r AP ⋅ Q C , L AP = r AP ⋅ R C , Auth AP = h(T C ||R C ||T AP ||R AP ||K AP ||L AP ) and the session key sk AP = h(T C ||R C ||T AP ||R AP ||L AP ), where T AP is the current timestamp. At last, AP sends the message M 2 = {R AP , T AP , Auth AP } to C.
-
3).
Upon receiving M 2 = {R AP , T AP , Auth AP }, C checks the freshness of T AP . If it is not fresh, C rejects the request. C computes L C = r C ⋅ R AP and checks if the equations Auth AP = h(T C ||R C ||T AP ||R AP ||K C ||L C ) holds. If it does not hold, C rejects the response; otherwise, C computes the session key sk C = h(T C ||R C ||T AP ||R C ||L C ).
From the description of the scheme, we have S C = s NM ⋅ Q C , R C = r C ⋅ Q C , K C = e(S C , r C ⋅ Q AP ), L C = r C ⋅ R AP , S AP = s NM ⋅ Q AP , R AP = r AP ⋅ Q C , L AP = r AP ⋅ R C and K AP = e(S AP , R C ). Then, we could get
and
Therefore, the correctness of the proposed authentication scheme for WBANs is proposed.
Security analysis
In this section, we analyze the security of the proposed authentication scheme for WBANs. First, we use the BAN logic [23] to demonstrate the validity of the proposed authentication scheme for WBANs. Then, we show the proposed scheme could withstand various attacks and provide some important attributes.
Authentication proof based on BAN logic
The BAN logic [23] has been widely used to analyze the security of authentication schemes and key agreement schemes. In this sub section, we use it to analyze the proposed authentication. Some notations and logical postulates used in our analysis are defined as follows.
-
P, Q: two principals;
-
X, Y: two statements;
-
P|≡X: P believes X;
-
# (X): X is fresh;
-
P ⇒ X: P has jurisdiction over X;
-
P ⊲ X: P says X;
-
P| ~ X: P once said X;
-
(X, Y): X or Y is one part of (X, Y);
-
(X) K : X is hash with the key K;
-
\( P\overset{K}{\leftrightarrow }Q \): the shared key K is used in the communication between P and Q;
-
sk: the session key;
-
\( \frac{P\Big|\equiv P\overset{K}{\leftrightarrow }Q,P\vartriangleleft {(X)}_K}{P\left|\equiv Q\right|\sim X} \): the message-meaning rule;
-
\( \frac{P\Big|\equiv \#(X)}{P\Big|\equiv \#\left(X,Y\right)} \): the freshness-conjuncatenation rule;
-
\( \frac{P\left|\equiv \#(X),P\right|\equiv Q\Big|\sim X}{P\left|\equiv Q\right|\equiv X} \): the nonce-verification rule;
-
\( \frac{P\left|\equiv Q\Rightarrow X,P\right|\equiv Q\Big|\equiv X}{P\Big|\equiv X} \): the jurisdiction rule;
The process of security analysis using the BAN logic consists of four steps: 1). Idealizing the proposed scheme; 2) Writing the assumptions; 3). Annotating the idealized scheme; 4). Discovering the beliefs. According to the security requirement of the authentication scheme for WBANs, the proposed scheme should satisfy the following goals:
-
Goal 1. \( C\Big|\equiv C\overset{sk}{\leftrightarrow }AP \)
-
Goal 2. \( C\left|\equiv AP\right|\equiv C\overset{sk}{\leftrightarrow }AP \)
-
Goal 3. \( AP\Big|\equiv C\overset{sk}{\leftrightarrow }AP \)
-
Goal 4. \( AP\left|\equiv C\right|\equiv C\overset{sk}{\leftrightarrow }AP \)
According to the description of the proposed scheme, it could be transformed to the idealized form.
According to the description of the proposed scheme, we could make the following assumptions about the initialization.
-
$$ \begin{array}{ll}{A}_1.\hfill & C\left|\equiv \#\left({T}_{AP}\right)\right.\hfill \end{array} $$
-
$$ \begin{array}{ll}{A}_2.\hfill & AP\left|\equiv \#\left({T}_C\right)\right.\hfill \end{array} $$
-
$$ \begin{array}{ll}{A}_3.\hfill & C\left|\equiv C\overset{K}{\leftrightarrow }AP\right.\hfill \end{array} $$
-
$$ \begin{array}{ll}{A}_4.\hfill & AP\left|\equiv C\overset{K}{\leftrightarrow }AP\right.\hfill \end{array} $$
-
$$ \begin{array}{ll}{A}_5.\hfill & C\left|\equiv AP\Rightarrow \left(C\overset{K}{\leftrightarrow }AP\right)\right.\hfill \end{array} $$
-
$$ \begin{array}{ll}{A}_6.\hfill & AP\left|\equiv C\Rightarrow \left(C\overset{K}{\leftrightarrow }AP\right)\right.\hfill \end{array} $$
Based on the BAN logic rules and the above assumptions, we analyze the proposed scheme’s idealized form as follows.
