Abstract
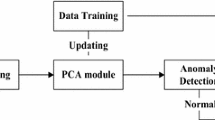
In this paper we demonstrate how to monitor a smartphone running Symbian operating system and Windows Mobile in order to extract features for anomaly detection. These features are sent to a remote server because running a complex intrusion detection system on this kind of mobile device still is not feasible due to capability and hardware limitations. We give examples on how to compute relevant features and introduce the top ten applications used by mobile phone users based on a study in 2005. The usage of these applications is recorded by a monitoring client and visualized. Additionally, monitoring results of public and self-written malwares are shown. For improving monitoring client performance, Principal Component Analysis was applied which lead to a decrease of about 80% of the amount of monitored features.










Similar content being viewed by others
Notes
In the sense of this work, we will use the expressions smartphone, mobile phone and mobile device equivalently.
Global Positioning System.
Global System for Mobile Communications.
Short Message Service.
General Packet Radio Service.
Wideband Code Division Multiple Access.
Freedom of Mobile Multimedia Access.
Universal Mobile Telecommunications System.
Infrared Data Association.
Formerly: Simple Object Access Protocol.
Tested on Version 9.1 S60 3rd.
International Mobile Equipment Identity.
International Mobile Subscriber Identity.
Will be substituted with MP3 (19%) due to UMTS usage and increasing interest for MP3 capabilities on devices.
This class was removed since all values are already represented.
References
Abowd GD, Iftode L, Mitchel H (2005) The Smart phone: a first platform for pervasive computing. IEEE Perv Comput 4:18–19
Albayrak S, Scheel C, Milosevic D, Müller A (2005) Combining self-organizing map algorithms for robust and scalable intrusion detection. In: Mohammadian M (ed) Proceedings of international conference on computational intelligence for modelling control and automation (CIMCA 2005). IEEE Computer Society, Los Alamitos, pp 123–130
Allen J, Christie A, Fithen W, McHugh J, Pickel J, Stoner E (2000) State of the practice of intrusion detection technologies. Technical Report, CMU/SEI-99-TR-028. Carnegie Mellon Software Engeneering Institue, Pittsburgh, PA, pp 15213–3890
Axelsson S (2000) Intrusion detection systems: a survey and taxonomy. Technical Report 99-15. Department of Computer Engineering Chalmers University of Technology Göteborg, Sweden
Buennemeyer TK, Nelson TM, Clagett LM, Dunning JP, Marchany RC, Tront JG (2008) Mobile device profiling and intrusion detection using smart batteries. In: HICSS ’08: Proceedings of the proceedings of the 41st annual Hawaii international conference on system sciences, p 296. IEEE Computer Society, Washington, DC. doi:10.1109/HICSS.2008.319
Bundesverband Informationswirtschaft Telekommunikation und neue Medien e.V.-BITKOM (2006) Mehr Handys als Einwohner in Deutschland. http://www.bitkom.de/41015_40990.aspx
Bulygin Y (2007) Epidemics of mobile worms. In: Proceedings of the 26th IEEE international performance computing and communications conference, IPCCC 2007, New Orleans, 11–13 April 2007. IEEE Computer Society, Los Alamitos, pp 475–478
Canalys (2006) EMEA Q3 2006—Highlight From the Canalys Research. http://www.canalys.com/pr/2006/r2006102.htm. http://www.canalys.com/ (online visited 2007.10.04)
Cheng J, Wong SHY, Yang H, Lu S (2007) Smartsiren: virus detection and alert for smartphones. In: International conference on mobile systems, applications, and services (Mobisys 2007), Puerto Rico, 11–14 June 2007, pp. 258–271
Davis G, Davis N (2004) Battery-based intrusion detection. In: Global telecommunications conference, 2004. GLOBECOM ’04, vol 4. IEEE, Piscataway, pp 2250–2255. doi:10.1109/GLOCOM.2004.1378409
