Abstract
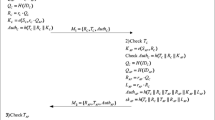
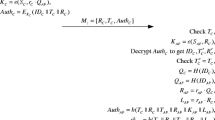
An increase in aging population and the consequent chronic diseases pose not only serious effects to the economy but also a heavy burden to the medical system. Wireless body area networks (WBANs) provide a simple and low-cost strategy for health monitoring and telemedicine of the elderly. Many authentication schemes based on WBAN have been presented to address the sensitivity and privacy of collected data and the open characteristic of wireless networks. Wu et al. recently presented an efficient anonymous authentication scheme for WBANs, in which a one-side bilinear pairing methodology was applied to reduce the burden on the WBAN client side. However, we demonstrate that their scheme suffers from client impersonation attacks and that the adversary can easily forge a legal client to access the network service. In this paper, we analyze the limitations of Wu et al.’s scheme and design a novel mutual authentication scheme for WBANs that adopt asymmetric bilinear pairing to enhance security. Results of security and performance analyses reveal that the new scheme offers more effective security, better performance, and higher efficiency than Wu et al.’s scheme. We also provide a formal security proof of the protocol by using BAN authentication logic.



Similar content being viewed by others
References
WHO, Life expectancy increased by 5 years since 2000, but health inequalities persist. Saudi Med. J. 37(6): 717–717, 2016.
Zimmerman, T. G., Personal area networks: near-field intrabody communication. IBM Syst. J. 35(3/4):609–617, 1996.
Ieee standard for local and metropolitan area networks - part 15.6: Wireless body area networks in IEEE Std, 2012
Toorani, M.: On vulnerabilities of the security association in the ieee 802.15.6 standard. In: International conference on financial cryptography and data security, pp. 245–260, 2015.
Toorani, M., Security analysis of the ieee 802.15.6 standard. Int. J. Commun. Syst. 29(17):2471–2489, 2016.
Monton, E., Hernandez, J. F., Blasco, J. M., and Hervé, T., Body area network for wireless patient monitoring. IET Commun. 2(2):215–222, 2008.
Seyedi, M., Kibret, B., Lai, D. T., and Faulkner, M., A survey on intrabody communications for body area network applications. IEEE Trans. Biomed. Eng. 60(8):2067–79, 2013.
He, D., Zeadally, S., and Wu, L., Certificateless public auditing scheme for cloud-assisted wireless body area networks. IEEE Syst. J. PP(99):1–10, 2015.
Jang, C. S., Lee, D. G., and Han, J. W.: A proposal of security framework for wireless body area network. In: International conference on security technology, pp. 202–205, 2008.
Rivest, R. L., Shamir, A., and Adleman, L., A method for obtaining digital signatures and public-key cryptosystems. Communications of the Acm 21(2):120–126, 1978.
Elgamal, T., A public key cryptosystem and a signature scheme based on discrete logarithms. IEEE Trans. Inf. Theory 31(4):469–472, 1984.
He, D., and Zeadally, S., Authentication protocol for ambient assisted living system. IEEE Commun. Mag. 35(1):71–77 , 2015.
He, D., Kumar, N., Chen, J., Lee, C. C., Chilamkurti, N., and Yeo, S. S., Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multimed. Syst. 21(1): 49–60, 2015.
He, D., Kumar, N., and Chilamkurti, N., A secure temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. Int. Symposium Wireless Pervasive Comput. 321(1):263–277, 2015.
He, D., and Wang, D., Robust biometrics-based authentication scheme for multiserver environment. IEEE Syst. J. 9(3):816–823, 2015.
Huang, X., Xiang, Y., Bertino, E., Zhou, J., and Xu, L., Robust multi-factor authentication for fragile communications. IEEE Trans. Dependable Secure Comput. 11(6):568–581, 2014.
Drira, W., Renault, E., and Zeghlache, D.: A hybrid authentication and key establishment scheme for wban. In: IEEE international conference on trust, security and privacy in computing and communications, pp. 78–83, 2012.
Liu, J., Zhang, Z., Chen, X., and Kwak, K. S., Certificateless remote anonymous authentication schemes for wirelessbody area networks. IEEE Trans. Parallel Distrib. Syst. 25(2):3332–342, 2014.
Xiong, H., and Qin, Z., Revocable and scalable certificateless remote authentication protocol with anonymity for wireless body area networks. IEEE Trans. Inf. Forensics Secur. 10(7):1442–1455, 2015.
Al-Riyami, S. S., and Paterson, K.G.: Certificateless public key cryptography. In: International conference on the theory and application of cryptology and information security, pp. 452–473, 2003.
Xiong, H., Cost-effective scalable and anonymous certificateless remote authentication protocol. IEEE Trans. Inf. Forensics Secur. 9(12):2327–2339, 2014.
Zhang, L., Liu, J., and Sun, R.: An efficient and lightweight certificateless authentication protocol for wireless body area networks. In: International conference on intelligent networking and collaborative systems, pp. 637–639, 2013.
Kang, B., Wang, J., and Shao, D.: Certificateless public auditing with privacy preserving for cloud-assisted wireless body area networks, Mobile Information Systems 2017(2017-7-6), 2017
He, D., Zeadally, S., Kumar, N., and Lee, J. H., Anonymous authentication for wireless body area networks with provable security. IEEE Syst. J. PP(99):1–12, 2016.
Zhao, Z., An efficient anonymous authentication scheme for wireless body area networks using elliptic curve cryptosystem. J. Med. Syst. 38(2):1–7, 2014.
Wang, C., and Zhang, Y., New authentication scheme for wireless body area networks using the bilinear pairing. J. Med. Syst. 39(11):1–8, 2015.
Wu, L., Zhang, Y., Li, L., and Shen, J., Efficient and anonymous authentication scheme for wireless body area networks. J. Med. Syst. 40(6):1–12, 2016.
Menezes, A. J., Okamoto, T., and Vanstone, S.A.: Reducing elliptic curve logarithms to logarithms in a finite field. In: ACM symposium on theory of computing, pp. 80–89, 1991.
Burrows, M., Abadi, M., and Needham, R., A logic of authentication. Acm Sigops Operating Systems Review 8(1):18–36, 1990.
Acknowledgements
This work was supported in part by the National Natural Science Foundation of China under grants U1435213 and 61172180, and Chengdu International Cooperation Project under grants 2016-GH02-00048-HZ and 2015-GH02-00041- HZ, and General Project of Education Department in Sichan under grants 18ZB0485.
Funding
This study was funded by National Natural Science Foundation of China (grant number U1435213 and 61172180), and Chengdu International Cooperation Project (grant number 2016-GH02-00048-HZ and 2015-GH02-00041-HZ), and General Project of Education Department in Sichuan (grant number 18ZB0485).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interests
Author Dezhong Peng has received research grants from National Natural Science Foundation of China and Chengdu International Cooperation Project. Author Rui Chen has received research grants from General Project of Education Department in Sichuan. Author Dezhong Peng declares that he has no conflict of interest. Author Rui Chen declares that he has no conflict of interest.
Ethical approval
This article does not contain any studies with human participants performed by any of the authors.
Additional information
This article is part of the Topical Collection on Systems-Level Quality Improvement
Rights and permissions
About this article
Cite this article
Chen, R., Peng, D. Analysis and Improvement of a Mutual Authentication Scheme for Wireless Body Area Networks. J Med Syst 43, 19 (2019). https://doi.org/10.1007/s10916-018-1129-9
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-018-1129-9