-
From Msg 1 of the idealized form, we have
$$ {S}_1:AP\vartriangleleft {\left({T}_C,{R}_C\right)}_K $$ -
From S 1, A 4 and the message-meaning rule, we have
$$ {S}_2:AP\left|\equiv C\right|\sim \left({T}_C,{R}_C\right) $$ -
From S 2, A 2 and the freshness conjuncatenation rule, we have
$$ {S}_3:AP\left|\equiv C\right|\equiv \left({T}_C,{R}_C\right) $$ -
From S 3, we have
$$ {S}_4:AP\left|\equiv C\right|\equiv \left({R}_C\right) $$ -
From L = r AP ⋅ R C and sk = h(T C ||R C ||T AP ||R AP ||L), we have
$$ \begin{array}{ll}{S}_5:AP\left|\equiv C\right|\equiv \left(C\overset{sk}{\leftrightarrow }AP\right)\hfill & \left( Goal\kern0.5em 4\right)\hfill \end{array} $$ -
From S 5, A 6 and the jurisdiction rule, we have
$$ \begin{array}{ll}{S}_6:AP\left|\equiv \left(C\overset{sk}{\leftrightarrow }AP\right)\right.\hfill & \left( Goal\ 3\right)\hfill \end{array} $$ -
From Msg 2 of the idealized form, we have
$$ {S}_7:C\vartriangleleft {\left({T}_C,{R}_C,{T}_{AP},{R}_{AP},C\overset{sk}{\leftrightarrow }AP\right)}_K $$ -
From S 7 and A 3, we have
$$ {S}_8:C\left|\equiv AP\right|\sim \left({T}_C,{R}_C,{T}_{AP},{R}_{AP},C\overset{sk}{\leftrightarrow }AP\right) $$ -
From S 8, A 1 and the freshness conjuncatenation rule, we have
$$ {S}_9:C\left|\equiv AP\right|\equiv \left({T}_C,{R}_C,{T}_{AP},{R}_{AP},C\overset{sk}{\leftrightarrow }AP\right) $$ -
From S 9, we have
$$ \begin{array}{ll}{S}_9:C\left|\equiv AP\right|\equiv \left(C\overset{sk}{\leftrightarrow }AP\right)\hfill & \left( Goal\ 2\right)\hfill \end{array} $$ -
From S 9, A 5 and the jurisdiction rule, we have
$$ \begin{array}{ll}{S}_{10}:C\left|\equiv \left(C\overset{sk}{\leftrightarrow }AP\right)\right.\hfill & \left( Goal\ 1\right)\hfill \end{array} $$
According to (Goal 1), (Goal 2), (Goal 3) and (Goal 4), we could confirm that the client and the application provider could generate a session key in the execution of the proposed scheme.
Other discussion
In this subsection, we show the proposed scheme can provide mutual authentication, client anonymity, perfect forward security and unlinkability [24–27]. We also demonstrate that the proposed scheme can withstand the impersonation attack, the man-in-the-middle attack, the relay attack, the modification attack, the stolen verifier table attack and the known-key attack [28–30]. For the security, the following theorems are proposed.
Theorem 1
The proposed authentication scheme for WBANs could provide mutual authentication.
Proof
From the description of the proposed scheme and the bilinear computational Diffie-Hellman problem, we know that only the one with the private key S C could generate R C = r C ⋅ Q C , K C = e(S C , r C ⋅ Q AP ) and Auth C = h(T C ||R C ||K C ). Then AP could authenticate C by checking the correctness of Auth C . Besides, only the one with the private key S AP could generate K AP = e(S AP , R C ) = K C , L AP = r AP ⋅ R C and Auth AP = h(T C ||R C ||T AP ||R AP ||K AP ||L AP ). Then C could authenticate AP by checking the correctness of Auth AP . Therefore, the proposed scheme could provide mutual authentication between C and AP.
Theorem 2
The proposed authentication scheme for WBANs could provide client anonymity.
