Abstract
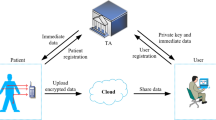
The technology of IoT combined with medical systems is expected to support advanced medical services. However, unsolved security problems, such as misuse of medical devices, illegal access to the medical server and so on, make IoT-based medical systems not be applied widely. In addition, users have a high burden of computation to access Things for the explosive growth of IoT devices. Because medical information is critical and important, but users have a restricted computing power, IoT-based medical systems are required to provide secure and efficient authentication for users. In this paper, we propose a selective group authentication scheme using Shamir’s threshold technique. The property of selectivity gives the right of choice to users to form a group which consists of things users select and access. And users can get an access authority for those Things at a time. Thus, our scheme provides an efficient user authentication for multiple Things and conditional access authority for safe IoT-based medical information system. To the best of our knowledge, our proposed scheme is the first in which selectivity is combined with group authentication in IoT environments.




Similar content being viewed by others
References
Jiang, Q., Ma, J., Ma, Z., and Li, G., A privacy enhanced authentication scheme for telecare medical information systems. J. Med. Syst. 37:9897, 2013.
Roman, R., Najera, P., and Lpoez, J., Securing the internet of things. Comput. 44(9):51–58, 2011.
Weber, R. H., Internet of Things—New security and privacy challenges. Comput. Law Security Rev. 26(1): 23–30, 2010.
Li, S. H., Wang, C. Y., LuW, H., Lin, Y. Y., and Yen, D. C., Design and implementation of a telecare information platform. J. Med. Syst. 36(3):1629–1650, 2012.
Gritzalis, S., Lambrinoudakis, C., Lekkas, D., and Deftereos, S., Technical guidelines for enhancing privacy and data protection in modern electronic medical environments. IEEE Trans. Inf. Technol. Biomed. 9(3):413–423, 2005.
Lambrinoudakis, C., and Gritzalis, S., Managing medical and insurance information through a smart-card-based information system. J. Med. Syst. 24(4):213–234, 2000.
Wu, Z. Y., Chung, Y., Lai, F., and Chen, T. S., A password-based user authentication scheme for the integrated EPR information system. J. Med. Syst. 36(2):631–638, 2012.
Kumari, S., Khan, M. K., and Kumar, R., Cryptanalysis and improvement of ’A privacy enhanced scheme for telecare medical information systems’. J. Med. Syst. 37:9952, 2013.
Cao, T., and Zhai, J., Improved dynamic ID-based authentication scheme for telecare medical information systems. J. Med. Syst. 37:9912, 2013.
Turkanovic, M., Brumen, B., and Hölbl, M., A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 20:96–112, 2014.
Yao, X., Han, X., Du, X., and Zhou, X., A lightweight multicast authentication mechanism for small scale IoT applications. IEEE Sensors J. 13(10):3693–3701, 2013.
Ndibanje, B., Lee, H. J., and Lee, S. G., Security analysis and improvements of authentication and access control in the internet of Things. Sensors 14(8):14786–14805, 2014.
Mahalle, P. N., Prasad, N. R., and Prasad, R., Threshold cryptography-based group authentication (TCGA) scheme for the Internet of Things (IoT), Wireless Communications, Vehicular Technology, Information Theory and Aerospace & Electronic Systems (VITAE) (2014)
Chen, H. M., Lo, J. W., and Yeh, C. K., An efficient and secure dynamic ID-based authentication scheme for telecare medical information systems. J. Med. Syst. 36(6):3907–3915, 2012.
Amin, R., Islam, S. K. H., Biswas, G. P., Khan, M. K., and Kumar, N., An efficient and practical smart card based anonymity preserving user authentication scheme for TMIS using elliptic curve cryptography. J. Med. Syst. 39:180, 2015.
Peng, S., An ID-based multiple authentication scheme against attacks in wireless sensor networks, CCIS 2012 (2012)
Shi, W., and Gong, P., A new user authentication protocol for wireless sensor networks usign elliptic curves cryptography. International Journal of Distributed Sensor Networks, 2013. Article ID 730831.
Sun, H. M., He, B. Z., Chen, C. M., Wu, T. Y., Lin, C. H., and Wang, H., A provable authenticated group key agreement protocol for mobile environment. Information Sciences 321(10):224–237, 2015.
Xu, B., Xu, L. D., Cai, H., Xie, C., Hu, J., and Bu, F., Ubiquitous data accessing method in IoT-based information system for emergency medical services. IEEE Trans. on Industrial Informatics 10(2):1578–1586, 2014.
Porambage, P., Schmitt, C., Kumar, P., Gurtov, A., Ylianttila, M., and Pauthkey, A pervasive authentication protocol and key establishment scheme for wireless sensor networks in distributed IoT applications. International Journal of Distributed Sensor Networks 2014, 2014. Article ID 357430.
Hou, J. L., and Yeh, K. H., Novel authentication schemes for IoT based healthcare systems. International Journal of Distributed Sensor Networks 2015, 2015. Article ID 183659.
Harn, L., and Lin, C., Authenticated Group Key Transfer Protocol Based on Secret Sharing. IEEE Trans. Computers 59(6):842–846, 2010.
Shamir, A., How to share a secret. Comm. ACM. 22(11):612–613, 1979.
Herzberg, A., Jarecki, S., Krawczyk, H., and Yung, M., Proactive secret sharing or: how to cope with perpetual leakage. CRYPTO 95,339–352, 1995.
Zhang, Y., and Lee, W., Intrusion detection in wireless ad-hoc networks. Mobicom 2000,275–283, 2000.
Bechler, M., Hof, H. J., Kraft, D., Pahlke, F., and Wolf, L., A cluster-based security architecture for ad hoc networks. Infocom, 2004,2393–2403, 2004.
Li, L.-C., and Liu, R.-S., Securing cluster-based ad hoc networks with distributed authorities. IEEE Trans. on Wireless Communications 9(10):3072–3081, 2010.
Menezes, A. J., van Oorschot, P. C., and Vanstone, S. A., Handbook of Applied Cryptography, pp. 524–526: CRC Press.
Acknowledgments
This study was supported by the BK21 Plus project funded by the Ministry of Education, Korea (21A20131600011).
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is part of the Topical Collection on Mobile & Wireless Health
Rights and permissions
About this article
Cite this article
Park, Y., Park, Y. A Selective Group Authentication Scheme for IoT-Based Medical Information System. J Med Syst 41, 48 (2017). https://doi.org/10.1007/s10916-017-0692-9
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-017-0692-9