Deegalla S, Bostrom H (2006) Reducing high-dimensional data by principal component analysis vs. random projection for nearest neighbor classification. In: ICMLA ’06: Proceedings of the 5th international conference on machine learning and applications. IEEE Computer Society, Washington, DC, pp 245–250. doi:10.1109/ICMLA.2006.43
Forrest S, Perelson AS, Allen L, Cherukuri R (1994) Self-nonself discrimination in a computer. In: Proceedings of the IEEE symposium on research in security and privacy. IEEE Computer Society, Silver Spring, pp 202–212
Glickman M, Balthrop J, Forrest S (2005) A machine learning evaluation of an artificial immune system. Evol Comput 13(2):179–212 (2005). doi:10.1162/1063656054088503
Gostev A (2006) Mobile malware evolution: An overview, part 1. http://www.viruslist.com/en/analysis?pubid=200119916
Gröber M (2007) Applications for Symbian. http://www.mgroeber.de/epoc.htm (15 Aug 2007)
Hofmeyr S, Forrest S (2000) Architecture for an artificial immune system. Evol Comput J 8(4):443–473. doi:10.1162/106365600568257
Jamaluddin J, Zotou N, Edwards R, Coulton P (2004) Mobile phone vulnerabilities: a new generation of malware. In: Proceedings of the 2004 IEEE international symposium on consumer Electronics. IEEE, Piscataway, pp 199–202
Kohonen T (2001) Self-organizing maps. Springer series in information sciences, vol 30, 3rd edn. Springer, Heidelberg. ISBN 3–540–67921–9, ISSN 0720–678X
Lawton G (2002) Open source security: opportunity or oxymoron? Comput 35(3):18–21. doi:10.1109/2.989921
Luther K, Bye R, Alpcan T, Albayrak S, Müller A (2007) A cooperative AIS framework for intrusion detection. In: Proceedings of the IEEE international conference on communications (ICC 2007), Glasgow, 24–28 June 2007
Microsoft Corporation (2007) Windows Mobile. http://www.microsoft.com/germany/windowsmobile/default.mspx. http://www.microsoft.com/ (online visited 2007.10.04)
Miettinen M, Halonen P, Hätönen K (2006) Host-based intrusion detection for advanced mobile devices. In: AINA ’06: proceedings of the 20th international conference on advanced information networking and applications, vol 2 (AINA’06). IEEE Computer Society, Washington, DC, pp. 72–76. doi:http://dx.doi.org/10.1109/AINA.2006.192
Nokia (2007) Nokia E61. http://www.nokia.co.uk/A4221036 (15 Aug 2007)
Oberheide J, Cooke E, Jahanian F (2008) Cloudav: N-version antivirus in the network cloud. In: Proceedings of the 17th USENIX security symposium (Security’08), San Jose, 28 July–1 August 2008
Rhodes BC, Mahaffey JA, Cannady JD (2000) Multiple self-organizing maps for intrusion detection. In: 23rd National information systems security conference—PROCEEDINGS, PAPERS, and SLIDE PRESENTATIONS. http://csrc.nist.gov/nissc/2000/proceedings/2000proceedings.html (2007-04-19)
Roussos G, March AJ, Maglavera S (2005) Enabling pervasive computing with Smart phones. IEEE Perv Comput 4:20–27
Spafford E, Zamboni D (2000) Data collection mechanisms for intrusion detection systems. CERIAS Technical Report 2000-08. CERIAS, Purdue University, 1315 Recitation Building, West Lafayette, IN
Symbian Software Limited (2007) Symbian OS—the mobile operating system. http://www.symbian.com (online visited 2007.10.04)
TNS Technology (2005) Consumer trends in mobile applications—a TNS technology briefing for technology decision makers. http://www.tns-global.com/ (online visited 2007.10.04)
Author information
Authors and Affiliations
Corresponding author
Additional information
This work was funded by Deutsche Telekom Laboratories.
Appendix: Definitions
Appendix: Definitions
The detection result charts base on the following definitions where Table 10 shows a description on the detection classification:
-
TP = True Positives
-
FN = False Negatives
-
FP = False Positives
-
TN = True Negatives
-
FA = False Alarm
Rights and permissions
About this article
Cite this article
Schmidt, AD., Peters, F., Lamour, F. et al. Monitoring Smartphones for Anomaly Detection. Mobile Netw Appl 14, 92–106 (2009). https://doi.org/10.1007/s11036-008-0113-x
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-008-0113-x