Proof
According to the description of the proposed scheme, the client’s identity is hidden in the message M 1 = {R C , T C , Auth C }, where R C = r C ⋅ Q C , K C = e(S C , r C ⋅ Q AP ) and \( Aut{h}_C={E}_{K_C}\left(I{D}_C\left\Vert {T}_C\right\Vert {R}_C\right) \). Without the private key S AP , anyone cannot compute K AP = K C = e(S AP , R C ). Then he cannot get the client’s identity by decrypting Auth C . Therefore, the proposed scheme could provide client anonymity.
Theorem 3
The proposed authentication scheme for WBANs could provide perfect forward security.
Proof
Suppose the adversary could get the client and the application provider’s private keys. We also assume that the adversary could get M 1 = {R C , T C , Auth C } and M 2 = {R AP , T AP , Auth AP } sent between the client and the application provider, where R C = r C ⋅ Q C , K C = e(S C , r C ⋅ Q AP ), \( Aut{h}_C={E}_{K_C}\left(I{D}_C\left|\right|{T}_C\left|\right|{R}_C\right) \), R AP = r AP ⋅ Q C , L AP = r AP ⋅ R C and Auth AP = h(T C ||R C ||T AP ||R AP ||K AP ||L AP ). The adversary has to compute L AP = L C = r AP ⋅ r C ⋅ Q C from R C = r C ⋅ Q C and R AP = r AP ⋅ Q C if he wants to compute the session key sk AP = h(T C ||R C ||T AP ||R AP ||L AP ). Then he has to solve the computational Diffie-Hellman problem. Therefore, the proposed authentication scheme could provide perfect forward security.
Theorem 4
The proposed authentication for WBANs could provide unlinkability.
Proof
According to the description of the proposed scheme, the client’s identity is hidden in M 1 = {R C , T C , Auth C }, where R C = r C ⋅ Q C , K C = e(S C , r C ⋅ Q AP ) and \( Aut{h}_C={E}_{K_C}\left({T}_C\left|\right|{R}_C\right) \). The adversary cannot link two messages generated by the same client because the client generates a new random number r C in each execution of the proposed scheme. Therefore, the proposed scheme could provide unlinkability.
Theorem 5
The proposed authentication scheme for WBANs is secure against the impersonation attack.
Proof
Suppose the adversary wants to impersonate the client to the application provider. He has to generate a correct message M 1 = {R C , T C , Auth C }, where R C = r C ⋅ Q C , K C = e(S C , r C ⋅ Q AP ) and \( Aut{h}_C={E}_{K_C}\left(I{D}_C\left|\right|{T}_C\left|\right|{R}_C\right) \). The adversary could generate R C = r C ⋅ Q C easily. However, he cannot generate K C = e(S C , r C ⋅ Q AP ) because he does not have the client’s private key S C . Then the application provider could find the attack by checking the correctness of Auth C . Suppose the adversary wants to impersonate the application provider to the client when he intercepts the message M 1 = {R C , T C , Auth C } sent by the client. He has to generate a correct message M 2 = {R AP , T AP , Auth AP }, where R AP = r AP ⋅ Q C , L AP = r AP ⋅ R C and Auth AP = h(T C ||R C ||T AP ||R AP ||K AP ||L AP ). The adversary could generate R AP = r AP ⋅ Q C and L AP = r AP ⋅ R C easily. However, he cannot generate K AP = e(S AP , R C ) because he does not have the application provider’s private key S AP . Then the client could find the attack by checking the correctness of Auth AP . According to the above analysis, we know that the proposed scheme is secure against the impersonation attack.
Theorem 6
The proposed authentication scheme for WBANs is secure against the man-in-the-middle attack.
Proof
According to the proof of Theorem 1, we know that the proposed scheme could provide mutual authentication between the client and the application provider. Therefore, the proposed scheme is secure against the man-in-the-middle attack.
Theorem 7
The proposed authentication scheme for WBANs is secure against the relay attack.
Proof
The current timestamp is included in messages M 1 = {R C , T C , Auth C } and M 2 = {R AP , T AP , Auth AP } sent between the client and the application provider. Then, the client and the application provider could find the replay attack by checking the freshness of T AP and T C respectively.
Theorem 8
The proposed authentication scheme for WBANs is secure against the modification attack.
Proof
Suppose the adversary intercepts the message M 1 = {R C , T C , Auth C } and send it to the application provider after modification, where R C = r C ⋅ Q C , K C = e(S C , r C ⋅ Q AP ) and \( Aut{h}_C={E}_{K_C}\left({T}_C\left|\right|{R}_C\right) \). It is easy to say that Auth C is the message authentication code of M 1 under the key K C and the adversary does not know the value of K C . Then the application provider could find any modification of M 1 by checking the correctness of Auth C . Though the same method, we could demonstrate that the client could find any modification on the message M 2 = {R AP , T AP , Auth AP }. Therefore, the proposed scheme is secure against the modification attack.
