Abstract
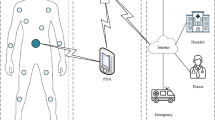
Real-time and ubiquitous patient monitoring demands the use of wireless data acquisition through resource constrained medical sensors, mostly configured with No-input No-output (NiNo) capabilities. Bluetooth is one of the most popular and widely adopted means of communicating this sensed information to a mobile terminal. However, over simplified implementations of Bluetooth low energy (BLE) protocol in eHealth sector is susceptible to several wireless attacks, in particular the Man-in-the-Middle (MITM) attack. The issue arises due to a lack of mutual authentication and integrity protection between the communicating devices, which may lead to compromise of confidentiality, availability and even the integrity of this safety-critical information. This research paper presents a novel framework named MARC to detect, analyze, and mitigate Bluetooth security flaws while focusing upon MITM attack against NiNo devices. For this purpose, a comprehensive solution has been proposed, which can detect MITM signatures based upon four novel anomaly detection metrics: analyzing Malicious scan requests, Advertisement intervals, RSSI levels, and Cloned node addresses. The proposed solution has been evaluated through practical implementation and demonstration of different attack scenarios, which show promising results concerning accurate and efficient detection of MITM attacks.













Similar content being viewed by others
References
Bello, O., Zeadally, S., Toward efficient smartification of the Internet of Things (IoT) services. Futur. Gener. Comput. Syst., 2017.
Yaseen, M., Saleem, K., Orgun, M. A., Abbas, H., Al-Muhtadi, J., Iqbal, W., Rashid, I., Secure sensors data acquisition and communication protection in eHealthcare: Review on the state of the art. Telematics Inform., 2017.
B.S. Proprietary, Bluetooth Core Specification version 5.0, in, Bluetooth, 2016.
Agrawal, V. M., and Chauhan, H., An overview of security issues in mobile ad hoc networks. International Journal of Computer Engineering and Sciences 1:9–17, 2015.
Jo, M., Han, L., Tan, N. D., and In, H. P., A survey: Energy exhausting attacks in MAC protocols in WBANs. Telecommunication Systems 58:153–164, 2014.
Kang, J., Adibi, S., A review of security protocols in mhealth wireless body area networks (WBAN), in: Communications in Computer and Information Science, Springer Science + Business Media, pp. 61–83, 2015.
Padgette, J., Guide to bluetooth security. NIST Special Publication 800:121, 2017.
Thilakanathan, D., Chen, S., Nepal, S., Calvo, R., and Alem, L., A platform for secure monitoring and sharing of generic health data in the cloud. Future Generation Computer Systems 35:102–113, 2014.
Arney, T. O., A literature review on the current state of security and privacy of medical devices and sensors with bluetooth low energy, 2018.
Ray, A., Raj, V., Oriol, M., Monot, A., Obermeier, S., Bluetooth low energy devices security testing framework, in: 2018 IEEE 11th International Conference on Software Testing, Verification and Validation (ICST), IEEE, pp. 384–393, 2018.
Albahar, M.A., Haataja, K., Toivanen, P., Bluetooth mitm vulnerabilities: A literature review, novel attack scenarios, novel countermeasures, and lessons learned. Int. J. Inf. Technol. Secur. 8, 2016.
Jasek, S., Gattacking Bluetooth smart devices, in: Black Hat USA Conference, 2016.
Ryan, M., Bluetooth: With low energy comes low security, in: WOOT, 2013.
Guo, Z., Harris, I. G., Jiang, Y., Tsaur, L.-F., An efficient approach to prevent Battery Exhaustion Attack on BLE-based mesh networks, in: Computing, Networking and Communications (ICNC), 2017 International Conference on, IEEE, pp. 1–5, 2017.
Saravanan, K., Vijayanand, L., Negesh, R., A novel bluetooth man-in-the-middle attack based on SSP using OOB association model, arXiv preprint arXiv:1203.4649, 2012.
Wang, P., Bluetooth low energy-privacy enhancement for advertisement, in, Institutt for telematikk, 2014.
ALMomani, I., Al-Saruri, M., and Al-Akhras, M., Secure public key exchange against man-in-the-middle attacks during secure simple pairing (ssp) in bluetooth. World Applied Sciences Journal 13:769–780, 2011.
Haataja, K. M., Hypponen, K., Man-in-the-middle attacks on bluetooth: a comparative analysis, a novel attack, and countermeasures, in: Communications, Control and Signal Processing, 2008. ISCCSP 2008. 3rd International Symposium on, IEEE, pp. 1096–1102, 2008.
Moon, J., Jung, I. Y., and Yoo, J., Security enhancement of wireless sensor networks using signal intervals. Sensors 17:752, 2017.
Albahar, M. A., Haataja, K., Toivanen, P., Towards enhancing just works model in bluetooth pairing. Int. J. Inf. Technol. Secur. 8, 2016.
Zhang, Q., Liang, Z., and Cai, Z., Developing a new security framework for bluetooth low energy devices. CMC-Computers Materials & Continua 59:457–471, 2019.
Shen, J., Yuen, T. T., Choo, K.-K. R., Zeng, Q., AMOGAP: Defending against man-in-the-middle and offline guessing attacks on passwords, in: Australasian Conference on Information Security and Privacy, Springer, pp. 514–532, 2019.
Jie, Y., Choo, K.-K. R., Li, M., Chen, L., Guo, C., Tradeoff gain and loss optimization against man-in-the-middle attacks based on game theoretic model. Futur. Gener. Comput. Syst., 2019.
Haataja, K., Toivanen, P., Two practical man-in-the-middle attacks on bluetooth secure simple pairing and countermeasures. IEEE Trans. Wirel. Commun. 9, 2010.
Gajbhiye, S., Karmakar, S., Sharma, M., and Sharma, S., Bluetooth secure simple pairing with enhanced security level. Journal of information security and applications 44:170–183, 2019.
Gajbhiye, S., Karmakar, S., Sharma, M., and Sharma, S., Two-party secure connection in Bluetooth-enabled devices. Information Security Journal: A Global Perspective 27:42–56, 2018.
Sun, D.-Z., Mu, Y., and Susilo, W., Man-in-the-middle attacks on secure simple pairing in Bluetooth standard V5. 0 and its countermeasure. Personal and Ubiquitous Computing 22:55–67, 2018.
Hassan, S. S., Bibon, S. D., Hossain, M. S., Atiquzzaman, M., Security threats in bluetooth technology. Comput. Secur., 2017.
Acknowledgements
The authors extend their appreciation to the Deanship of Scientific Research at King Saud University for funding this work through research group no (RG-1439-022).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Highlights
• Simulation of MITM attack using Gattacker on Bluetooth Low Energy (BLE) NiNo devices.
• Detailed comparison and critical analysis of existing solutions.
• Automated detection of MITM and cloned-node attacks using a novel mechanism.
• Design evaluation through implementation of multiple mitigation techniques
This article is part of the Topical Collection on Systems-Level Quality Improvement
Rights and permissions
About this article
Cite this article
Yaseen, M., Iqbal, W., Rashid, I. et al. MARC: A Novel Framework for Detecting MITM Attacks in eHealthcare BLE Systems. J Med Syst 43, 324 (2019). https://doi.org/10.1007/s10916-019-1440-0
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-019-1440-0