Theorem 9
The proposed authentication scheme for WBANs is secure against the stolen verifier table attack.
Proof
From the description of the proposed scheme, we know that neither the network manager nor the application provider maintains a table to keep information for mutual authentication between the client and the application provider. Then the stolen verifier table attack is not valid for the proposed scheme.
Theorem 10
The proposed authentication scheme for WBANs is secure against the known-key attack.
Proof
From the execution of the proposed scheme, we know a session key sk = h(T C ||R C ||T AP ||R AP ||L) is generated the client and the application provider, where R C = r C ⋅ Q C , R AP = r AP ⋅ Q C and L = r AP ⋅ r C ⋅ Q C . The compromise of a session key in previous session does influence the security of session key in other session because the client and the application provider generate new random numbers r C and r AP respectively. Therefore, the proposed scheme is secure against the known-key attack.
Performance analysis
In this section, we analyze the performance of the proposed authentication scheme for WBANs. We also compare it with Liu et al.’s preliminary scheme [21], Liu et al.’s enhanced scheme [21] and Zhao’s scheme [22].
Compared with the running time of an elliptic curve scale multiplication operation, a bilinear pairing operation and a module exponentiation operation, the running time of other operations in related schemes could be ignored. Therefore, we only need to count the number of such three operations. Let T ME , T SM and T P denote the running time of a module exponentiation operation, an elliptic curve scale multiplication operation and a bilinear pairing operation separately. According to Liu et al.’s experiments, the running time of such three operations is list in Table 1 [21].
The comparison of performance among different schemes is list in Table 2. According to Table 2, the running time of the application provider and the client in the proposed scheme is 2T SM +1T P ≈32.80 ms and 3T SM +1T P ≈188.36 ms separately. The running time of the application provider and the client n Liu et al.’s scheme is 1T ME +1T SM +1T P ≈39.63 ms and 1T ME +4T SM ≈186.19 ms separately. The running time of the application provider and the client in Zhao’s scheme is 6T SM ≈38.28 ms and 13T SM ≈92.01 separately. The proposed scheme has better performance than other three schemes at the application provider side. Zhao et al.’s scheme has better performance than other three schemes at the client side. However, Liu et al.’s scheme cannot withstand the stolen verifier table attack and Zhao et al.’s scheme cannot provide unlinkability. The proposed scheme could overcome those problems and has a acceptable performance. Therefore, the proposed scheme is suitable for WBANs.
Conclusion
With the application of WBANs in our daily life, it is urgent to design authentication scheme for WBANs to ensure secure communication in it. Liu et al. proposed two authentication using certificatless cryptography. However, Zhao pointed out that Liu et al.’s schemes cannot withstand the stolen verifier table attack. Although Zhao’s scheme could solve security problems in Liu et al.’s scheme. Unfortunately, Zhao et al.’s scheme cannot provide unlinkability. In this paper, we propose a novel authentication scheme for WBANs to satisfy practical applications. Security analysis shows the proposed scheme could solve security problems in previous schemes.
References
Zimmerman, T. G., Personal area networks: Near-field intrabody communication. IBM Syst. J. 35(3/4):609–617, 1996.
Kwak, K. S., Sana, U., and Niamat, U., An overview of IEEE 802.15.6 standard. In: Proc. ISABEL 2010, pp. 1–6, 2010.
The Institute of Electrical and Electronics Engineers, 802.15.6–2012—IEEE standard for local and metropolitan area networks—Part 15.6: Wireless body area networks, 2012.
Rivest, R. L., Shamir, A., and Adleman, L., A method for obtaining digital signatures and public key cryptosystems. Commun. ACM 21(2):120–126, 1978.
ElGamal, T., A public key cryptosystem and a signature scheme based on discrete logarithms. IEEE Trans. Inf. Theory IT-31:469–472, 1985.
Tian, X., Wong, D., and Zhu, R., Analysis and improvement of authenticated key exchange protocol for sensor networks. IEEE Commun. Lett. 9(11):970–972, 2005.
Jia, Z., Zhang, Y., Shao, H., Lin, Y., and Wang, J., A remote user authentication scheme using bilinear pairings and ECC. In: Proceedings of the sixth international conference on intelligent system design and applications; 1091–1094, 2006.
Jiang, C., Li, B., and Xu, H., An efficient scheme for user authentication in wireless sensor networks. In: Proceedings of 21st international conference on advanced information networking and applications workshops; 438–442, 2007.
Liao, Y., and Wang, S., A secure and efficient scheme of remote user authentication based on bilinear pairings. In: Proceedings of 2007 I.E. region 10 conference; 1–4, 2007.
Abichar, P., Mhamed, A., and Elhassan, B., A fast and secure elliptic curve based authenticated key agreement protocol for low power mobile communications. In: Proceedings of the 2007 international conference on next generation mobile applications, services and technologies; 235–240, 2007.
Miller, V. S., Use of elliptic curves in cryptography. In: Advances in cryptology, proceedings of CRYPTO’85, 417–26, 1986.
Koblitz, N., Elliptic curve cryptosystem. Math. Comput. 48:203–209, 1987.
Shamir, A., Identity based cryptosystems and signature schemes. In: Proceedings of CRYPTO’ 84; 47–53, 1984.
Jiang, Q., Ma, J., Ma, Z., et al., A privacy enhanced authentication scheme for telecare medical information systems. J. Med. Syst. 37(1):1–8, 2013.
Das, A. K., and Bruhadeshwar, B., An improved and effective secure password-based authentication and key agreement scheme using smart cards for the telecare medicine information system. J. Med. Syst. 37(5):1–17, 2013.
Tan, Z., A user anonymity preserving three-factor authentication scheme for Telecare medicine information systems. J. Med. Syst. 38(3):1–9, 2014.
He, D., and Zeadally, S., Authentication protocol for ambient assisted living system. IEEE Commun. Mag. 35(1):71–77, 2015.
He, D., Kumar, J., Chen, J., et al., Robust anonymous authentication protocol for healthcare applications using wireless medical sensor networks. Multimedia Systems 21(1):49–60, 2015.
He, D., Kumar, J., and Chilamkurti, N., A secure temporal-credential-based mutual authentication and key agreement scheme with pseudo identity for wireless sensor networks. Inf. Sci. 321:263–277, 2015.
He, D., and Wang, D., Robust biometrics-based authentication scheme for multi-server environment. IEEE Syst. J. 9(3):816–823, 2015.
Liu, J., Zhang, Z., Chen, X., and Kwak, K., Certificateless remote anonymous authentication schemes for wireless body sensor networks. IEEE Trans. Parallel Distrib. Syst. 25(2):332–342, 2014.
Zhao, Z., An efficient anonymous authentication scheme for wireless body area networks using elliptic curve cryptosystem. J. Med. Syst. 38(2):1–7, 2014.
Burrows, M., Abadi, M., and Needham, R., A logic of authentication. ACM Trans. Comput. Syst. 8(1):18–36, 1990.
Shen, J., Tan, H., Wang, J., et al., A novel routing protocol providing good transmission reliability in underwater sensor networks. J. Internet Technol. 16(1):171–178, 2015.
Fu, Z., Sun, X., Liu, Q., et al., Achieving efficient cloud search services: Multi-keyword ranked search over encrypted cloud data supporting parallel computing. IEICE Trans. Commun. E98-B(1):190–200, 2015.
Wang, D., He, D., Wang, P., et al., Anonymous two-factor authentication in distributed systems: Certain goals are beyond attainment. IEEE Trans. Dependable Secure Comput. 12(4):428–442, 2015.
Zhu, Z., An efficient authentication scheme for telecare medicine information systems. J. Med. Syst. 36(6):3833–3838, 2012.
Guo, P., Wang, J., Li, B., et al., A variable threshold-value authentication architecture for wireless mesh networks. J. Internet Technol. 15(6):929–936, 2014.
Zhao, Z., A secure RFID authentication protocol for healthcare environments using elliptic curve cryptosystem. J. Med. Syst. 38(5):1–7, 2014.
Xie, Q., Liu, W., Wang, S., et al., Improvement of a uniqueness-and-anonymity-preserving user authentication scheme for connected health care. J. Med. Syst. 38:91, 2014.
Acknowledgments
This research is supported by the Natural Science Foundation of Hubei Province of China (No. 2013CFB021) and the National Natural Science Foundation of China (No. 61170135).
Conflict of Interest
The authors declare that he has no conflict of interest.
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is part of the Topical Collection on Systems-Level Quality Improvement
Rights and permissions
About this article
Cite this article
Wang, C., Zhang, Y. New Authentication Scheme for Wireless Body Area Networks Using the Bilinear Pairing. J Med Syst 39, 136 (2015). https://doi.org/10.1007/s10916-015-0331-2
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-015-0331-2